- Post-installation steps for Linux
- Manage Docker as a non-root user
- Configure Docker to start on boot
- Use a different storage engine
- Configure default logging driver
- Configure where the Docker daemon listens for connections
- Configuring remote access with systemd unit file
- Configure the daemon with systemd
- Custom Docker daemon options
- Manually create the systemd unit files
- Configure the Docker daemon to use a proxy server
- What is the Command Line Procedure to Restart Docker?
- What is the Command-Line Procedure to Restart Docker?
- How to Restart Docker Using Command Line on Windows?
- How to Restart Docker Using Command Line on Linux?
- How to Restart Docker Using Command Line on Mac?
- Conclusion
- About the author
- Laiba Younas
Post-installation steps for Linux
This section contains optional procedures for configuring Linux hosts to work better with Docker.
Manage Docker as a non-root user
The Docker daemon binds to a Unix socket instead of a TCP port. By default that Unix socket is owned by the user root and other users can only access it using sudo . The Docker daemon always runs as the root user.
If you don’t want to preface the docker command with sudo , create a Unix group called docker and add users to it. When the Docker daemon starts, it creates a Unix socket accessible by members of the docker group.
Warning
The docker group grants privileges equivalent to the root user. For details on how this impacts security in your system, see Docker Daemon Attack Surface.
To create the docker group and add your user:
$ sudo usermod -aG docker $USER This command downloads a test image and runs it in a container. When the container runs, it prints a message and exits. If you initially ran Docker CLI commands using sudo before adding your user to the docker group, you may see the following error, which indicates that your ~/.docker/ directory was created with incorrect permissions due to the sudo commands.
WARNING: Error loading config file: /home/user/.docker/config.json - stat /home/user/.docker/config.json: permission denied To fix this problem, either remove the ~/.docker/ directory (it is recreated automatically, but any custom settings are lost), or change its ownership and permissions using the following commands:
$ sudo chown "$USER":"$USER" /home/"$USER"/.docker -R $ sudo chmod g+rwx "$HOME/.docker" -R Configure Docker to start on boot
Most current Linux distributions (RHEL, CentOS, Fedora, Debian, Ubuntu 16.04 and higher) use systemd to manage which services start when the system boots. On Debian and Ubuntu, the Docker service is configured to start on boot by default. To automatically start Docker and Containerd on boot for other distros, use the commands below:
$ sudo systemctl enable docker.service $ sudo systemctl enable containerd.service To disable this behavior, use disable instead.
$ sudo systemctl disable docker.service $ sudo systemctl disable containerd.service If you need to add an HTTP Proxy, set a different directory or partition for the Docker runtime files, or make other customizations, see customize your systemd Docker daemon options.
Use a different storage engine
For information about the different storage engines, see Storage drivers. The default storage engine and the list of supported storage engines depend on your host’s Linux distribution and available kernel drivers.
Configure default logging driver
Docker provides the capability to collect and view log data from all containers running on a host via a series of logging drivers. The default logging driver, json-file , writes log data to JSON-formatted files on the host filesystem. Over time, these log files expand in size, leading to potential exhaustion of disk resources.
To alleviate such issues, either configure the json-file logging driver to enable log rotation, use an alternative logging driver such as the “local” logging driver that performs log rotation by default, or use a logging driver that sends logs to a remote logging aggregator.
Configure where the Docker daemon listens for connections
By default, the Docker daemon listens for connections on a UNIX socket to accept requests from local clients. It is possible to allow Docker to accept requests from remote hosts by configuring it to listen on an IP address and port as well as the UNIX socket. For more detailed information on this configuration option take a look at “Bind Docker to another host/port or a unix socket” section of the Docker CLI Reference article.
Secure your connection
Before configuring Docker to accept connections from remote hosts it is critically important that you understand the security implications of opening docker to the network. If steps are not taken to secure the connection, it is possible for remote non-root users to gain root access on the host. For more information on how to use TLS certificates to secure this connection, check this article on how to protect the Docker daemon socket.
Configuring Docker to accept remote connections can be done with the docker.service systemd unit file for Linux distributions using systemd, such as recent versions of RedHat, CentOS, Ubuntu and SLES, or with the daemon.json file which is recommended for Linux distributions that do not use systemd.
systemd vs daemon.json
Configuring Docker to listen for connections using both the systemd unit file and the daemon.json file causes a conflict that prevents Docker from starting.
Configuring remote access with systemd unit file
- Use the command sudo systemctl edit docker.service to open an override file for docker.service in a text editor.
- Add or modify the following lines, substituting your own values.
[Service] ExecStart= ExecStart=/usr/bin/dockerd -H fd:// -H tcp://127.0.0.1:2375 $ sudo systemctl daemon-reload Configure the daemon with systemd
This page describes how to customize daemon settings when using systemd.
Custom Docker daemon options
Most configuration options for the Docker daemon are set using the daemon.json configuration file. See Docker daemon configuration overview for more information.
Manually create the systemd unit files
When installing the binary without a package manager, you may want to integrate Docker with systemd. For this, install the two unit files ( service and socket ) from the github repository to /etc/systemd/system .
Configure the Docker daemon to use a proxy server
The Docker daemon uses the following environment variables in its start-up environment to configure HTTP or HTTPS proxy behavior:
- HTTP_PROXY
- http_proxy
- HTTPS_PROXY
- https_proxy
- NO_PROXY
- no_proxy
In Docker Engine version 23.0 and later versions, you may also configure proxy behavior for the daemon in the daemon.json file:
"proxies": "http-proxy": "http://proxy.example.com:3128", "https-proxy": "https://proxy.example.com:3129", "no-proxy": "*.test.example.com,.example.org,127.0.0.0/8" > > These configurations override the default docker.service systemd file.
If you are behind an HTTP or HTTPS proxy server, for example in corporate settings, the daemon proxy configurations must be specified in the systemd service file, not in the daemon.json file or using environment variables.
Note for rootless mode
The location of systemd configuration files are different when running Docker in rootless mode. When running in rootless mode, Docker is started as a user-mode systemd service, and uses files stored in each users’ home directory in ~/.config/systemd/user/docker.service.d/ . In addition, systemctl must be executed without sudo and with the —user flag. Select the “rootless mode” tab below if you are running Docker in rootless mode.
$ sudo mkdir -p /etc/systemd/system/docker.service.d [Service] Environment="HTTP_PROXY=http://proxy.example.com:3128" [Service] Environment="HTTPS_PROXY=https://proxy.example.com:3129" [Service] Environment="HTTP_PROXY=http://proxy.example.com:3128" Environment="HTTPS_PROXY=https://proxy.example.com:3129" Note Special characters in the proxy value, such as #?!()[]<> , must be double escaped using %% . For example:
[Service] Environment="HTTP_PROXY=http://domain%%5Cuser:complex%%23pass@proxy.example.com:3128/" - IP address prefix ( 1.2.3.4 )
- Domain name, or a special DNS label ( * )
- A domain name matches that name and all subdomains. A domain name with a leading “.” matches subdomains only. For example, given the domains foo.example.com and example.com :
- example.com matches example.com and foo.example.com , and
- .example.com matches only foo.example.com
[Service] Environment="HTTP_PROXY=http://proxy.example.com:3128" Environment="HTTPS_PROXY=https://proxy.example.com:3129" Environment="NO_PROXY=localhost,127.0.0.1,docker-registry.example.com,.corp"$ sudo systemctl daemon-reload $ sudo systemctl restart docker$ sudo systemctl show --property=Environment docker Environment=HTTP_PROXY=http://proxy.example.com:3128 HTTPS_PROXY=https://proxy.example.com:3129 NO_PROXY=localhost,127.0.0.1,docker-registry.example.com,.corp$ mkdir -p ~/.config/systemd/user/docker.service.d[Service] Environment="HTTP_PROXY=http://proxy.example.com:3128"[Service] Environment="HTTPS_PROXY=https://proxy.example.com:3129"[Service] Environment="HTTP_PROXY=http://proxy.example.com:3128" Environment="HTTPS_PROXY=https://proxy.example.com:3129"Note Special characters in the proxy value, such as #?!()[]<> , must be double escaped using %% . For example:
[Service] Environment="HTTP_PROXY=http://domain%%5Cuser:complex%%23pass@proxy.example.com:3128/"- IP address prefix ( 1.2.3.4 )
- Domain name, or a special DNS label ( * )
- A domain name matches that name and all subdomains. A domain name with a leading “.” matches subdomains only. For example, given the domains foo.example.com and example.com :
- example.com matches example.com and foo.example.com , and
- .example.com matches only foo.example.com
[Service] Environment="HTTP_PROXY=http://proxy.example.com:3128" Environment="HTTPS_PROXY=https://proxy.example.com:3129" Environment="NO_PROXY=localhost,127.0.0.1,docker-registry.example.com,.corp"$ systemctl --user daemon-reload $ systemctl --user restart docker$ systemctl --user show --property=Environment docker Environment=HTTP_PROXY=http://proxy.example.com:3128 HTTPS_PROXY=https://proxy.example.com:3129 NO_PROXY=localhost,127.0.0.1,docker-registry.example.com,.corpWhat is the Command Line Procedure to Restart Docker?
Docker is a software forum that permits developers to build, run, and share applications by utilizing containers. It offers tools and services to create and manage containers, as well as to store and share container images. Restarting Docker means stopping the Docker Daemon and then starting it again. The Docker daemon manages images, containers, volumes, and networks and it runs as a separate process on the host operating system.
This article will demonstrate the command line procedure to restart Docker on different operating systems.
What is the Command-Line Procedure to Restart Docker?
The procedure to restart Docker relies on the operating system. It can be done on various operating systems, such as:
How to Restart Docker Using Command Line on Windows?
To restart Docker using the command line on Windows, first, launch Windows PowerShell as an administrator. Then, stop the Docker Daemon using the “net stop docker” command and start it again via the “net start docker” command.
Follow the given-provided steps for a better understanding.
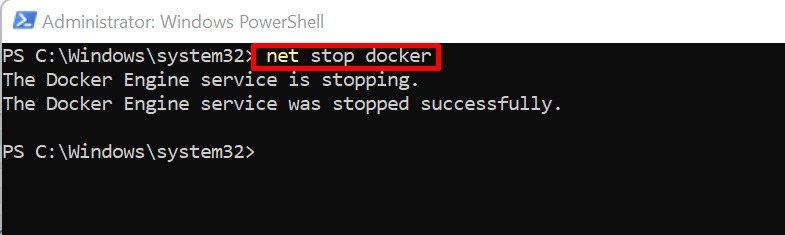
Step 1: Stop Docker Daemon
First, execute the provided command to stop the Docker Daemon:In the above, Docker has been stopped.
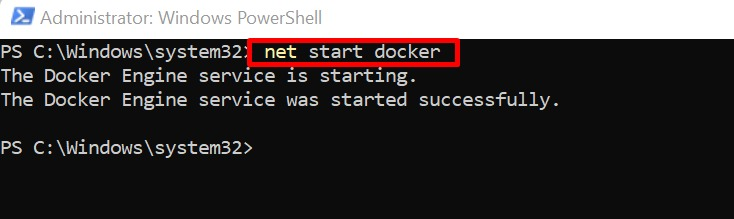
Step 2: Restart Docker Daemon
Then, start the Docker Daemon again with the help of the below-listed command:The above output indicates that Docker has been successfully restarted.
How to Restart Docker Using Command Line on Linux?
To restart Docker using the command line on Linux, first, launch the Ubuntu terminal as an administrator. Then, restart the Docker Daemon using the “sudo systemctl restart docker” command. Next, verify whether the Docker is running via the “sudo systemctl status docker” command.
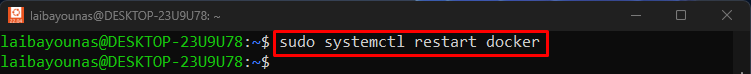
Step 1: Restart Docker Daemon
Run the given-provided command to restart the Docker Daemon on Linux OS:In this way, Docker has been restarted successfully.
Step 2: Verification
Then, ensure that the Docker is running by using the below-listed command:As you can see Docker has been restarted successfully.
How to Restart Docker Using Command Line on Mac?
To restart Docker using the command line on Mac, first, open the terminal window. Then, execute the “killall Docker && open /Applications/Docker.app” command:
This command first stops the Docker daemon and then starts the Docker application.
Conclusion
To restart Docker using the command line on Windows, first, stop the Docker Daemon using the “net stop docker” command and start it again via the “net start docker” command. For Linux OS, utilize the “sudo systemctl restart docker” command. Moreover, use the “killall Docker && open /Applications/Docker.app” command on Mac OS. This article has demonstrated the command line procedure to restart Docker on different operating systems.
About the author
Laiba Younas
I have done bachelors in Computer Science. Being passionate about learning new technologies, I am interested in exploring different programming languages and sharing my experience with the world.