- How to Run Linux Commands as Another User?
- Method 1: Using the “runuser” Command
- Syntax
- Example 1: Switch the User and then Run Commands
- Example 2: Run the Linux Commands as Another User from the Same Shell
- Method 2: Using the su Command
- Example 1: Switch the User and then Run Commands
- Example 2: Run the Linux Commands as Another User from the Same Shell
- Method 3: Using the “pkexec” command
- Syntax
- Example
- Conclusion
- How can I execute a group of commands as another user in Bash?
- 3 Answers 3
- How to run a command as a specific user in an init script?
- 6 Answers 6
- Run script as another user on Linux
- 3 Answers 3
How to Run Linux Commands as Another User?
Sometimes, there is a need to run a Linux command from another user account, and to do so, the conventional approach is to switch to that user and then run the command. However, Linux distributions also support a feature to run a command as another user without logging out of the current user.
This blog will explore different approaches to run the Linux commands as another user.
Method 1: Using the “runuser” Command
The “runuser” command allows running the command as the substitute user in Linux distributions. The general syntax of using the “runuser” command to run Linux commands as another user:
Syntax
$ sudo runuser -[options] [username] [command]
According to the above general usage of the runuser command, we can use this command as the root user or with super-user privilege by using the “sudo”.
Then, we can use the different options of the runuser, which can be explored with the command:
The options and their application will be displayed on the screen.
Coming back to the general syntax of the “runuser” command, after specifying options, you have specified the user name to which you want to use and then the command.
Example 1: Switch the User and then Run Commands
For example, we will log in to another user, “john,” by using the runuser command’s option “-l”:
Now, we can run the multiple commands in the user john and then exit the shell by using the command:
The shell of john user has been logout.
Example 2: Run the Linux Commands as Another User from the Same Shell
If you want to run the command as John user from the same shell:
The contents of the john user directory have been displayed.
Method 2: Using the su Command
Next is switching the specified user account using the “su” command. The general syntax of using the “su” command:
$ su [options] - [username] [arguments]
The above general syntax of switching to another account is simple to understand. Use the su command with the “-” sign and specify the username. It will ask you for the user account’s password and log in to another user account.
Example 1: Switch the User and then Run Commands
To understand it more clearly, we will use the su command to log in to the “john” user account:
After asking for the password, it is logged in to the john user shell. Run the ls command in the new shell:
To go back to the “itslinux” user, again use the su command:
We are back to the shell of our user account.
Example 2: Run the Linux Commands as Another User from the Same Shell
To run the command without logging into another user shell, use the command:
First, it asks for a password, and then the result of the command is printed.
Method 3: Using the “pkexec” command
The “pkexec” command can also be used to run Linux commands by another user. The usage of the pkexec command is visualized in the following syntax:
Syntax
$ sudo pkexec --user [username] [command]
Example
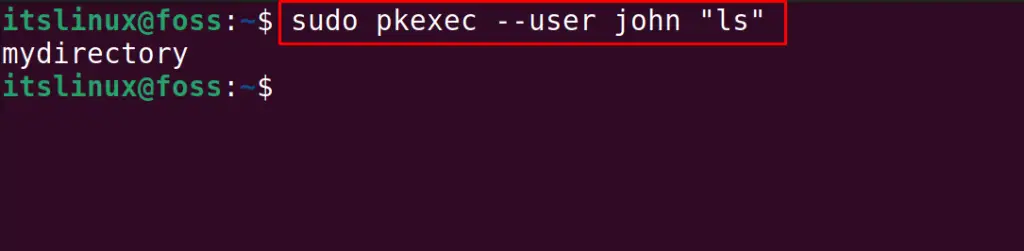
Following the above general syntax, we will log in to the john account and run the command:
The command has been executed in the “john” user account.
Conclusion
To run Linux commands as another user, we can use the “runuser” command and “pkexec” command and can log in to another user with the “su” command. All these commands switch to another user (either while execution or before execution) to run the command from a specific user’s account. This post has briefly explained the methods to run Linux commands as another user.
How can I execute a group of commands as another user in Bash?
There are already some existing questions asked here about running commands as another user. However, the question and answers focus on a single command instead of a long group of commands. For example, consider the following script:
#!/bin/bash set -e root_command -p param1 # run as root # these commands must be run as another user command1 -p 'parameter with "quotes" inline' command2 -p 'parameter with "quotes" inline' command3 -p 'parameter with "quotes" inline' - The final three commands must be run as another user using su or sudo . In the example there were three commands, but suppose that there were many more.
- The commands themselves make use of single and double quotes.
The second point above prevents the use of the following syntax:
. since the commands themselves contain quotes.
What is the proper way to «group» the commands and run them under another user account?
3 Answers 3
here-doc. The next token is the delimiter, and everything up to a line beginning with the delimiter is fed as standard input to the command. Putting the delimiter in single quotes prevents variable substitution within the here-doc.
This will be useful to some: If you need the command to actually run in the user’s full environment, as if they had logged in, which may include different paths, for example. Add they hyphen before ‘somebody’, like so: su — somebody .
Make sure there is no whitespace before closing EOF (eg when calling from indented ‘if’ statement). Error is thrown otherwise — see tldp.org/LDP/abs/html/here-docs.html
@PatrizioBekerle I did it interactively in the terminal, but I just tried it in a script as well, and they both worked.
I’m not that great with Bash-foo, so there is bound to be a more elegant way, but I’ve approached this problem in the past by using multiple scripts and a «driver».
#!/bin/bash set -e su root script1 su somebody script2 #!/bin/bash set -e root_command -p param1 # Run as root #!/bin/bash set -e # These commands must be run as another user command1 -p 'parameter with "quotes" inline' command2 -p 'parameter with "quotes" inline' command3 -p 'parameter with "quotes" inline' This script checks if the current user running the script is the desired user. If not, then the script is re-executed with the desired user.
#!/usr/bin/env bash TOKEN_USER_X=TOKEN_USER_X USER_X=peter # other user! SCRIPT_PATH=$(readlink -f "$BASH_SOURCE") if [[ "$@" != "$TOKEN_USER_X" ]]; then ###### RUN THIS PART AS the user who started the script echo "This script is $SCRIPT_PATH" echo -n "Current user: " echo $USER read -p "insert: " echo "got $REPLY" su - $USER_X -c "$SCRIPT_PATH $TOKEN_USER_X" # execute code below after else (marked #TOKEN_USER_X) else #TOKEN_USER_X -- come here only if script received one parameter TOKEN_USER_X ###### RUN THIS PART AS USER peter echo echo "Now this script is $SCRIPT_PATH" echo -n "Current user: " echo $USER read -p "insert: " echo "got $REPLY" exit 0 fi echo echo "Back to initial user. " echo -n "Current user: " echo $USER How to run a command as a specific user in an init script?
I’m writing an init script which is supposed to execute a single command as a user different than root. This is how I’m doing it currently:
sudo -u username command This generally works as expected on Ubuntu/Debian, but on RHEL the script which is executed as the command hangs.
Is there another way to run the command as another user?
(Note that I can’t use lsb init functions as they’re not available on RHEL/Centos 5.x.)
Notice that this question is about something set up exclusively by the administrator (typically, a daemon that runs as some user for security). A slightly different case is users setting up on their own commands to run at boot, with their user crontab. See askubuntu.com/questions/260845/…
6 Answers 6
On RHEL systems, the /etc/rc.d/init.d/functions script is intended to provide similar to what you want. If you source that at the top of your init script, all of it’s functions become available.
The specific function provided to help with this is daemon . If you are intending to use it to start a daemon-like program, a simple usage would be:
daemon --user=username command If that is too heavy-handed for what you need, there is runuser (see man runuser for full info; some versions may need -u prior to the username):
/sbin/runuser username -s /bin/bash -c "command(s) to run as user username" Run script as another user on Linux
One difference between your examplar question and your question is that the other question uses user1 ALL=(user2) NOPASSWD: /home/user2/bin/test.sh but you omit the = in your version. That might be all that’s wrong; it might be innocent. It’s worth checking.
I made sure it had the equals and still got the same results. The output is owned by wayne so I know its running correct script.
3 Answers 3
The answer is change from su to sudo.
su is primarily for switching users, while sudo is for executing commands as other users. The -u flag lets you specify which user to execute the command as:
sudo -u wayne '/home/wayne/script2.sh' gives Sorry user is not allowed to execute
Solution: In order to run commands/scripts as another user on linux/unix you need sudo permission and run the following formula:
For example:
sudo -H -u wayne bash -c 'echo "user:$USER|home:$HOME|action:run_script"; ./home/wayne/script.sh' from Documentation:
sudo allows a permitted user to execute a command as the superuser or another user, as specified by the security policy. -H The -H (HOME) option requests that the security policy set the HOME environment variable to the home directory of the target user (root by default) as specified by the password database. Depending on the policy, this may be the default behavior. -u user The -u (user) option causes sudo to run the specified command as a user other than root. To specify a uid instead of a user name, use #uid. When running commands as a uid, many shells require that the '#' be escaped with a backslash ('\'). Security policies may restrict uids to those listed in the password database. The sudoers policy allows uids that are not in the password database as long as the targetpw option is not set. Other security policies may not support this.