Summary
Virtual Local Area Network (VLAN) is a Layer 2 method that allows multiple Virtual LANs on a single physical interface (ethernet, wireless, etc.), giving the ability to segregate LANs efficiently.
You can use MikroTik RouterOS (as well as Cisco IOS, Linux, and other router systems) to mark these packets as well as to accept and route marked ones.
As VLAN works on OSI Layer 2, it can be used just like any other network interface without any restrictions. VLAN successfully passes through regular Ethernet bridges.
You can also transport VLANs over wireless links and put multiple VLAN interfaces on a single wireless interface. Note that as VLAN is not a full tunnel protocol (i.e., it does not have additional fields to transport MAC addresses of sender and recipient), the same limitation applies to bridging over VLAN as to bridging plain wireless interfaces. In other words, while wireless clients may participate in VLANs put on wireless interfaces, it is not possible to have VLAN put on a wireless interface in station mode bridged with any other interface.
802.1Q
The most commonly used protocol for Virtual LANs (VLANs) is IEEE 802.1Q. It is a standardized encapsulation protocol that defines how to insert a four-byte VLAN identifier into the Ethernet header.
Each VLAN is treated as a separate subnet. It means that by default, a host in a specific VLAN cannot communicate with a host that is a member of another VLAN, although they are connected in the same switch. So if you want inter-VLAN communication you need a router. RouterOS supports up to 4095 VLAN interfaces, each with a unique VLAN ID, per interface. VLAN priorities may also be used and manipulated.
When the VLAN extends over more than one switch, the inter-switch link has to become a ‘trunk’, where packets are tagged to indicate which VLAN they belong to. A trunk carries the traffic of multiple VLANs; it is like a point-to-point link that carries tagged packets between switches or between a switch and router.
The IEEE 802.1Q standard has reserved VLAN IDs with special use cases, the following VLAN IDs should not be used in generic VLAN setups: 0, 1, 4095
Q-in-Q
Original 802.1Q allows only one VLAN header, Q-in-Q on the other hand allows two or more VLAN headers. In RouterOS, Q-in-Q can be configured by adding one VLAN interface over another. Example:
/interface vlan add name=vlan1 vlan-id=11 interface=ether1 add name=vlan2 vlan-id=12 interface=vlan1
If any packet is sent over the ‘vlan2′ interface, two VLAN tags will be added to the Ethernet header — ’11’ and ’12’.
Properties
- disabled — the interface will not use ARP
- enabled — the interface will use ARP
- local-proxy-arp — the router performs proxy ARP on the interface and sends replies to the same interface
- proxy-arp — the router performs proxy ARP on the interface and sends replies to other interfaces
- reply-only — the interface will only reply to requests originated from matching IP address/MAC address combinations which are entered as static entries in the IP/ARP table. No dynamic entries will be automatically stored in the IP/ARP table. Therefore for communications to be successful, a valid static entry must already exist.
MTU should be set to 1500 bytes same as on Ethernet interfaces. But this may not work with some Ethernet cards that do not support receiving/transmitting of full-size Ethernet packets with VLAN header added (1500 bytes data + 4 bytes VLAN header + 14 bytes Ethernet header). In this situation, MTU 1496 can be used, but note that this will cause packet fragmentation if larger packets have to be sent over the interface. At the same time remember that MTU 1496 may cause problems if path MTU discovery is not working properly between source and destination.
Setup examples
Layer2 VLAN examples
There are multiple possible configurations that you can use, but each configuration type is designed for a special set of devices since some configuration methods will give you the benefits of the built-in switch chip and gain larger throughput. Check the Basic VLAN switching guide to see which configuration to use for each type of device to gain maximum possible throughput and compatibility, the guide shows how to setup a very basic VLAN trunk/access port configuration.
There are some other ways to setup VLAN tagging or VLAN switching, but the recommended way is to use Bridge VLAN Filtering. Make sure you have not used any known Layer2 misconfigurations.
Layer3 VLAN examples
Simple VLAN routing
Let us assume that we have several MikroTik routers connected to a hub. Remember that a hub is an OSI physical layer device (if there is a hub between routers, then from the L3 point of view it is the same as an Ethernet cable connection between them). For simplification assume that all routers are connected to the hub using the ether1 interface and have assigned IP addresses as illustrated in the figure below. Then on each of them the VLAN interface is created.
Configuration for R2 and R4 is shown below:
[admin@MikroTik] /interface vlan> add name=VLAN2 vlan-id=2 interface=ether1 disabled=no [admin@MikroTik] /interface vlan> print Flags: X - disabled, R - running, S - slave # NAME MTU ARP VLAN-ID INTERFACE 0 R VLAN2 1500 enabled 2 ether1
[admin@MikroTik] /interface vlan> add name=VLAN2 vlan-id=2 interface=ether1 disabled=no [admin@MikroTik] /interface vlan> print Flags: X - disabled, R - running, S - slave # NAME MTU ARP VLAN-ID INTERFACE 0 R VLAN2 1500 enabled 2 ether1
The next step is to assign IP addresses to the VLAN interfaces.
[admin@MikroTik] ip address> add address=10.10.10.3/24 interface=VLAN2 [admin@MikroTik] ip address> print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK BROADCAST INTERFACE 0 10.0.1.4/24 10.0.1.0 10.0.1.255 ether1 1 10.20.0.1/24 10.20.0.0 10.20.0.255 pc1 2 10.10.10.3/24 10.10.10.0 10.10.10.255 vlan2 [admin@MikroTik] ip address>
[admin@MikroTik] ip address> add address=10.10.10.5/24 interface=VLAN2 [admin@MikroTik] ip address> print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK BROADCAST INTERFACE 0 10.0.1.5/24 10.0.1.0 10.0.1.255 ether1 1 10.30.0.1/24 10.30.0.0 10.30.0.255 pc2 2 10.10.10.5/24 10.10.10.0 10.10.10.255 vlan2 [admin@MikroTik] ip address>
At this point it should be possible to ping router R4 from router R2 and vice versa:
"Ping from R2 to R4:" [admin@MikroTik] ip address> /ping 10.10.10.5 10.10.10.5 64 byte ping: ttl=255 time=4 ms 10.10.10.5 64 byte ping: ttl=255 time=1 ms 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max = 1/2.5/4 ms "From R4 to R2:" [admin@MikroTik] ip address> /ping 10.10.10.3 10.10.10.3 64 byte ping: ttl=255 time=6 ms 10.10.10.3 64 byte ping: ttl=255 time=1 ms 2 packets transmitted, 2 packets received, 0% packet loss round-trip min/avg/max = 1/3.5/6 ms
To make sure if the VLAN setup is working properly, try to ping R1 from R2. If pings are timing out then VLANs are successfully isolated.
"From R2 to R1:" [admin@MikroTik] ip address> /ping 10.10.10.2 10.10.10.2 ping timeout 10.10.10.2 ping timeout 3 packets transmitted, 0 packets received, 100% packet loss
InterVLAN routing
If separate VLANs are implemented on a switch, then a router is required to provide communication between VLANs. A switch works at OSI layer 2 so it uses only Ethernet header to forward and does not check IP header. For this reason, we must use the router that is working as a gateway for each VLAN. Without a router, a host is unable to communicate outside of its own VLAN. The routing process between VLANs described above is called inter-VLAN communication.
To illustrate inter-VLAN communication, we will create a trunk that will carry traffic from three VLANs (VLAN2 and VLAN3, VLAN4) across a single link between a Mikrotik router and a manageable switch that supports VLAN trunking.
Each VLAN has its own separate subnet (broadcast domain) as we see in figure above:
VLAN configuration on most switches is straightforward, basically, we need to define which ports are members of the VLANs and define a ‘trunk’ port that can carry tagged frames between the switch and the router.
/interface vlan add name=VLAN2 vlan-id=2 interface=ether1 disabled=no add name=VLAN3 vlan-id=3 interface=ether1 disabled=no add name=VLAN4 vlan-id=4 interface=ether1 disabled=no
Add IP addresses to VLANs:
/ip address add address=10.10.20.1/24 interface=VLAN2 add address=10.10.30.1/24 interface=VLAN3 add address=10.10.40.1/24 interface=VLAN4
RouterOS /32 and IP unnumbered addresses
In RouterOS, to create a point-to-point tunnel with addresses you have to use the address with a network mask of ‘/32’ that effectively brings you the same features as some vendors unnumbered IP address.
There are 2 routers RouterA and RouterB where each is part of networks 10.22.0.0/24 and 10.23.0.0/24 respectively and to connect these routers using VLANs as a carrier with the following configuration:
/ip address add address=10.22.0.1/24 interface=ether1 /interface vlan add interface=ether2 vlan-id=1 name=vlan1 /ip address add address=10.22.0.1/32 interface=vlan1 network=10.23.0.1 /ip route add gateway=10.23.0.1 dst-address=10.23.0.0/24
/ip address add address=10.23.0.1/24 interface=ether1 /interface vlan add interface=ether2 vlan-id=1 name=vlan1 /ip address add address=10.23.0.1/32 interface=vlan1 network=10.22.0.1 /ip route add gateway=10.22.0.1 dst-address=10.22.0.0/24
Что такое VLAN?
VLAN (Virtual Local Area Network, виртуальная локальная сеть) — это функция в роутерах и коммутаторах, позволяющая на одном физическом сетевом интерфейсе (Ethernet, Wi-Fi интерфейсе) создать несколько виртуальных локальных сетей. VLAN используют для создания логической топологии сети, которая никак не зависит от физической топологии.
Примеры использования VLAN
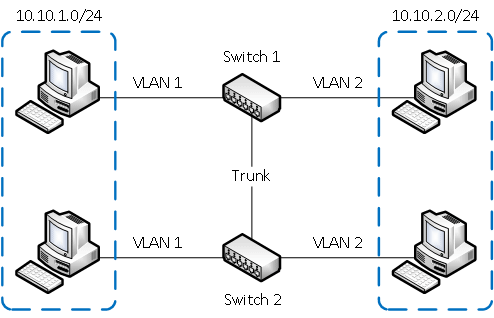
Объединение в единую сеть компьютеров, подключенных к разным коммутаторам.
Допустим, у вас есть компьютеры, которые подключены к разным свитчам, но их нужно объединить в одну сеть. Одни компьютеры мы объединим в виртуальную локальную сеть VLAN 1, а другие — в сеть VLAN 2. Благодаря функции VLAN компьютеры в каждой виртуальной сети будут работать, словно подключены к одному и тому же свитчу. Компьютеры из разных виртуальных сетей VLAN 1 и VLAN 2 будут невидимы друг для друга.
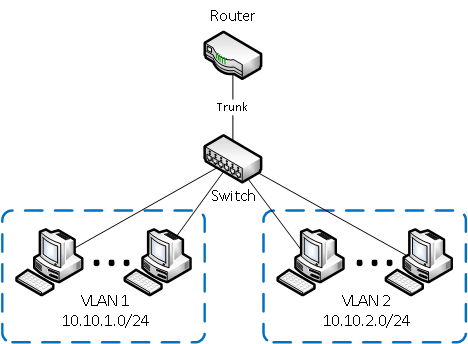
Разделение в разные подсети компьютеров, подключенных к одному коммутатору.
На рисунке компьютеры физически подключены к одному свитчу, но разделены в разные виртуальные сети VLAN 1 и VLAN 2. Компьютеры из разных виртуальных подсетей будут невидимы друг для друга.
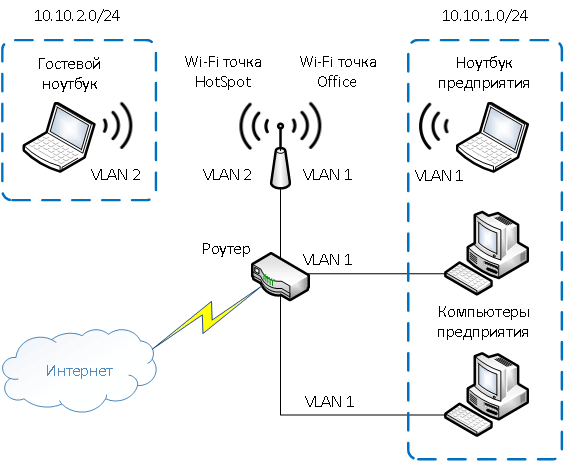
Разделение гостевой Wi-Fi сети и Wi-Fi сети предприятия.
На рисунке к роутеру подключена физически одна Wi-Fi точка доступа. На точке созданы две виртуальные Wi-Fi точки с названиями HotSpot и Office. К HotSpot будут подключаться по Wi-Fi гостевые ноутбуки для доступа к интернету, а к Office — ноутбуки предприятия. В целях безопасности необходимо, чтобы гостевые ноутбуки не имели доступ к сети предприятия. Для этого компьютеры предприятия и виртуальная Wi-Fi точка Office объединены в виртуальную локальную сеть VLAN 1, а гостевые ноутбуки будут находиться в виртуальной сети VLAN 2. Гостевые ноутбуки из сети VLAN 2 не будут иметь доступ к сети предприятия VLAN 1.
Достоинства использования VLAN
Гибкое разделение устройств на группы
Как правило, одному VLAN соответствует одна подсеть. Компьютеры, находящиеся в разных VLAN, будут изолированы друг от друга. Также можно объединить в одну виртуальную сеть компьютеры, подключенные к разным коммутаторам.
Уменьшение широковещательного трафика в сети
Каждый VLAN представляет отдельный широковещательный домен. Широковещательный трафик не будет транслироваться между разными VLAN. Если на разных коммутаторах настроить один и тот же VLAN, то порты разных коммутаторов будут образовывать один широковещательный домен.
Увеличение безопасности и управляемости сети
В сети, разбитой на виртуальные подсети, удобно применять политики и правила безопасности для каждого VLAN. Политика будет применена к целой подсети, а не к отдельному устройству.
Уменьшение количества оборудования и сетевого кабеля
Для создания новой виртуальной локальной сети не требуется покупка коммутатора и прокладка сетевого кабеля. Однако вы должны использовать более дорогие управляемые коммутаторы с поддержкой VLAN.