- Linux OS Service ‘named’
- Service Control
- Configuration
- How to use the Linux BIND command to install and configure DNS
- How DNS works
- Great Linux resources
- Where does DNS get IP addresses?
- Forward and reverse lookups
- Install and configure DNS
- Configure the /etc/named.conf file
- Define the forward and reverse zones
- Create forward and reverse zone files
- Add the nameserver IP to /etc/resolv.conf
- Start/restart and enable the named service
- Verify the DNS name resolution
- Query with nslookup
- Query with dig
- Wrap up
Linux OS Service ‘named’
The named service executes the DNS (Dynamic Name Service) server daemon. It converts host names to IP addresses and vice versa. There are several different kinds of DNS servers, such as primary server, slave server and cached server etc. Its data is stored in the directory /var/named.
The Domain Name System (DNS) is the hierarchical, distributed database. It stores information for mapping Internet host names to IP addresses and vice versa, mail routing information, and other data used by Internet applications.
The data stored in the DNS is identified by domain names that are organized as a tree according to organizational or administrative boundaries. Each node of the tree, called a domain, is given a label. The domain name of the node is the concatenation of all the labels on the path from the node to the root node. This is represented in written form as a string of labels listed from right to left and separated by dots. A label need only be unique within its parent domain.
For administrative purposes, the name space is partitioned into areas called zones, each starting at a node and extending down to the leaf nodes or to nodes where other zones start. The data for each zone is stored in a name server, which answers queries about the zone using the DNS protocol
Clients look up information in the DNS by calling a resolver library, which sends queries to one or more name servers and interprets the responses. The BIND 9 software distribution contains both a name server and a resolver library. This service is not usually used on a server because most servers are not designated to be DNS servers. An organisation typically only implements a small number of DNS servers. For DNS client use, just configure /etc/resolve.conf – this daemon is not needed for DNS clients.
Service Control
This service is handled by init.d script /etc/init.d/named. Its usage is as follows:
# /sbin/service named Usage: /etc/init.d/named
Start the service as follows:
# /sbin/service named start Starting named: [ OK ]
Stop the service as follows:
# /sbin/service named stop Stopping named: [ OK ]
Check if the serivce is started or stopped:
Restart the service like this:
# /sbin/service named restart Stopping named: [ OK ] Starting named: [ OK ]
If the service is started, then restart it; otherwise do nothing.
# /sbin/service named condrestart Stopping named: [ OK ] Starting named: [ OK ]
# /sbin/service named reload Reloading named: [ OK ]
Probe the service status using /usr/sbin/rndc command
# service named probe start
Query runlevel information for the service:
# /sbin/chkconfig --list named named 0:off 1:off 2:off 3:off 4:off 5:off 6:off
Configuration
The named service is complex to describe in detail here. /etc/named.conf is the configuration file for named. Statements are enclosed in braces and terminated with a semi-colon. Clauses in the statements are also semi-colon terminated. Below is an example named.conf file.
# cat /etc/named.conf // // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // // See the BIND Administrator's Reference Manual (ARM) for details about the // configuration located in /usr/share/doc/bind-/Bv9ARM.html options < listen-on port 53 < 127.0.0.1; >; listen-on-v6 port 53 < ::1; >; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query < localhost; >; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; >; logging < channel default_debug < file "data/named.run"; severity dynamic; >; >; zone "." IN < type hint; file "named.ca"; >; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
How to use the Linux BIND command to install and configure DNS
The Domain Name System helps you get where you want to be on the internet. Make sure you know what it is and how to set up, configure, and test it.
The Domain Name System (DNS) is used to resolve (translate) hostnames to internet protocol (IP) addresses and vice versa. A DNS server, also known as a nameserver, maps IP addresses to hostnames or domain names.
In this article, you will learn the basics of DNS, from how DNS gets the IP address and hostname, to the concepts of forward and reverse lookup zones. It will also show you how to install and configure DNS, define and edit zone files, and verify whether the DNS can resolve to the correct address with the help of commands. If you are new to DNS, this article will help you play with it on your system using basic configurations.
How DNS works
When a client requests information from a nameserver, it usually connects to port 53, and then the nameserver resolves the name requested.
Great Linux resources
Where does DNS get IP addresses?
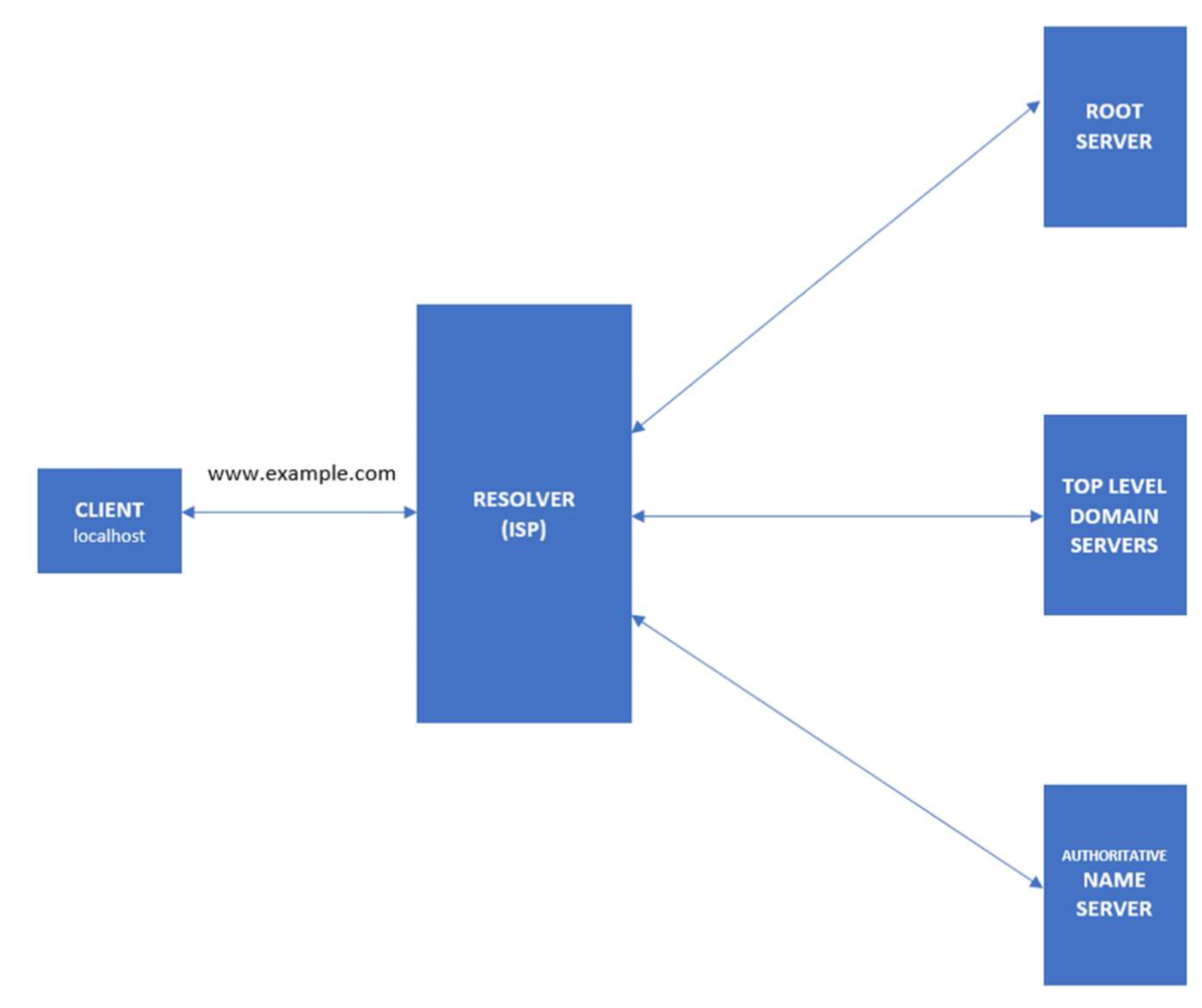
You might wonder how DNS gets the IP of the corresponding hostname or domain name. How does DNS search among different IP addresses and associate your domain name correctly? Who stores those mappings between domain names and IP addresses?
The DNS workflow illustrates how communication happens within DNS and how it resolves the addresses.
- When the client searches for the domain www.example.com , the request will initially go to the internet service provider’s (ISP) resolver. It will respond to the user’s request to resolve a domain name.
- If the IP address is not found on the resolver, the request is forwarded to a root DNS server and later to the top-level domain (TLD) servers.
- TLD servers store information for top-level domains, such as .com or .net.
- Requests are forwarded to the nameservers, which know detailed information about domains and IP addresses.
- Nameservers respond to the ISP’s resolver, and then the resolver responds to the client with the requested IP.
- When the resolver doesn’t know the IP, it stores the IP and its domain in a cache to service future queries.
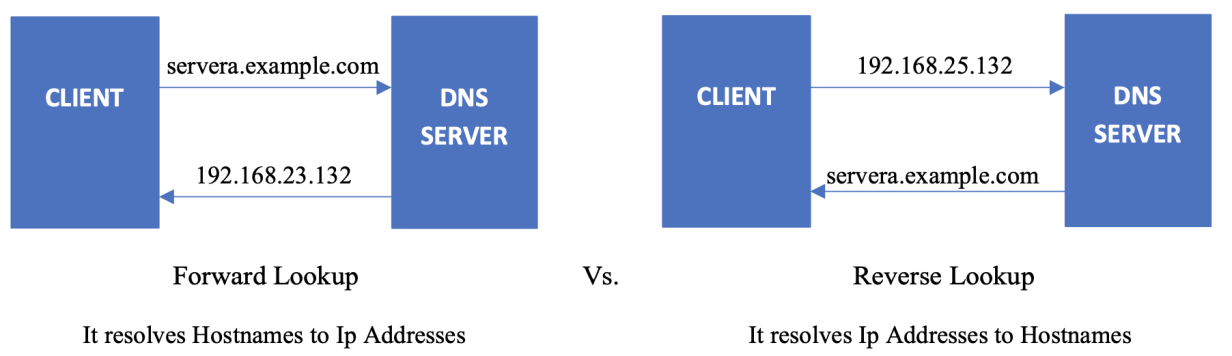
Forward and reverse lookups
The forward lookup zone uses the domain name to search for IP addresses, whereas the reverse lookup zone uses IP addresses to search for the domain name.
Install and configure DNS
BIND is a nameserver service responsible for performing domain-name-to-IP conversion on Linux-based DNS servers.
[root@servera ~] # yum install bindThe BIND package provides the named service. It reads the configuration from the /etc/named and /etc/named.conf files. Once this package is installed, you can start configuring DNS.
Configure the /etc/named.conf file
First, add or edit the two values in the options field. One is the DNS server address, and the other is the allow-query to any.
[root@servera ~] # vim /etc/named.conf listen-on port 53 < 127.0.0.1; 192.168.25.132; >; allow-query < localhost; any; >;Here are the values from the above file:
- 192.168.25.132 – DNS server address
- any – matches every IP address
Define the forward and reverse zones
Define the forward and reverse zones in the /etc/named.conf or /etc/named.rfc1912.zones (you can define zones in either of those files). In this example, I am appending zone definition details to the /etc/named.rfc1912.zones file.
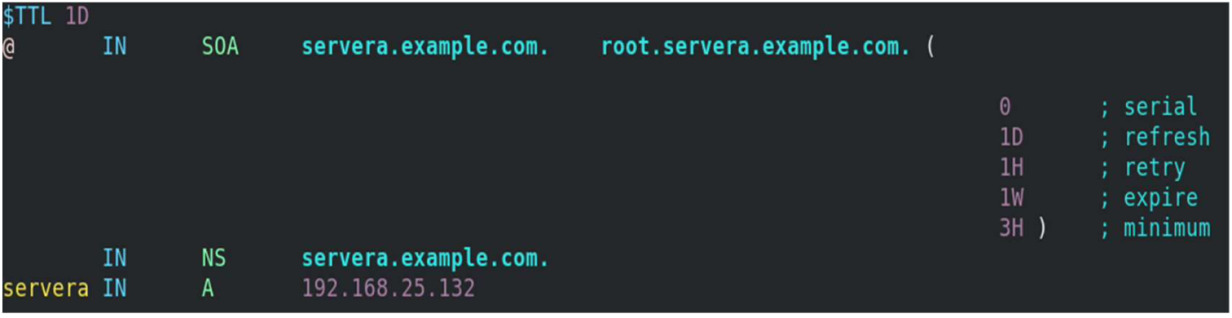
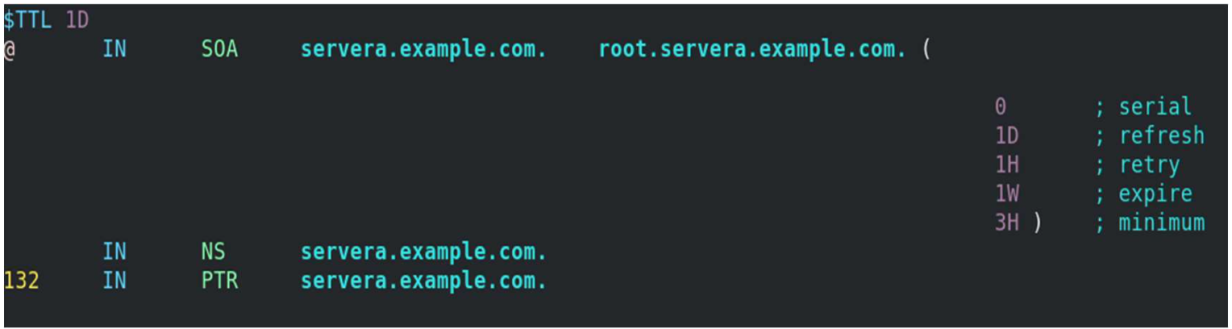
[root@servera ~] # vim /etc/named.rfc1912.zones zone "example.com" IN < type master; file "example.forward.zone"; allow-update < none; >; >; zone "25.168.192.in-addr.arpa" IN < type master; file "example.reverse.zone"; allow-update < none; >; >; Create forward and reverse zone files
You also need to create forward and reverse zone files in the /var/named directory.
Note: By default, the named.conf file includes the /var/named directory for checking zone files. Sample zone files named.localhost and named.loopback are created during the installation of the BIND package.
[root@servera ~] # vim /var/named/example.forward.zone[root@servera ~] # vim /var/named/example.reverse.zoneAdd the nameserver IP to /etc/resolv.conf
First, you must disable DNS processing by NetworkManager because it dynamically updates the /etc/resolv.conf file with DNS settings from its active connection profiles. To disable this and allow manual editing of /etc/resolv.conf , you must create a file (For example, 90-dns-none.conf ), as root in the /etc/NetworkManager/conf.d/ directory that contains the following:
Save the file and reload (restart) NetworkManager.
# systemctl reload NetworkManagerAfter you reload NetworkManager, it won’t update /etc/resolv.conf . Now, you can manually add the nameserver’s IP address to the /etc/resolv.conf file.
[root@servera ~] # vim /etc/resolv.conf # Generated by NetworkManager search localdomain example.com nameserver 192.168.25.132[ Be prepared in case something goes wrong. Read An introduction to DNS troubleshooting. ]
Start/restart and enable the named service
If the named service is not running or is disabled, then start and enable it. If it is already active (running) and you made all these configurations, you need to restart the service to make changes.
[root@servera ~] # systemctl status named.service [root@servera ~] # systemctl start named.service [root@servera ~] # systemctl enable named.service [root@servera ~] # systemctl restart named.service Verify the DNS name resolution
You have installed the BIND package, configured named files, created lookup zones, and restarted the service to make configurations take effect. Now use the nslookup and dig commands to check whether DNS is working properly and verify whether you are getting the intended results.
- nslookup is a program to query internet domain name servers.
- dig is a tool for interrogating DNS servers. It performs DNS lookups and displays the answers that are returned from the nameserver.
Query with nslookup
[root@servera ~] # nslookup servera.example.com Server: 192.168.25.132 Address: 192.168.25.132#53 Name: servera.example.com Address: 192.168.25.132 [root@servera ~] # nslookup 192.168.25.132 132.25.168.192.in-addr.arpa name = servera.example.com.Query with dig
Here is a forward lookup, where DNS responds with 192.168.11.132 as an IP for servera.example.com:
[root@servera ~] # dig servera.example.com . output truncated. ;; ANSWER SECTION: servera.example.com. 86400 IN A 192.168.25.132 ;; AUTHORITY SECTION: example.com. 86400 IN NS servera.example.com. . output truncated. This example displays a reverse lookup, where the DNS server responds with servera.example.com as the domain name for 192.168.25.132:
[root@servera ~] # dig -x 192.168.25.132 . output truncated. ;; ANSWER SECTION: 132.25.168.192.in-addr.arpa. 86400 IN PTR servera.example.com. ;; AUTHORITY SECTION: 25.168.192.in-addr.arpa. 86400 IN NS servera.example.com. ;; ADDITIONAL SECTION: servera.example.com. 86400 IN A 192.168.25.132 . output truncated. [ Network getting out of control? Check out Network automation for everyone, a free book from Red Hat. ]
Wrap up
In this article, you learned what DNS is and how it works. Also, you now know what forward and reverse lookup zones are and how they work. You also learned how to install the BIND package, which is responsible for setting up DNS on the system and configuring the named files and lookup zones. Finally, you learned two commands, nslookup and dig , to interrogate DNS resolutions.