Tinder — знакомства и чат
Tinder® — это ведущее бесплатное приложение для знакомств, в котором уже образовано более 70 миллиардов пар. Ищешь настоящую любовь? Открытые отношения? Хочешь сходить на свидание или завести новых друзей? В Tinder ты сможешь знакомиться с людьми по всему миру и получать положительные эмоции:
Наше приложение открыто для гетеросексуалов, геев, бисексуалов и других ориентаций: Tinder позволяет тебе быть собой и находить кого угодно
Делись интересами и узнавай больше о своих парах, находи общие темы и приятных собеседников.
Профили с проверенными фото: чтобы единственным сюрпризом на первом свидании были цветы.
Видеочат: проверь свою симпатию и знакомься с новыми людьми прямо из дома!
Собираешься в путешествие? Пообщайся с местными из любой точки мира. Знакомства в Москве, новые друзья в Тбилиси или свидания в Лондоне — мы поможем найти компанию где угодно.
Для кого-то мы «самое надёжное приложение для поиска пар», для других — «самый популярный в мире сайт для знакомств». Мы не знаем, кем станем для тебя, но точно поможем найти компанию поблизости.
Знакомься. Общайся. Встречайся. Это наш девиз.
Знакомиться с новыми людьми в Tinder® просто и увлекательно. Чтобы сделать профиль заметным, добавь свои лучшие фотографии и расскажи немного о себе. Свайпай вправо, чтобы поставить кому-то лайк, или свайпай влево, чтобы перейти к следующему профилю. Если тебе поставили ответный лайк, пара совпала! Не волнуйся: образовать пару можно только при наличии взаимного интереса. Много ли приложений способны на такое?
Наслаждайся премиум-функциями Tinder с подпиской Tinder Gold™
Лайки — узнай, кто тебя лайкнул, и сэкономь время
Безлимит лайков — не упускай потенциальные пары
Перемотка — отменяй последний свайп
Загранпаспорт — находи знакомых в других странах и регионах прямо из дома
Ежемесячный буст — помести свой профиль на первое место на 30 минут, чтобы привлечь еще больше внимания
5 суперлайков в неделю — потому что иногда простого лайка недостаточно
Оформи подписку Tinder Platinum™, чтобы получить все эти премиум-функции, а также приоритетные лайки, возможность добавлять сообщения до создания пары и многое другое.
Если пока не хочешь оформлять Gold или Platinum, ничего страшного! Получи безлимит лайков, неограниченную Перемотку и Загранпаспорт с подпиской Tinder Плюс.
Чего же ты ждёшь? Скачай лучшее бесплатное приложение для знакомств уже сегодня! Если ты хочешь встречаться с новыми людьми, искать друзей или найти идеальную пару, ты по адресу — Tinder не хватает именно тебя.
Если ты решишь купить Tinder Плюс, Tinder Gold™ или Tinder Platinum™, то сделать это можно через аккаунт Google Play. С этого же аккаунта будут списаны средства за 24 часа до завершения текущего платного периода. Автоматическое продление подписки можно отключить в настройках Google Play в любое время после покупки. Отменить текущую подписку в период её действия невозможно. Если ты не планируешь покупать Tinder Плюс, Tinder Gold™ или Tinder Platinum™, можешь продолжать пользоваться Tinder бесплатно.
На всех фотографиях изображены модели, которые используются только в качестве примера.
Wireless Security — Bluetooth Hacking Tools
On the internet, there are tens of hundreds of tools already made, that will facilitate Bluetooth hacking. For sure, it is not possible to be aware and know all of them, and in my opinion — the fundamental knowledge that is needed is to know the tools used for a reconnaissance phase.
When you pass through this stage, you have to decide what is the goal of hacking approach to inject some files? Or to steal data? Or to execute malicious malware? Depending on your direction, there are a different set of tools you should use.
Therefore, concentrating on the reconnaissance (discovery phase) and internal kali Bluetooth hacking tools would be our goal for this chapter.
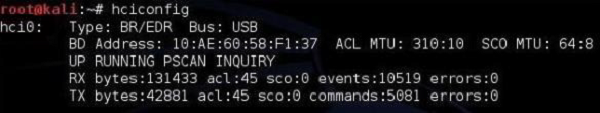
hciconfig
This hciconfig is the main Linux command line utility used for interacting with Bluetooth device (Bluetooth dongle). If you know Linux, you may already see the reference to other tools like ifconfig or iwconfig.
The information you get read from hciconfig output are −
- The name of the interface — «hci0«.
- How it is connected to a PC (either via a USB or built-in) here it is the USB dongle.
- MAC address of the Bluetooth dongle — 10:AE:60:58:F1:37.
- It is currently running (UP flag) and you can see received (RX) and transmitted (TX) packets.
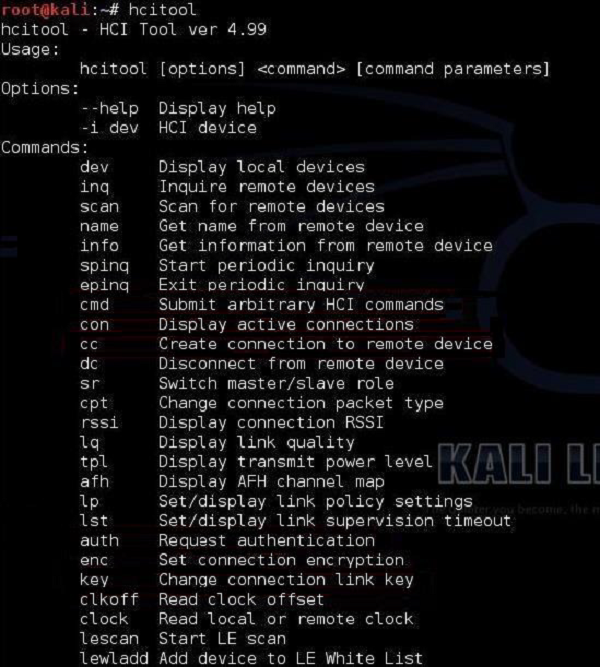
hcitool
This hcitool is a very powerful CLI tool implemented in kali Linux that allows a user to interface with the Bluetooth stack. It is also a great tool that you can use in your own scripts.
The most common options of this hcitool are scan and inq.
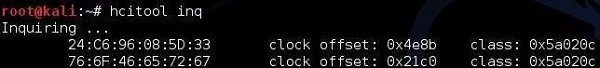
An hcitool scan will allow you to find Bluetooth devices that are sending out their discovery beacons (something like 802.11 beacon frames sent out by AP).
As you can see that in the neighborhood, two Bluetooth enabled devices were sending out beacon frames to inform about their readiness to accept Bluetooth connections. You can try to find more Bluetooth information about those two by using the hcitool inq.
What this output says is that the following devices belong to class 0x5a020c (you can find the description and mapping of the classes here − (https://www.bluetooth.com/specifications/assigned-numbers/service-discovery )
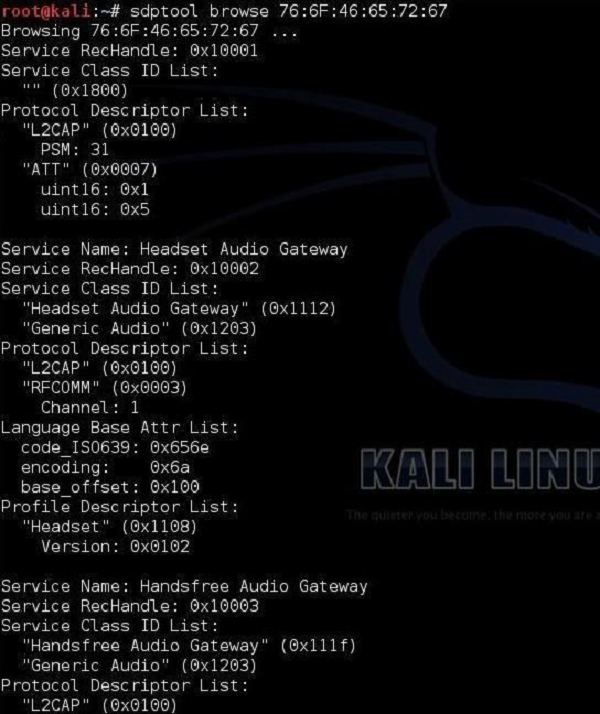
sdptool
Kali Linux also has a built-in tool for performing Service Discovery (SDP). It allows you to enumerate all the services running on the Bluetooth device.
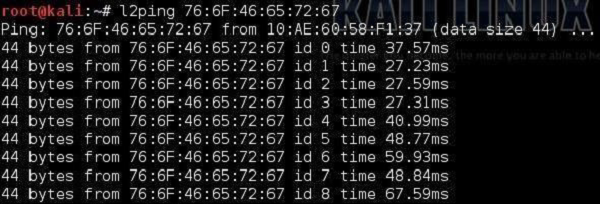
l2ping
All of us know the ping utility from the IP world that is used to check the connectivity between IP nodes using the ICMP protocol. The Bluetooth world has its own equivalent called l2ping. This discovery tool, allows the user to check whether a particular device is within the range and is reachable for Bluetooth communication.
Those were the basic tools that will allow you to play with Bluetooth technology and make very good reconnaissance of its operation. The tool that was mentioned earlier hcitool, this is the one you should spend some time with, if you want to really develop in this area of Bluetooth penetration testing.
H A C K R Z
Bluetooth Technology is great. No doubt. It provides an easy way for a wide range of mobile devices to communicate with each other without the need for cables or wires. However, despite its obvious benefits, it can also be a potential threat for the privacy and security of Bluetooth users (remember Paris Hilton?).
If you are planning to gain a deeper understanding of Bluetooth security, you will need a good set of tools with which to work. By familiarizing yourself with the following tools, you will not only gain a knowledge of the vulnerabilities inherent in Bluetooth-enabled devices, but you will also get a glimpse at how an attacker might exploit them.
This hack highlights the essential tools, mostly for the Linux platform, that can be used to search out and hack Bluetooth-enabled devices.
DISCOVERING BLUETOOTH DEVICES
BlueScanner – BlueScanner searches out for Bluetooth-enabled devices. It will try to extract as much information as possible for each newly discovered device.
BlueSniff – BlueSniff is a GUI-based utility for finding discoverable and hidden Bluetooth-enabled devices.
BTBrowser – Bluetooth Browser is a J2ME application that can browse and explore the technical specification of surrounding Bluetooth-enabled devices. You can browse device information and all supported profiles and service records of each device. BTBrowser works on phones that supports JSR-82 – the Java Bluetooth specification.
BTCrawler – BTCrawler is a scanner for Windows based devices. It scans for other devices in range and performs service query. It implements the BlueJacking and BlueSnarfing attacks.
HACKING BLUETOOTH DEVICES
BlueBugger – BlueBugger exploits the BlueBug vulnerability. BlueBug is the name of a set of Bluetooth security holes found in some Bluetooth-enabled mobile phones. By exploiting those vulnerabilities, one can gain an unauthorized access to the phone-book, calls lists and other private information.
CIHWB – Can I Hack With Bluetooth (CIHWB) is a Bluetooth security auditing framework for Windows Mobile 2005. Currently it only support some Bluetooth exploits and tools like BlueSnarf, BlueJack, and some DoS attacks. Should work on any PocketPC with the Microsoft Bluetooth stack.
Bluediving – Bluediving is a Bluetooth penetration testing suite. It implements attacks like Bluebug, BlueSnarf, BlueSnarf++, BlueSmack, has features such as Bluetooth address spoofing, an AT and a RFCOMM socket shell and implements tools like carwhisperer, bss, L2CAP packetgenerator, L2CAP connection resetter, RFCOMM scanner and greenplaque scanning mode.
Transient Bluetooth Environment Auditor – T-BEAR is a security-auditing platform for Bluetooth-enabled devices. The platform consists of Bluetooth discovery tools, sniffing tools and various cracking tools.
Bluesnarfer – Bluesnarfer will download the phone-book of any mobile device vulnerable to Bluesnarfing. Bluesnarfing is a serious security flow discovered in several Bluetooth-enabled mobile phones. If a mobile phone is vulnerable, it is possible to connect to the phone without alerting the owner, and gain access to restricted portions of the stored data.
BTcrack – BTCrack is a Bluetooth Pass phrase (PIN) cracking tool. BTCrack aims to reconstruct the Passkey and the Link key from captured Pairing exchanges.
Blooover II – Blooover II is a J2ME-based auditing tool. It is intended to serve as an auditing tool to check whether a mobile phone is vulnerable.
BlueTest – BlueTest is a Perl script designed to do data extraction from vulnerable Bluetooth-enabled devices.
BTAudit – BTAudit is a set of programs and scripts for auditing Bluetooth-enabled devices.
What’s next ? Let everyone know to disable Bluetooth until they really need it. Additionally, make sure to update your phone software on a regular basis.
7 Most Popular Bluetooth Hacking Software to Hack Mobile Phones
We all are familiar with the term hacking and the disadvantages faced by anyone when it is being used in illegal ways. Previously, hacking was restricted to computers or computer networks only but as time changed this field has grown up and now mobile phones, especially the multimedia phones are more prone to hacking. There are various hacks and software already present on the web which helps hackers in hacking any multimedia phones. In this post, I have outlined only Bluetooth Hacking Software. These software are very efficient and can hack any Bluetooth-enabled device without any prior knowledge of the user.
So here comes the list of useful Bluetooth hacking software.
1. Super Bluetooth Hack 1.08
This software is used for controlling and reading information from a remote phone via Bluetooth or infrared. Phone list and SMS can be stored in HTML format. In addition to it, it will display information about battery, network, and sim card.
2. Blue Scanner
Blue Scanner searches out for Bluetooth-enabled devices and tries to extract as much information as possible for each newly discovered device in other words one can use this one to spy on others who are close.
3. Blue Sniff
BlueSniff is a simple utility for finding discoverable and hidden Bluetooth-enabled devices. It operates on Linux.
4. BlueBugger
This simply exploits the BlueBug (name of a set of Bluetooth security holes) vulnerability of the Bluetooth-enabled devices. By exploiting these vulnerabilities one can access phone-book, call lists, and other information of that device.
5. BTBrowser
BT Browser is a J2ME application which can browse and explore the technical specification of surrounding Bluetooth-enabled devices. One can browse device information and all supported profiles and services records of each device.
6. BTCrawler
BT Crawler is a scanner for Windows Mobile Based devices. It scans for other devices in range and performs service queries. It implements Bluejacking and BlueSnarfing attacks.
7. BlueSnarfing
Bluesnarfing is a method of hacking into Bluetooth-enabled mobile phones and with this, you can copy its entire information like contact book, etc. With this software you give the complete freedom to hackers, to send a “corruption code” to you which will completely shut-down the phone down and make it unusable for you.
Disclaimer: I have outlined these software for your information and knowledge purpose only. It’s an advice to all the multimedia phone users to keep off your Bluetooth and if any harm will occur then we do not take any responsibility.
Please leave your thoughts on Bluetooth hacking in the comments section below.