- Troubleshoot Kerberos Authentication on Linux
- Troubleshooting Linux Kerberos System Setup and Monitoring Problems
- Troubleshooting Linux Kerberos Client Utility Issues
- Method 1: Using the Klist Command
- Method 2: Using Kinit Command to Check for Issues on KDC Client
- Method 3: Using kinit Command to Check SMP Problems
- Method 4: Using the ktpass Command
- Troubleshooting KDC Support Issues
- Troubleshooting Keytab Issues
- About the author
- Kennedy Brian
- How to Troubleshoot Kerberos Authentication on Linux
- Introduction to Kerberos
- How to Troubleshoot Kerberos Authentication on Linux
- Installation of protocols on both machines
- Timings are the same on both machines
- Check domain name service (DNS) entries on both machines
- Troubleshooting client utility issues of Kerberos
- Try the klist command to visualize tickets
- Try kinit command for checking KDC client issues
- Use kinit command to check the SMP problems
- Try ktpass command
- Troubleshooting KDC support issues
- Troubleshooting the keytab issues
Troubleshoot Kerberos Authentication on Linux
Like many other authentication protocols, you may often face problems configuring Linux to authenticate with Kerberos. Of course, issues always vary depending on your stage of authentication.
This article addresses some of the issues you may find. Some of the issues that we include here are:
- Issues arising from system setup
- Issues arising from client utilities and failure to use or manage the Kerberos environment
- KDC encryption issues
- Keytab problems
Troubleshooting Linux Kerberos System Setup and Monitoring Problems
Notably, the problems you may face with Linux Kerberos often begin from the setup stage. And the only way you can minimize setup and monitoring issues is by following these steps:
Step 1: Ensure you have a functional Kerberos protocol correctly installed in both machines.
Step 2: Synchronize the time on both machines to ensure that they run on a similar time frame. Notably, use the network time synchronization (NTS) to ensure that the machines are within 5 minutes of each other.
Step 3: Check if all hosts in the domain network service (DNS) have the correct entries. While at that, ensure that each entry in the host file has relevant IP addresses, host names, and fully-qualified domain names (FQDN). A good entry should look like this:
Troubleshooting Linux Kerberos Client Utility Issues
If you are finding it difficult to manage client utilities, you can always use the following three methods to solve the issues:
Method 1: Using the Klist Command
The Klist command will help you visualize all tickets in any credentials cache or the keys in the key tab file. Once you have the tickets, you can forward the details to complete the authentication process. A Klist output for troubleshooting client utilities will look like this:
Method 2: Using Kinit Command to Check for Issues on KDC Client
You can also use the Kinit command to confirm if you have any issues with your KDC host and KDC client. The Kinit utility will help you obtain and cache a ticket-granting ticket for the service principal and the user. Client utility problems could always result from a wrong principal name or a wrong user name.
Below is the Kinit syntax for the user principal:
The above command will prompt for a password as it creates a user principal. When running the command, ensure that you replace the username with a valid entry from your directory.
On the other hand, the Kinit syntax for service principal is similar to the details in the below screenshot. Note that this can vary from one host to another:
Interestingly, the Kinit command for the service principal will not prompt any passwords since it uses the bracketed key tab file to authenticate the service principal.
Method 3: Using kinit Command to Check SMP Problems
You can also run the below command irrespective of whether the above kit command worked or not. It helps to determine if there are any issues with the SMP host. Notably, this is more useable when testing your sever on mail.company.com.
Your kinit command will take the below structure:
Method 4: Using the ktpass Command
Sometimes the problem could be a problem with your passwords. To ascertain that this is not the cause of your Linux Kerberos issues, you can verify your ktpass utility version.
Troubleshooting KDC Support Issues
Kerberos can often fail due to an array of issues. But sometimes, the issues could result from KDC encryption support. Notably, such a problem will bring the message below:
Do the following in case you receive the above message:
- Verify if your KDC settings block or restrict any encryption types
- Confirm if your server account has all the encryption types checked.
Troubleshooting Keytab Issues
You can take the following steps if you encounter any key tab issues:
Step 1: Verify that both the location and name of the key tab file for the host are similar to the details in krb5.conf file.
Step 2: Verify if the host and client servers have principal names.
Step 3: Confirm the encryption type before creating a key tab file.
Step 4: Verify the validity of the key tab file by running the below kinit command;
The above command should return no error if you have a valid key tab file. But in case of an error, you can verify the validity of the SPN using this command:
The above utility will prompt you to key in your password. Failure to ask for a password implies that your SPN is invalid or unidentifiable. Once you key in a valid password, the command will not return any error.
The above are some common problems you might encounter when configuring or authenticating with Linux Kerberos. This write-up also contains the possible solutions for each of the issues you might face.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.
How to Troubleshoot Kerberos Authentication on Linux
Understanding how to troubleshoot Kerberos Authentication on Linux is essential to keeping your system secure. Here’s everything you need to know about it.
Authentication is a fundamental security objective in any communication system, and several protocols are available in Linux to address the authentication problem. Amongst these protocols, Kerberos is one such that’s widely used.
In this article, we will discuss the various issues that arise during the use of Kerberos, and we will also discuss the steps for troubleshooting these problems in Linux.
Introduction to Kerberos
Kerberos is a three-phased authentication protocol for client-server applications using cryptographic techniques. It was developed by MIT in 1988 to protect network services provided by Project Athena. The client can authenticate using this protocol over an insecure network. After a client is authenticated, further messages are to ensure integrity and privacy.
We will now proceed towards the discussions on various problems related to Kerberos authentication in Linux and also provide the steps for troubleshooting. These problems relate to setup and monitoring, client utility management, KDC support, and keytab issues.
How to Troubleshoot Kerberos Authentication on Linux
These are the initial problems associated with setup and monitoring. Following are the few steps that you may employ to address these problems.
Installation of protocols on both machines
To work correctly, a functional Kerberos protocol must be installed on both machines. Please make sure this requirement is met before proceeding to steps ahead.
Timings are the same on both machines
The Kerberos authentication may fail because of clock skew errors. Make sure that the timings on both machines are the same, i.e., the policy server clock and KDC system clock are synchronized. For this purpose, you can use network time synchronization (NTS) such that both machines are within 5 minutes of each other.
Check domain name service (DNS) entries on both machines
Make sure that the DNS entries are the same on both machines. To be precise, ensure that each entry in the host file has the relevant internet protocol (IP) address, hostname, and fully qualified domain name (FQDN). Alternatively, access should have been provided in the /etc/hosts file. A good entry should look like the following:
Note: The order of the DNS entries provided matters if you want the operating system to try each of those nameservers in sequence to find a given domain. Also, multiple entries should be separated by spaces.
Troubleshooting client utility issues of Kerberos
On topics related to managing client utility, the following methods may be tried out.
Try the klist command to visualize tickets
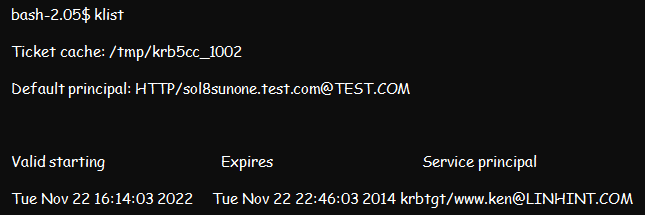
The klist can be used to list down the information of the keytab file. It is an essential command that can also visualize all the tickets in any credentials’ cache or the keys in the key tab file. After having the ticket, the details can be forwarded to complete the authentication process. Following is the sample output of klist :
bash-2.05$ list
Ticket cache: /tmp/krb5cc_1002
Default principal: HTTP/[email protected]
Valid starting Expires Service principal
Mon Dec 12 15:00:03 2022 Mon Dec 12 21:40:03 2012 krbtgt/[email protected]
Kinit
Try kinit command for checking KDC client issues
This command can be used to verify if there are any issues with the KDC host and client. The utility can be used to get and cache a ticket-granting ticket for the service principal and the user. It is possible that the client utility issue arises from the wrong principal name or the wrong user. Following is the kinit syntax for the user principal:
When you run the above command, it will prompt you for the password before creating a user principal. While using the kinit command, ensure you provide the user name with a valid entry from the directory.
Now, we will see the use of kinit command for the service principal. Following is the syntax for this command:
kinit –k [-t keytab_file] principal_name
Note: The kinit command for the service principal will not ask for any password as the keytab file is provided, and this file will be used for authentication.
Use kinit command to check the SMP problems
After trying the above two steps, you can also use kinit command to determine if there are any issues related to the SMP host. For this purpose, the following command can be used:
kbd> kinit –S host/mail.company.com#SERVER01.COMPANY.COM
Try ktpass command
One of the possible reasons for issues can be the password problem. To make sure that the problem is not arising because of the password, you can use the ktpass utility version.
Troubleshooting KDC support issues
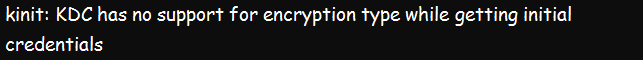
The Kerberos can cause issues because of KDC encryption support. The following error may arise in this case:
kinit: KDC has no support for encryption type while getting initial credentials.
In such as case, you may try following two steps to resolve the issues. Specifically, make sure that:
- The KDC settings are not blocking or restricting any encryption types
- All encryption types are checked in the server account
Troubleshooting the keytab issues
There may be issues arising because of keytab. In this case, the following steps may be taken:
- There are details related to location and name in krb5.conf file. Similar details should be provided in the key tab file
- The principal names have been provided for both client and servers
- Verify the encryption type before the creation of the tab file
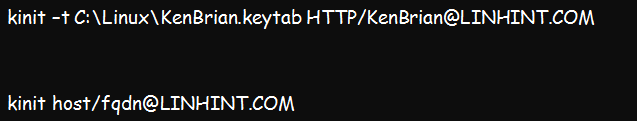
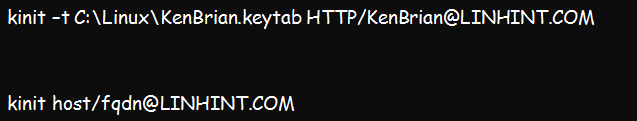
- Confirm the validity of the key tab file. This step can be performed using the following kinit command:
kinit –t khan.keytab HTTP/[email protected]
Kinit host/[email protected]
This command should run fine without any error if the key tab file is valid. If any error arises, verify the validity of SPN.
Finally, the following are some more suggestions:
- Install any packet tracer to visualize the tokens that are exchanged between the browser and web server
- It is recommended that logs are enabled for the policy server and web agent such that authentication error messages are recorded
- You should log off the workstation host after any change in the encryption type
- Finally, confirm the key version number (kvno). The version number of the service principal should match the value in keytab file
In this article, we have discussed the common issues that arise for Kerberos. The article discusses the steps for troubleshooting these problems.
If this guide helped you, please share it.
Husain is a staff writer at Distroid and has been writing on all things Linux and cybersecurity for over 10 years. He previously worked as a technical writer for wikiHow. In his past time, he loves taking tech apart and see what makes them tick, without necessarily putting it all back together. LinkedIn
Leave a Reply
You must be logged in to post a comment.