- Saved searches
- Use saved searches to filter your results more quickly
- trustedsec/social-engineer-toolkit
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- Kali Linux: Social Engineering Toolkit
- Social Engineering Attack to gain email access
- STEP 1. SETUP PHISING PAGE
- STEP 2. HUNTING VICTIMS
- In conclusion
- Mastering Social Engineering with the SET: A Comprehensive Guide
- Setup Online to local machine Forwarding for SET Social Engineering Toolkit in Kali Linux
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
The Social-Engineer Toolkit (SET) repository from TrustedSec — All new versions of SET will be deployed here.
trustedsec/social-engineer-toolkit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Allow import cgi on older python versions
Git stats
Files
Failed to load latest commit information.
README.md
The Social-Engineer Toolkit (SET)
The Social-Engineer Toolkit is an open-source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly. SET is a product of TrustedSec, LLC – an information security consulting firm located in Cleveland, Ohio.
DISCLAIMER: This is only for testing purposes and can only be used where strict consent has been given. Do not use this for illegal purposes, period. Please read the LICENSE under readme/LICENSE for the licensing of SET.
Install via requirements.txt
pip3 install -r requirements.txt python3 setup.py
Kali Linux: Social Engineering Toolkit
Humans are the best resource and end-point of security vulnerabilities ever. Social Engineering is a kind of attack targeting human behavior by manipulating and playing with their trust, with the aim to gain confidential information, such as banking account, social media, email, even access to target computer. No system is safe, because the system is made by humans.The most common attack vector using social engineering attacks is spread phishing through email spamming. They target a victim who has a financial account such as banking or credit card information.
Social engineering attacks are not breaking into a system directly, instead it is using human social interaction and the attacker is dealing with the victim directly.
Do you remember Kevin Mitnick? The Social Engineering legend of the old era. In most of his attack methods, he used to trick victims into believing that he holds the system authority. You might have seen his Social Engineering Attack demo video on YouTube. Look at it!
In this post i am going to show you the simple scenario of how to implement Social Engineering Attack in daily life. It is so easy, just follow along the tutorial carefully. I will explain the scenario clearly.
Social Engineering Attack to gain email access
Goal: Gaining email credential account information
Attacker: Me
Target: My friend. (Really? yes)
Device: Computer or laptop running Kali Linux. And my mobile phone!
Environment: Office (at work)
Tool: Social Engineering Toolkit (SET)
So, based on the scenario above you can imagine that we don’t even need the victim’s device, i used my laptop and my phone. I only need his head and trust, and stupidity too! Because, you know, human stupidity can not be patched, seriously!
In this case we first are going to setup phishing Gmail Account login page in my Kali Linux, and use my phone to be a trigger device. Why i used my phone? I will explain below, later.
Fortunately we are not gonna install any tools, our Kali Linux machine has pre-installed SET (Social Engineering Toolkit), That’s all we need. Oh yeah, if you don’t know what is SET is, i will give you the background on this toolkit.
Social Engineering Toolkit, is design to perform human-side penetration test. SET (shortly) is developed by the founder of TrustedSec (https://www.trustedsec.com/social-engineer-toolkit-set/), which is written in Python, and it is open source.
Alright that was enough let’s do the practice. Before we conduct the social engineering attack, we need to set up our phising page first. Here, i am sitting down on my desk, my computer (running Kali Linux) is connected to the internet the same Wi-Fi network as my mobile phone (i am using android).
STEP 1. SETUP PHISING PAGE
Setoolkit is using Command Line interface, so don’t expect ‘clicky-clicky’ of things here. Open up terminal and type:
You will see the welcome page at the top and the attack options at the bottom, you should see something like this.
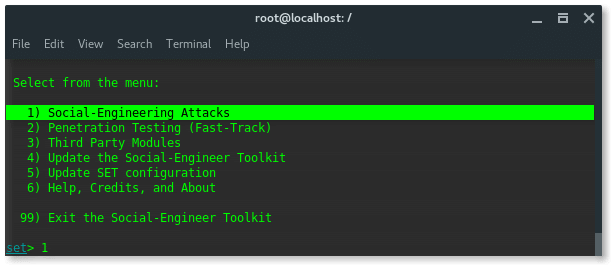
Yes, of course, we are going to perform Social Engineering Attacks, so choose number 1 and hit ENTER.
And then you will be displayed the next options, and choose number 2. Website Attack Vectors. Hit ENTER.
Next, we choose number 3. Credential Harvester Attack Method. Hit Enter.
Further options are narrower, SET has pre-formatted phising page of popular websites, such Google, Yahoo, Twitter and Facebook. Now choose number 1. Web Templates.
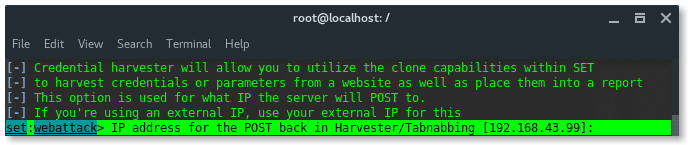
Because, my Kali Linux PC and my mobile phone were in the same Wi-Fi network, so just input the attacker (my PC) local IP address. And hit ENTER.
PS: To check your device IP address, type: ‘ifconfig’
Alright so far, we have set our method and the listener IP address. In this options listed pre-defined web phising templates as i mentioned above. Because we aimed Google account page, so we choose number 2. Google. Hit ENTER.
Now, SET starts my Kali Linux Webserver on port 80, with the fake Google account login page. Our setup is done. Now i am ready walking into my friends room to login into this phishing page using my mobile phone.
STEP 2. HUNTING VICTIMS
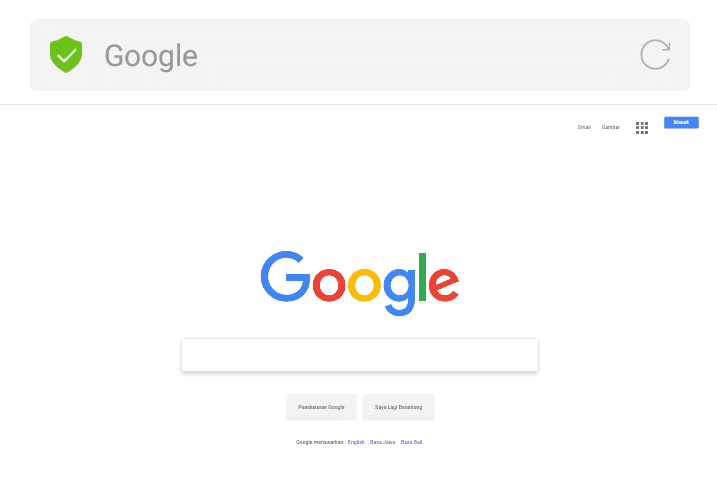
The reason why i am using mobile phone (android)? Let see how the page displayed in my built-in android browser. So, i am accessing my Kali Linux webserver on 192.168.43.99 in the browser. And here is the page:
See? It looks so real, there are no security issues displayed on it. The URL bar showing the title instead the URL itself. We know the stupid will recognize this as the original Google page.
So, i bring my mobile phone, and walk into my friend, and talk to him as if i failed to login to Google and act if I am wondering if Google crashed or errored. I give my phone and ask him to try to login using his account. He doesn’t believe my words and immediately begins typing in his account information as if nothing will happen badly here. Haha.
He already typed all the required forms, and let me to click the Sign in button. I click the button… Now It is loading… And then we got Google search engine main page like this.
PS: Once the victim clicks the Sign in button, it will send the authentication information to our listener machine, and it is logged.
Nothing is happening, i tell him, the Sign In button is still there, you failed to login though. And then i am opening again the phising page, while another friend of this stupid coming to us. Nah, we got another victim.
Until i cut the talk, then i go back to my desk and check the log of my SET. And here we got,
In conclusion
I am not good at story telling (thats the point), to sum up the attack so far the steps are:
- Open ‘setoolkit’
- Choose 1) Social Engineering Attacks
- Choose 2) Website Attack Vectors
- Choose 3) Credential Harvester Attack Method
- Choose 1) Web Templates
- Input the IP address
- Choose Google
- Happy hunting ^_^
Mastering Social Engineering with the SET: A Comprehensive Guide
Mostly SET Social Engineering toolkit is widely used for hacking Facebook, twitter, Instagram, LinkedIn and other social sites by creating fake (Phishing Page). but generally this kit has been developed for social engineering attack. Social engineering toolkit exist in Kali Linux by default.
I saw many people created a phishing page for Facebook hacking by using SET within 5 minutes.
Problem: their page is working only on Local Area Network, If they send this link to the victim through email, chat or other method. The page is not working there.
Those guys read online somewhere “how to hack Facebook account by using Kali Linux”, but they don’t know actual scenario behind it.
But no problem at all, If you are one of them. I will solve your problem and at the end of this article you will be able to make your server accessible on WAN (Wide Area Network). You here because you want to learn more and more. And I never disappointed you.
So Go ahead and read more about SET Social Engineering toolkit.
I have already written article about access your local server on WAN. but I don’t know you have read or not. Here is the link How to ssh port forwarding in router – full guide
So Create a phishing page by using Social Engineering toolkit and forward port to make accessibility of page on WAN.
If you think It is complected and not able to setup all these things then continue reading .. I will describe another easy method for you.
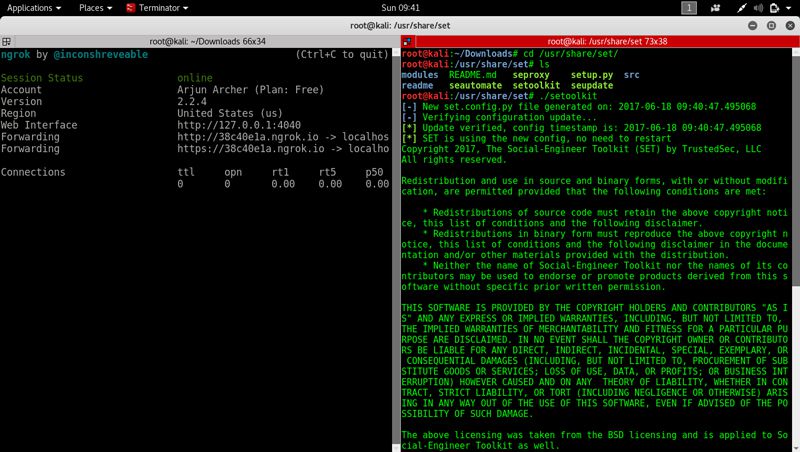
Setup Online to local machine Forwarding for SET Social Engineering Toolkit in Kali Linux
You will follow the given steps to setup forwarding.
- Go on ngrok.com and click on Sign Up
- Fill your detail and register.
- Download ngrok zip file, choose appropriate architecture as per your system (64bit/32bit). otherwise you will face problem.
- Extract the files
- Run terminal and reach at location you have extracted ngrok file.
- After sign up on ngrok.com you will get two commands written there. Execute both commands in sequence.
- Start SET Social Engineering toolkit
Select 1 > 2 > 3 > 2 options after starting toolkit and hit enter after pressing each key. - It will ask for IP Address, Copy forwarding link generated by ngrok and paste here.
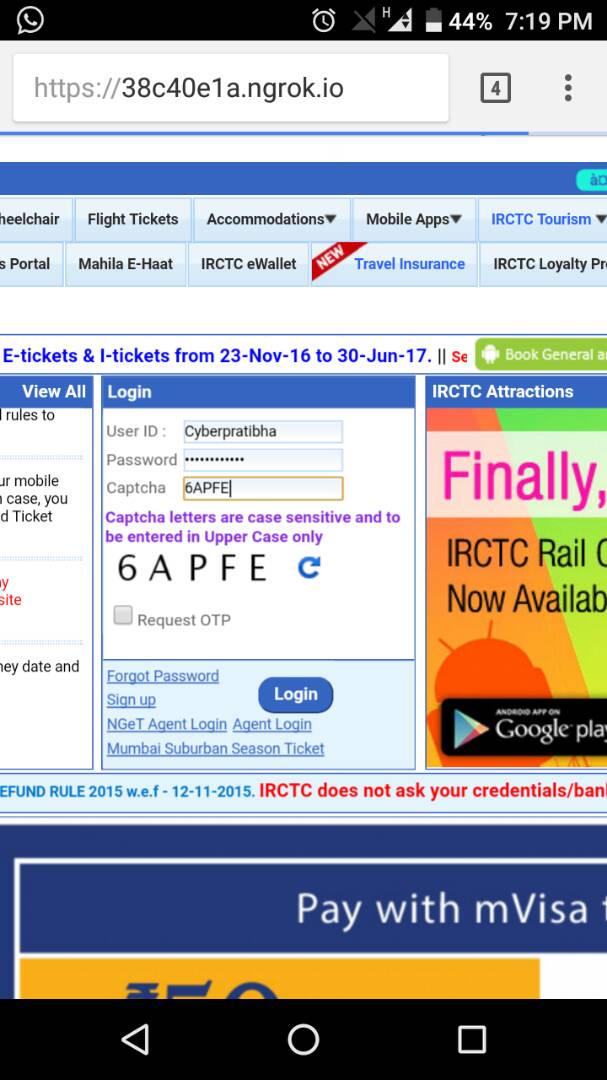
- Give the website name you want to create phishing page.
- Send link to victim and wait for logging him/her
- After Login
I hope you like this article if you have any question comment in box.