- Installing and Configuring OpenSSH on Ubuntu and Debian-based Distributions
- Enable SSH on Ubuntu and Debian with OpenSSH
- Check if SSH is already enabled and running
- Installing OpenSSH on Ubuntu and Debian
- Installing OpenSSH for desktop or end users
- Installing OpenSSH for servers
- Controlling the SSH daemon sshd (for servers)
- Start the sshd service
- Stop the sshd service
- Restart the sshd service
- Enable SSH on Ubuntu automatically at each boot
- Disable SSH auto start on reboot
- Configuring SSH (for servers)
- 1. Change the default SSH port
- 2. Disable root login via SSH
- 3. Allow SSH Key-Based Authentication on
- How to Start and Enable SSHD Service in OpenSUSE Linux
- How to Start and Enable SSHD Service in OpenSUSE Linux
- 1. How to Start SSHD Service on OpenSUSE Linux
- 2. How to Enable SSHD Service on OpenSUSE Linux
- 3. How to Stop SSHD Service on OpenSUSE Linux
- 4. How to Check Status of SSHD Service on OpenSUSE Linux
Installing and Configuring OpenSSH on Ubuntu and Debian-based Distributions
Here’s how to enable SSH on Ubuntu and Debian based Linux distributions. Also learn how to properly configure the SSH daemon on a Linux server to allow remote logins.
If you want to enable SSH on Ubuntu desktop, use the following command:
sudo apt install openssh-client
If you want to enable SSH on Ubuntu server, use the following command:
sudo apt install openssh-server
Read the rest of the article for more detailed information.
Every system admin and developer has experienced the need for remote logins into the systems for quicker administration and debugging purposes.
In an IT environment, almost all the sysadmin tasks these days are performed via remote logins.
And not just sysadmins, even normal users sometimes need to remote login to the servers.
So how do you remotely connect to a Linux system? There are multiple tools available for remote logins but when it comes to Linux, SSH is the most popular choice.
SSH, short for secure shell, is a protocol that allows remote login securely from one computer to another.
Now the question is how do you enable SSH on Ubuntu or Debian or any other Linux distributions you are using?
Remember that SSH is only a protocol and this can protocol can be implemented via a number of tools such as lsh, Dropbear etc., but the most widely used tool for SSH is the open source software OpenSSH.
In this tutorial, you’ll see how to install OpenSSH and configure it to enable SSH on Ubuntu and Debian based Linux distributions. The steps mentioned are applicable to both desktop and server versions of Ubuntu/Debian.
I also advise reading this article to get acquainted with the basics of SSH.
Enable SSH on Ubuntu and Debian with OpenSSH
As I mentioned earlier, OpenSSH is the software for making SSH logins. It listens on a port and authenticates the incoming users and creates a new shell for the remote user.
For SSH to work, an ssh server needs to be running on the remote system to which the user needs to log in. You also need to have an ssh client in the local system from which the user will log into the remote system.
OpenSSH provides both of these functionalities. There is openssh-client for end-users and openssh-server for the remote servers.
Before you install OpenSSH, you should check if SSH is already installed and running on your system.
Check if SSH is already enabled and running
It’s more likely that SSH is already enabled on your system. To verify, run the following command on either of the remote server or the end user system:
If SSH is enabled, you should see an information about SSH agent on your desktop:
ps -aux | grep ssh abhishek 1736 0.0 0.0 11304 36 ? Ss 08:18 0:00 /usr/bin/ssh-agent /usr/bin/im-launch env GNOME_SHELL_SESSION_MODE=ubuntu gnome-session --session=ubuntu abhishek 10462 0.0 0.0 21536 1044 pts/0 S+ 10:15 0:00 grep --color=auto sshOn the server, you should see the information about a SSH daemon running:
ps -aux | grep ssh root 920 0.0 0.2 72296 6028 ? Ss 2018 0:17 /usr/sbin/sshd -D root 22708 0.0 0.3 108172 7364 ? Ss 05:13 0:00 sshd: [email protected]/0 root 22873 0.0 0.0 14856 1068 pts/0 S+ 05:14 0:00 grep --color=auto sshIf you don’t see an output similar to the ones mentioned above, you don’t have SSH running on your system. It’s time to install OpenSSH.
Installing OpenSSH on Ubuntu and Debian
A quick note about openssh-client and openssh-server before you go on installing OpenSSH.
openssh-client: This is the package you need if you want to connect to a remote Linux system using SSH. This is what you need as the end-user/desktop user.
openssh-server: This is the package you need if you want to allow remote logins via SSH to your system. This is what you need on your Linux server.
Note that installing openssh-server also enables you to remote login to other systems via SSH. In other words, openssh-server consists openssh-client. But if you are just an end user with a Linux desktop, there is (mostly) no need to install openssh-server and allow remote login to your system.
Now that you know the difference between the two, it’s time to see how to install them.
Note that to install OpenSSH on Ubuntu or Debian, you need to have sudo/root rights. If you don’t have such permission, contact your system administrator. You may also read this article about creating sudo users.
Installing OpenSSH for desktop or end users
If you just want to connect to other remote systems over SSH, you should install the openssh-client package using the following command:
sudo apt update sudo apt install openssh-clientOnce you have installed ssh on your system, you are read to use it. Please refer to this detailed article to know how to use SSH.
Installing OpenSSH for servers
If you are setting up an Ubuntu/Debian server, should install the openssh-server package so that other remote users can connect to your system.
sudo apt update sudo apt install openssh-serverOnce you have installed openssh-server, it’s time to learn how to tweak it and configure it as per your need.
Controlling the SSH daemon sshd (for servers)
You’ll have the SSH daemon named sshd installed and enabled to be started on reboot automatically by default. systemctl is one of the several ways to control the SSH daemon. To know more about systemctl, please refer to this article.
Start the sshd service
The service can be started by simply issuing:
sudo systemctl start sshdStop the sshd service
The service can be stopped in a similar way:
Restart the sshd service
If you want the sshd service to be stopped and started (usually needed in the case of changing configurations to sshd service), you can simply use this command:
sudo systemctl restart sshdEnable SSH on Ubuntu automatically at each boot
Some services need to be started on rebooting itself to avoid manual interaction and if it is very frequently used. It is very essential for services like Apache, mongod, mysqld, sshd in servers.
If you want to enable such auto start for sshd, use:
sudo systemctl enable sshdDisable SSH auto start on reboot
If you don’t want the sshd to be started on reboot automatically, use
sudo systemctl disable sshdAbove said four tips are necessary whenever you make a change to the ssh service such as changing the port. You can make use of the above commands to manage any service (like mysqld, mongod, apache) with the service name sshd replaced with the target service.
Configuring SSH (for servers)
As of now, our ssh service will be listening on port 22 and ready to authenticate any user (also root) once a key is stored.
If you want to change any of the configurations such as port to listen for connections, you can edit the file “/etc/ssh/sshd_config” by adding, deleting, commenting or uncommenting the lines and then restart the sshd service.
There are many options to configure. I have created a list of configurations that will be most likely needed.
1. Change the default SSH port
Usually, the sshd service listens on TCP port 22. If you want, you can change the SSH port to say 5678 by adding/editing the following line in /etc/ssh/ssh_config.
Restart the service to see the change immediately.
2. Disable root login via SSH
Allowing root users to authenticate by ssh is not a good idea due to security reasons. sudo users can be logged in remote but not root as root is in the top of security food chain.
Root Login can be disabled by adding (if not already present) the following line and restarting the service.
If the line is already present, then ensure it is not commented out.
3. Allow SSH Key-Based Authentication on
You may want to allow ssh key-based authentication so that end user won’t have to enter the password all the time. Just using the ssh [email protected] will be enough for logging into the remote system.
For this, you should configure SSH to allow public key authentication:
If the line is already present, then ensure it is not commented out.
Now if you want to allow a particular system to log in via public key, you need to add that public key of the end user in the file .ssh/authorized_keys.
You can make ssh keys (public key and private key) with the help of ssh-keygen. To know more about key-gen, refer to this great resource.
You can transfer the public key of the end-user to the remote server by any means you prefer. You may use scp command if you like or simply get it via FTP. It’s really up to you.
Above three are most needed, but if you want to change further, please refer the manpage of sshd_config.
I think that’s a good enough reading material to know how to enable SSH on Ubuntu/Debian and how to configure SSH on your server for remote logins.
In a related article, you can refer to this article detailing a SSH error that arises due to copying public key between systems.
If you found this article useful, Share it with your friends. If you have any suggestions or comments or if you think I missed something, feel free to drop a comment below.
How to Start and Enable SSHD Service in OpenSUSE Linux
In this article, I will show you how to start and enable sshd service in OpenSUSE Linux. Sometimes when you try to connect your Server through ssh protocol on Port 22, you won’t be able to connect because sshd service is not yet started or not running. Even if you start the sshd service and then if you restart your server and try to again connect your server on ssh port 22 then you find that you are again not able to connect. This happens when you forgot to enable your service. In this article, I will guide you through the steps to start and enable sshd service so that you can connect your server even after restart.
How to Start and Enable SSHD Service in OpenSUSE Linux
1. How to Start SSHD Service on OpenSUSE Linux
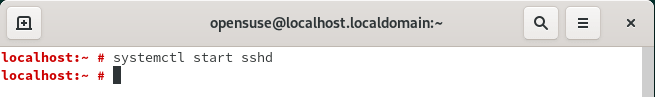
To start sshd service on OpenSUSE Linux you need to use systemctl start sshd command as shown below. Alternatively you can also use service sshd start command to start the sshd service.
2. How to Enable SSHD Service on OpenSUSE Linux
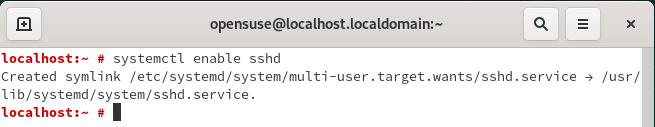
To enable sshd service on OpenSUSE Linux you need to use systemctl enable sshd command as shown below. After enabling the service if you reboot the Server it will start automatically. You don’t have to manually start the Service after every reboot.
3. How to Stop SSHD Service on OpenSUSE Linux
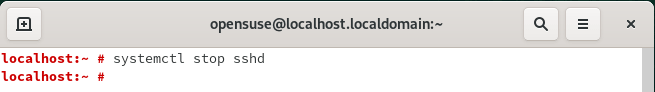
To Stop sshd service on OpenSUSE Linux you need to use systemctl stop sshd command as shown below. Alternatively you can also use service sshd stop command to stop the sshd service.
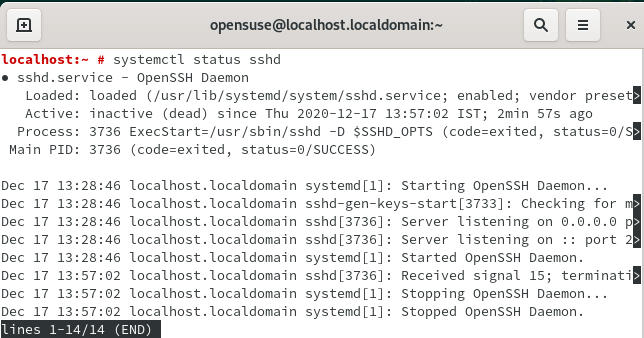
4. How to Check Status of SSHD Service on OpenSUSE Linux
To check the status of sshd service on OpenSUSE Linux you need to use systemctl status sshd command as shown below. Alternatively you can also use service sshd status command to check the sshd service status.
If you see any error during sshd service restart then you need to open and check your ssh configuration file using your favourite editor as shown below. SSH Configuration file can usually be found in /etc/ssh/sshd_config file. You can check more about sshd config on SSH Man Page.
localhost:~ # vi /etc/ssh/sshd_config # $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options override the # default value. Port 22 #AddressFamily any #ListenAddress 0.0.0.0 #ListenAddress :: #HostKey /etc/ssh/ssh_host_rsa_key #HostKey /etc/ssh/ssh_host_ecdsa_key #HostKey /etc/ssh/ssh_host_ed25519_key # Ciphers and keying #RekeyLimit default none # Logging #SyslogFacility AUTH #LogLevel INFO # Authentication: #LoginGraceTime 2m PermitRootLogin yes #StrictModes yes #MaxAuthTries 6 #MaxSessions 10
To check sshd process if it is running or not you can use pgrep sshd command as shown below.
localhost:~ # pgrep sshd 1246 6554
Alternatively, you can also check the sshd process by using ps -ef | grep -i sshd | grep -v grep command as shown below.
localhost:~ # ps -ef | grep -i sshd | grep -v grep root 1246 1 0 Dec17 ? 00:00:00 /usr/sbin/sshd -D root 6554 1246 0 09:52 ? 00:00:00 sshd: root@pts/1
If you want to check all the options set in the sshd_config file then you can invoke sshd command with -T option and check that as shown below. This option is used to test the sshd configuration.
localhost:~ # sshd -T port 22 addressfamily any listenaddress [::]:22 listenaddress 0.0.0.0:22 usepam yes logingracetime 120 x11displayoffset 10 maxauthtries 6 maxsessions 10 clientaliveinterval 0 clientalivecountmax 3 streamlocalbindmask 0177 permitrootlogin yes ignorerhosts yes ignoreuserknownhosts no hostbasedauthentication no hostbasedusesnamefrompacketonly no
Popular Recommendations:-