- How to Test Port [TCP/UDP] Connectivity from a Linux Server
- Testing TCP port connectivity with telnet
- Using nc command to test TCP port connectivity
- Testing UDP port connectivity wit nc command
- Some more articles you might also be interested in …
- How to check if TCP / UDP port is open on Linux & Windows Cloud Servers
- Linux
- Windows
- Related Tutorials
- Best Examples to Test Port Connectivity in Linux(RedHat 7/CentOS 7/Ubuntu 18.04)
- Test Port Connectivity
- What is Port
- Prerequisites
- Test TCP Ports
- What is TCP
- Test UDP Ports
- What is UDP
- 5 ways to check if a Port is open on a remote Linux PC
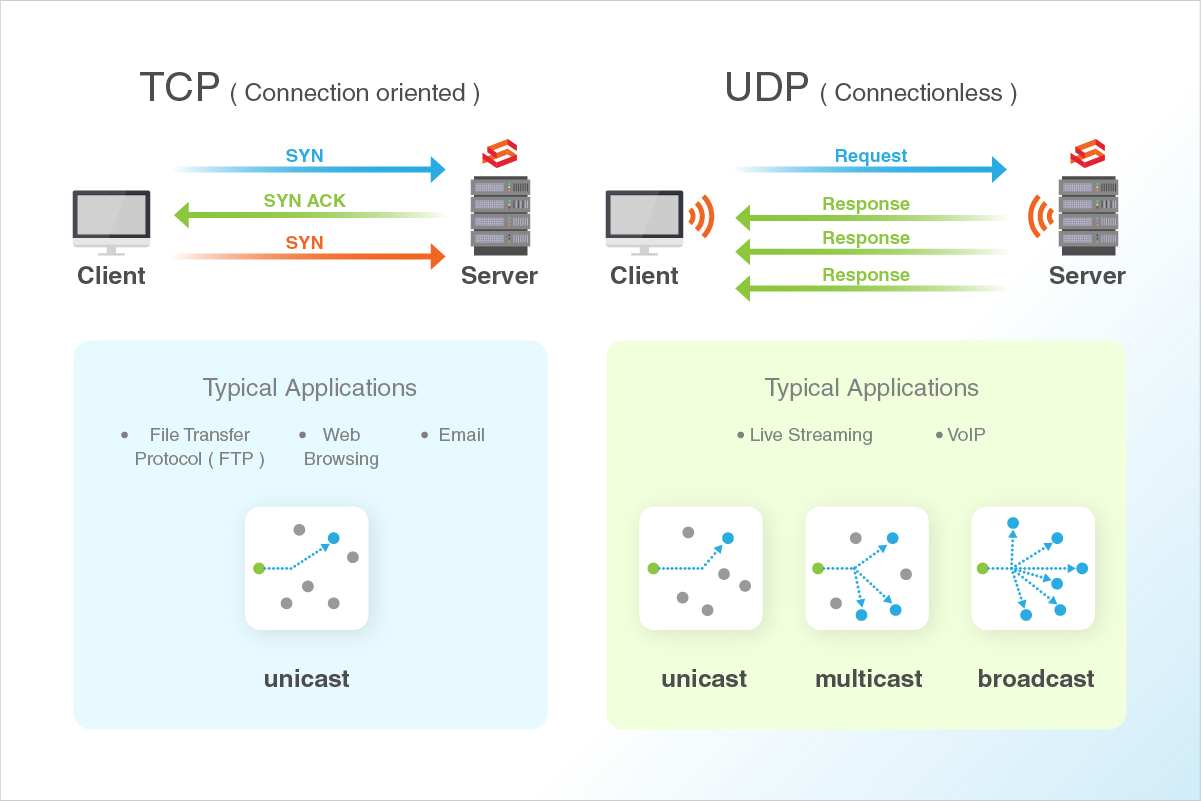
- TCP and UDP ports
- Best ways to check if a Port is open on a Linux PC
- 1. netcat command
How to Test Port [TCP/UDP] Connectivity from a Linux Server
Here is a short post to check port [TCP/UDP] connectivity from a Linux server. A TCP/IP network connection may be either blocked, dropped, open, or filtered. These actions are generally controlled by the IPtables firewall the system uses and is independent of any process or program that may be listening on a network port.
Telnet and nc are common tools used to test port connectivity from Linux server. Telnet can be used to test tcp port connections, where as nc can be used to test both tcp/udp ports connectivity. Make sure telnet and nc tools are installed on the Linux server you are trying to test connectivity.
# yum install nc # yum install telnet
Testing TCP port connectivity with telnet
Lets see how we can use telnet command to test the TCP port connectivity. The syntax to use the telnet command is as follows:
# telnet [hostname/IP address] [port number]
Example of successful connection:
# telnet 192.168.12.10 22 Trying 192.168.12.10. Connected to 192.168.12.10. Escape character is '^]'. SSH-2.0-OpenSSH_6.6.1 Protocol mismatch. Connection closed by foreign host.
Example of unsuccessful connection:
# telnet 192.168.12.10 22 Trying 192.168.12.10. telnet: connect to address 192.168.12.10: No route to host
Using nc command to test TCP port connectivity
The syntax to use nc command for testing TCP post connectivity is as follows:
# nc -z -v [hostname/IP address] [port number]
Example of successful connection:
# nc -z -v 192.168.10.12 22 Connection to 192.118.20.95 22 port [tcp/ssh] succeeded!
Example of unsuccessful connection:
# nc -z -v 192.168.10.12 22 nc: connect to 192.118.20.95 port 22 (tcp) failed: No route to host
Testing UDP port connectivity wit nc command
The syntax to test UDP port connectivity with nc command is as follows:
# nc -z -v -u [hostname/IP address] [port number]
Example of successful connection:
# nc -z -v -u 192.168.10.12 123 Connection to 192.118.20.95 123 port [udp/ntp] succeeded!
Some more articles you might also be interested in …
How to check if TCP / UDP port is open on Linux & Windows Cloud Servers
Verifying which all ports (TCP/UDP) are open and listening on the network interfaces of a server is very important when it comes to server security as well as troubleshooting service-related issues. Vulnerable open ports can be the cause of severe security breaches in a server. It is a must that such ports are found out and closed/disabled.
In case of service-related issues, checking which all ports are in use can be used as a troubleshooting mechanism to find if multiple services are listening on the same port.
The following are the common port numbers:
- Ports 0 to 1023 are Well-Known Ports
- Ports 1024 to 49151 are Registered Ports (*Often registered by a software developer to designate a particular port for their application)
- Ports 49152 to 65535 are Public Ports
| Port | Name of the Service | Transport protocol |
|---|---|---|
| 20,21 | FTP | TCP |
| 22 | SSH | TCP and UDP |
| 23 | Telnet | TCP |
| 25 | SMTP | TCP |
| 50,51 | IPSec | / |
| 53 | DNS | TCP and UDP |
| 67,68 | DHCP | UDP |
| 69 | TFTP | UDP |
| 80 | HTTP | TCP |
| 110 | POP3 | TCP |
| 119 | NNTP | TCP |
| 123 | NTP | TCP |
| 135-139 | NetBIOS | TCP and UDP |
| 143 | IMAP | TCP and UDP |
| 161,162 | SNMP | TCP and UDP |
| 389 | Lightweight Directory Access | TCP and UDP |
| 443 | HTTPS | TCP and UDP |
| 465 | SMTP over SSL | TCP |
| 989 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 990 | FTP Protocol (data) over TLS/SSL | TCP and UDP |
| 993 | IMAP over SSL | TCP |
| 995 | POP3 over SSL | TCP |
| 3389 | Remote Desktop | TCP and UDP |
This guide outlines the basic steps to determine which all ports are open in a service using commands such as lsof , netstat and nmap in Linux server and netstat on Windows server.
Linux
An example of this is when both Apache and Nginx services run on the same server.
Method 1 — Using lsof command
lsof (list open files) is a command that is used to display the list of all open files in a server and the services that have opened them.
- The general syntax of the lsof command is as below:
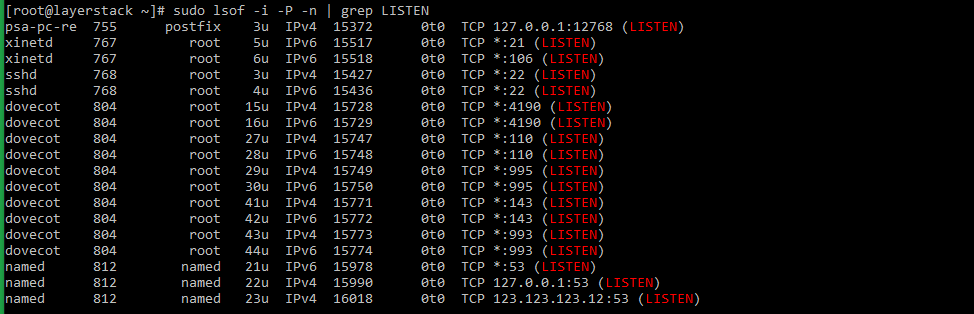
Using pipe and grep commands, the result of the above command can be filtered to show the result of files that are listening on different ports in the server.
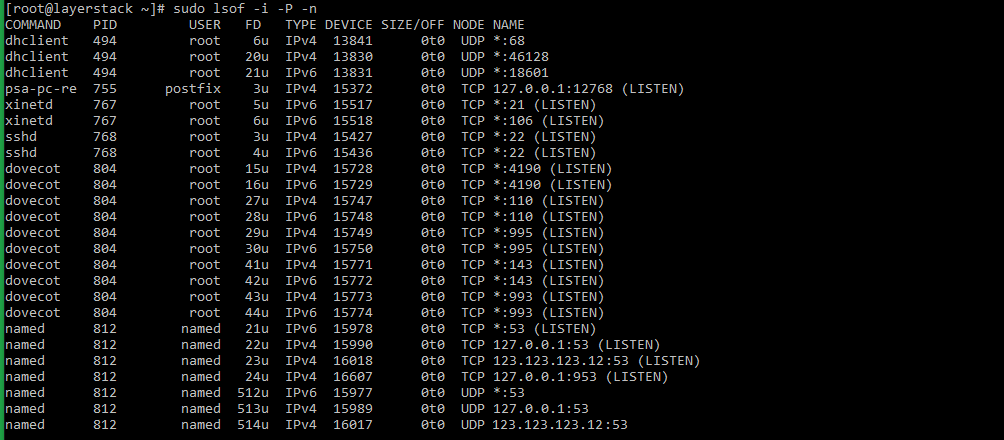
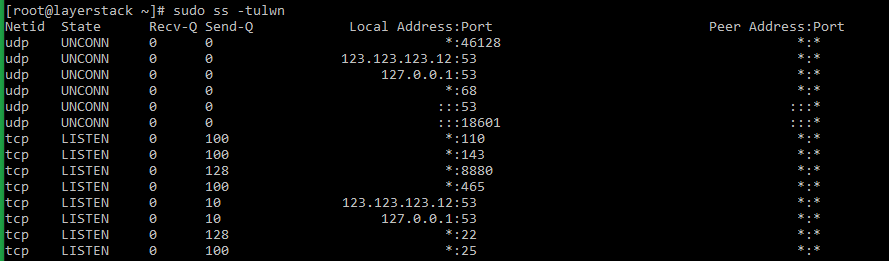
# sudo lsof -i -P -n | grep LISTEN # doas lsof -i -P -n | grep LISTEN (for OpenBSD systems) Taking the last line from sample output, the result can be explained as below:
named 812 named 23u IPv4 16018 0t0 TCP 123.123.123.12:53 (LISTEN) - named : name of the service.
- 123.123.123.12 : IP on which the named service is bound to.
- 53 : TCP port of the service that is being used.
- 812 : Process ID of the service.
Method 2 — Using netstat command
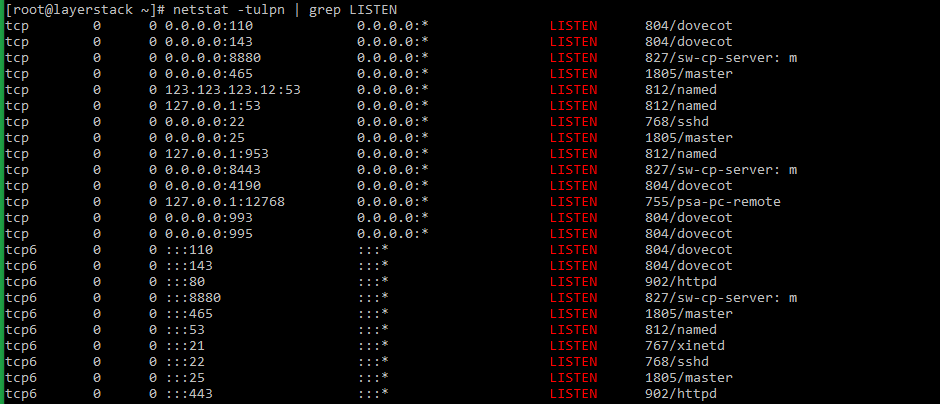
netstat (network statistics) is a command-line tool that can be used to monitor both incoming and outgoing network connections in a server.
- The netstat command along with the grep command to check the listening services can be used in the below syntax
# netstat -tulpn | grep LISTEN # netstat -nat | grep LISTEN (for OpenBSD systems) netstat command has been deprecated in the latest versions of Linux distribution. The ss command has taken its place.
The syntax for using the ss command is as provided below:
The switches for the ss command mean as follows:
- t: Show only TCP sockets.
- u: Show only UDP sockets.
- l: Show listening sockets.
- p: Show the name of the process that opened the socket.
- n: Do not try to resolve service names.
Method 3 — Using nmap command
nmap (network mapper) is a network scanner command tool that can be used to find out hosts and services on a server. This is done by sending packets to the server and analyzing the results further.
- The general syntax of the nmap command that can be executed from within the server is as follows:
# sudo nmap -sT -O localhost # sudo nmap -sTU -O 123.123.123.12 (scan both TCP and UDP for server) 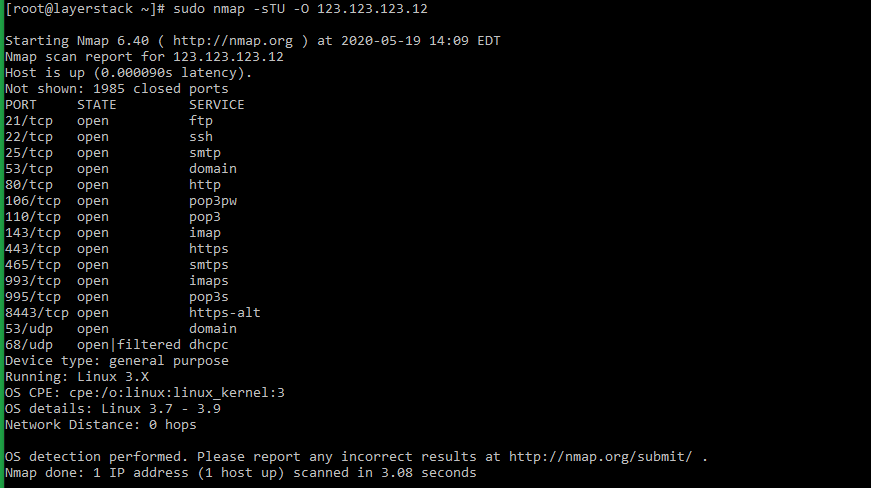
Windows
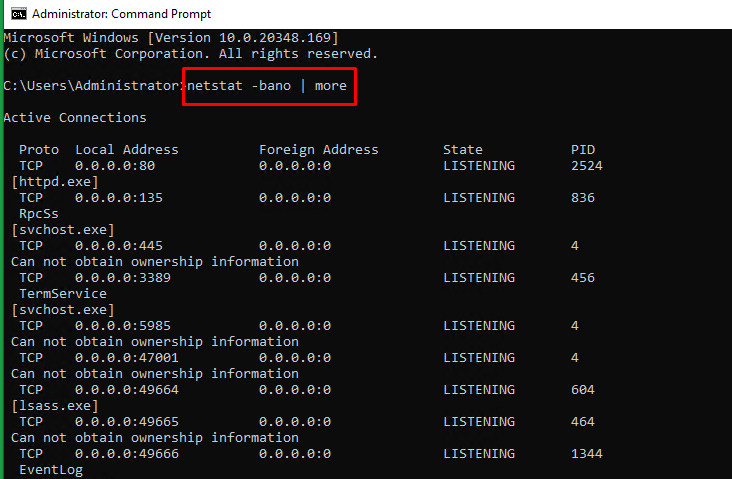
In Windows servers, the netstat command can be used to check the ports that are currently in use in the server.
- The syntax for the netstat command to be used in Windows servers is as below:
> netstat -bano | more > netstat -bano | findstr /R /C:"[LISTENING]" 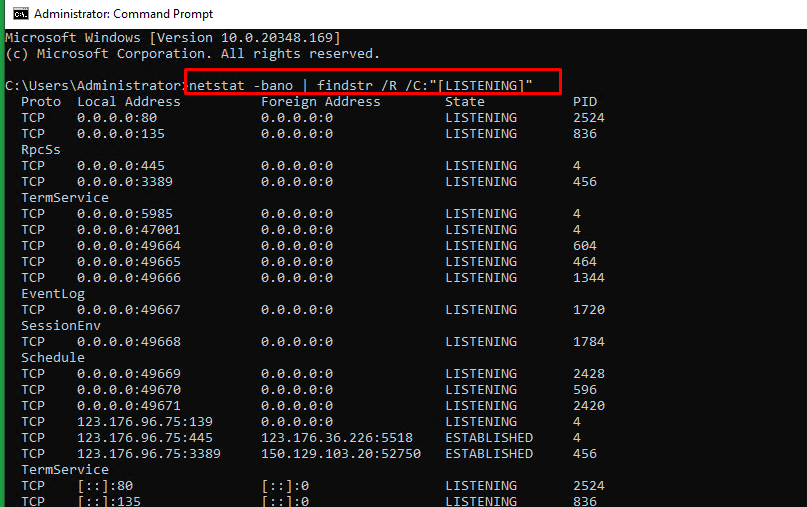
- Proto : The protocol being used for the socket (TCP/UDP).
- Local address : Source IP address and port to which the service is listening to.
- State : The current state of the service.
- PID : Process ID of the service, followed by the service name.
Related Tutorials
Best Examples to Test Port Connectivity in Linux(RedHat 7/CentOS 7/Ubuntu 18.04)
In this tutorial, I will take you through the different tools that can be used to check/test port connectivity in Linux.
Test Port Connectivity
You might be aware of curl, netstat, telnet and nc command in Linux: —
curl — It is usually used for downloading web pages or files from a Linux/Unix command line. But there’s another great usage curl command has: testing TCP ports connectivity. Taking an example, let’s assume you’re helping with some network changes and need to confirm that connection from your server to some remote host and specific TCP port still works.
telnet — telnet command is used for interactive communication with another host using the TELNET protocol. It begins in command mode, where it prints a telnet command prompt («telnet>»). If telnet is invoked with a host argument, it performs an open command implicitly.
nc — nc command is for performing maintenance/diagnosis tasks related to network . It can perform operations like read,write or data redirections over the network, similar to how you can use cat command to manipulate files on Linux system
What is Port
Ports are basically Communication endpoint in Network Topology through which outbound and inbound traffic flows.
Prerequisites
You need to have netstat, curl, nc and telnet command in linux.
Test TCP Ports
What is TCP
TCP stands for Transmission Control Protocol. Using this method, the system sending the data connects directly to the computer it is sending the data it to, and stays connected for the duration of the transfer.
With this method, the two systems can guarantee that the data has received safely and correctly without compromising the integrity of packets, and then they disconnect the connection.
This method of transferring data tends to be quicker and more reliable, but puts a higher load on the system as it has to monitor the connection and the data flowing across it.
Here’s how you can do it using curl command and its telnet functionality.
Test SSH port connection with curl
You can test local port 22 through curl command as specified below.
[root@localhost ~]# curl -v telnet://127.0.0.1:22 * About to connect() to 127.0.0.1 port 22 (#0) * Trying 127.0.0.1. * Connected to 127.0.0.1 (127.0.0.1) port 22 (#0) SSH-2.0-OpenSSH_7.4 ^C Test SSH port connection with telnet
You can test port 22 by using telnet command as mentioned below.
[root@localhost ~]# telnet 127.0.0.1 22 Trying 127.0.0.1. Connected to 127.0.0.1. Escape character is '^]'. SSH-2.0-OpenSSH_7.4 ^C Test UDP Ports
What is UDP
UDP is known as User Datagram Protocol. Using this method, the system sending the data packages the information into a nice little packets and releases it into the network with the hopes that it will get to the right destination.
What this means is that UDP does not connect directly to the receiving computer like TCP does, but rather sends the data out and relies on the network devices in between the transmitting system and the receiving system to get the data where it is supposed to go properly.
This method of transmission does not provide any guarantee that the data you transmit will ever reach its destination. On the other hand, this method of transmission has a very low overhead and is therefore very popular to use for services that are not that important to work on the first go.
Test SSH port connection with nc
You can test udp port 123 by using below netcat command:-
[root@localhost ~]# nc -v -z -u 127.0.0.1 123 Ncat: Version 7.50 ( https://nmap.org/ncat ) Ncat: Connected to 127.0.0.1:123. Ncat: UDP packet sent successfully Ncat: 1 bytes sent, 0 bytes received in 2.02 seconds. 5 ways to check if a Port is open on a remote Linux PC
T here is an ample number of ways to check for any open ports on a remote Linux PC. Knowing open ports on a Linux machine helps system administrators to connect to the remote PC for troubleshooting system and cloud server issues.
TCP and UDP ports
TCP stands for Transmission Control Protocol. In this method, the computers get connected directly until the data transfer is taking place. Therefore, with this method, the data transfer is guaranteed and is reliable but puts a higher load on the server as it has to monitor the connection and the data transfer too.
UDP stands for User Datagram Protocol. Using this method, the data is sent in the form of little packages into the network with the hope that it reaches the final destination. It means the two computers are not connected directly to each other. This method does not provide any guarantee that the data you send will ever reach its destination. Load on the server is less, and so this method is used commonly by the system administrators first to try something that’s not so important.
Now that you know the types are ports on a Linux system, let’s get started with ways of finding the ones that are open.
Best ways to check if a Port is open on a Linux PC
There are multiple ways you can do it. However, the most reliable way to do this is by using the following commands:
- nc: netcat command
- nmap: network mapper tool
- telnet: telnet command
- echo > /dev/tcp/..
- netstat – tuplen
Let’s go through each method one by one.
1. netcat command
netcat is a simple Unix utility that can be used to write and read data using UDP and TCP protocol across network connections.
The primary reason for its design is to provide a back-end tool that works with the scripts and programs. It is also an exploration and network debugging tool that offers tons of features.
To use it, you need to install it in your distro using the respective installation commands.