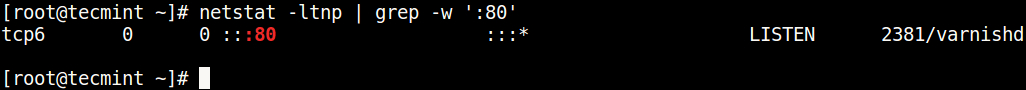- How to know what program is listening on a given port?
- 8 Answers 8
- 3 Ways to Find Out Which Process Listening on a Particular Port
- 1. Using netstat Command
- 2. Using lsof Command
- 3. Using fuser Command
- Check for Listening Ports in Linux
- What is Listening Port
- Check Listening Ports with netstat
- Check Listening Ports with ss
- Check Listening Ports with lsof
- Conclusion
How to know what program is listening on a given port?
I suspect a program is listening on port 8000 on my machine. When I run the following command, I get this error:
> python -m SimpleHTTPServer # Lots of python error socket.error: [Errno 98] Address already in use If I use another port ( 8000 is the default), the web server runs fine. If I run wget localhost:8000 from the command line, it returns 404 Not Found . What can I do (or what tools are available) to find what program is listening on port 8000 , and from there where that program is configured?
8 Answers 8
Open your terminal and type as
that command will list you the application used by that port with PID. (If no results run via sudo since your might have no permission to certain processes.)
For example, with port 8000 ( python3 -m http.server ):
$ lsof -i :8000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME python3 3269 user 3u IPv4 1783216 0t0 TCP *:8000 (LISTEN) $ sudo lsof -i :22 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME sshd 998 root 3u IPv4 1442116 0t0 TCP *:ssh (LISTEN) sshd 998 root 4u IPv6 1442118 0t0 TCP *:ssh (LISTEN) @Imray the example searches for port 8881. The PID column contains the process IDs and the NAME column contains the ports.
You can use netstat to see which process is listening on which port.
You can use this command to have a full detail :
if you need to know exactly which one is listening on port 8000 you can use this :
sudo netstat -peanut | grep ":8000 " There is no process that can hide from netstat.
To kill/end the process use kill
To expound on the answer by @33833 you can get some very detailed info, for example:
$ lsof -i :8000 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME squid3 1289 proxy 15u IPv6 14810490 0t0 TCP *:8000 (LISTEN) $ ps -fp 1289 UID PID PPID C STIME TTY TIME CMD proxy 1289 1 0 09:48 ? 00:00:00 /usr/sbin/squid3 -N -f /etc/squid-deb-proxy/squid-deb-proxy.conf I can see right there that squid is the process, but it is actualy my squid-deb-proxy that is taking up the port.
Another good example of a java app:
$ lsof -i :4242 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME java 3075 root 86u IPv4 12019 0t0 TCP *:4242 (LISTEN) $ ps -fp 3075 UID PID PPID C STIME TTY TIME CMD root 3075 1 15 May24 ? 3-16:07:25 /usr/local/crashplan/jre/bin/java -Dfile.encoding=UTF-8 -Dapp=CrashPlanService -DappBaseName=CrashPl You can see in lsof (LiSt Open Files) that it is java, which is less than helpful. Running the ps command with the PID we can see right away that it is CrashPlan.
3 Ways to Find Out Which Process Listening on a Particular Port
A port is a logical entity that represents an endpoint of communication and is associated with a given process or service in an operating system. In previous articles, we explained how to find out the list of all open ports in Linux and how to check if remote ports are reachable using the Netcat command.
In this short guide, we will show different ways of finding the process/service listening on a particular port in Linux.
1. Using netstat Command
netstat (network statistics) command is used to display information concerning network connections, routing tables, interface stats, and beyond. It is available on all Unix-like operating systems including Linux and also on Windows OS.
In case you do not have it installed by default, use the following command to install it.
$ sudo apt-get install net-tools [On Debian/Ubuntu & Mint] $ sudo dnf install net-tools [On CentOS/RHEL/Fedora and Rocky Linux/AlmaLinux] $ pacman -S netstat-nat [On Arch Linux] $ emerge sys-apps/net-tools [On Gentoo] $ sudo dnf install net-tools [On Fedora] $ sudo zypper install net-tools [On openSUSE]
Once installed, you can use it with the grep command to find the process or service listening on a particular port in Linux as follows (specify the port).
In the above command, the flags.
- l – tells netstat to only show listening sockets.
- t – tells it to display tcp connections.
- n – instructs it to show numerical addresses.
- p – enables showing of the process ID and the process name.
- grep -w – shows matching of exact string (:80).
Note: The netstat command is deprecated and replaced by the modern ss command in Linux.
2. Using lsof Command
lsof command (List Open Files) is used to list all open files on a Linux system.
To install it on your system, type the command below.
$ sudo apt-get install lsof [On Debian, Ubuntu and Mint] $ sudo yum install lsof [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/lsof [On Gentoo Linux] $ sudo pacman -S lsof [On Arch Linux] $ sudo zypper install lsof [On OpenSUSE]
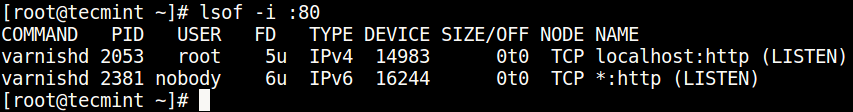
To find the process/service listening on a particular port, type (specify the port).
3. Using fuser Command
fuser command shows the PIDs of processes using the specified files or file systems in Linux.
You can install it as follows:
$ sudo apt-get install psmisc [On Debian, Ubuntu and Mint] $ sudo yum install psmisc [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a sys-apps/psmisc [On Gentoo Linux] $ sudo pacman -S psmisc [On Arch Linux] $ sudo zypper install psmisc [On OpenSUSE]
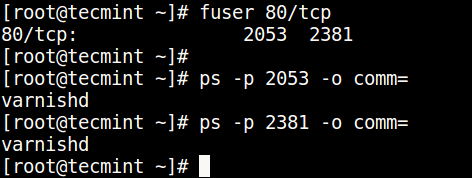
You can find the process/service listening on a particular port by running the command below (specify the port).
Then find the process name using PID number with the ps command like so.
$ ps -p 2053 -o comm= $ ps -p 2381 -o comm=
You can also check out these useful guides about processes in Linux.
You might also like:
That’s all! Do you know of any other ways of finding the process/service listening on a particular port in Linux, let us know via the comment form below.
Check for Listening Ports in Linux
When troubleshooting network connectivity or application-specific issues, one of the first things to check should be what ports are actually in use on your system and which application is listening on a specific port.
This article explains how to use the netstat , ss and lsof commands to find out which services are listening on which ports. The instructions are applicable for all Linux and Unix-based operating systems like macOS.
What is Listening Port
Network port is identified by its number, the associated IP address, and type of the communication protocol, such as TCP or UDP.
Listening port is a network port on which an application or process listens on, acting as a communication endpoint.
Each listening port can be open or closed (filtered) using a firewall. In general terms, an open port is a network port that accepts incoming packets from remote locations.
You can’t have two services listening to the same port on the same IP address.
For example, if you are running an Apache web server that listens on ports 80 and 443 and you try to install Nginx , the later will fail to start because the HTTP and HTTPS ports are already in use.
Check Listening Ports with netstat
netstat is a command-line tool that can provide information about network connections.
To list all TCP or UDP ports that are being listened on, including the services using the ports and the socket status use the following command:
The options used in this command have the following meaning:
- -t — Show TCP ports.
- -u — Show UDP ports.
- -n — Show numerical addresses instead of resolving hosts.
- -l — Show only listening ports.
- -p — Show the PID and name of the listener’s process. This information is shown only if you run the command as root or sudo user.
The output will look something like this:
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 445/sshd tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 929/master tcp6 0 0 . 3306 . * LISTEN 534/mysqld tcp6 0 0 . 80 . * LISTEN 515/apache2 tcp6 0 0 . 22 . * LISTEN 445/sshd tcp6 0 0 . 25 . * LISTEN 929/master tcp6 0 0 . 33060 . * LISTEN 534/mysqld udp 0 0 0.0.0.0:68 0.0.0.0:* 966/dhclient The important columns in our case are:
- Proto — The protocol used by the socket.
- Local Address — The IP Address and port number on which the process listen to.
- PID/Program name — The PID and the name of the process.
If you want to filter the results, use the grep command . For example, to find what process listens on TCP port 22 you would type:
sudo netstat -tnlp | grep :22 The output shows that on this machine port 22 is used by the SSH server:
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 445/sshd tcp6 0 0 . 22 . * LISTEN 445/sshd If the output is empty it means that nothing is listening on the port.
You can also filter the list based on criteria, for example, PID, protocol, state, and so on.
netstat is obsolete and replaced with ss and ip , but still it is of the most used commands to check network connections.
Check Listening Ports with ss
ss is the new netstat . It lacks some of the netstat features, but exposes more TCP states and it is slightly faster. The command options are mostly the same, so the transition from netstat to ss is not difficult.
To get a list of all listening ports with ss you would type:
The output is almost the same as the one reported by netstat :
State Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=445,fd=3)) LISTEN 0 100 0.0.0.0:25 0.0.0.0:* users:(("master",pid=929,fd=13)) LISTEN 0 128 *:3306 *:* users:(("mysqld",pid=534,fd=30)) LISTEN 0 128 *:80 *:* users:(("apache2",pid=765,fd=4),("apache2",pid=764,fd=4),("apache2",pid=515,fd=4)) LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=445,fd=4)) LISTEN 0 100 [::]:25 [::]:* users:(("master",pid=929,fd=14)) LISTEN 0 70 *:33060 *:* users:(("mysqld",pid=534,fd=33)) Check Listening Ports with lsof
lsof is a powerful command-line utility that provides information about files opened by processes.
In Linux, everything is a file. You can think of a socket as a file that writes to the network.
To get a list of all listening TCP ports with lsof type:
sudo lsof -nP -iTCP -sTCP:LISTEN The options used are as follows:
- -n — Do not convert port numbers to port names.
- -p — Do not resolve hostnames, show numerical addresses.
- -iTCP -sTCP:LISTEN — Show only network files with TCP state LISTEN.
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME sshd 445 root 3u IPv4 16434 0t0 TCP *:22 (LISTEN) sshd 445 root 4u IPv6 16445 0t0 TCP *:22 (LISTEN) apache2 515 root 4u IPv6 16590 0t0 TCP *:80 (LISTEN) mysqld 534 mysql 30u IPv6 17636 0t0 TCP *:3306 (LISTEN) mysqld 534 mysql 33u IPv6 19973 0t0 TCP *:33060 (LISTEN) apache2 764 www-data 4u IPv6 16590 0t0 TCP *:80 (LISTEN) apache2 765 www-data 4u IPv6 16590 0t0 TCP *:80 (LISTEN) master 929 root 13u IPv4 19637 0t0 TCP *:25 (LISTEN) master 929 root 14u IPv6 19638 0t0 TCP *:25 (LISTEN) Most of the output columns names are self-explanatory:
- COMMAND , PID , USER — The name, the pid and the user running the program associated with the port.
- NAME — The port number.
To find what process is listening on a particular port, for example, port 3306 you would use:
sudo lsof -nP -iTCP:3306 -sTCP:LISTEN The output shows that MySQL server uses port 3306 :
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME mysqld 534 mysql 30u IPv6 17636 0t0 TCP *:3306 (LISTEN) For more information, visit the lsof man page and read about all other powerful options of this tool.
Conclusion
We have shown you several commands that you can use to check what ports are in use on your system, and how to find what process listens on a specific port.
If you have any questions or remarks, please leave a comment below.