- Notes for TurnKey Domain-Controller v15.x/v16.x/v17.x
- Compatibility with Windows Server
- Steps that need to be taken when first launched:
- Administer your AD: install RSAT
- Features to be added in the future:
- Backups
- General best practice recommendations
- Running AD DC in a container
- General DC Notes
- File storage/fileserver
- Further domain configuration e.g. DNS
- Realm/TLD
- Integration with LDAP
- Domain Controller
- Run from browser
- V 17.1
- V 16.2
- GitHub
- Important
- Usage details & Logging in for Administration
- Saved searches
- Use saved searches to filter your results more quickly
- turnkeylinux-apps/domain-controller
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.rst
Notes for TurnKey Domain-Controller v15.x/v16.x/v17.x
Note: at the time of writing, v17.0 is still under development so the full feature set is as yet unconfirmed.
Recent versions of TurnKey’s Domain-Controller (DC) appliance uses Samba4 to provide a Microsoft Active Directory domain.
However, it should be noted that the current appliance is a fairly bare-bones AD server. It is provided as a «better starting point» for those that wish to use Samba4 as an AD DC but is far from being feature complete.
Compatibility with Windows Server
Please note that Samba4 is not compatible with the latest Windows Server AD Schema. This should not be a problem if all your Domain Controllers use Samba. However, if you wish to join to an existing AD domain, please check the Windows AD schema to confirm it is compatible with Samba. TurnKey Linux uses the version of Samba packaged by Debian. In v16.x that is 4.9 and in v17.x will be 4.13.
Windows 2008R2 AD schema (or below) should be supported out of the box (although there may be some 2008R2 related edge case bugs still apparent in v16.x). However, you may be able to upgrade to Windows Server 2012 AD schema support (should be possible in TurnKey v17.x — unconfirmed in v16.x) or perhaps even higher (requires specific workaround).
If you try this, please be sure to post feedback (either confirming that it works, or the issues that you hit if it doesn’t) in the TurnKey Forums.
Steps that need to be taken when first launched:
- Set a static IP on your domain-controller
- If running on AWS (e.g. TurnKey Hub) then connect an «Elastic IP» (AWS equivalent of a static IP).
- Otherwise; easiest via confconsole
- if not using the DHCP assigned IP please re-run the domain provision inithook — copy/paste the following into commandline:
/usr/lib/inithooks/bin/domain-controller.py
# Substitute $ADMIN_PASS for the administrator password # the 1.168.192 is from the "network IP" (backwards) i.e. this example is for 192.168.1.x samba-tool dns zonecreate dc1 1.168.192.in-addr.arpa \ --username=administrator --password="$ADMIN_PASS" # as above but 50 is from the IP i.e. 192.168.1.50 samba-tool dns add dom-controller 1.168.192.in-addr.arpa 192.168.1.50 PTR dc1.domain.lan \ --username=administrator --password="$ADMIN_PASS"
- currently hardcoded to Google DNS (8.8.8.8)
edit /etc/samba/smb.conf and adjust the field that is currently «dns forwarder = 8.8.8.8»
To join a Windows Desktop to a Samba AD domain see the Samba Wiki: https://wiki.samba.org/index.php/Joining_a_Windows_client_to_a_domain
Administer your AD: install RSAT
To administer your AD please install Microsoft RSAT (Remote Server Administration Tools) onto a Windows member of your Domain. Note RSAT should already be pre-installed in the latest versions of Windows 10.
Some simple administration tasks, such as adding new AD/Samba users; can be completed via samba-tool from your TurnKey Domain-Controller commandline. For more info please see the Samba Wiki — Add Users to Samba AD.
Features to be added in the future:
- Option to provision a fileserver AD member server
- not yet sure on how this will be implemented.
- see «Best Practice» notes below
- will require AD member fileserver
- strictly speaking they’re not required but would be good
Backups
Currently TKLBAM won’t properly backup a domain. If you wish to use TKLBAM hooks to script it there is info on the Samba Wiki: https://wiki.samba.org/index.php/Backup_and_restore_an_Samba_AD_DC
Note: if you have multiple AD DCs then rather than restore from backup; just rejoin the server to the domain. Restoring a backup to a server that is already a member of a domain will likely cause DB corruption and/or multiple identical domain objects.
General best practice recommendations
Running AD DC in a container
For best experience it is recommended that TurnKey Domain Controller is run within a «proper» VM (or bare metal; rather than within a LXC or Docker container). However, Samba4 should generally function ok within a «privileged» container (although no guarantees that there will be no issues). Some functionality may work within a «unprivileged» container, but strange unexpected issues will likely occur, including (but not limited to) failures when running ‘samba-tool’.
General DC Notes
In production it is recommended that you have a minimum of 2 domain controllers in an AD domain.
File storage/fileserver
Samba advise against using a (Samba4) domain controller as a fileserver as well. Instead it is recommended that you create a dedicated fileserver (as a domain member server). The current TurnKey fileserver appliance is NOT useful for this with it’s default config. See notes on the Samba wiki on setting up a member server: https://wiki.samba.org/index.php/Setting_up_Samba_as_a_Domain_Member
Please note, that the TurnKey Fileserver appliance includes the same version of Sambas as the DC appliance, but is configured as «stand-alone» by default. You are welcome to reconfigure it to join an existing domain and that should work fine. Please post on the forums if you do that and would like to share your experience and/or need a hand.
Further domain configuration e.g. DNS
As noted above, Samba recommend using Microsoft RSAT (from within a Windows workstation) to do additional AD (Samba4) configuration.
Realm/TLD
For production usage it is recommended to use a domain name that you have registered with a domain registrar as the realm. If you plan to use a domain that you already own (e.g. «example.com») as your realm then add a unique subdomain to avoid potential problems (e.g. «ad.example.com»)
Do not use «.local» realms/tlds as they can conflict with Apple (bonjour) and zeroconf type networked devices.
Integration with LDAP
Samba4 includes it’s own custom AD user database. As a general rule, you should just use this built-in service. However, there is some limited support for integration with LDAP. For more info, please see these Samba Wiki links:
Domain Controller
A Samba4-based Active Directory-compatible domain controller that supports printing services and centralized Netlogon authentication for Windows systems, without requiring Windows Server. Since 1992, Samba has provided a secure and stable free software re-implementation of standard Windows services and protocols (SMB/CIFS).
Run from browser
V 17.1
V 16.2
GitHub
This appliance includes all the standard features in TurnKey Core, and on top of that:
- SSL support out of the box.
- Webmin modules for configuring Samba.
- Domain controller (Samba) configurations:
- Preconfigured NetBIOS name: DC1
- Sets domain/realm names on first boot
- Create new AD domain, or join existing AD domain
- Created administrator account is pre-set as Domain User/Admin
- Domain Admins have full permissions on the domain.
- Default permissions: owner full permissions.
- Installed PDF printer (drops printed docs to $HOME/PDF).
- Configured cups web interface to bind to all interfaces and support SSL.
Important
Usage details & Logging in for Administration
No default passwords: For security reasons there are no default passwords. All passwords are set at system initialization time.
Ignore SSL browser warning: browsers don’t like self-signed SSL certificates, but this is the only kind that can be generated automatically without paying a commercial Certificate Authority.
Username for samba:
Login as username administrator
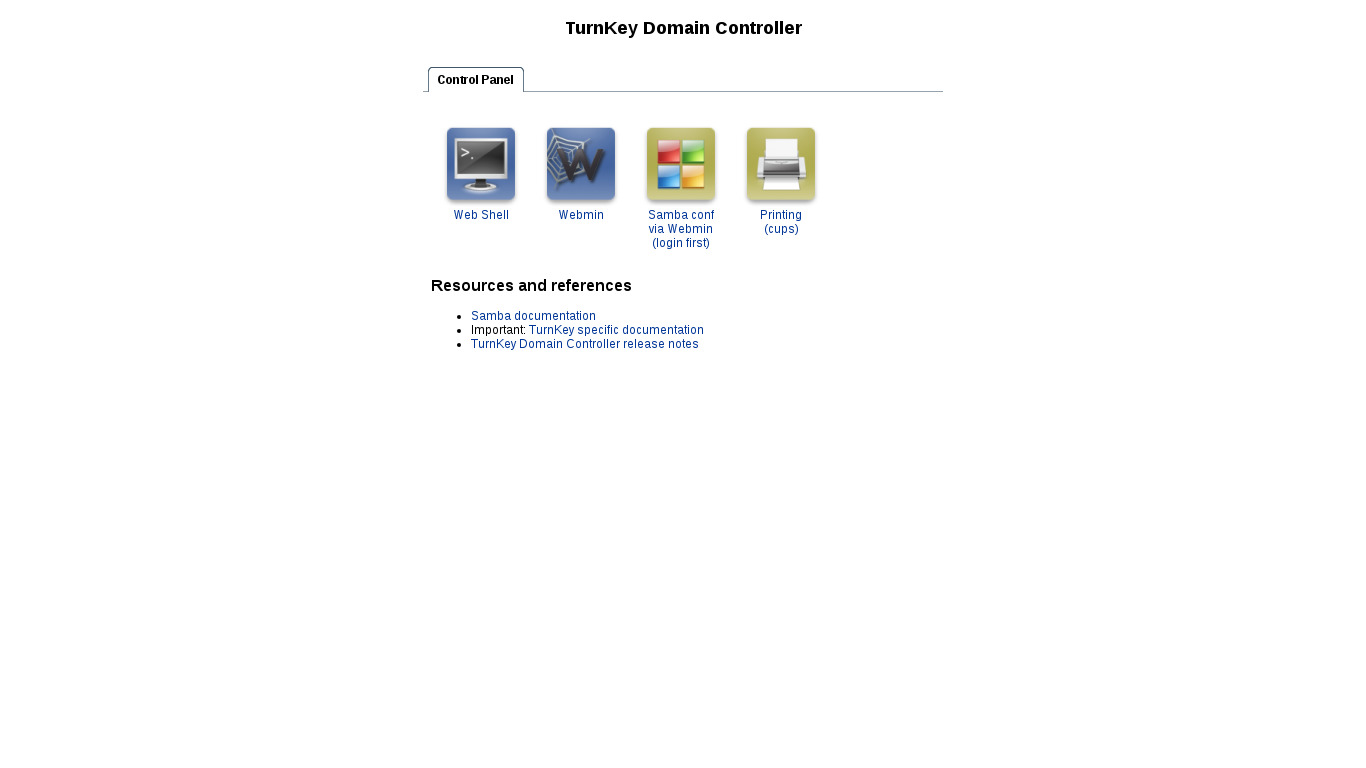
Web — point your browser at either:
Username for database administration:
Login as MySQL username root at
- https://12.34.56.789:12322/ — Adminer database management web app
- MySQL command line tool:
$ mysql --user root --password Enter password: Welcome to the MySQL monitor. Commands end with ; or \g. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
Username for OS system administration:
Login as root except on AWS marketplace which uses username admin.
- Point your browser to:
- https://12.34.56.789:12321/ — System control panel
- https://12.34.56.789:12320/ — Web based command line terminal
- Login with SSH client:
* Replace 12.34.56.789 with a valid IP or hostname.
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Domain Controller — Drop-in DC replacement
turnkeylinux-apps/domain-controller
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.rst
Domain Controller — free Active Directory server
A Samba4-based Active Directory-compatible domain controller that supports printing services and centralized Netlogon authentication for Windows systems, without requiring Windows Server. Since 1992, Samba has provided a secure and stable free software re-implementation of standard Windows services and protocols (SMB/CIFS).
This appliance includes all the standard features in TurnKey Core, and on top of that:
- SSL support out of the box.
- Webmin modules for configuring Samba.
- Domain controller (Samba) configurations:
- Preconfigured NetBIOS name: DC1
- Sets domain/realm names on first boot
- Create new AD domain, or join existing AD domain
- Created administrator account is pre-set as Domain User/Admin
- Domain Admins have full permissions on the domain.
- Default permissions: owner full permissions.
- Installed PDF printer (drops printed docs to $HOME/PDF).
- Configured cups web interface to bind to all interfaces and support SSL.
Credentials (passwords set at first boot)
- Webmin, Webshell, SSH, MySQL: username root
- Samba: username administrator