- What is a segmentation fault?
- 3 Answers 3
- Troubleshooting Segmentation Fault Errors in Linux
- What Is a Segmentation Fault?
- Identifying Segmentation Faults
- Debugging Segmentation Faults with GDB
- Troubleshooting a Segmentation Fault
- Conclusion
- Fix: segmentation fault (core dumped) Linux
- Reason: Attempting the Non-Existing Memory
- Solution 1: Remove the Lock File
- Solution 2: Kill the Specific Process
- Conclusion
What is a segmentation fault?
In Ubuntu I have faced the segmentation fault error many times. What is a segmentation fault and when does it occur?
Just to cover it up: I had a similar problem, whereas my segfaults were not reliably reproduceable and they came from (almost) random applications. Found out that most likely my memory is broken. So if quite any program causes segfaults, one might have a closer look at the RAM.
3 Answers 3
An error saying segmentation fault (or segfault, or SIGSEGV) in Ubuntu and other Unix-like operating systems, or saying general protection fault in Windows, is when a program attempts to access a part of memory that cannot be accessed, or which the program is prohibited from accessing. A segmentation fault is a kind of program crash, that is, an abnormal termination of a program. See the Wikipedia articles on crashes, memory protection, segmentation fault, general protection fault, and SIGSEGV for more information (and a more textured understanding of the topic than is presented here).
A segmentation fault is almost always due to a bug in the program where it occurs. I am guessing most or all of your segmentation faults are happening from the same application. Please provide more details about the circumstances under which segmentation faults are happening on your machine, and what program is crashing. Please also provide the full and exact text of the error message you’re receiving and any other messages that appear before it. This should make it possible for us to provide detailed advice specific to your problem (rather than just general information about what a segmentation fault is).
The best way for you to provide this information is for you to edit your question to include it. Alternatively, if you want this question to be just about segmentation faults in general, you could post a new question to ask about what specifically is causing your segmentation faults (if you do this, make sure to provide all these details in your new question).
Troubleshooting Segmentation Fault Errors in Linux
Linux, like any robust operating system, is built to handle various types of errors. One such error that often perplexes beginners and even intermediate users is a Segmentation Fault, colloquially referred to as ‘segfault.’ This article aims to provide a comprehensive understanding of segmentation faults and offer pragmatic troubleshooting measures to handle them effectively in a Linux environment.
What Is a Segmentation Fault?
A Segmentation Fault is an error that occurs when a running program attempts to access a memory location not allocated to it or tries to perform an operation not permitted in that particular memory segment. This illicit activity could be reading or writing into a forbidden segment, or attempting to execute data in a non-executable segment.
The operating system’s response to such a transgression is abrupt and decisive. It raises a `SIGSEGV` signal, terminating the offending program instantaneously, resulting in a Segmentation Fault.
Identifying Segmentation Faults
Spotting a Segmentation Fault is relatively straightforward. If you attempt to run a program from the terminal and it crashes midway, printing an output `Segmentation fault (core dumped)`, you have encountered a segfault. While this output signals a memory-related error, it does not specify the error’s cause. To glean more detailed information about the error’s origins, debuggers such as `gdb` (GNU Debugger) come in handy.
Debugging Segmentation Faults with GDB
The GNU Debugger (gdb) is a robust debugging tool that allows you to scrutinize programs at the source code level. To use gdb to diagnose a segfault, follow these steps:
First, compile your program with the `-g` flag, which instructs the compiler to collect comprehensive debugging information.
gcc -g myprogram.c -o myprogram Next, execute the program within gdb.
Within the gdb shell, use the `run` command to start the program. If the program crashes, gdb will pinpoint the function and the line number where the Segmentation Fault transpired, providing a clue about the error’s root cause.
Troubleshooting a Segmentation Fault
Repairing a Segmentation Fault demands that your program refrain from accessing unowned memory. Here are a few common sources of segfaults and their remedies:
- Null Pointer Dereferencing: Ensure that your program does not dereference a null pointer. Always validate pointers before using them.
- Buffer Overflow: Buffer overflows occur when your program writes more data to a buffer than it was designed to accommodate. Always verify the array boundaries before performing read or write operations.
- Uninitialized Pointer: Using an uninitialized pointer can result in a Segmentation Fault. Make it a habit to initialize your pointers before their use.
- Accessing Freed Memory: If your program attempts to access a memory location that has been freed, it could trigger a Segmentation Fault. Steer clear of using pointers after passing them to `free`.
Conclusion
Dealing with Segmentation Faults is an inevitable part of a programmer’s journey, particularly when working with languages that allow direct memory manipulation like C and C++. These errors can be intimidating initially, but with a deep understanding and the right tools like `gdb`, you can diagnose and fix these faults with confidence. Above all, writing safe and clean code that respects memory boundaries will drastically reduce the occurrence of these errors, ensuring your programs run smoothly and reliably.
Fix: segmentation fault (core dumped) Linux
In Linux, the error “segmentation fault (core dumped)” comes across during the execution of the script file (C, C++, Python, Java) from the terminal. The core dump is when a code performs read and write operations on a free memory location.
This article will provide multiple solutions to the above-stated “segmentation fault (core dumped)” error. The supported content of this guideline is as follows:
Reason: Attempting the Non-Existing Memory
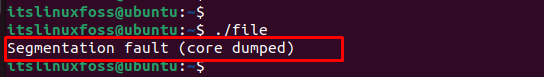
The main cause of this error is that you are trying to access a specific portion of memory that does not exist. For instance, when users try to read or write the elements of a non-existent array, do not define the pointer before using it or use a memory address with the same variable value. Therefore, the particular program will crash and display the “segmentation fault” error when executing the file:
The next sections contain several solutions to encounter the above error.
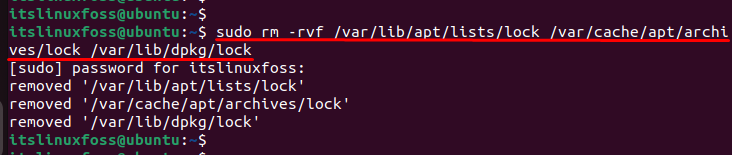
Solution 1: Remove the Lock File
During the execution of a program, locked files are created to make the script files executable. To resolve the error, one of the solutions is to remove the lock file that attempts the non-existent memory. For removing these files, the “rm” command is used to delete the lock files:
$ sudo rm -rvf /var/lib/apt/lists/lock /var/cache/apt/archives/lock /var/lib/dpkg/lock
Let’s head over to another solution.
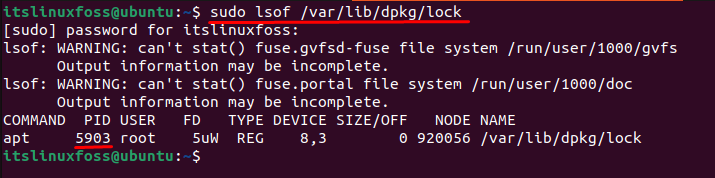
Solution 2: Kill the Specific Process
Users can consider another solution to resolve errors by killing the specific process. First, locate the process id stored in the “/var/lib/dpkg/lock” directory:
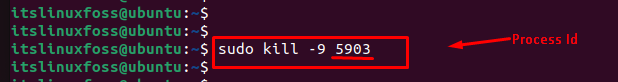
After identifying the specific process id, you can go to terminate the process. For this, the “kill” command is utilized with a “-9” signal that forcefully terminates the running process “5903”:
You can verify that the “kill” command terminates the specific process via “5903” id.
Conclusion
In Linux, the error “segmentation fault (core dumped)” occurs when the process requires additional memory that the operating system does not permit access. It can be resolved by removing the “lock” files through the “rm” command, clearing the cache repository, or killing the process via “process id”. This article has explained all possible solutions to encounter the error mentioned above.