- How to Test Port [TCP/UDP] Connectivity from a Linux Server
- Testing TCP port connectivity with telnet
- Using nc command to test TCP port connectivity
- Testing UDP port connectivity wit nc command
- Some more articles you might also be interested in …
- Telnet to a Specific Port for Testing Purposes
- Checking ports before starting:
- Getting started with Telnet to specific ports for testing purposes:
- About Telnet:
- Bonus: testing specific ports for possible vulnerabilities with Nmap:
- Scanning a specific port to find vulnerabilities on the service:
- About the author
- David Adams
- How to Use telnet Command in Linux?
- Installing Telnet in Different Linux Distributions
- CentOS, Fedora, and RHEL
- Ubuntu and Debian-Based Distributions
- How to Use telnet in Linux
- Check for Open Ports
- Download Web Page to File
- Test SMTP Communication
- Connect to Remote System
How to Test Port [TCP/UDP] Connectivity from a Linux Server
Here is a short post to check port [TCP/UDP] connectivity from a Linux server. A TCP/IP network connection may be either blocked, dropped, open, or filtered. These actions are generally controlled by the IPtables firewall the system uses and is independent of any process or program that may be listening on a network port.
Telnet and nc are common tools used to test port connectivity from Linux server. Telnet can be used to test tcp port connections, where as nc can be used to test both tcp/udp ports connectivity. Make sure telnet and nc tools are installed on the Linux server you are trying to test connectivity.
# yum install nc # yum install telnet
Testing TCP port connectivity with telnet
Lets see how we can use telnet command to test the TCP port connectivity. The syntax to use the telnet command is as follows:
# telnet [hostname/IP address] [port number]
Example of successful connection:
# telnet 192.168.12.10 22 Trying 192.168.12.10. Connected to 192.168.12.10. Escape character is '^]'. SSH-2.0-OpenSSH_6.6.1 Protocol mismatch. Connection closed by foreign host.
Example of unsuccessful connection:
# telnet 192.168.12.10 22 Trying 192.168.12.10. telnet: connect to address 192.168.12.10: No route to host
Using nc command to test TCP port connectivity
The syntax to use nc command for testing TCP post connectivity is as follows:
# nc -z -v [hostname/IP address] [port number]
Example of successful connection:
# nc -z -v 192.168.10.12 22 Connection to 192.118.20.95 22 port [tcp/ssh] succeeded!
Example of unsuccessful connection:
# nc -z -v 192.168.10.12 22 nc: connect to 192.118.20.95 port 22 (tcp) failed: No route to host
Testing UDP port connectivity wit nc command
The syntax to test UDP port connectivity with nc command is as follows:
# nc -z -v -u [hostname/IP address] [port number]
Example of successful connection:
# nc -z -v -u 192.168.10.12 123 Connection to 192.118.20.95 123 port [udp/ntp] succeeded!
Some more articles you might also be interested in …
Telnet to a Specific Port for Testing Purposes
Telnet is both a protocol allowing us to access a remote device to control it and the program used to connect through this protocol. The Telnet protocol is the “cheap” version of ssh, unencrypted, vulnerable to sniffing and Man In the Middle attacks, by default the Telnet port must be closed.
The telnet program, which is not the Telnet protocol, can be useful to test port states which is the functionality this tutorial explains. The reason why this protocol is useful to connect to different protocols such as POP is both protocols support plain text (which is their main problem and why such services should not be used).
Checking ports before starting:
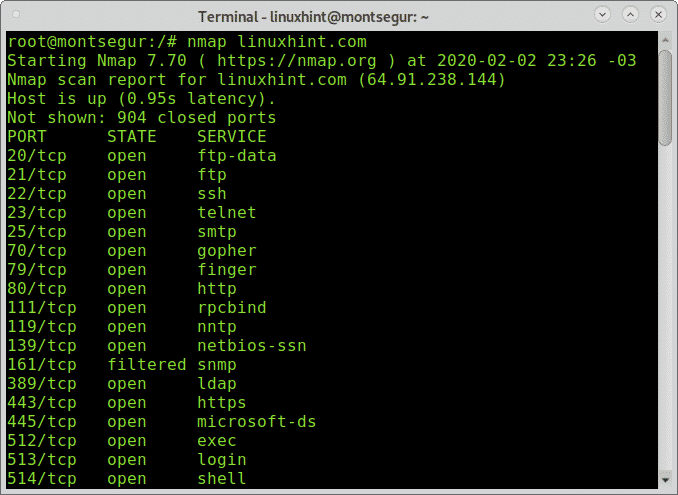
Before starting with telnet, let’s check with Nmap some ports on the sample target (linuxhint.com).
Getting started with Telnet to specific ports for testing purposes:
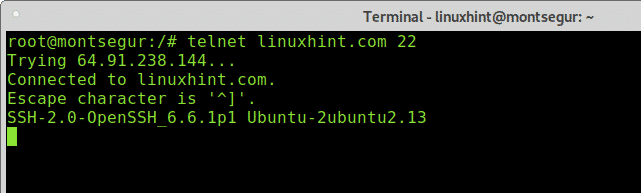
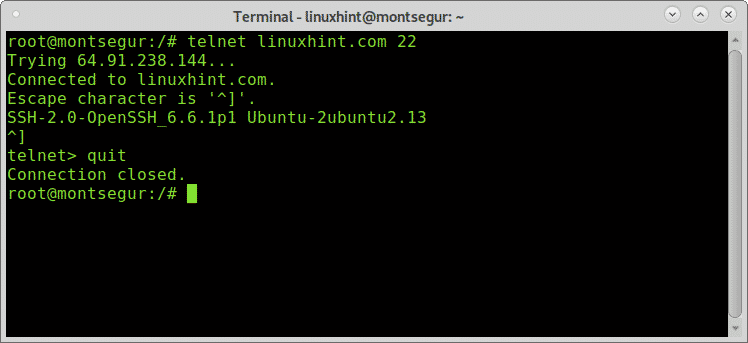
Once we learned about open ports, we can start launching tests, let’s try the port 22 (ssh), on the console write “telnet ” as shown below:
As you can see in the example below the output says I’m connected to linuxhint.com, therefore the port is open.
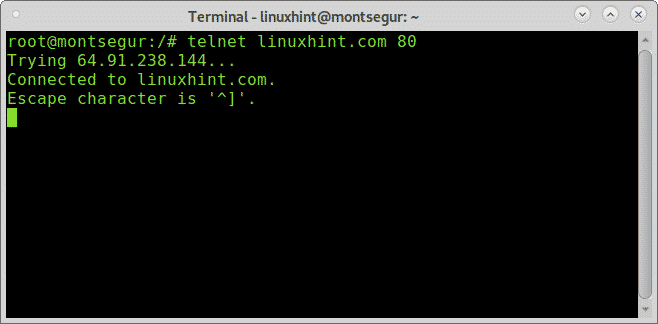
Let’s try the same on the port 80 (http):
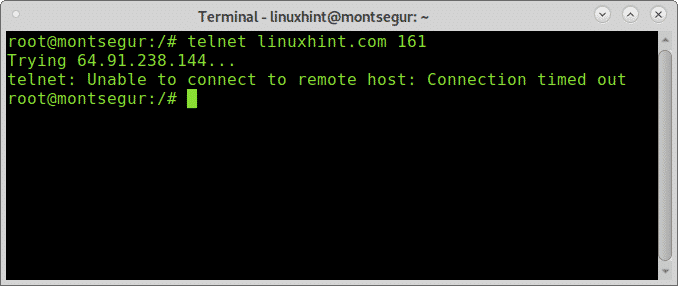
The output is similar with port 80, now let’s try the port 161 which according to Nmap is filtered:
As you see the filtered port didn’t allow the connection to be established returning a time out error.
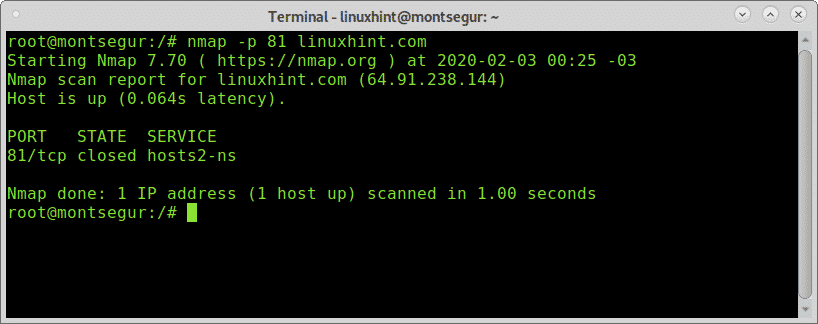
Now let’s try Telnet against a closed (not filtered) port, for this example I will use the port 81. Since Nmap didn’t report on closed ports before proceeding I will confirm it is closed, by scanning the specific port using the -p flag:
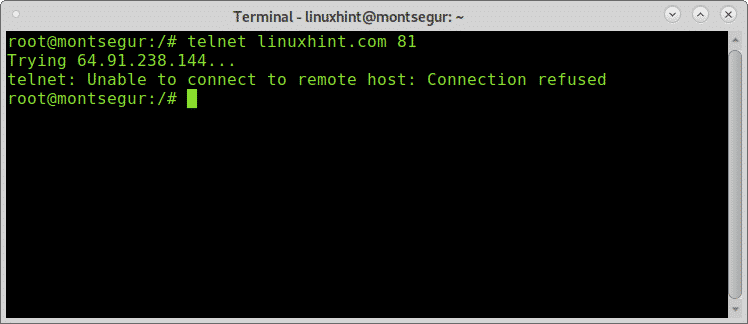
Once confirmed the port is closed, let’s test it with Telnet:
As you can see the connection wasn’t established and the error is different than with the filtered port showing “Connection refused”.
To close an established connection, you can press CTRL+] and you will see the prompt:
Then type “quit” and press ENTER.
Under Linux you can easily write a little shell script to connect through telnet with different targets and ports.
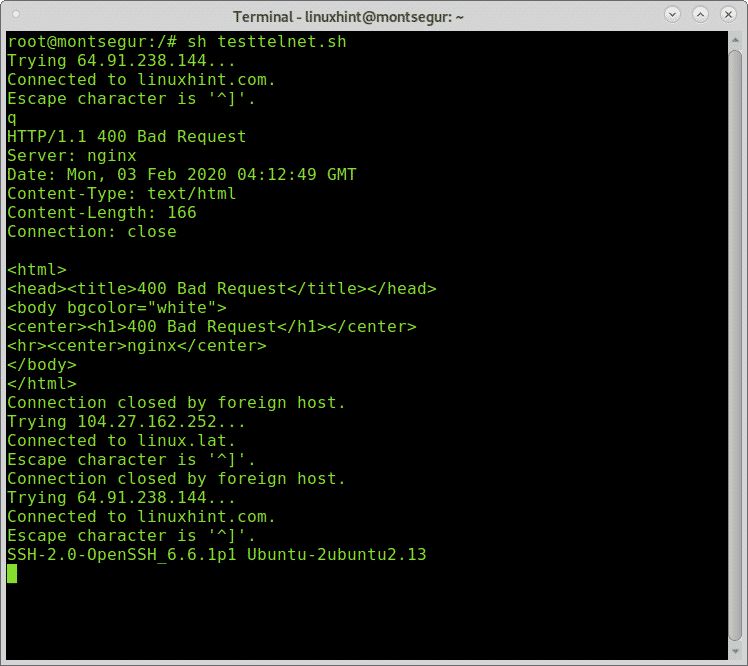
Open nano and create a file called multipletelnet.sh with the following content inside:
#! /bin/bash #The first uncommented line will connect to linuxhint.com through port $ telnet linuxhint.com 80 #The second uncommented line will connect to linux.lat through ssh. telnet linux.lat 22 #The third uncommented line will connect to linuxhint.com through ssh telnet linuxhint.com 22
Connections only start after the previous was closed, you can close the connection by passing any character, In the example above I passed “q”.
Yet, if you want to test many ports and targets simultaneously Telnet isn’t the best option, for which you have Nmap and similar tools
About Telnet:
As said before, Telnet is an unencrypted protocol vulnerable to sniffers, any attacker can intercept the communication between the client and the server in plain text accessing sensible information such as passwords.
The lack of authentication methods also allow possible attackers to modify the packages sent between two nodes.
Because of this Telnet was rapidly replaced by SSH (Secure Shell) which provides a variety of authentication methods and also encrypts the whole communication between nodes.
Bonus: testing specific ports for possible vulnerabilities with Nmap:
With Nmap we can go far more than with Telnet, we can learn the version of the program running behind the port and we can even test it for vulnerabilities.
Scanning a specific port to find vulnerabilities on the service:
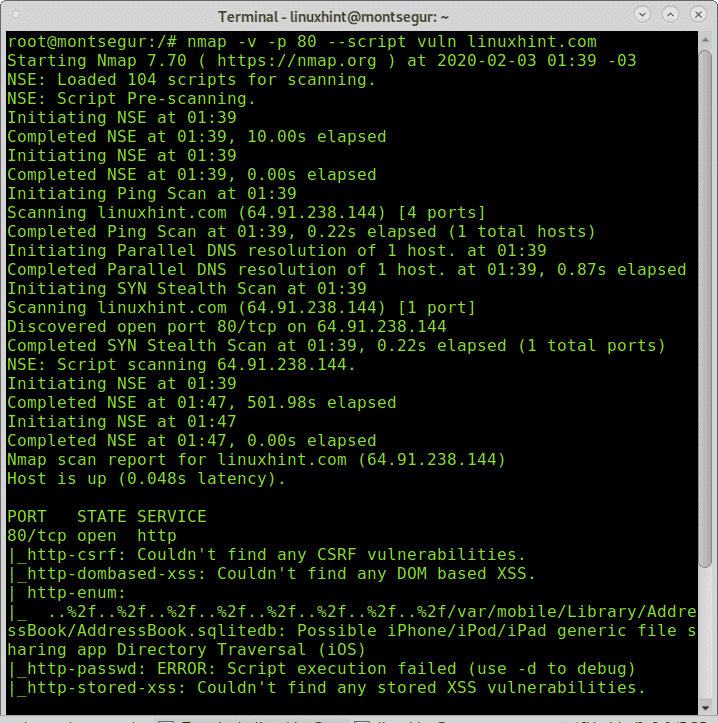
The following example shows a scan against the port 80 of linuxhint.com calling Nmap NSE script vuln to test offensive scripts looking for vulnerabilities:
As you can see, since it is LinuxHint.com server no vulnerabilities were found.
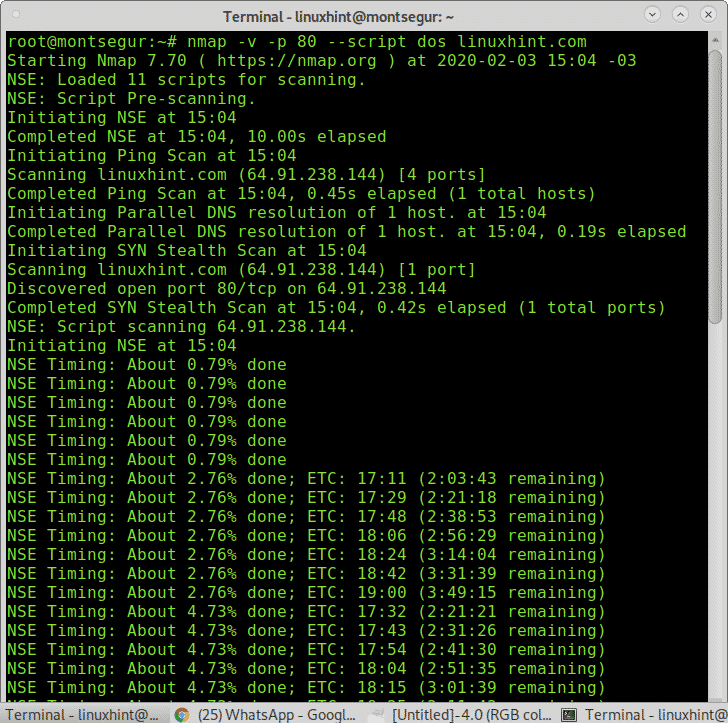
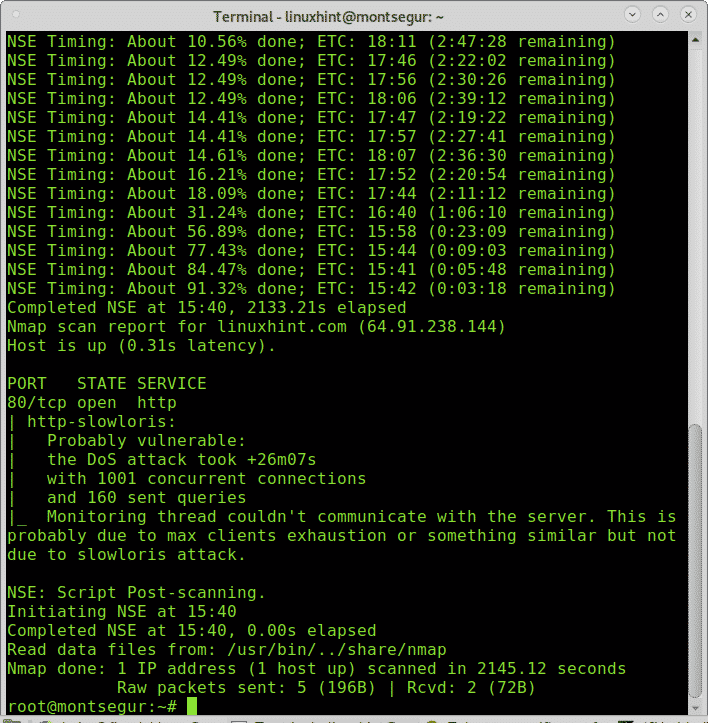
It is possible to scan a specific port for a specific vulnerability; the following example shows how to scan a port using Nmap to find DOS vulnerabilities:
As you can see Nmap found a possible vulnerability (it was a false positive in this case).
You can find a lot of high quality tutorials with different port scanning techniques at https://linuxhint.com/?s=scan+ports.
I hope you found this tutorial on Telnet to a specific port for testing purposes useful. Keep following LinuxHint for more tips and updates on Linux and networking
About the author
David Adams
David Adams is a System Admin and writer that is focused on open source technologies, security software, and computer systems.
How to Use telnet Command in Linux?
Home » Networking » How to Use telnet Command in Linux?
The telnet command (short for teletype network) utilizes the telnet network protocol to connect to remote machines and manage them through a TCP/IP network. The protocol uses port 23 to establish a connection and provides a way to manage remote systems using the CLI.
Although telnet is similar to SSH, the two are different because SSH is a much more secure option as it uses encryption. telnet , on the other hand, sends data without encryption, making it an easy target for hackers.
In this tutorial, you will learn to use the telnet command in Linux.
- A system running Linux (for Windows users, learn about telnet on Windows).
- An account with root privileges.
- Access to the terminal (Ctrl+Alt+T).
Installing Telnet in Different Linux Distributions
Depending on the Linux distribution you are using, follow the steps below to download and install telnet .
CentOS, Fedora, and RHEL
CentOS, Fedora, and RHEL use yum (Yellowdog Update Manager) as the primary package manager. Follow the steps below:
1. Update the system package repository to make sure the latest version is installed:
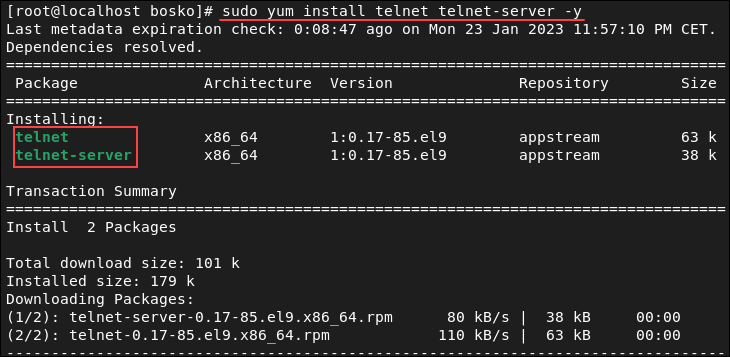
2. Run the following commands to install telnet and the telnet server packages required for it to function properly:
sudo yum install telnet telnet-server -yThe command installs the two packages. The -y flag automatically answers Yes to any prompts during the installation.
3. After the installation completes, start and enable the telnet service by running:
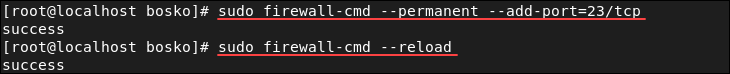
systemctl start telnet.socket systemctl enable telnet.socket4. Allow the telnet port (the default port is 23) through the firewall on the remote machine. Run the following command:
sudo firewall-cmd --permanent --add-port=23/tcp5. Reload the firewall to apply the changes:
The telnet port is now allowed through the firewall.
Ubuntu and Debian-Based Distributions
Ubuntu and other Debian-based distributions use the apt package manager by default. Follow the steps below to install telnet :
1. Update the system package repository:
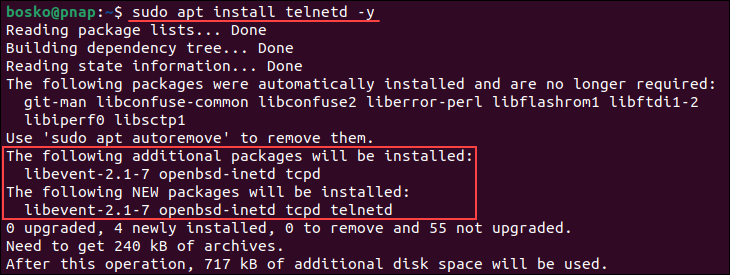
2. Run the following command to install telnet :
sudo apt install telnetd -yWait for the installation to complete. The service should start automatically.
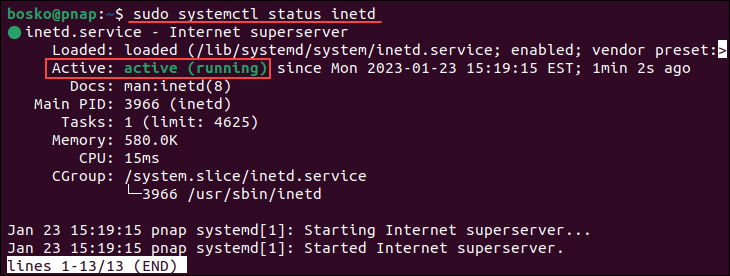
3. Check if telnet is properly installed by running:
sudo systemctl status inetdThe output shows that the daemon is up and running.
4. Allow port 23 through the firewall on the remote machine by running:
The telnet port is now allowed through the firewall.
Note: The command above is for the ufw firewall. If you are using a different firewall, follow the instructions for that specific program.
How to Use telnet in Linux
A vital prerequisite for using telnet is to have it installed on both the local and remote machine, and that the default port 23 is allowed through the firewall on the remote machine.
The syntax for the telnet command is:
telnet [options] [remote_server_address] [port]The [options] and [port] parameters are optional. For [remote_server_address] , telnet accepts symbolic and numeric addresses.
Running the command without options or without specifying an address opens the telnet interactive mode:
Use the interactive shell to connect to remote servers, print the connection status, etc.
To end a session and exit telnet , run:
The sections below provide practical telnet use case examples.
Check for Open Ports
Although it is not a secure option for establishing a remote connection, telnet is a great way to check if a specific port is open on a server. Check if a certain port is answering any calls by specifying the port number in the command. Doing so allows you to see what’s going on in a network and if a port is responsive or not.
1. Use the following syntax:
telnet [server_address] [port]2. Not specifying a port number defaults to port 23. For example, to check if port 22 is open on a server, run:
The connection breaks, which means that the specified port is not open.
3. However, trying port 80 yields a different result:
The output shows that the port is open since the connection was established.
Download Web Page to File
telnet allows users to connect to port 80 of a website and download the HTML source code to the terminal. This allows you to save and inspect the source code, check it for errors, etc.
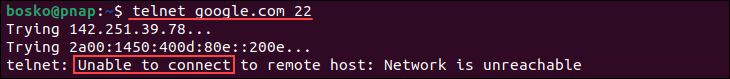
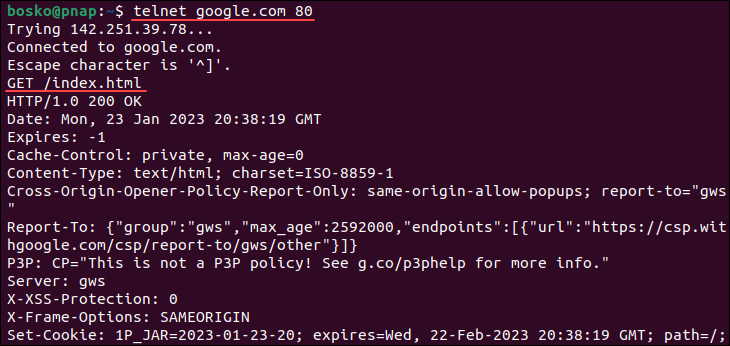
1. For example, the following command connects to port 80 on google.com:
2. After establishing the connection, download the HTML web page by running:
The screenshot above shows that the command has downloaded the homepage source code.
3. Save the code to a file or inspect it in the terminal.
Test SMTP Communication
Another useful feature of telnet is that it allows users to test the SMTP port by sending emails directly from the command line. To do so, you need an email server that doesn’t require authentication. It is a great way to troubleshoot problems in an email client.
Note: Want to send and read email using the CLI? See how to use the Linux mail command.
Follow the steps below to send an email using telnet :
1. Connect to the server via the SMTP port:
telnet [server_address] [port]For [server_address] , specify the SMTP server address. For example, for Gmail it is smtp.gmail.com, while the SMTP [port] can be 25, 465, 587, etc., depending on the provider.
Important: Since May 2022, Google has prohibited access to Google accounts for less secure apps and won’t accept connections from telnet .
2. Greet the server with HELO or EHLO :
5. Specify the subject and email body, separated by a blank line:
SUBJECT: This is the email subject. "" This is the email body.Note: Most mail servers flag unsolicited anonymous mail, which means that it will likely end up in the spam folder.
Connect to Remote System
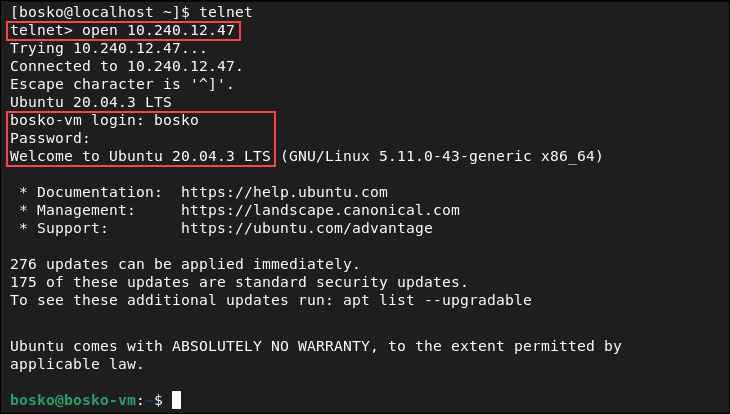
If you decide to use telnet for remote connections despite its lack of security, do it by specifying the remote machine’s IP address.
Make sure that telnet is installed on both machines and port 23 is allowed through the firewall on the remote machine.
When prompted, enter the account username and password to log in to the system. After logging in, you can operate the other machine remotely.
After the connection is established, you are in control of the remote machine.
This tutorial showed how to use the telnet command in Linux. Although it has poor security features and isn’t recommended for remote connections, the command has other uses that make it beneficial.
Next, see how SSH works and why it is more secure than telnet .