How to view, setup and analyze sshd(Secure shell daemon) logs in redhat or centos linux ?
In this article, we will look how to view, analyze and setup SSHD logs on our Redhat or Centos Linux system.
1. Viewing SSHD Log file.
## For Ubuntu [root@nglinux ~]# ls -l /var/log/auth.log ls: cannot access /var/log/auth.log: No such file or directory ## For Redhat or Centos [root@nglinux ~]# ls -l /var/log/secure -rw-------. 1 root root 0 May 30 20:36 /var/log/secure
2. Check out the logs in logfile
[root@nglinux ~]# cat /var/log/secure [root@nglinux ~]#
We can see there are no logs in the file.
It seems the SSH logging is disabled on the server .
Lets check it out.
[root@nglinux ~]# cat /etc/ssh/sshd_config | grep -iA 4 logging # Logging # obsoletes QuietMode and FascistLogging #SyslogFacility AUTH SyslogFacility AUTHPRIV #LogLevel INFO
In above output, we can see “Loglevel INFO” is commented out, due to which the logging is not captured.
3. Setup SSH Log: Enable logging and restart service.
## Uncomment Loglevel line below [root@nglinux ~]# cat /etc/ssh/sshd_config | grep -iA 4 logging # Logging # obsoletes QuietMode and FascistLogging #SyslogFacility AUTH SyslogFacility AUTHPRIV LogLevel INFO [root@nglinux ~]# [root@nglinux ~]# vim /etc/ssh/sshd_config [root@nglinux ~]# ## And then restart the service. [root@nglinux ~]# service sshd reload Reloading sshd: [ OK ]
4. Verify if logs started to appear in Log file.
[root@nglinux ~]# cat /var/log/secure May 31 01:54:09 localhost sshd[1796]: Received SIGHUP; restarting. May 31 01:54:09 localhost sshd[28471]: Server listening on 0.0.0.0 port 22. May 31 01:54:09 localhost sshd[28471]: Server listening on :: port 22. [root@nglinux ~]#
5. Understanding ssh login attempt history
[root@nglinux ~]# cat /var/log/secure May 31 01:54:09 localhost sshd[1796]: Received SIGHUP; restarting. May 31 01:54:09 localhost sshd[28471]: Server listening on 0.0.0.0 port 22. May 31 01:54:09 localhost sshd[28471]: Server listening on :: port 22. May 31 01:56:48 localhost sshd[4267]: Received disconnect from 172.21.49.223: 11: disconnected by user --> Logged out the session. May 31 01:56:48 localhost sshd[4267]: pam_unix(sshd:session): session closed for user root May 31 01:56:52 localhost sshd[28476]: Accepted password for root from 172.21.49.223 port 57163 ssh2 ---> User login from IP 172.21.49.223 via port 57163 May 31 01:56:53 localhost sshd[28476]: pam_unix(sshd:session): session opened for user root by (uid=0) May 31 01:56:53 localhost sshd[28480]: lastlog_openseek: Couldn't stat /var/log/lastlog: No such file or directory May 31 01:56:53 localhost sshd[28480]: lastlog_openseek: Couldn't stat /var/log/lastlog: No such file or directory May 31 01:56:54 localhost sshd[28476]: Received disconnect from 172.21.49.223: 11: disconnected by user May 31 01:56:54 localhost sshd[28476]: pam_unix(sshd:session): session closed for user root May 31 01:56:56 localhost unix_chkpwd[28504]: password check failed for user (root) ----> wrong password entered by user. May 31 01:56:56 localhost sshd[28502]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=172.21.49.223 user=root May 31 01:56:58 localhost sshd[28502]: Failed password for root from 172.21.49.223 port 57164 ssh2 May 31 01:57:00 localhost sshd[28502]: Accepted password for root from 172.21.49.223 port 57164 ssh2 May 31 01:57:00 localhost sshd[28502]: pam_unix(sshd:session): session opened for user root by (uid=0) May 31 01:57:00 localhost sshd[28507]: lastlog_openseek: Couldn't stat /var/log/lastlog: No such file or directory May 31 01:57:00 localhost sshd[28507]: lastlog_openseek: Couldn't stat /var/log/lastlog: No such file or directory
“SyslogFacility AUTH” logs the messages into /var/log/messages.
“SyslogFacility AUTHPRIV” logs the messages into separate file, /var/log/secure in our case.
syslog.conf or rsyslog.conf file mentions the filename as shown below.
/etc/rsyslog.conf:45:authpriv.*
[root@nglinux ~]# cat /etc/ssh/sshd_config | grep -iA 4 logging # Logging # obsoletes QuietMode and FascistLogging #SyslogFacility AUTH SyslogFacility AUTHPRIV LogLevel INFO
How to Check the sshd Logs in Linux?
“The sshd stands for Secure Shell Daemon. It’s a silent process that listens to all the authentication and login attempts of Linux. As soon as you start your system, the process begins.
Using sshd logs, you can monitor authorized and unauthorized login attempts on your system. This helps in keeping your system secure.
Today, we will explore how to dive into sshd logs on Ubuntu 22.04. We have presented two ways to access the sshd logs. This tutorial uses easy-to-follow Linux commands to see sshd logs. By the end of this tutorial, you will be able to explore sshd logs on your own.”
Without any further ado, let’s get started!
Guide
Following are the two ways you can check sshd logs on Ubuntu 22.04:
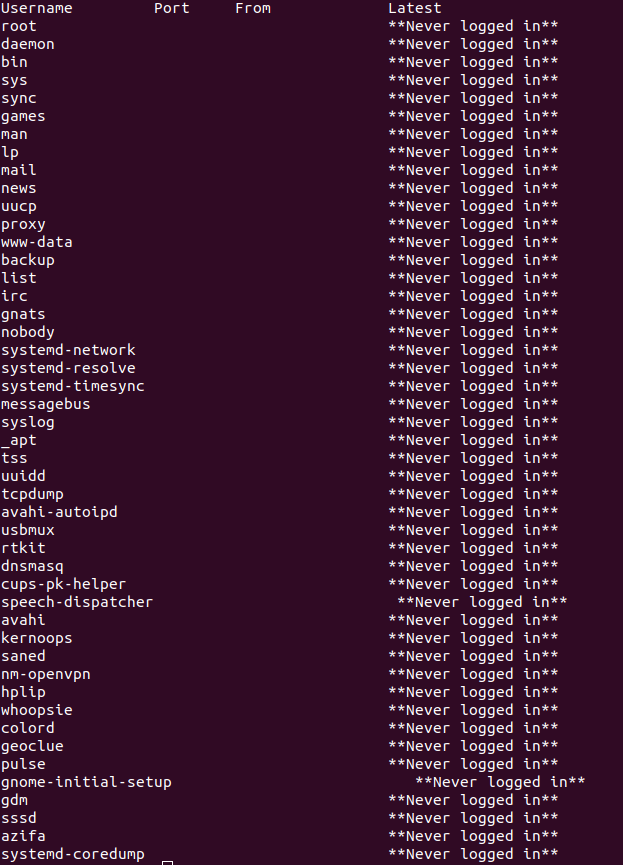
Method 1: Check SSHD Logs Using the “lastlog” Command
We make use of this method when we only want to see the login logs using sshd. To see the logs, run the lastlog command on the command line (Terminal) as shown below:
Once the command is executed, you will see all the login-related logs on your screen, as shown in the image below:
Method 2: Check SSHD Logs Using auth.log
We make use of this method when we not only want to see logs of login attempts but also all the sshd logs. To see these logs, first go to the log directory following the path /var/log. Here, there is a file with the name auth.log that keeps all the sshd logs.
To see the logs, use the cat command as shown below:
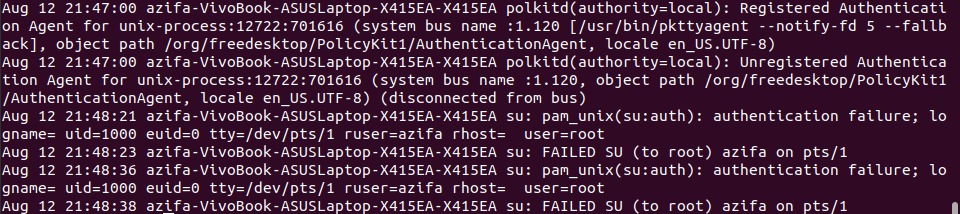
This will present to you all the sshd logs like this:
If you run into an error while accessing the auth.log file, try accessing it with root privileges. Use sudo with the cat command, and it will grant you access to the sshd logs.
Conclusion
In today’s guide, we saw in detail how to access sshd logs in Ubuntu 22.04. You saw how we could see login attempt logs using a basic Linux command. Later, we also explored how to see all the sshd logs kept in the auth.log file. Every time you try to make a new connection, share a file, or attempt to authenticate yourself, the auth.log file gets updated. Using these logs, you can monitor the security of your system to some extent by keeping an eye on the authorized and unauthorized login attempts.
We hope you liked the tutorial.
About the author
Karim Buzdar
Karim Buzdar holds a degree in telecommunication engineering and holds several sysadmin certifications. As an IT engineer and technical author, he writes for various web sites. He blogs at LinuxWays.
Logging SSH access attempts
I’ve configured an ubuntu server with openssh in order to connect to it and execute commands from a remote system like a phone or a laptop. The problem is. I’m probably not the only one. Is there a way to know all the login attempts that have been made to the server?
You should also consider running sshd on a non-standard port. Also, it is possible to set up iptables to deny new connection attempts if a single IP attempts a new ssh connection X times in a minute.
8 Answers 8
On Ubuntu servers, you can find who logged in when (and from where) in the file /var/log/auth.log . There, you find entries like:
May 1 16:17:02 owl CRON[9019]: pam_unix(cron:session): session closed for user root May 1 16:17:43 owl sshd[9024]: Accepted publickey for root from 192.168.0.101 port 37384 ssh2 May 1 16:17:43 owl sshd[9024]: pam_unix(sshd:session): session opened for user root by (uid=0) @JoelDavis My Ubuntu 12.04 does, but the output is a single line that doesn’t look like your output at all. Maybe it needs to be configure.
On Red Hat based distros such as Fedora/CentOS/RHEL you can check for the users logged in inside the file /var/log/secure .
@Anthon, surprisingly I do not have /var/log/auth in my systems. That’s why before posting the answer, I checked if I had /var/log/secure in my system, which is also a Ubuntu server 🙂
I had checked 14.04, 12.04 and and old machine under 8.04. Which version are you running? Done anything special to get that file?
@Anthon, turns out the server in which I tested was RHEL. However, the answer in the link that I had provided was for Ubuntu which seems weird, since you had checked 3 variations of ubuntu and there is no /var/log/secure .
Note that the default configuration on Ubuntu is to NOT log ssh logins to the /var/log/auth file. This is the INFO logging level.
If you want to have it include login attempts in the log file, you’ll need to edit the /etc/ssh/sshd_config file (as root or with sudo) and change the LogLevel from INFO to VERBOSE .
After that, restart the sshd daemon with
sudo service rsyslog restart After that, the ssh login attempts will be logged into the /var/log/auth.log file.
On Ubuntu you can log in via SSH and use the Linux tail command to display the last x number of lines of your /var/log/auth.log file. When you’re logged in via SSH use the following command to view 100 last lines of your SSH log:
tail -100 /var/log/auth.log | grep 'sshd' Wouldn’t an even cleaner way be: grep sshd /var/log/auth.log | tail -100 ? That way you know you’re getting 100 sshd auth event items if there are 100 or more, unlike your commands.
My recommendation is to use auditd. This is logging using the linux kernel’s audit subsystem and in my opinion the proper way to do it if you are serious. And given the nature of the question you should be using PAM as well. At the default level of just having auditd and PAM installed, you should automatically be getting all successful and unsuccessful SSH attempts logged in your audit.log file. So you really don’t have to configure anything, just have auditd and PAM installed. I know this first hand for SLES. And would bet RHEL and any other enterprise version of linux would operate similarly.
within the raw audit log generated by auditd you can use either use something like aureport to filter it which is described in the auditd man pages, write your own text parser, or just use VI and search for keywords.
here is an except of my /var/log/audit/audit.log file with me ssh’ing into my linux server.
node=shark type=CRED_DISP msg=audit(1480622612.317:2211277): user pid=117768 uid=0 auid=23456 ses=2201 msg='op=PAM:setcred acct="ron" exe="/usr/sbin/sshd" (hostname=abc415.mycompany.us, addr=172.16.152.5, terminal=ssh res=success)' - from the above, my server name is shark.
- many lines like this are in audit.log, I want this one based on exe=»/usr/sbin/sshd»
- the uid of the account being ssh’d into is the value of auid, which is 23456 for this example
- the name of the user account associated with auid is specified by acct=»ron»
- most times the audit system will record the dns hostname of the system trying to connect, but it always has it’s ip address
- the date of the entry which is in epoch time, so you’ll have to convert that via something like date —date @1480622612.317 which results in Thu Dec 1 15:03:32 EST 2016 and is when I ssh’d into my server.
When res=failed is when you want to investigate those ip addresses and hostnames to see what systems were trying to connect, under what attempted user name. And obviously the successful ssh attempts to understand what’s happening on your system — for example your coworker bob who sits at same desk everyday with hostname=bobscomputer and ip address=192.168.5.5; if you see a successful ssh attempt at 2am yesterday under his username from ip address 10.10.5.6 for example then it might be in your best interest to talk to bob to investigate. Possible hack attempt by someone else? And shortly after are there su attempts to root in audit log from bob’s account?
when you see repetitive res=failed and auid=0 and acct=root then that’s someone trying to ssh into your box into the root account, and is when you modify /etc/hosts.deny with that IP address for SSHD.