- Packages and Binaries:
- Kali Linux: Social Engineering Toolkit
- Social Engineering Attack to gain email access
- STEP 1. SETUP PHISING PAGE
- STEP 2. HUNTING VICTIMS
- In conclusion
- Social engineering toolkit кали линукс
- Learn Latest Tutorials
- Preparation
- Trending Technologies
- B.Tech / MCA
- Javatpoint Services
- Training For College Campus
Packages and Binaries:
The Social-Engineer Toolkit (SET) is an open-source Python-driven tool aimed at penetration testing around Social-Engineering.
Installed size: 48.50 MB
How to install: sudo apt install set
- aircrack-ng
- ettercap-common
- libapache2-mod-php
- metasploit-framework
- nginx
- openssl
- python3
- python3-impacket
- python3-openssl
- python3-paramiko
- python3-pefile
- python3-pexpect
- python3-pil
- python3-pycryptodome
- python3-pymssql
- python3-qrcode
- python3-requests
- upx-ucl
se-toolkit
[email protected]:~# se-toolkit -h The se-toolkit command is deprecated. Use the setoolkit command to launch the Social-Engineer Toolkit. setoolkit
[email protected]:~# setoolkit -h [-] New set.config.py file generated on: 2023-05-24 12:05:55.633222 [-] Verifying configuration update. [*] Update verified, config timestamp is: 2023-05-24 12:05:55.633222 [*] SET is using the new config, no need to restart Copyright 2020, The Social-Engineer Toolkit (SET) by TrustedSec, LLC All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution. * Neither the name of Social-Engineer Toolkit nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. The above licensing was taken from the BSD licensing and is applied to Social-Engineer Toolkit as well. Note that the Social-Engineer Toolkit is provided as is, and is a royalty free open-source application. Feel free to modify, use, change, market, do whatever you want with it as long as you give the appropriate credit where credit is due (which means giving the authors the credit they deserve for writing it). Also note that by using this software, if you ever see the creator of SET in a bar, you should (optional) give him a hug and should (optional) buy him a beer (or bourbon - hopefully bourbon). Author has the option to refuse the hug (most likely will never happen) or the beer or bourbon (also most likely will never happen). Also by using this tool (these are all optional of course!), you should try to make this industry better, try to stay positive, try to help others, try to learn from one another, try stay out of drama, try offer free hugs when possible (and make sure recipient agrees to mutual hug), and try to do everything you can to be awesome. The Social-Engineer Toolkit is designed purely for good and not evil. If you are planning on using this tool for malicious purposes that are not authorized by the company you are performing assessments for, you are violating the terms of service and license of this toolset. By hitting yes (only one time), you agree to the terms of service and that you will only use this tool for lawful purposes only. Do you agree to the terms of service [y/n]: Kali Linux: Social Engineering Toolkit
Humans are the best resource and end-point of security vulnerabilities ever. Social Engineering is a kind of attack targeting human behavior by manipulating and playing with their trust, with the aim to gain confidential information, such as banking account, social media, email, even access to target computer. No system is safe, because the system is made by humans.The most common attack vector using social engineering attacks is spread phishing through email spamming. They target a victim who has a financial account such as banking or credit card information.
Social engineering attacks are not breaking into a system directly, instead it is using human social interaction and the attacker is dealing with the victim directly.
Do you remember Kevin Mitnick? The Social Engineering legend of the old era. In most of his attack methods, he used to trick victims into believing that he holds the system authority. You might have seen his Social Engineering Attack demo video on YouTube. Look at it!
In this post i am going to show you the simple scenario of how to implement Social Engineering Attack in daily life. It is so easy, just follow along the tutorial carefully. I will explain the scenario clearly.
Social Engineering Attack to gain email access
Goal: Gaining email credential account information
Attacker: Me
Target: My friend. (Really? yes)
Device: Computer or laptop running Kali Linux. And my mobile phone!
Environment: Office (at work)
Tool: Social Engineering Toolkit (SET)
So, based on the scenario above you can imagine that we don’t even need the victim’s device, i used my laptop and my phone. I only need his head and trust, and stupidity too! Because, you know, human stupidity can not be patched, seriously!
In this case we first are going to setup phishing Gmail Account login page in my Kali Linux, and use my phone to be a trigger device. Why i used my phone? I will explain below, later.
Fortunately we are not gonna install any tools, our Kali Linux machine has pre-installed SET (Social Engineering Toolkit), That’s all we need. Oh yeah, if you don’t know what is SET is, i will give you the background on this toolkit.
Social Engineering Toolkit, is design to perform human-side penetration test. SET (shortly) is developed by the founder of TrustedSec (https://www.trustedsec.com/social-engineer-toolkit-set/), which is written in Python, and it is open source.
Alright that was enough let’s do the practice. Before we conduct the social engineering attack, we need to set up our phising page first. Here, i am sitting down on my desk, my computer (running Kali Linux) is connected to the internet the same Wi-Fi network as my mobile phone (i am using android).
STEP 1. SETUP PHISING PAGE
Setoolkit is using Command Line interface, so don’t expect ‘clicky-clicky’ of things here. Open up terminal and type:
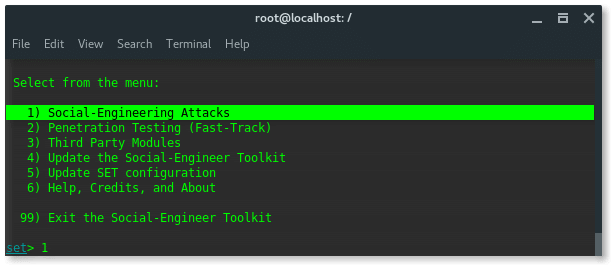
You will see the welcome page at the top and the attack options at the bottom, you should see something like this.
Yes, of course, we are going to perform Social Engineering Attacks, so choose number 1 and hit ENTER.
And then you will be displayed the next options, and choose number 2. Website Attack Vectors. Hit ENTER.
Next, we choose number 3. Credential Harvester Attack Method. Hit Enter.
Further options are narrower, SET has pre-formatted phising page of popular websites, such Google, Yahoo, Twitter and Facebook. Now choose number 1. Web Templates.
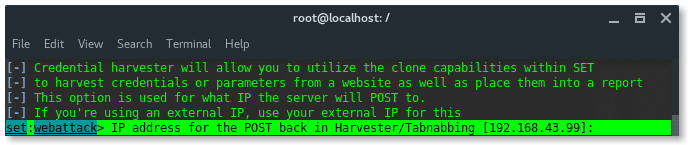
Because, my Kali Linux PC and my mobile phone were in the same Wi-Fi network, so just input the attacker (my PC) local IP address. And hit ENTER.
PS: To check your device IP address, type: ‘ifconfig’
Alright so far, we have set our method and the listener IP address. In this options listed pre-defined web phising templates as i mentioned above. Because we aimed Google account page, so we choose number 2. Google. Hit ENTER.
Now, SET starts my Kali Linux Webserver on port 80, with the fake Google account login page. Our setup is done. Now i am ready walking into my friends room to login into this phishing page using my mobile phone.
STEP 2. HUNTING VICTIMS
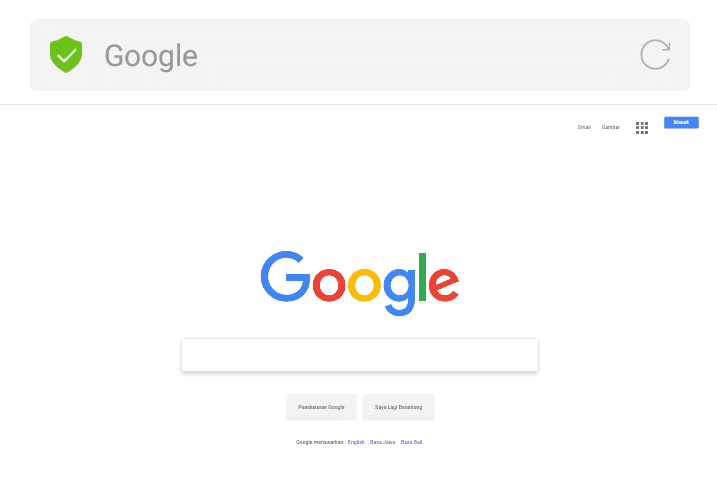
The reason why i am using mobile phone (android)? Let see how the page displayed in my built-in android browser. So, i am accessing my Kali Linux webserver on 192.168.43.99 in the browser. And here is the page:
See? It looks so real, there are no security issues displayed on it. The URL bar showing the title instead the URL itself. We know the stupid will recognize this as the original Google page.
So, i bring my mobile phone, and walk into my friend, and talk to him as if i failed to login to Google and act if I am wondering if Google crashed or errored. I give my phone and ask him to try to login using his account. He doesn’t believe my words and immediately begins typing in his account information as if nothing will happen badly here. Haha.
He already typed all the required forms, and let me to click the Sign in button. I click the button… Now It is loading… And then we got Google search engine main page like this.
PS: Once the victim clicks the Sign in button, it will send the authentication information to our listener machine, and it is logged.
Nothing is happening, i tell him, the Sign In button is still there, you failed to login though. And then i am opening again the phising page, while another friend of this stupid coming to us. Nah, we got another victim.
Until i cut the talk, then i go back to my desk and check the log of my SET. And here we got,
In conclusion
I am not good at story telling (thats the point), to sum up the attack so far the steps are:
- Open ‘setoolkit’
- Choose 1) Social Engineering Attacks
- Choose 2) Website Attack Vectors
- Choose 3) Credential Harvester Attack Method
- Choose 1) Web Templates
- Input the IP address
- Choose Google
- Happy hunting ^_^
Social engineering toolkit кали линукс
Learn Latest Tutorials
Preparation
Trending Technologies
B.Tech / MCA
Javatpoint Services
JavaTpoint offers too many high quality services. Mail us on h[email protected], to get more information about given services.
- Website Designing
- Website Development
- Java Development
- PHP Development
- WordPress
- Graphic Designing
- Logo
- Digital Marketing
- On Page and Off Page SEO
- PPC
- Content Development
- Corporate Training
- Classroom and Online Training
- Data Entry
Training For College Campus
JavaTpoint offers college campus training on Core Java, Advance Java, .Net, Android, Hadoop, PHP, Web Technology and Python. Please mail your requirement at [email protected].
Duration: 1 week to 2 week
Like/Subscribe us for latest updates or newsletter