- List all connected SSH sessions?
- 7 Answers 7
- 6 commands to check and list active SSH connections in Linux
- Check active SSH connections
- 1. Using ss command
- 2. Using last command
- 3. Using who command
- 4. Using w command
- 5. Using netstat command
- 6. Using ps command
- Check ssh connection history
- Просмотр истории входа в Linux. Кто и когда входил в систему
- Где хранятся логи входа в систему
- Просмотр истории входа в систему
- Просмотр истории входа для определенного пользователя
- Ограничить количество строк
- Просмотр неудачных попыток входа в систему
- Заключение
List all connected SSH sessions?
I just SSH’d into root, and then SSH’d again into root on the same machine. So I have two windows open both SSH’d into root on my remote machine. From the shell, how can I see a list of these two sessions?
7 Answers 7
who or w ; who -a for additional information.
These commands just show all login sessions on a terminal device. An SSH session will be on a pseudo-terminal slave ( pts ) as shown in the TTY column, but not all pts connections are SSH sessions. For instance, programs that create a pseudo-terminal device such as xterm or screen will show as pts . See Difference between pts and tty for a better description of the different values found in the TTY column. Furthermore, this approach won’t show anybody who’s logged in to an SFTP session, since SFTP sessions aren’t shell login sessions.
I don’t know of any way to explicitly show all SSH sessions. You can infer this information by reading login information from utmp / wtmp via a tool like last , w , or who like I’ve just described, or by using networking tools like @sebelk described in their answer to find open tcp connections on port 22 (or wherever your SSH daemon(s) is/are listening).
A third approach you could take is to parse the log output from the SSH daemon. Depending on your OS distribution, SSH distribution, configuration, and so on, your log output may be in a number of different places. On an RHEL 6 box, I found the logs in /var/log/sshd.log . On an RHEL 7 box, and also on an Arch Linux box, I needed to use journalctl -u sshd to view the logs. Some systems might output SSH logs to syslog. Your logs may be in these places or elsewhere. Here’s a sample of what you might see:
[myhost ~]% grep hendrenj /var/log/sshd.log | grep session May 1 15:57:11 myhost sshd[34427]: pam_unix(sshd:session): session opened for user hendrenj by (uid=0) May 1 16:16:13 myhost sshd[34427]: pam_unix(sshd:session): session closed for user hendrenj May 5 14:27:09 myhost sshd[43553]: pam_unix(sshd:session): session opened for user hendrenj by (uid=0) May 5 18:23:41 myhost sshd[43553]: pam_unix(sshd:session): session closed for user hendrenj The logs show when sessions open and close, who the session belongs to, where the user is connecting from, and more. However, you’re going to have to do a lot of parsing if you want to get this from a simple, human-readable log of events to a list of currently active sessions, and it still probably won’t be an accurate list when you’re done parsing, since the logs don’t actually contain enough information to determine which sessions are still active — you’re essentially just guessing. The only advantage you gain by using these logs is that the information comes directly from SSHD instead of via a secondhand source like the other methods.
I recommend just using w . Most of the time, this will get you the information you want.
6 commands to check and list active SSH connections in Linux
How to check active SSH connections in Linux. Show SSH connection history. How to show active ssh sessions in Linux. List all the active SSH connections in Unix. Find out all the currently active ssh connections on any Linux node. Which all tools can be used to list all the active ssh connections in Linux. Show active SSH sessions. Check ssh connection history using log files in Linux.
Some more more articles you may be interested on similar topics:
Check active SSH connections
There are various commands and tools available in Linux which can be used to check active SSH connections or sessions on your Linux node. In this article I will share a list of tools which can be used to get the list of active SSH connections. If you are aware of any more commands to show active ssh sessions then please let me know via comment section.
1. Using ss command
ss is used to dump socket statistics. It allows showing information similar to netstat . It can display more TCP and state information than other tools. We will use grep function to only get the list of active SSH sessions on our local host
[root@node3 ~]# ss | grep -i ssh tcp ESTAB 0 0 10.0.2.32:ssh 10.0.2.31:37802 tcp ESTAB 0 64 10.0.2.32:ssh 10.0.2.2:49966 tcp ESTAB 0 0 10.0.2.32:ssh 10.0.2.30:56088
From the above example we know that there are three hosts which are currently connected to our node3. We have active SSH connections from 10.0.2.31, 10.0.2.30 and 10.0.2.2
2. Using last command
last searches back through the file /var/log/wtmp (or the file designated by the -f flag) and displays a list of all users logged in (and out) since that file was created. Names of users and tty’s can be given, in which case last will show only those entries matching the arguments.
Using this command you can also get the information about the user using which the SSH connection was created between server and client. So below we know the connection from 10.0.2.31 is done using ‘deepak‘ user, while for other two hosts, ‘root‘ user was used for connecting to node3.
[root@node3 ~]# last -a | grep -i still deepak pts/1 Fri May 31 16:58 still logged in 10.0.2.31 root pts/2 Fri May 31 16:50 still logged in 10.0.2.30 root pts/0 Fri May 31 09:17 still logged in 10.0.2.2
Here I am grepping for a string «still» to get all the patterns with » still logged in «. So now we know we have three active SSH connections from 10.0.2.31, 10.0.2.30 and 10.0.2.2
3. Using who command
who is used to show who is logged on on your Linux host. This tool can also give this information
[root@node3 ~]# who root pts/0 2019-05-31 09:17 (10.0.2.2) root pts/1 2019-05-31 16:47 (10.0.2.31) root pts/2 2019-05-31 16:50 (10.0.2.30)
Using this command we also get similar information as from last command. Now you get the user details used for connecting to node3 from source host, also we have terminal information on which the session is still active.
4. Using w command
w displays information about the users currently on the machine, and their processes. This gives more information than who and last command and also serves our purpose to get the list of active SSH connections. Additionally it also gives us the information of the running process on those sessions.
Using w command you will also get the idle time details, i.e. for how long the session is idle. If the SSH session is idle for long period then it is a security breach and it is recommended that such idle SSH session must be killed, you can configure your Linux host to automatically kill such idle SSH session.
[root@node3 ~]# w 17:01:41 up 7:44, 3 users, load average: 0.00, 0.01, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT root pts/0 10.0.2.2 09:17 9:41 0.31s 0.00s less -s deepak pts/1 10.0.2.31 16:58 3:06 0.03s 0.03s -bash root pts/2 10.0.2.30 16:50 5.00s 0.07s 0.02s w
5. Using netstat command
Similar to ss we have netstat command to show active ssh sessions. Actually we can also say that ss is the new version of netstat. Here we can see all the ESTABLISHED SSH sessions from remote hosts to our localhost node3. it is also possible that one or some of these active ssh connections are in hung state so you can configure your host to automatically disconnect or kill these hung or unresponsive ssh sessions in Linux.
[root@node3 ~]# netstat -tnpa | grep 'ESTABLISHED.*sshd' tcp 0 0 10.0.2.32:22 10.0.2.31:37806 ESTABLISHED 10295/sshd: deepak tcp 0 0 10.0.2.32:22 10.0.2.2:49966 ESTABLISHED 4329/sshd: root@pts tcp 0 0 10.0.2.32:22 10.0.2.30:56088 ESTABLISHED 10125/sshd: root@pt
6. Using ps command
Now to show active ssh sessions, ps command may not give you accurate results like other commands we discussed in this article but it can give you some more additional information i.e. PID of the SSHD process which are currently active and connected.
# ps auxwww | grep sshd: | grep -v grep root 4329 0.0 0.1 154648 5512 ? Ss 09:17 0:00 sshd: root@pts/0 root 10125 0.0 0.1 154648 5532 ? Ss 16:50 0:00 sshd: root@pts/2 root 10295 0.0 0.1 154648 5480 ? Ss 16:58 0:00 sshd: deepak [priv] deepak 10301 0.0 0.0 156732 2964 ? S 16:58 0:00 sshd: deepak@pts/1
Check ssh connection history
To get the ssh connection history you can always check your SSHD logs for more information on connected or disconnected SSH session. Now the sshd log file may vary from distribution to distribution. On my RHEL 7.4 my sshd logs are stored inside /var/log/sshd
Lastly I hope the steps from the article to check active SSH connections and ssh connection history in Linux was helpful. So, let me know your suggestions and feedback using the comment section.
Didn’t find what you were looking for? Perform a quick search across GoLinuxCloud
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can either use the comments section or contact me form.
Thank You for your support!!
Просмотр истории входа в Linux. Кто и когда входил в систему
Данная информация обычно нужна системным администраторам для просмотра истории входа в систему на многопользовательском сервере.
Помимо этого, бывает полезно узнать о неудачных попытках входа. Это могут быть боты, но могут быть и попытки взлома вашего сервера.
Где хранятся логи входа в систему
Информация о том, кто входил (залогинивался) или пытался войти в систему, хранится в лог файлах. Для этого используется три лог-файла:
/var/log/btmp — неудачные попытки входа.
/var/run/utmp — кто в данный момент залогинен (текущие сессии).
/var/log/wtmp — список всех сессий входа в систему.
Эти файлы, в отличии от большинства других лог-файлов Linux, имеют бинарный формат. Если вы попробуете просмотреть их командой cat , то на экран будет выведена «каша». Для их просмотра используется команда last .
Просмотр истории входа в систему
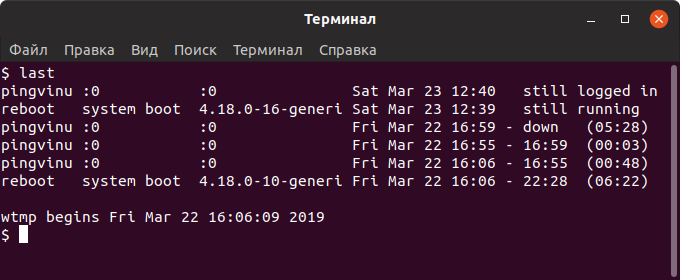
Для просмотра логов входа в систему используется команда last . По умолчанию команда last выводит информацию из файла /var/log/wtmp , в котором хранятся записи обо всех сессиях входа.
yuriy pts/0 181.23.456.189 Sat Mar 23 12:27 still logged in nifnif pts/11 181.45.678.912 Wed Mar 20 05:30 - 05:49 (00:19) nafnaf pts/22 181.45.678.312 Fri Mar 15 00:01 - 02:27 (02:26) nufnuf pts/33 181.45.678.411 Wed Mar 13 11:02 - 11:28 (00:26) . Как вы можете видеть, выводится таблица с информацией. В ней содержатся имена пользователей, IP-адрес, с которого осуществлялся вход, дата и время входа и продолжительность сессии. Запись вида pts/0 означает, что для входа использовалось SSH соединение (или другое удаленное соединение, например, telnet).
Также выводится информация о включении/выключении системы.
Последняя строка в файле /var/log/wtmp показывает, когда был создан файл.
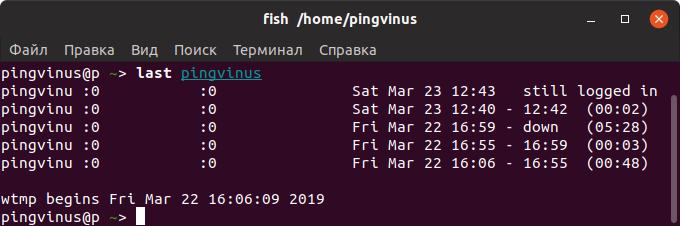
Просмотр истории входа для определенного пользователя
Чтобы показать информацию о сессиях определенного пользователя, то для команды last необходимо указать имя этого пользователя:
Ограничить количество строк
Иногда лог, который выводит команда last , может быть очень большой. Чтобы ограничить количество выводимых строк, используется опция -n ЧислоСтрок или просто -ЧислоСтрок .
Выведем только десять свежих записей:
Просмотр неудачных попыток входа в систему
Как было сказано выше, записи о неудачных попытках входа в систему хранятся в лог-файле /var/log/btmp .
Команда last по умолчанию выводит информацию из файла /var/log/wtmp . Чтобы вывести информацию из другого файла, используется опция -f ИмяФайла
Выведем записи о неудачных попытках входа (из файла /var/log/btmp ):
Или же можно воспользоваться командой lastb . Команда lastb работает точно также, как и команда last , но выводит информацию из файла /var/log/btmp
Заключение
Мы рассмотрели использование команды last для просмотра информации об истории входа в систему.
Дополнительную информацию по использованию команды last можно получить, выполнив в терминале: