22.4. Configuring a Samba Server
The default configuration file ( /etc/samba/smb.conf ) allows users to view their home directories as a Samba share. It also shares all printers configured for the system as Samba shared printers. In other words, you can attach a printer to the system and print to it from the Windows machines on your network.
22.4.1. Graphical Configuration
To configure Samba using a graphical interface, use the Samba Server Configuration Tool . For command line configuration, skip to Section 22.4.2, “Command Line Configuration”.
The Samba Server Configuration Tool is a graphical interface for managing Samba shares, users, and basic server settings. It modifies the configuration files in the /etc/samba/ directory. Any changes to these files not made using the application are preserved.
To use this application, you must be running the X Window System, have root privileges, and have the system-config-samba RPM package installed. To start the Samba Server Configuration Tool from the desktop, go to the System (on the Panel) > Administration > Server Settings > Samba or type the command system-config-samba at a shell prompt (for example, in an XTerm or a GNOME terminal).
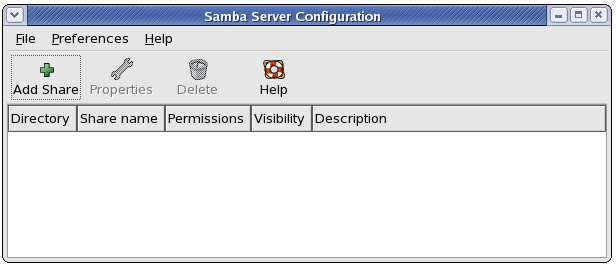
Figure 22.3. Samba Server Configuration Tool
The Samba Server Configuration Tool does not display shared printers or the default stanza that allows users to view their own home directories on the Samba server.
22.4.1.1. Configuring Server Settings
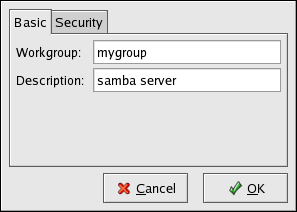
The first step in configuring a Samba server is to configure the basic settings for the server and a few security options. After starting the application, select Preferences > Server Settings from the pulldown menu. The Basic tab is displayed as shown in Figure 22.4, “Configuring Basic Server Settings”.
Figure 22.4. Configuring Basic Server Settings
On the Basic tab, specify which workgroup the computer should be in as well as a brief description of the computer. They correspond to the workgroup and server string options in smb.conf .
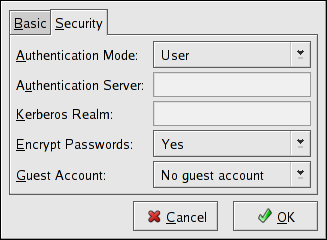
Figure 22.5. Configuring Security Server Settings
Authentication Mode — This corresponds to the security option. Select one of the following types of authentication.
ADS — The Samba server acts as a domain member in an Active Directory Domain (ADS) realm. For this option, Kerberos must be installed and configured on the server, and Samba must become a member of the ADS realm using the net utility, which is part of the samba-client package. Refer to the net man page for details. This option does not configure Samba to be an ADS Controller. Specify the realm of the Kerberos server in the Kerberos Realm field.
The Kerberos Realm field must be supplied in all uppercase letters, such as EXAMPLE.COM .
Using a Samba server as a domain member in an ADS realm assumes proper configuration of Kerberos, including the /etc/krb5.conf file.
Domain — The Samba server relies on a Windows NT Primary or Backup Domain Controller to verify the user. The server passes the username and password to the Controller and waits for it to return. Specify the NetBIOS name of the Primary or Backup Domain Controller in the Authentication Server field.
The Encrypted Passwords option must be set to Yes if this is selected.
Server — The Samba server tries to verify the username and password combination by passing them to another Samba server. If it can not, the server tries to verify using the user authentication mode. Specify the NetBIOS name of the other Samba server in the Authentication Server field.
Share — Samba users do not have to enter a username and password combination on a per Samba server basis. They are not prompted for a username and password until they try to connect to a specific shared directory from a Samba server.
User — (Default) Samba users must provide a valid username and password on a per Samba server basis. Select this option if you want the Windows Username option to work. Refer to Section 22.4.1.2, “Managing Samba Users” for details.
Encrypt Passwords — This option must be enabled if the clients are connecting from a system with Windows 98, Windows NT 4.0 with Service Pack 3, or other more recent versions of Microsoft Windows. The passwords are transferred between the server and the client in an encrypted format instead of as a plain-text word that can be intercepted. This corresponds to the encrypted passwords option. Refer to Section 22.4.3, “Encrypted Passwords” for more information about encrypted Samba passwords.
Guest Account — When users or guest users log into a Samba server, they must be mapped to a valid user on the server. Select one of the existing usernames on the system to be the guest Samba account. When guests log in to the Samba server, they have the same privileges as this user. This corresponds to the guest account option.
After clicking OK , the changes are written to the configuration file and the daemon is restarted; thus, the changes take effect immediately.
22.4.1.2. Managing Samba Users
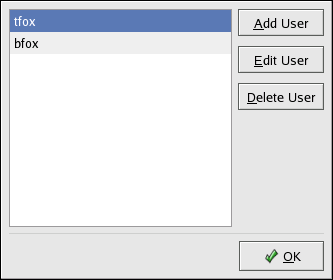
The Samba Server Configuration Tool requires that an existing user account be active on the system acting as the Samba server before a Samba user can be added. The Samba user is associated with the existing user account.
Figure 22.6. Managing Samba Users
To add a Samba user, select Preferences > Samba Users from the pulldown menu, and click the Add User button. In the Create New Samba User window select a Unix Username from the list of existing users on the local system.
If the user has a different username on a Windows machine and needs to log into the Samba server from the Windows machine, specify that Windows username in the Windows Username field. The Authentication Mode on the Security tab of the Server Settings preferences must be set to User for this option to work.
Also, configure a Samba Password for the Samba User and confirm it by typing it again. Even if you opt to use encrypted passwords for Samba, it is recommended that the Samba passwords for all users are different from their system passwords.
To edit an existing user, select the user from the list, and click Edit User . To delete an existing Samba user, select the user, and click the Delete User button. Deleting a Samba user does not delete the associated system user account.
Getting started with Samba for interoperability
The Samba suite helps you to easily share files between Linux and Windows systems. This first article of two teaches you how and where to begin with interoperability.
File shares are important for collaboration in any network. In this series of articles, I will show you how Samba can help you set up and serve file shares on Linux servers that are accessible from both Linux and Windows clients.
Before we dive in and set up file shares, let’s cover what Samba is and what it can do for you.
Great Linux resources
Samba is a suite of applications that implements the Server Message Block (SMB) protocol. Many operating systems, including Microsoft Windows, use the SMB protocol for client-server networking. Samba enables Linux / Unix machines to communicate with Windows machines in a network.
Samba is open source software. Originally, Samba was developed in 1991 for fast and secure file and print share for all clients using the SMB protocol. Since then it has evolved and added more capabilities. Today Samba provides a suite of applications enabling seamless networking and interoperability between *nix and Windows.
Install the Samba packages
In this example, I’m using CentOS 8 with the hostname centos as my Samba server with an IP address of 192.168.1.122. The only package you will need to install is Samba, but I would like to include other client tools like samba-common and samba-client to test out our shares later.
# yum install samba samba-client samba-common -yCreate a directory to share and set its permissions
Once you’ve installed the required packages on the server, let’s create a directory and provide the required permissions on the directory. Create a directory called share on our root directory. You can name this directory anything you want to, and give it read, write and execute permissions. In this example, we will rely on the Samba configuration to control read, write access to the shared directory.
# mkdir /share # chmod -R 777 /shareNow that we have installed necessary packages, it’s time to configure the shared directory. The configuration file is located under /etc/samba . Using your favorite text editor, append the following to /etc/samba/smb.conf . Leave the rest of the configuration file as is and this should be good for our setup.
# vim /etc/samba/smb.conf [myshare] comment = My share path = /share read only = NoI have created a share called myshare and provided a path to the share, which in our case is located at /share . I then gave it read/write permissions with read only = No . There are many other configuration parameters that you may pass here, but for our setup these settings are good.
Check the Samba configuration
Samba provides a tool to check our configuration file. We can check if our configuration file has any errors by using the testparm command.
Next, we need to create a Samba user account, so that Samba can communicate in Samba sessions with shares. The smbpasswd command has several functions depending on if you run the command as root or as a standard user. If you issue smbpasswd without any arguments as a non-root user, by default smbpasswd will change the current logged in user’s Samba password. When you run smbpasswd command as root , you will be able to create new Samba accounts. You can create a Samba account only for existing Linux user accounts.
# smbpasswd -a user New SMB password: Retype new SMB password:We need to configure SELinux on the /share directory so the Samba service has proper permissions.
# semanage fcontext -a -t samba_share_t "/share(/.*)?" # restorecon -R -v /shareNext, we need to enable and start the smb and nmb services.
# systemctl enable smb # systemctl start smb #systemctl enable nmb #systemctl start nmbIf you have firewalld running on your server, we need to configure it to allow Samba traffic. You can do so by using the firewall-cmd command. Don’t forget to make those changes permanent and reload firewalld .
Now we have our services enabled and started. We can check to see if the share is available from the server by using the smbclient tool. This is the reason I have installed the Samba client tools on the local machine. The command uses the following syntax:
# smbclient -U user -L 192.168.1.122 Enter SAMBA\user's password:Let’s check if we can access the share by issuing the following command on the server:
# smbclient -U user //192.168.1.122/myshare Enter SAMBA\user's password: Try "help" to get a list of possible commands. smb: \>We have installed and configured the Samba file share service on our Linux server. We were able to access those shares on the local machine. In the next article, we will set up one Linux client and one Windows 10 client to access share we just created.
[ Want to learn more about Linux system administration? Take a Red Hat system administration course. ]