- Setting default permissions for newly created files and sub-directories under a directory in Linux?
- Set Default Permission for New Files and Subdirectories
- 1. Overview
- 2. Setting the Default Permission
- 2.1. What Is ACL?
- 2.2. Enabling ACL on the Filesystem
- 2.3. Setting the Permissions With setfacl
- 2.4. Setting Default Permission for Different User or a Group
- 2.5. Tools That Preserve Permissions
- 3. Conclusion
- What is Umask and How to Use It
- Umask Overview
- How Does Umask Work?
- The umask Command Syntax
- Symbolic and Numeric umask Values
- How to Calculate Umask Values
- How to Set and Update the Default Umask Value
- Setting Up a Symbolic Umask Value
- Setting Up a Numeric Umask Value
- Difference Between umask and chmod
Setting default permissions for newly created files and sub-directories under a directory in Linux?
I have a bunch of long-running scripts and applications that are storing output results in a directory shared amongst a few users. I would like a way to make sure that every file and directory created under this shared directory automatically had u=rwxg=rwxo=r permissions. I know that I could use umask 006 at the head off my various scripts, but I don’t like that approach as many users write their own scripts and may forget to set the umask themselves. I really just want the filesystem to set newly created files and directories with a certain permission if it is in a certain folder. Is this at all possible? Update: I think it can be done with POSIX ACLs, using the Default ACL functionality, but it’s all a bit over my head at the moment. If anybody can explain how to use Default ACLs it would probably answer this question nicely.
POSIX ACLs are nice, however a good 60% of the machines that you encounter won’t have them turned on for certain file systems, depending on the distribution. Here is a very good introduction and example: suse.de/~agruen/acl/linux-acls/online
You mean the same document I linked 🙂 I haven’t had a change to read it yet but thanks for the head’s up on the availability problem.
The link in Tim Post’s comment appears to be dead, but thanks to the Internet Archive, I could view it, and verify that vanemery.com/Linux/ACL/POSIX_ACL_on_Linux.html contains the exact same document. I’ll edit the question to update the link.
Set Default Permission for New Files and Subdirectories
The Kubernetes ecosystem is huge and quite complex, so it’s easy to forget about costs when trying out all of the exciting tools.
To avoid overspending on your Kubernetes cluster, definitely have a look at the free K8s cost monitoring tool from the automation platform CAST AI. You can view your costs in real time, allocate them, calculate burn rates for projects, spot anomalies or spikes, and get insightful reports you can share with your team.
Connect your cluster and start monitoring your K8s costs right away:
1. Overview
In this tutorial, we’ll look at setting default permissions for newly created files and sub-directories on a directory or a filesystem. First, we’ll start with a brief introduction to ACL and how we can enable it on our filesystem. Then, we’ll work our way up to setting up the permissions for newly created files on a home directory.
2. Setting the Default Permission
File permissions are privileges for carrying out specific operations on files. We can grant these permissions to a certain user or a group of users. The operations that a user can carry out on files can either be read, written, execute or a combination of these operations.
On Linux, by default, when we create new files, they are given rw-rw-r– permissions. The r, w, and x signify the read, write, and execute permissions, respectively.
Let’s break down the rw-rw-r– permission for files:
- The first rw- signifies read-write permissions for the user or the owner of the file
- The second rw- indicates read-write permissions for the group the file belongs to
- The final r– read permission is for all other users
Similarly, for newly created directories, the default permission is rwxrwxr-x .
2.1. What Is ACL?
Access Control List (ACL) is a mechanism that allows us to set complex permissions to a filesystem. Not only that, but we can also use ACL to apply permissions to a specific file or a directory. With ACL, we can modify the default permissions for newly created files and directories.
On ext4, the ACL support is already enabled. However, we can enable it on other filesystem types as well, which we’ll cover in the next section.
2.2. Enabling ACL on the Filesystem
We can easily enable the ACL support on other filesystem types, such as ext3 and fat, by adding the acl option to the partition entry in the fstab file. The fstab file is located in the /etc directory and contains the configuration for our partitions.
Let’s open up the fstab file and add the acl option for the required partitions’ entries:
# /dev/sda4 /home ext3 rw,relatime,acl 0 1 . . .In this case, we’ve added the acl option to our /dev/sda partition, which is mounted on the /home directory. Once we’ve added the option, we can simply remount the partition with mount for our changes to take effect:
Now, the ACL support should be enabled, and we can apply our desired permissions for newly created files and directories on the /dev/sda4 partition.
2.3. Setting the Permissions With setfacl
On Linux, the setfacl utility is used to manage the ACLs of directories and files. This utility comes with the acl package, which should already be installed on our machine by default. However, we can install it from our distribution’s official repository if, for some reason, it’s not installed on our machine.
We can apply default permissions for files and directories with setfacl using the following command syntax:
$ setfacl [OPTIONS] [PERMISSIONS] [FILE|DIRECTORY]Now, let’s apply default permissions for files and directories under /dev/sda4 partition, which happens to be mounted on /home:
$ setfacl -PRdm u::rwx,g::rw,o::r /home- -d sets the default permission for the /home directory
- -m signifies that we want to make changes to the ACL
- -R will apply the permission to all the files and subdirectories in the /home folder recursively
- -P will prevent the operation from following symbolic links — to avoid the risk of compromising security
- The pattern afterward specifies the default permissions for the /home directory
The permissions for each class of users are separated by commas. For example, the u::rwx specifies default permissions for the user or the owner of the /home directory. In this case, the owner can read, write, and execute newly created files and directories in the /home directory. Similarly, the owning group receives read-write permissions, while others receive only the read permission.
Now, let’s create a file under the /home directory to test our new permissions:
$ touch /home/hey/test $ ls -l /home/hey/test .rwxrw-r-- hey hey 0 B Fri Jan 21 22:42:01 2022 testSince we’ve used the -R option, any new files and folders under the /home hierarchy will receive the appropriate default permissions.
2.4. Setting Default Permission for Different User or a Group
We can also put a uid (user ID) or a gid (group ID) between the colons. So, we should use this approach if we want to assign permissions for a user who is not the file or directory owner. As an example, if we want to set permission for the user doe, with uid 1001, we can simply specify the permissions as:
$ setfacl -PRdm u:1001:rw /home2.5. Tools That Preserve Permissions
There are tools like cp, tar, unzip, and rsync that will try to preserve the permissions of the source files when creating new files and directories. In other words, these tools will mask the permission of our default ACL. Therefore, when using these tools, we should apply our required permissions to the resulting new files and directories manually with chmod.
3. Conclusion
In this article, we saw how we could set default permission for newly created files and directories on a Linux partition or a directory. We covered what ACL is and how to use the setfacl helper utility to set default permissions for newly created files and directories.
What is Umask and How to Use It
When creating a new file or directory, Linux applies the default set of permissions. The umask command lets you change these default permissions.
In this tutorial, you will learn what umask is, how it works, and how to use it to set up file and directory permissions for individual users or groups.
- Linux-based system (e.g., Ubuntu, CentOS, Debian)
- A user account with sudo privileges
- Access to the command terminal
Umask Overview
The term umask refers to two things:
1. The Linux umask command. umask (user file-creation mode) is a Linux command that lets you set up default permissions for newly created files and folders.
2. A user-defined permissions ‘mask’. A user can choose how to restrict permissions by using a permissions mask. A permission mask interacts with the default system permissions and changes them. The umask command is used to apply this mask.
How Does Umask Work?
The umask command works by affecting the default Linux file and folder permissions.
There are three categories of permissions for every file and folder in Linux:
- User: Defines permissions for each individual user. By default, the user who creates a file or folder is set as the owner.
- Group: Defines permissions for a group of users that share the same level of access.
- Other: Defines permissions for anyone not included in the two previous categories.
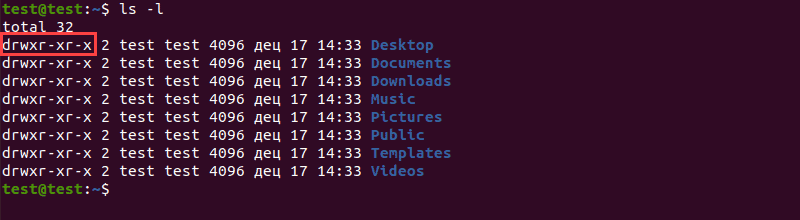
Use the following command to review permissions for the home folder:
Each line of the output starts with a 10-character string detailing permissions. Breaking down the highlighted entry, this string consists of the following elements:
- d : Indicates the file type (directory).
- rwx : Indicates user permissions (read, write, and execute).
- r-x : Indicates group permissions (read and execute).
- r-x : Indicates other permissions (read and execute).
The umask Command Syntax
Using the umask command without additional command options returns the current mask as the output:
The umask command uses the following syntax:
- [mask] : The new permissions mask you are applying. By default, the mask is presented as a numeric (octal) value.
- [-S] : Displays the current mask as a symbolic value.
- [-p] : Displays the current mask along with the umask command, allowing it to be copied and pasted as a future input.
Symbolic and Numeric umask Values
As we mentioned in the example above, umask can be displayed as a numeric (octal) or symbolic value.
A mask can have the following numeric, and the corresponding symbolic, values:
| 0 | — | No permission |
| 1 | —x | Execute |
| 2 | -w- | Write |
| 3 | -wx | Write and execute |
| 4 | r— | Read |
| 5 | r-x | Read and execute |
| 6 | rw- | Read and write |
| 7 | rwx | Read, write, and execute |
How to Calculate Umask Values
Linux uses the following default mask and permission values:
- The system default permission values are 777 ( rwxrwxrwx ) for folders and 666 ( rw-rw-rw- ) for files.
- The default mask for a non-root user is 002, changing the folder permissions to 775 ( rwxrwxr-x ), and file permissions to 664 ( rw-rw-r— ).
- The default mask for a root user us 022, changing the folder permissions to 755 ( rwxr-xr-x ), and file permissions to 644 ( rw-r—r— ).
This shows us that the final permission value is the result of subtracting the umask value form the default permission value (777 or 666).
For example, if you want to change the folder permission value from 777 (read, write, and execute for all) to 444 (read for all), you need to apply a umask value of 333, since:
How to Set and Update the Default Umask Value
Use the following syntax to apply a new umask value:
Setting Up a Symbolic Umask Value
Set a new umask value by using symbolic values with the following syntax:
- u : Indicates user permissions.
- g : Indicates group permissions.
- o : Indicates other permissions.
- # : The symbolic permission value you want to apply, as detailed in the table above.
Note: Never use space after comas when setting up a symbolic mask value.
There are also other operators you can use:
- = : Creates specified file permissions and prohibits unspecified permissions.
- + : Creates specified permissions, but does not change unspecified permissions.
- — :Prohibits specified permissions, but does not change unspecified permissions.
Setting Up a Numeric Umask Value
Once you calculate the required umask numeric value, set it up by using:
Difference Between umask and chmod
The chmod command in Linux works in a similar way to the umask command. It too is used to define permissions for files and folders.
The difference between umask and chmod is that umask changes the default permissions and thus the permissions for all newly created files and folders, while chmod sets permissions for files and folders that already exist.
After following this tutorial, you should be able to review and change umask using symbolic or numeric values.
Make sure you also take a look at our Linux command cheat sheet for more commonly used Linux commands.