DESCRIPTION
The groupadd command creates a new group account using the values specified on the command line plus the default values from the system. The new group will be entered into the system files as needed.
Groupnames may contain only lower and upper case letters, digits, underscores, or dashes. They can end with a dollar sign. Dashes are not allowed at the beginning of the groupname. Fully numeric groupnames and groupnames . or .. are also disallowed.
Groupnames may only be up to 32 characters long.
OPTIONS
The options which apply to the groupadd command are:
This option causes the command to simply exit with success status if the specified group already exists. When used with -g, and the specified GID already exists, another (unique) GID is chosen (i.e. -g is turned off).
-g, —gid GID
The numerical value of the group’s ID. GID must be unique, unless the -o option is used. The value must be non-negative. The default is to use the smallest ID value greater than or equal to GID_MIN and greater than every other group.
See also the -r option and the GID_MAX description.
-K, —key KEY=VALUE
Overrides /etc/login.defs defaults (GID_MIN, GID_MAX and others). Multiple -K options can be specified.
Example: -K GID_MIN=100 -K GID_MAX=499
Note: -K GID_MIN=10,GID_MAX=499 doesn’t work yet.
permits the creation of a group with an already used numerical ID. As a result, for this GID, the mapping towards group NEWGROUP may not be unique.
-p, —password PASSWORD
defines an initial password for the group account. PASSWORD is expected to be encrypted, as returned by crypt (3).
Without this option, the group account will be locked and with no password defined, i.e. a single exclamation mark in the respective field of ths system account file /etc/group or /etc/gshadow.
Note: This option is not recommended because the password (or encrypted password) will be visible by users listing the processes.
You should make sure the password respects the system’s password policy.
The numeric identifiers of new system groups are chosen in the SYS_GID_MIN—SYS_GID_MAX range, defined in login.defs, instead of GID_MIN—GID_MAX.
-R, —root CHROOT_DIR
Apply changes in the CHROOT_DIR directory and use the configuration files from the CHROOT_DIR directory. Only absolute paths are supported.
-P, —prefix PREFIX_DIR
Apply changes to configuration files under the root filesystem found under the directory PREFIX_DIR. This option does not chroot and is intended for preparing a cross-compilation target. Some limitations: NIS and LDAP users/groups are not verified. PAM authentication is using the host files. No SELINUX support.
The default behavior (if the -g, -N, and -U options are not specified) is defined by the USERGROUPS_ENAB variable in /etc/login.defs.
CONFIGURATION
The following configuration variables in /etc/login.defs change the behavior of this tool:
GID_MAX (number), GID_MIN (number)
Range of group IDs used for the creation of regular groups by useradd, groupadd, or newusers.
The default value for GID_MIN (resp. GID_MAX) is 1000 (resp. 60000).
MAX_MEMBERS_PER_GROUP (number)
Maximum members per group entry. When the maximum is reached, a new group entry (line) is started in /etc/group (with the same name, same password, and same GID).
The default value is 0, meaning that there are no limits in the number of members in a group.
This feature (split group) permits to limit the length of lines in the group file. This is useful to make sure that lines for NIS groups are not larger than 1024 characters.
If you need to enforce such limit, you can use 25.
Note: split groups may not be supported by all tools (even in the Shadow toolsuite). You should not use this variable unless you really need it.
SYS_GID_MAX (number), SYS_GID_MIN (number)
Range of group IDs used for the creation of system groups by useradd, groupadd, or newusers.
The default value for SYS_GID_MIN (resp. SYS_GID_MAX) is 101 (resp. GID_MIN-1).
How to Add a User on Arch Linux
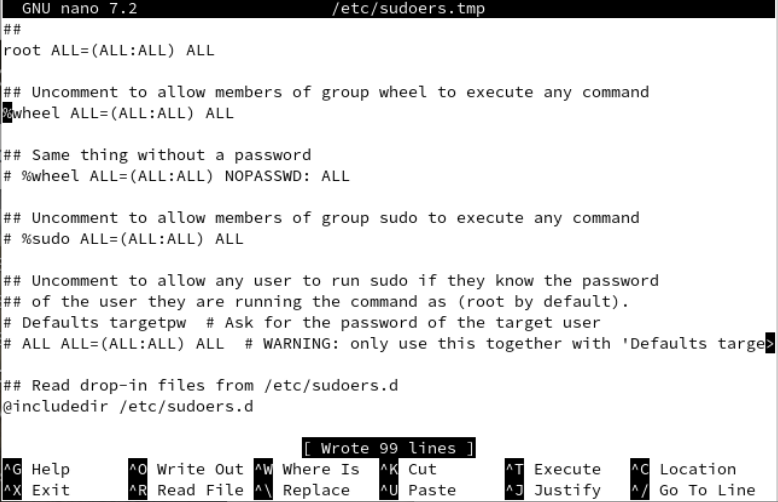
User management is the most needed utility in any operating system because it makes your system secure and provides you an opportunity to assign the right privileges to the right ones. The users can make a lot of changes to your system according to the rights they have. Therefore, it’s very necessary to have a very close look at each activity that is performed by the users. Thus, this guide elaborates on the method to add the new users to the Arch Linux system and how to manage them. Before moving towards the addition of users in the Arch Linux system, we need to make sure that the group is already enabled. To do so, we use the following “visudo” command with “sudo”. This is typically used to make changes to the sudoers file:
The sudouers file is launched in the “nano” editor. You will find the “wheel” group in the following illustration. Uncomment it and save the file to update the changes. Use “Ctrl-x” to exit.
Add a User
Now, we add a new “test” user to the Arch Linux system using the “useradd” instruction with the “sudo” rights. This instruction doesn’t take anything in return which indicates that the user is created.
Now, it’s very necessary to secure an account that is just created. For this, we establish a new user and add a new password. Therefore, we utilize the shell’s “passwd” command along with the user “test” as our input. You are prompted by the terminal to enter a new password. After providing the password twice, it is updated successfully.
passwd: password updated successfully
In case you want to perform the process of user addition to arch Linux along with setting its password at once, you can do so by modifying the useradd instruction. For this, you should use the “-m” and “-p” flags in the instruction. The “-m” flag can be utilized to name a new user while the “-p” option can be used to set the password for the user to be created. For example, we create a “dummy” user with the “dummy123” password via the useradd instruction in the following:
The other thing that you can achieve using the useradd instruction is to set the custom directory for a new user using the “-d” option with the path to the directory. The following instruction shows that we created a “new” user and a “new” password and set its custom directory as “/tmp/new”:
There are a lot of groups which are available in Arch Linux to perform the different functions according to their group types. To add a user to a particular group in Arch Linux, the useradd command comes up with the “-G” option to add a particular user to any group. For example, the following instruction adds a new “blue” user in the wheel, audio, and video group while creating:
There is also a way to add the system users in Arch Linux using the useradd instruction. For this, you need to use the “-r” option with the “-s” flag followed by the path to the “fish” directory, i.e. “/usr/bin/fish”. The “hell” user is created as you can see from the attached command. The output of this instruction generates a warning.
useradd: Warning: missing or non-executable shell ‘/usr/bin/fish’
You can also do it if you wish to confirm the outcome of the aforementioned instruction. For that, try using the following “su’ instruction with the name of a user that you just created. It might show you a warning.
su: warning: cannot change directory to /home/hell: No such file or directory
After that, try the whoami one-word instruction on the shell. You will see that it returns the name of a system user that you just created.
User Modification
While using the arch Linux and creating new users, you should have a piece of knowledge about the user properties and a way to modify them. Consider the scenario where we want to rename the “test” to “test1” user. For this, we use the usermod instruction with the “-l” option followed by the new name and then an old name as shown in the following attached command:
Now, if you want to set the expiry date for a newly created user account, you can also set that using the usermod instruction followed by its “—expiry date” option. The option follows the date and then a username. The “test1” is our new user name in this case.
Now, if you want to add your user to the additional groups, you can do so by using the –append option in the usermod instruction followed by the –groups option with the group names and the name of a user to be added. The wheel and users are 2 groups while the test1 is a user.
To modify the default shell that is used by a user, you can use the –shell option in a usermod instruction. In this instruction, you should provide the path to the shell file like /usr/bin/bash.
Lock/Unlock the User
In case you don’t want anybody to use the particular account, you might lock it. To lock an account, the –lock option can be used in the usermod instruction with the name of a user which is “test1”.
In the same way, if you want to allow a particular user to use its system account, you should unlock the particular account using the “unlock” option in the usermod instruction with the same user name as shown in the attached instruction:
Delete the User
To display the currently available users of your Arch Linux, try using the instruction as follows:
To delete the new and previously made users, the “userdel” instruction can be utilized. This command takes one or more usernames at once.
[ omar @ omar ~ ] $ sudo userdel test1
[ omar @ omar ~ ] $ sudo userdel hell
[ omar @ omar ~ ] $ sudo userdel blue new
[ / c ] c
If you create a user with a related home directory, you can delete it using the –r option.
[ cc lang = «bash» width = «100%» height = «100%» escaped = «true» theme = «blackboard» nowrap = «0» ]
[ omar @ omar ~ ] $ sudo userdel -r dummy
Conclusion
The introductory paragraph explains the importance of user management in all sorts of operating systems. To support the discussion, we tried the different instructions to create the new users, modify, lock or unlock, and delete them. For this, we utilized the useradd, usermod, and userdel instructions with the –m, -p, -G, -r, -s, -l, –append, –shell, –lock, –unlock, and –expiredate options.
About the author
Omar Farooq
Hello Readers, I am Omar and I have been writing technical articles from last decade. You can check out my writing pieces.