- List of essential Linux security commands
- Setting basic rules with UFW:
- Auditing yourself with nmap:
- The command chkrootkit to check your system for chrootkit infections:
- Checking your SELinux status and enable it if needed:
- About the author
- David Adams
- Linux Command Line Tools For Network Security
- Linux Command Switches
- Linux Help Functionality
- Case Sensitivity on the Command Line
- Linux Commands for Network Security
- The «ping» Command
- Check Name Resolution With The ping Command
- Using Ping to Check Security Posture
- The «ipconfig», «ifconfig», and «ip» Commands
- Security Commands in Linux
- A short overview on commands you can use to keep your machine secure
List of essential Linux security commands
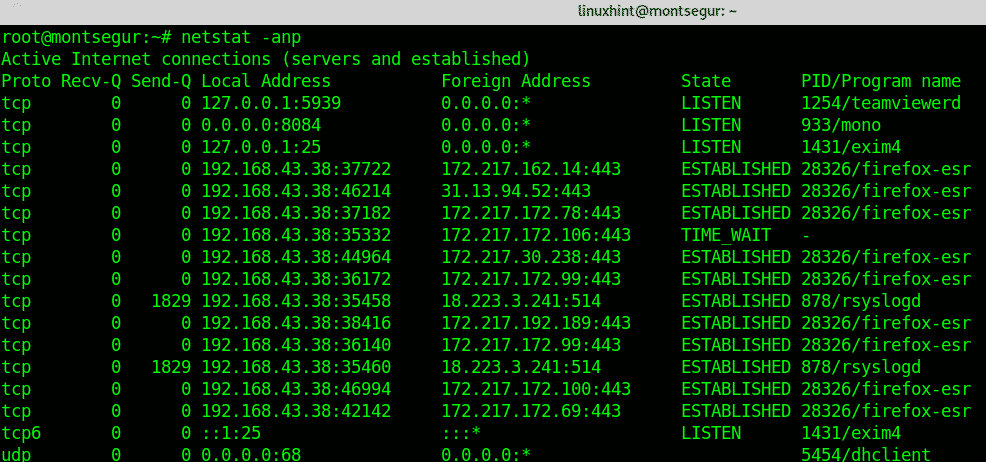
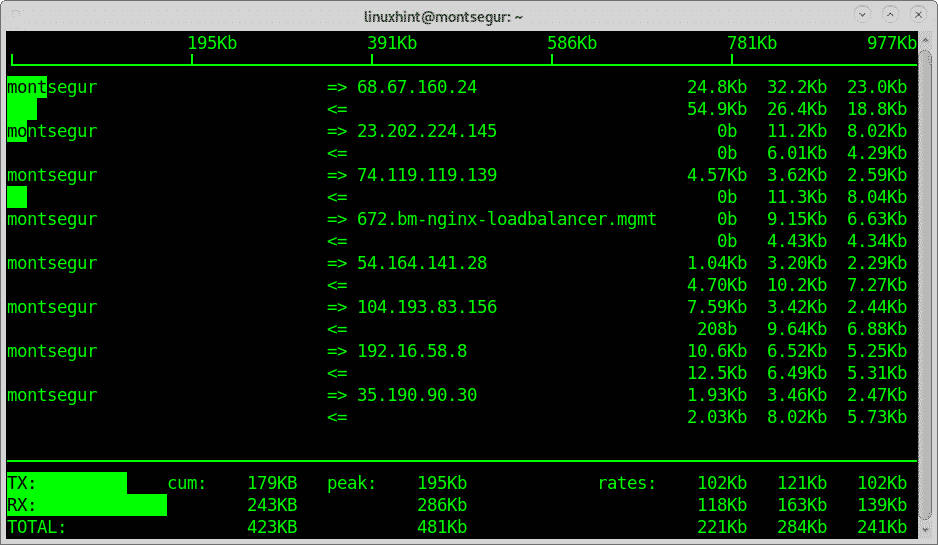
One of the most basic commands to monitor the state of your device is netstat which shows the open ports and established connections.
Below an example of the netstat with additional options output:
Where:
-a: shows the state for sockets.
-n: shows IP addresses instead of hots.
-p: shows the program establishing the conenction.
An output extract better look:
The first column shows the protocol, you can see both TCP and UDP are included, the first screenshot also shows UNIX sockets. If you are suspicious that something is wrong, checking ports is of course mandatory.
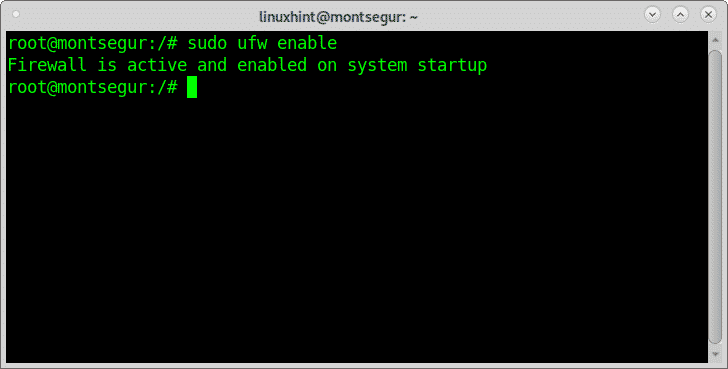
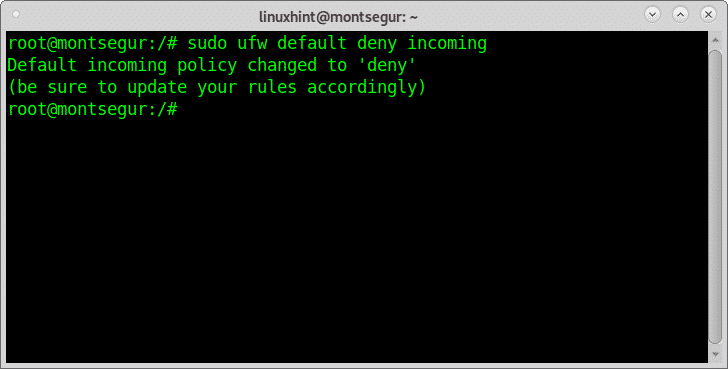
Setting basic rules with UFW:
LinuxHint has published great tutorials on UFW and Iptables, here I will focus on a restrictive policy firewall. It is recommended to keep a restrictive policy denying all incoming traffic unless you want it to be allowed.
To enable the firewall at startup run:
Then apply a default restrictive policy by running:
You will need to manually open the ports you want to use by running:
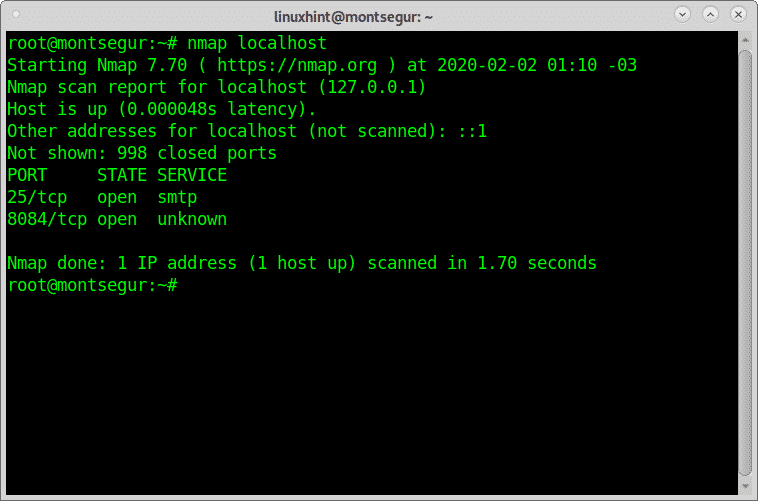
Auditing yourself with nmap:
Nmap is, if not the best, one of the best security scanners in the market. It is the main tool used by sysadmins to audit their network security. If you are in a DMZ you can scan your external IP, you can also scan your router or your local host.
A very simple scan against your localhost would be:
As you see the output shows my port 25 and port 8084 are open.
Nmap has a lot of possibilities, including OS, Version detection, vulnerability scans, etc.
At LinuxHint we have published a lot of tutorials focused on Nmap and its different techniques. You can find them here.
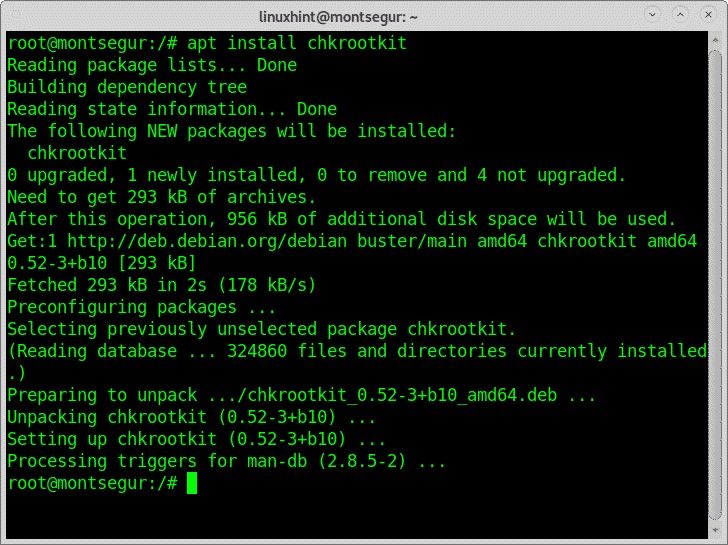
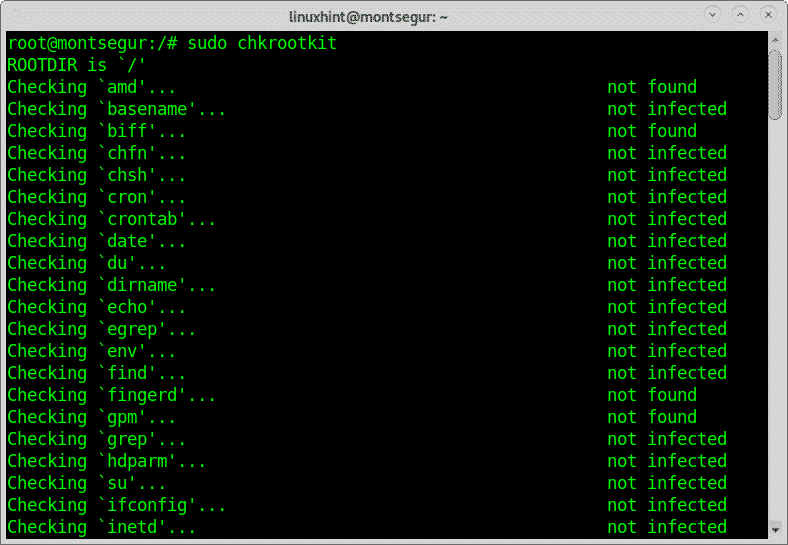
The command chkrootkit to check your system for chrootkit infections:
Rootkits are probably the most dangerous threat to computers. The command chkrootkit
(check rootkit) can help you to detect known rootkits.
To install chkrootkit run:
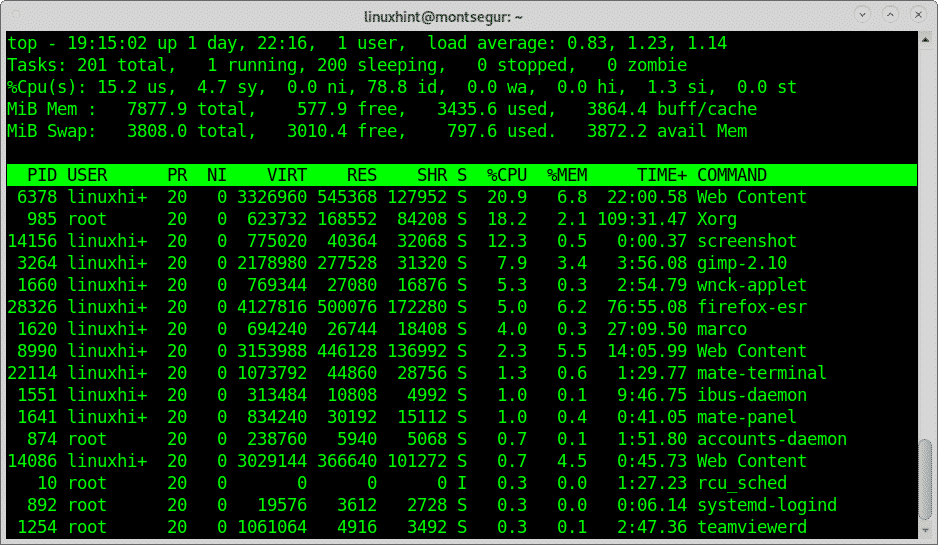
Using the command top to check processes taking most of your resources:
To get a fast view on running resources you can use the command top, on the terminal run:
The command iftop to monitor your network traffic:
Another great tool to monitor your traffic is iftop,
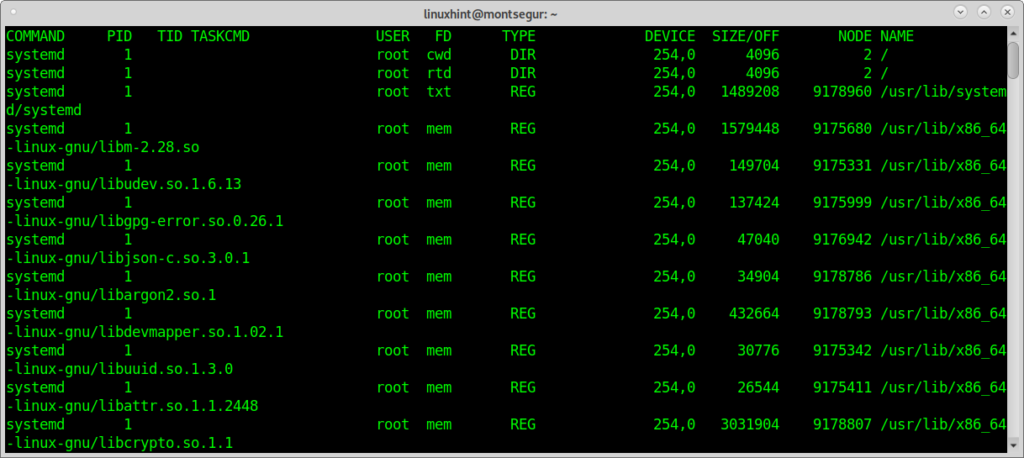
The command lsof (list open file) to check for files<>processes association:
Upon being suspicious something is wrong, the command lsof can list you the open processes and to which programs are they associated, on the console run:
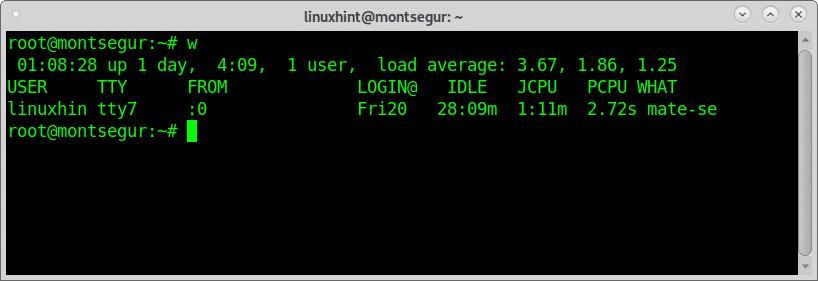
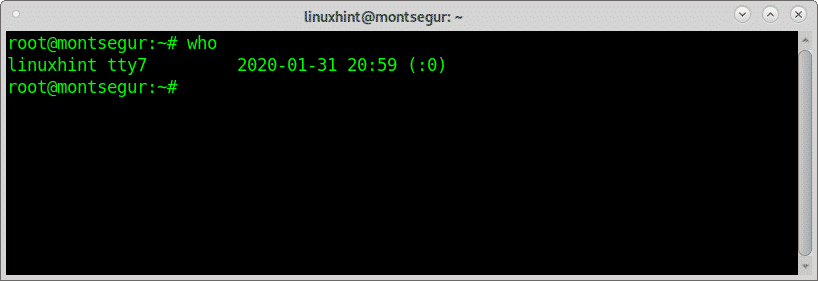
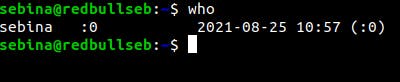
The who and w to know who is logged into your device:
Additionally, to know how to defend your system it is mandatory to know how to react before you are suspicious your system has been hacked. One of the first commands to run before such situation are w or who which will show what users are logged into your system and through what terminal. Let’s begin with the command w:
Note: commands “w” and “who” may not show users logged from pseudo terminals like Xfce terminal or MATE terminal.
The column called USER displays the username, the screenshot above shows the only user logged is linuxhint, the column TTY shows the terminal (tty7), the third column FROM displays the user address, in this scenario there are not remote users logged in but if they were logged in you could see IP addresses there. The LOGIN@ column specifies the time in which the user logged in, the column JCPU summarizes the minutes of process executed in the terminal or TTY. the PCPU displays the CPU used by the process listed in the last column WHAT.
While w equals to executing uptime, who and ps -a together another alternative, despite with less information is the command “who”:
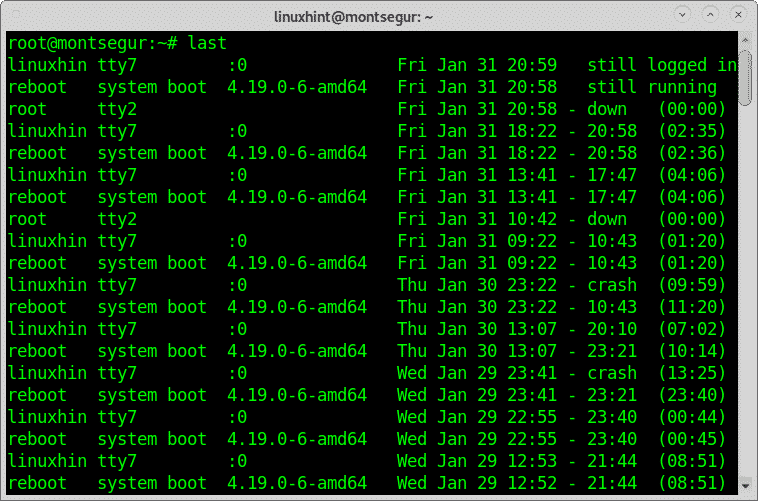
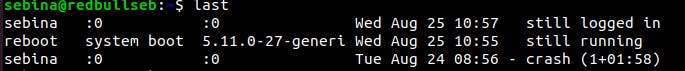
The command last to check the login activity:
Other way to supervise users’ activity is through the command “last” which allows to read the file wtmp which contains information on login access, login source, login time, with features to improve specific login events, to try it run:
Checking the login activity with the command last:
The command last reads the file wtmp to find information on login activity, you can print it by running:
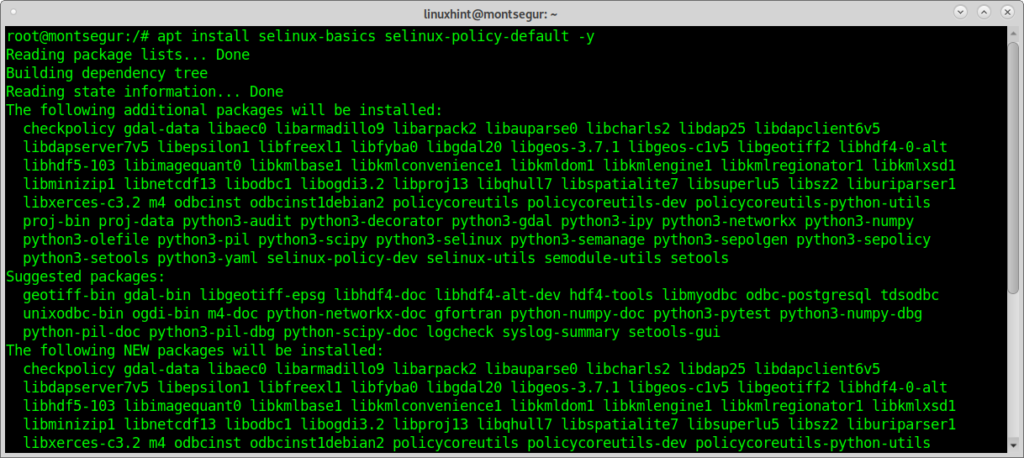
Checking your SELinux status and enable it if needed:
SELinux is restriction system which improves any Linux security, it comes by default on some Linux distributions, it is widely explained here on linuxhint.
You can check your SELinux status by running:
If you get a command not found error, you can install SELinux by running:
Check any user activity using the command history:
At any time, you can check any user activity (if you are root) by using the command history logged as the user you want to monitor:
The command history reads the file bash_history of each user. Of course, this file can be adulterated, and you as root can read this file directly without invoking the command history. Yet, if you want to monitor activity running is recommended.
I hope you found this article on essential Linux security commands useful. Keep following LinuxHint for more tips and updates on Linux and networking.
About the author
David Adams
David Adams is a System Admin and writer that is focused on open source technologies, security software, and computer systems.
Linux Command Line Tools For Network Security
Before diving in and throwing some Linux command line tools for network security at you, we figured we would ease you into it if you were new to Linux by going over switches, getting help and understanding case sensitivity.
Linux Command Switches
Almost every command you’ll run across has options available that you can invoke with a switch.
- A Windows command-line: switch uses a forward slash (/) or a dash (-) after the command and includes an option that modifies the command to perform a different function. The most used switch in Windows systems is the help switch identified with a question mark. For example, you can use the help switch to get help using these commands:
ping /? or ping -?
ipconfig /? or ipconfig -?
netstat /? or netstat -?
- Linux commands: Use switches too, but they typically only use a dash. Instead, if you want basic help on a command, you can often just type the command without any switch, or use the pipe symbol (|) and the word help
Linux Help Functionality
Most Linux distributions include a built-in user manual, the “man pages” that you can query with the man command. The syntax for the command is:
Be warned, there isn’t a consistent standard to get help for all commands in Linux. Sometimes, one method works, but another one doesn’t.
Case Sensitivity on the Command Line
Be aware that there is a substantial different in the way Windows and Linux handle case sensitivity
- Windows: Most Windows commands are not case sensitive; you can type in a command using uppercase characters, lowercase characters, or any combination. For example, each of the following commands will ping the localhost IPv6 address (::1) and provide the same output:
ping -6 localhost
PiNg -6 localHOST
PING -6 LocalHost
- Linux: Commands are typically lowercase and if you use uppercase letters, you’ll find that the command is not recognized.
And now, without any more ado, lets dive into some useful Linux command line tools for network security.
Linux Commands for Network Security
The «ping» Command
The “ping” command is a basic command used to test connectivity for remote systems; it verifies if a system can resolve valid host names to IP addresses, test the NIC and in short, check the security posture of a network.
The command checks connectivity by sending Internet Control Message Protocol (ICMP) “ echo request ” packets. Remote systems answer with “ ICMP echo reply ” packets, so receiving echo replies means that the remote system is operational. As a simple example, the use the “ping” command to verifies your computer can connect with another computer on your network:
ping 192.168.1.1
- Windows systems: ping sends out four ICMP echo requests. Systems that receive the ICMP echo requests respond with ICMP echo replies.
- On Linux-based systems, ping continues until you press the Ctrl + C keys to stop it. You can do control the number of pings by using:
- The -t switch like this:
Check Name Resolution With The ping Command
The name resolution process resolves a host name, such as cnn.com) to a specific IP address by querying a Domain Name System (DNS) with the host name and the DNS responds with an IP address.
A hacker might attempt to break the name resolution process for specific hosts by preventing a systems from get updates from an update server..
Verify name resolution works by pinging the host name of a remote system with the following command syntax to resolve the host name (cnn.com) to an IP address:The screenshot below shows the result when the command is executed at the command prompt on a Windows system.
If a ping command fails, it doesn’t always mean that the remote system is inoperable or or unreachable. Due to the fact that many denial-of-service (DoS) attacks use ICMP to disrupt services on Internet-based systems, firewalls often block ICMP traffic to prevent these attacks; the remote system might be operational, but the ping fails because the firewall is blocking ICMP traffic.
If you can connect to a site connect to the using a web browser, but experience ping failure, it is a good indication a firewall is blocking ICMP traffic.
Using Ping to Check Security Posture
Use ping to check the security posture of a network to confirm you’ve configured firewalls and routers to block ping traffic, you can verify the firewalls and routers are blocking the traffic by using ping to check it. You can use ping to simulate an attack from a couple of computers to repeatedly send ping requests. If you have an IPS up and running properly, it will block these attacks and the pings will stop receiving replies.
The «ipconfig», «ifconfig», and «ip» Commands
One of the most commonly used Linux command line tools for network security are the “ ipconfig ” (Windows) and “ ifconfig ” (Linux) commands. These shows the Transmission Control Protocol/Internet Protocol (TCP/IP) configuration information for a system. Technicians often use “ipconfig/ifconfig” as a first step when troubleshooting network problems. This information includes items such as the:
- Computer’s IP address
- Subnet mask
- Default gateway
- MAC address
- Address of a Domain Name System (DNS) server.
- Configuration information for all wired and wireless network interface cards (NICs) on a systems.
The Linux command, “ ifconfig “, an abbreviation of the term “interface configuration” has more has more capabilities than “ipconfig”, and can configure the NIC in addition to listing the properties of the NIC. Having said that, the “ ifconfig ” command was deprecated in 2009 in Debian Linux distributions of Linux. So while the command is part of the “ net-tools ” package and developers are no longer maintaining that package, you will still see ifconfig and other tools in the net-tools package on most Linux systems, including Kali Linux. The preferred tool to use is the “ip” command, which can display information and configure network interfaces, but lacks the functionality of “ ifconfig “. The screenshot below shows the use some common commands on Windows:
Security Commands in Linux
A short overview on commands you can use to keep your machine secure
Heyo everyone! Today I’m doing an overview on a few security commands! If you prefer threads, I already did a thread on this a while back, check out Twitter
Because I have been busy with school, I’ve not really had time to create any new articles so I will be doing a lot of review and article creating on my old threads. 😆
You may know ss to be more of a ‘networking’ command, but the command can also be used for security purposes.
ss = lists all connections
ss -a = lists listening and non listening ports
ss -t = lists tcp connections
the ‘who’ commands lists everyone who is logged in.
This may not apply to you, but since Linux is multi-user, this command can be used to find who is logged in.
The ‘last’ command showed you who logged in last and some activity.
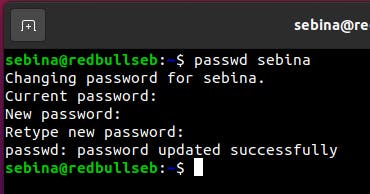
This is a very basic command, all it does it change the password, but of course changing your password from time to time can help with the security of your machine.
You use ‘passwd’ to change the password of a user if needed.
‘ufw’ stands for uncomplicated firewall, this is used to manage firewall rules.
Some distros that use this command are Arch and Ubuntu.
Thank you for reading my article today!🥳 I’ll be doing my best to get back to posting as I used to, I’m hoping to get actual new content out there. But, if you’re interested in keeping up, follow me on twitter that is where I will be most active. Thank you again 😃