How to Pass Password to SSH Command in Linux
The only way a user can accomplish a complete Linux operating system experience is if this user has had a partial or full glimpse of both sides of the Linux environment. Linux operating system exists both as a desktop environment and as a server environment.
For the desktop environment, users have the advantage of using GUI icons and applications to fulfill their operating system objectives. As for the server environment, an OS user needs some level of authentic familiarity with the Linux terminal commands to achieve an OS goal.
Most users stick to the desktop environment and others to the server environment. However, a multidimensional user will want to experience both sides of these environments. In this case, a Linux desktop user will need to flexibly access a Linux server environment and a Linux server user might also want to access other Linux server environments, routers, and firewalls.
Connecting to Linux Server Using SSH
There is no better-known tool for accessing Linux routers, firewalls, and servers than through the SSH cryptographic network protocol. The traditional approach of using the SSH protocol is summarized in by the following syntax:
$ ssh [email protected]_domain_name_or_server_ip_address
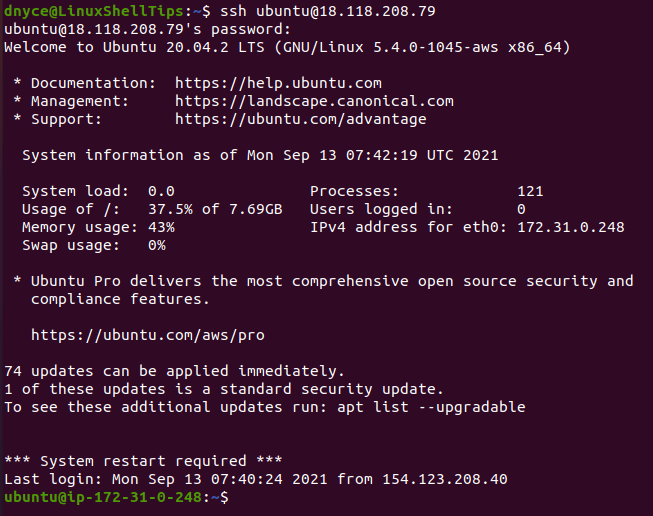
For example, I could access one of my servers in the following manner:
As per the above screen capture, the first access attempt to the Linux server was initiated by the command:
The execution of the above SSH command then later led to the prompt:
It is at this point that I keyed in the user-related (ubuntu) password and was successfully able to gain access to the Linux server.
For a novice Linux user or learner, this server-access approach is exciting and worth the pursuit. However, as you become an elite Linux user, you do not want to repeat yourself with a two-liner Linux command when you could only use one.
This article is here to fix this two-liner server access issue and provide an effective one-liner SSH access command for all your future Linux servers, routers, and firewalls access.
Install SSHPass in Linux – A SSH Password Provider
sshpass command-line tool will do the job for us. It facilitates a simplified approach to non-interactive ssh sign-in and supports one-liner ssh password input.
Firstly, you need to install the sshpass tool on your Linux operating system. Before the installation, ensure that you either have Sudo privileges or you are a Sudoer user of the Linux system.
$ sudo apt-get install sshpass [On Debian, Ubuntu and Mint] $ sudo yum install sshpass [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/sshpass [On Gentoo Linux] $ sudo pacman -S sshpass [On Arch Linux] $ sudo zypper install sshpass [On OpenSUSE]
How to Add Password to SSH Command in Linux
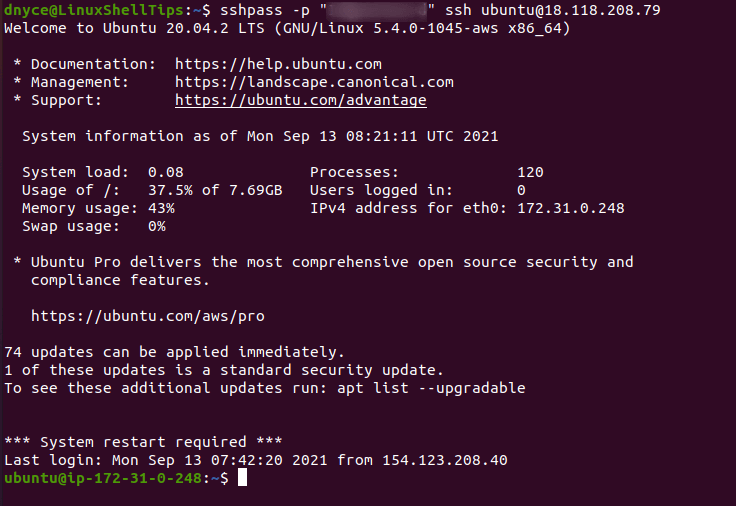
With the successful installation of SSHPASS, the one-liner SSH command syntax for accessing a remote Linux server, router, or firewall will look like the following:
In my case, I would implement SSHPASS usage in the following manner:
As expected, I have successfully accessed my Linux server with a one-liner command.
Combining the use of SSHPASS and SSH to access a remote server, router, or firewall gets rid of unnecessary two-liner commands that lead to an additional password entry prompt. It makes your remote access to other Linux environments faster and efficient.
adding password to .ssh/config [closed]
Questions should demonstrate reasonable information technology management practices. Questions that relate to unsupported hardware or software platforms or unmaintained environments may not be suitable for Server Fault.
I’m using ubuntu 12.04. I’m using ssh for connecting to many servers daily, so I put their parameters in .ssh/config file; like this :
Host server1 User tux Port 2202 HostName xxx.x.xx.x I know we should use key-pair ensure security, however sometimes we can’t add public key into the remote machine (e.g. a public SSH server which accepting password and execute a specific command, or an user without a home directory). So, is there a way to put passwords in this file, for each connection? So when the server asks for a password, the terminal puts its pass and send it to the server, so I need not type the password each time.
@MichaelHampton RTFQ: I know we should use key-pair ensure security, however sometimes we can’t add public key into the remote machine (e.g. a public SSH server which accepting password and execute a specific command, or an user without a home directory).
7 Answers 7
No, There is no method to specify or provide on the command line the password in a non-interactive manner for ssh authentication using a openssh built-in mechanism. At least not one what I know of. You could hardcode your password into expect script but it is not a good solution either.
You definitely would want to use keypairs for passwordless authentication as Michael stated, in the end private key is pretty much a big password in the file.
The thing is, its my clients servers and they dont allow login using keys. Im writing a bash script using expect for login to all servers where the credentials are being stored n taken from a usb storage device. Thanks
Quite insecure. The only thing to suggest in that script to lock that file with tough file permissions.
If they don’t allow keys they misunderstand how ssh works — allowing password login opens you up to dictionary attacks etc (albeit very, very slow ones) — it is next to impossible to accomplish the same with a private key pair, and if they’re worried about the keys falling in to the wrong hands you can password-encrypt the private part of the key so that you need two factors to be able to use it (the password can also be remembered in your keychain / by your ssh agent)
Educate your clients. Explain them that is better to disable password authentication and only permit keys that the reverse.
Gotta love when you run into a stackoverflow question where the top answer is categorically wrong, and accepted, and you have to scroll down to find the real answers, provided by people that understand that sometimes you have to connect to a server where the admin is not willing to enable key login.
To avoid the string of comments: Yes, this is insecure (not even arguably insecure). I would strongly recommend you only do it in a lab situation on an isolated network or a similiar situation that does not involve production servers or potentientially production server without a full reset/format.
I wanted to set this up as I don’t think my 2950 switch supports private/public keys and I hope at some point to get that knowledge, but I am not there yet.
Using an alias and sshpass this can be accomplished.
- Install sshpass
- Alter your .ssh/config file to include the username as listed in the question
- Add an alias to your terminal (I used .bashrc and would recommend against gloabl settings)
- Use alias to log into the target
alias ssc='sshpass -pcisco ssh' Where «cisco» is the password. Note there is no space between the -p and the password.
Usage is (referencing the question):
Note: This answers the question in title only for those using search engines. If you are using servers like the question example, private/public key pairs and not this answer should be used
How to specify password in ssh command
From the terminal I type: ssh user@ip and then it prompts for a password.
Is there a way to specify the password in the ssh command itself?
2 Answers 2
sshpass -ffilename ssh user@ip # prefer this sshpass -pPa5sw0rd ssh user@ip # avoid this where your password is in the first line of the file filename or it is literally Pa5sw0rd . Notes:
- In the manual there is no space after -p or -f , but at least sshpass 1.06 in my Debian 10 allows it; your sshpass may or may not.
- If your password contains characters your shell will interpret (like $ , ‘ or ; ) then you should quote it properly in the command line (but not in the file).
- Avoid -p . Use chmod 600 filename to make the file private (root will still be able to access it though). Read about security considerations in the manual.
Any solution for macOS? sshpass isn’t part of the default OS, and doesn’t seem to be available in Homebrew either.
The correct way to do this, is to switch from password authentication to a public/private key pair. This typically needs no reconfiguration at all and is quite easy.
Step 1: If you do not have a key, create one: ssh-keygen will do that for you
Step 2: Authorize this key on the remote host: Run ssh-copy-id user@ip once, using your password
Step 3: From now on ssh user@ip will no longer ask for your password
Thats correct. But the servers that i am working with are currently having password based authentication. And its really irritating to type password each time they prompt
from a security perspective this is the correct way to do it. but the OP asked «How to specify password in ssh command».
Nearly ALL servers allow key authentication in addition to password authentication — so you use the password authentication (via ssh-copy-id ) to enable the key.