- How to Check SSL Certificates Details with Open SSL in Linux?
- Check the full details of the certificate
- Show the SSL certificate itself (encoded):
- Verify if the Keys Match
- Check who issued the SSL certificate
- Check whom the SSL certificate is issued to
- Check the validity of the SSL certificate
- Display the all above info about the SSL certificate
- Final Words
- Save 10% on SSL Certificates when ordering today!
- Проверка SSL на валидность при помощи openssl
- How to Check Certificate with OpenSSL
- Optional: Generating a TLS/SSL Certificate
- Checking the Status of a Certificate
- Using OpenSSL to View the Status of a Website’s Certificate
- Verifying Information within a Certificate
- Verifying a .crt Type Certificate
- Checking a .csr (Certificate Signing Request) type file
- Verifying a KEY type file
- Working with .pem type Files
- Verifying a Public Key
- Conclusion
How to Check SSL Certificates Details with Open SSL in Linux?
SSL certificates are now a requirement for any website. If you don’t encrypt your site, browsers will flag it as not secure, leaving visitors with an annoying warning message. But even if you add an SSL certificate, managing it is tricky. An SSL error may pop up unexpectedly, causing you all sorts of trouble.
To avoid SSL outages, you should monitor your SSL certificate frequently and always replace it on time. And, with certs expiring in one year, this task can become quite a chore. Thankfully, there are SSL tools to help you manage your certificates, and not a single program does a better job than the versatile OpenSSL utility.
With OpenSSL, you can apply for your digital certificate (Generate the Certificate Signing Request) and install the SSL files on your server. You can also convert your certificate into various SSL formats, as well as do all kinds of verifications. In this article, we’ll show you how to verify SSL certificate details using OpenSSL in Linux.
Most Linux systems will have OpenSSL pre-installed, but it’s better to ensure you have the latest running version. You can check your OpenSSL version by running the following command:
Certificate files in Linux are located by default in the /etc/pki/tls/certs folder or sometimes within an application-specific folder such as /etc/httpd for Apache. These generally use .pem or .crt extensions and will likely be named yourdomain.pem or yourdomain.crt, but sometimes the generic “server” file name is used as well. If you’ve applied for the SSL certificate and installed it on the server, you should already know its location and file names.
Check the full details of the certificate
OpenSSL provides a rich variety of commands to generate, install, and manage certificates. To check the details of a particular certificate, run the following command:
openssl x509 -in (path to certificate and certificate filename) -text -noout
Here’s what you should see:
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=DigiCert, Inc, CN=DigiCert SHA2
Not Before: Jun 31 23:32:14 2021 GMT
Not After : Jun 31 23:32:14 2022 GMT
Subject: C=US, ST=CA, L=Sacramento, O=Yourplc, OU=IT, CN=yourplc.com
Public Key Algorithm: rsaEncryption
Show the SSL certificate itself (encoded):
$ echo | openssl s_client -servername howtouselinux.com -connect yourplc.com:443 2>/dev/null | openssl x509
Verify if the Keys Match
To verify the public and private keys match, you need to extract the public key from each file and generate a hash output for it. All three files should share the same public key and the same hash value.
Use the following commands to generate a hash of each file’s public key:
openssl pkey -pubout -in privateKey.key | openssl sha256
openssl req -pubkey -in CSR.csr -noout | openssl sha256
openssl x509 -pubkey -in certificate.crt -noout | openssl sha256
Check who issued the SSL certificate
$ echo | openssl s_client -servername yourplc.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -issuer
issuer= /C=US/DigiCert Inc/CN=DigiCert SHA2
Check whom the SSL certificate is issued to
$ echo | openssl s_client -servername .com -connect howtoyourplcuselinux.com:443 2>/dev/null | openssl x509 -noout -subject
Check the validity of the SSL certificate
$ echo | openssl s_client -servername howtouselinux.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -dates
notBefore=Jun 31 23:32:14 2021 GMT
notAfter=Jun 31 23:32:14 2022 GMT
Display the all above info about the SSL certificate
$ echo | openssl s_client -servername howtouselinux.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -issuer -subject -dates
echo | openssl s_client -servername yourplc.com -connect yourplc.com:443 2>/dev/null | openssl x509 -noout -issuer -subject -dates
issuer= /C=US/O=DigiCert Inc/CN=DigiCert SHA2
notBefore=Jun 31 23:32:14 2021 GMT
notAfter=Jun 31 23:32:14 2022 GMT
Final Words
If something goes wrong with your SSL connection, verifying your certificate’s details is the first step towards finding the culprit. In OpenSSL, you have a great utility to perform all kinds of checks, from inspecting the certificate issuer to analyzing technical data and seeing when the certificate expires. OpenSSL integrates with Linux and provides control over SSL installation via its flexible command lines.
Save 10% on SSL Certificates when ordering today!
Fast issuance, strong encryption, 99.99% browser trust, dedicated support, and 25-day money-back guarantee. Coupon code: SAVE10
Проверка SSL на валидность при помощи openssl
Частенько приходится устанавливать сертификаты и бывают не соответствия, что бы убедится что сертификаты валидны есть openssl который в этом нам поможет.
Проверка pem,crt — сертификата вместе с цепочкой(если у вас несколько файлов, объедините в один, сначала идет сертификат потом цепочка)
openssl x509 -noout -modulus -in server.crt | openssl md5
openssl rsa -noout -modulus -in server.key | openssl md5
openssl req -noout -modulus -in request.csr | openssl md5
MD5 у всех должен совпадать — но для работоспособности должны быть одинаковы только у приватного ключа и сертификата, csr вам может пригодится если вы соберетесь продлевать данный сертификат.
Данная команда покажет информацию о сертификате
openssl x509 -in certificate.crt -text -noout
openssl rsa -in server.key -check
openssl s_client -connect clsv.ru:443
openssl s_client -proxy 192.168.103.115:3128 -connect clsv.ru:443
openssl req -x509 -nodes -newkey rsa:2048 -days 365 -keyout ./key.pem -out cert.pem -subj /C=/ST=/L=/O=/CN=clsv.ru
И в каталоге у вас появится Ключ — key.pem и Сертификат cert.pem и теперь можно их использовать для шифрования трафика вашего сервиса.
Сделать PFX сертификат из имеющихся
openssl pkcs12 -export -out domain.name.pfx -inkey domain.name.key -in domain.name.crt
How to Check Certificate with OpenSSL
Learn how to use the openssl command to check various kinds of certificates on Linux systems.
Keeping a tab on your SSL certificates is a crucial part of a sysadmin’s job.
There are various ways to do it. You can use a monitoring service like Checkmk to monitor the certificates or you can use the good old openssl command for this purpose.
In this guide, I’ll explain to you how to use the openssl command to check various certificates on Linux systems.
Optional: Generating a TLS/SSL Certificate
To demonstrate this guide, I’ll create some keys and certificate files. If you already have these things, you can skip to the next step.
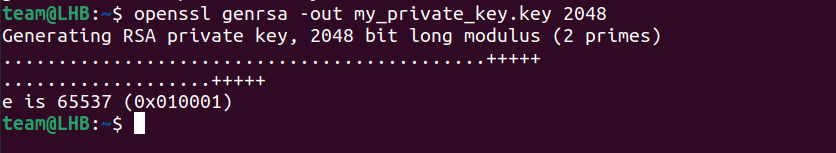
Let’s begin with a private key, use the following command to create a private key:
openssl genrsa -out my_private_key.key 2048The above command will create a key with the name my_private_key.key file.
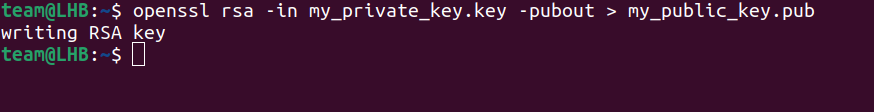
Now that you have a private key, create a public key with it:
openssl rsa -in my_private_key.key -pubout > my_public_key.pubThat’s good, you now have your private and public keys and you can use them to generate a certificate file. It is important to know beforehand that you are generating a self-signed certificate here. This is because using a CA (Certificate Authority) for signing a certificate requires additional costs.
But don’t worry. Your certificate will suffice as you will use it only for demonstration purposes. Use the below command to build your certificate:
openssl req -x509 -new -key my_private_key.key -days 365 -out mycert.pemThe above command will result in a PEM-type certificate file with the name mycert.pem.
Each option here has its meaning. The 365 indicates the period in days for which the certificate will be valid.
Now enter the details for various questions on the prompt:
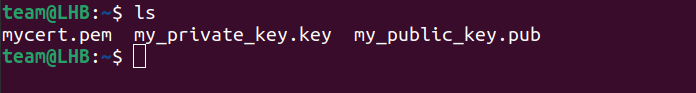
Country Name (2 letter code) [AU]:IN State or Province Name (full name) [Some-State]: [Name of your state] Locality Name (eg, city) []: [Name of your city] Organization Name (eg, company) [Internet Widgits Pty Ltd]: [Name of your organization] Organizational Unit Name (eg, section) []: Common Name (e.g. server FQDN or YOUR name) []:[Enter a common name here]You can now see all your files listed in the current directory with the ls command:
Checking the Status of a Certificate
It is very important to ensure the SSL certificates you are using are not expired or on the verge of being expired. Negligence in this regard can have a devastating impact on the production systems.
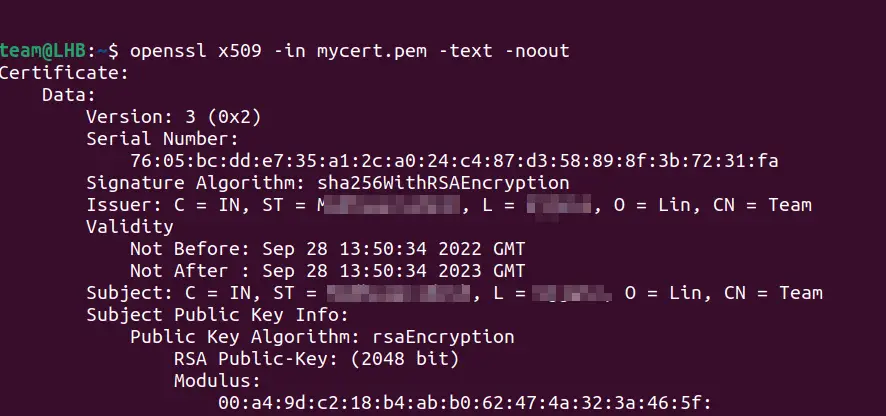
Certificate files usually have a .pem or .crt extension. You can use the openssl commands to explore the details of a certificate. For example, the below command gives the details of the certificate you created above:
openssl x509 -in mycert.pem -text -nooutYou will see a long output printed on your terminal describing various attributes of the certificate as: Version, Serial Number, Signature Algorithm, Issuer, Validity Status, etc.
Similarly, you can use this command with a port with an SSL certificate attached to it. I guess you will have figured out the validity range of our certificate from the above output.
Always use this command when you plan to replace or renew your SSL certificate. This way you are likely to avoid any mistakes in certificate management.
Using OpenSSL to View the Status of a Website’s Certificate
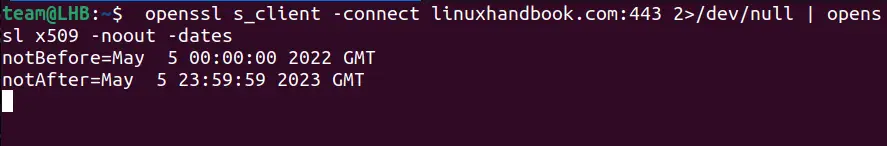
Let me show you how you can use openssl command to verify and check SSL certificate validity for this website www.linuxhandbook.com or a remote system with a fully qualified domain name (FQDN):
openssl s_client -connect linuxhandbook.com:443 2>/dev/null | openssl x509 -noout -datesAs you can see from the output, the target certificate is valid only for the specified range: May 5, 2022 to May 5, 2023.
Let’s break down this command:
- s_client: This command implements a general SSL/TLS-based client and establishes an SSL/TLS connection to a remote system.
- -connect host:port: Here, you specify the host and port number to connect to.
- x509: This command has multiple uses like showing certificate-related information, converting certificates to various other forms, signing certificate requests, etc.
Verifying Information within a Certificate
CER and CRT type files can be used in parallel as both are identical. The openssl command can also be used to verify a Certificate and CSR(Certificate Signing Request).
Verifying a .crt Type Certificate
For verifying a crt type certificate and to get the details about signing authority, expiration date, etc., use the command:
openssl x509 -in certificate.crt -text -nooutChecking a .csr (Certificate Signing Request) type file
You can use the below command to check a csr type file and retrieve the CSR data entered while creating this file:
openssl req -text -noout -verify -in server.csrVerifying a KEY type file
This is an extra tip for verifying a KEY type file and its consistency:
openssl rsa -in my_private_key.key -checkWorking with .pem type Files
In a mega IT setup, you may find thousands of servers out there. They only accept certificates that are formatted in a particular manner. This means if you are using a .pem format for a server that needs .crt format, then you are at a complete loss until you convert them to the desired format.
Technically, there are some commands that you can use to convert certificates and keys to other formats. In this way, you can make them work with different types of formats required by various servers. For e.g., you can convert a DER file (.cer, .crt or .der) to PEM format as:
openssl x509 -inform der -in base-certificate.cer -out target-certificate.pemTo find the expiration date of a .pem type TLS/SSL certificate, the following command is very handy:
openssl x509 -enddate -noout -in /path/of/the/pem/fileVerifying a Public Key
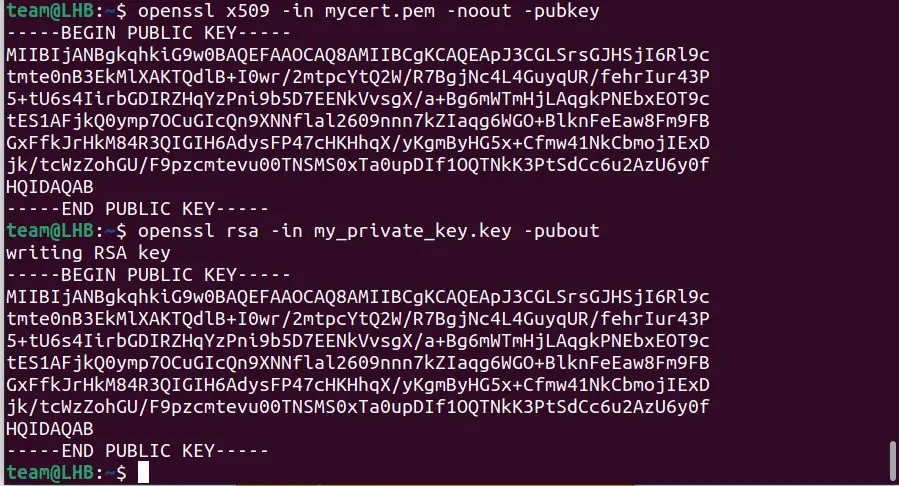
The public key contained in a private key and a certificate must be the same. You can check this with the openssl command as:
openssl x509 -in certificate.pem -noout -pubkeyopenssl rsa -in ssl.key -puboutAs you can see, the outputs from the above commands are the same.
Conclusion
You have so far seen how to generate keys and certificates, how to change one form to another, and how to verify different types of files.
Keeping knowledge of your certificate status is very important and OpenSSL does a good job here. Also, if you do not want to engage (or mess up) with the command line, you can use downtime monitoring services like Better Uptime to automatically check the certificates.