Recommendations for a Certificate Management tool for Linux [closed]
A client is looking to roll out OpenVPN to all its mobile employees and will use certificates on both the server and all clients. This creates a new challenge to manage all these certificates and handle certificate revocations and renewals. Any recommendations on a Linux GUI tool to manage hundreds of certificates? I have done testing using the CLI, but that is going to become a nightmare as the number of certificates increases into the hundreds.
4 Answers 4
XCA is a nice little tool, which is also cross-platform. Though I have to add, that in my experience, graphical tools will only get you so far. Especially if you create a lot of certificates, working your way into openssl pays off.
I find XCA to be the most perfect tool for testing and development, not so sure about using it in production, it doesn’t provide ACLs
You may want to try EJBCA. It is free, opensource, graphical, and runs on Linux.
Note that proper certificate management is 95% procedures; software can only get you so far.
Can you expand on which procedures or types of procedures you believe are critical to proper certificate mangaement?
A certificate links a physical identity to a cryptographic key. So you must ask yourself how you identify people, who does it, who checks it, who creates keys, how keys are stored, how and when keys are destroyed, who does what in case of key compromise, who is accountable for mishaps, and so on. Software can help you do the actual signing and encoding of certificates, but most of the job is about understanding what happens and planning for security events, and software will not help you for that.
Major tasks will include (1) revoking certificates of employees who leave the organization (2) revoking certificates used on systems that might be stolen, lost, etc (3) keeping track of certificates that need to be renewed. Regarding the question of identity, these certificates will be used either by employees or contract staff, so the identity issue is handled under normal HR procedures.
GUI-based CA Management
This list only includes free software as defined by the GNU foundation. Please contribute a small description if you think your favorite tool should be included in the list.
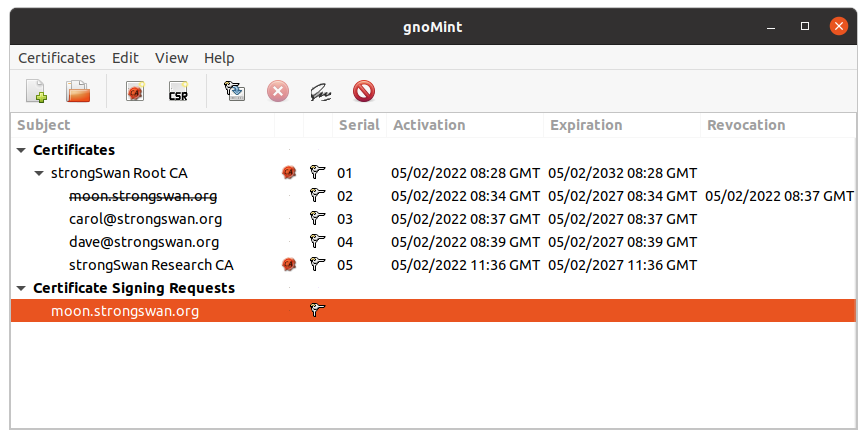
gnoMint
gnoMint allows any person to run a Certification Authority, creating certificates for any purpose: e-mail signing and/or crypting; TLS authentication through web, VPNs or other protocols; secured web-servers… Its development was started due to the lack of a ‘just-works’ CA software: creating a CA from zero, through open-source command-line utilities, was possible, but was unconfortable to remember all the neccessary parameters. And you had to create a difficult configuration file. So here is gnoMint, and it will help all systems and network administrators to deploy a Certification Authority very easily.
Features
- Creating all the infrastructure to keep and run a Certification Authority, saved in only one file.
- Create Certification Signing Requests, allowing to export them to PKCS#8 files, so they can be send to other CAs.
- Create X.509 certificates, with a usual set of subject-parameters.
- Export certificates and private keys to PEM files, so they can be used by external applications.
- For each CA, establish a set of policies for certificate generation.
- Import CSRs made by other applications.
- Export PKCS#12 structures, so the certificates can be imported easily by web and mail clients.
- Revoke certificates, and generate the corresponding CRLs.
- Allow the possibility of keeping the CA private key or other private keys in external files or devices (as USB drives).
- Allow the management of a whole hierarchy of CAs with their respectives certificates.
- Import pre-existing Certification Authorities with all their data.
- Allows an easy CA operation from command-line tools, for batch certificate creation, or integration with other utilities.
Drawbacks
- With the exception of the Root CA key where the RSA key size can be chosen, only 2048 bit RSA end entity or intermediate CA keys are available which doesn’t allow for a 128 bit security strength.
- No support of ECDSA keys.
- No support of subjectAlternativeNames which doesn’t allow to use Fully Qualified Domain Names (FQDNs) for hosts or email addresses for users as IKEv2 identities.
- The selection of the Country Name from a dropdown list is quite tiresome.
- No new releases since version 1.3.0 in 2016.
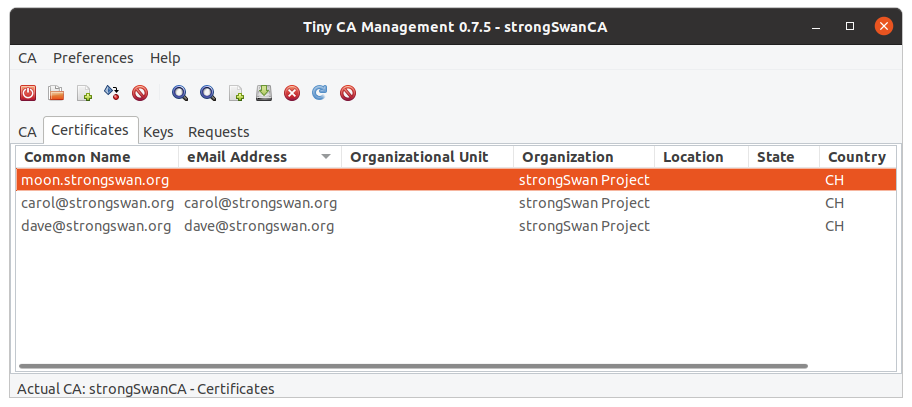
TinyCA 2
TinyCA is a simple graphical user interface written in Perl/Gtk to manage a small Certification Authority. TinyCA works as a frontend for openssl.
Features
- Unlimited CAs possible.
- Support for creating and managing Intermediate CAs.
- Creation and Revocation of X.509 certificates.
- PKCS#10 Requests can be imported and signed.
- Certificates can be exported as: PEM, DER, TXT or PKCS#12.
- Certificates can have a Fully Qualified Domain Name (FQDN), an IP address or an email address as a subjectAlternativeName .
- Certificate Revocation List (CRL).
- CRLs can be exported as: PEM, DER and TXT.
Drawbacks
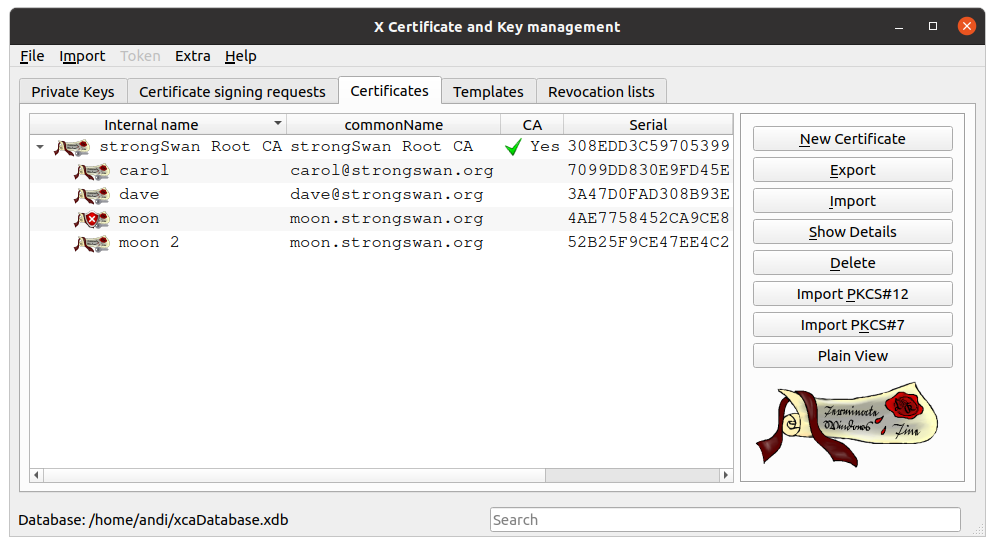
Xca
Xca is a graphical user interface for handling X.509 certificates, RSA or ECDSA keys, PKCS#10 requests and CRLs in software and on smartcards.
Features
- Start your own PKI and create all kinds of private keys, certificates, requests or CRLs.
- Import and export them in any format like PEM, DER, PKCS#7, PKCS#12.
- Use them for your IPsec, OpenVPN, TLS or any other certificate based setup.
- Manage your Smart-Cards via PKCS#11 interface.
- Export certificates and requests as OpenSSL config file.
- Create Subject- and/or Extension- templates to ease issuing similar certs.
- Convert existing certificates or requests to templates.
- Get the broad support of x509v3 extensions as flexible as OpenSSL but more user-friendly.
- Adapt the columns to have your important information at a glance.
Copyright © 2021-2023 The strongSwan Team and individual contributors. The content is provided under a CC BY 4.0 license
The UI for this site is derived from the Antora default UI and is licensed under the MPL-2.0 license.