- Kali Linux Nmap Guide
- Kali Linux working with Nmap:
- Finding live hosts on your network:
- Find open ports via Nmap:
- Find Services Listening on Ports on host Kali machine:
- Find Anonymous FTP Logins on Hosts:
- Check for Vulnerabilities on Hosts:
- Conclusion:
- About the author
- Younis Said
- How To Install nmap on Kali Linux
- What is nmap
- Install nmap Using apt-get
- Install nmap Using apt
- Install nmap Using aptitude
- How To Uninstall nmap on Kali Linux
- Uninstall nmap And Its Dependencies
- Remove nmap Configurations and Data
- Remove nmap configuration, data, and all of its dependencies
- References
- Summary
Kali Linux Nmap Guide
Nmap (“Network Mapper”) tool is used in active reconnaissance in order to not only determine live systems but also determine the holes in systems. This versatile tool is one of the best tools in the hacking community and is well supported. Nmap is available in all operating systems and is also available in a GUI. It is used to find network vulnerabilities. It is a network penetration testing tool used by most of the pentesters while doing pentesting. The Nmap team created Zenmap. It provides a graphical user interface representation of Nmap. It is an additional way of using Nmap, so if you don’t like the command-line interface and how the information is displayed, you can use zenmap.
Kali Linux working with Nmap:
On the Kali Linux screen, the installer will appear the user for a ‘root’ user password, which you will need to log in. The Enlightenment Desktop Environment can be started by using startx command after logging into the Kali Linux machine. The desktop environment is not required to run by Nmap.
You will have to open the terminal window once you have logged into enlightenment. The menu will appear by clicking the desktop background. To navigate to the terminal can be done as follows :
Applications –> System –> “Root Terminal”.
All shell programs work for purposes of the Nmap. After the successful launching of the terminal, Nmap fun can begin.
Finding live hosts on your network:
The IP address of the kali machine is 10.0.2.15, and the IP address of the target machine is ‘192.168.56.102’.
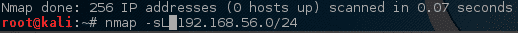
What is live on a particular network can be determined by a quick Nmap scan. It is a ‘Simple List’ scan.
Unfortunately, no live hosts were returned by using this initial scan.
Find and Ping All Live Hosts on My Network:
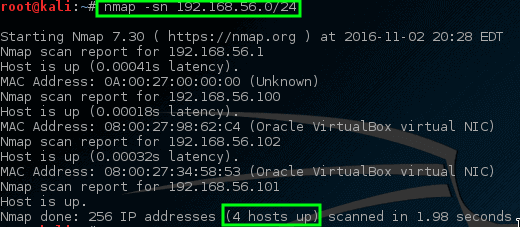
Fortunately, you do not have to worry, because using some tricks enabled by Nmap, we can find these machines. Trick mentioned will tell Nmap to ping all addresses in the 192.168.56.0/24 network.
So, Nmap has returned some potential hosts for scanning.
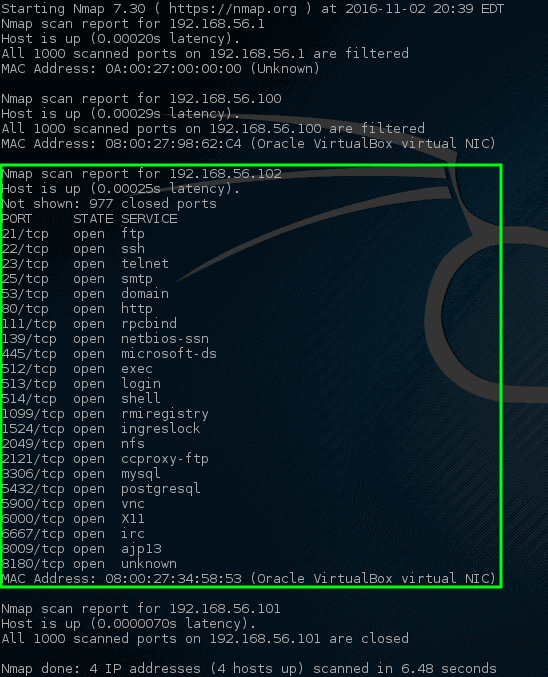
Find open ports via Nmap:
Let nmap perform a port scan to find particular targets and see the results.
Some listening service on this specific machine is indicated by these ports. An IP address is assigned to metasploitable vulnerable machines; this is why there are open ports on this host. A lot of ports opened on most machines is abnormal. It would be wise to investigate the machine closely. The physical machine on the network can be tracked down by administrators.
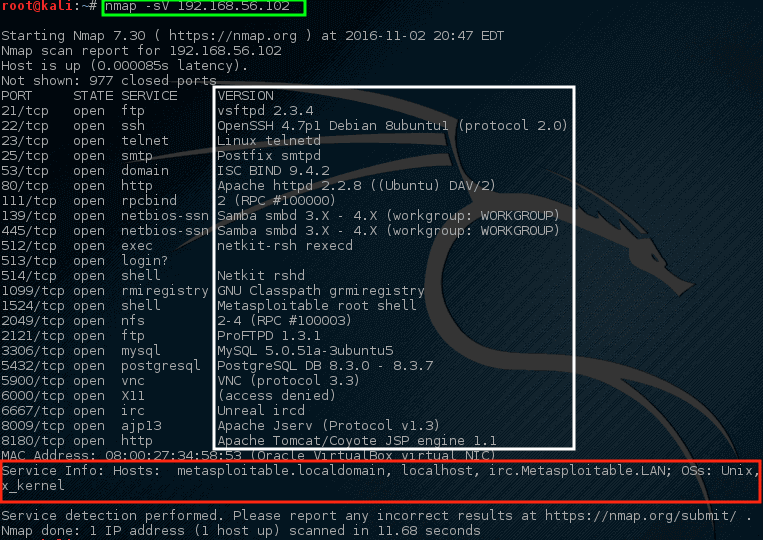
Find Services Listening on Ports on host Kali machine:
It is a service scan performed via Nmap, and its purpose is to check which services might be listening on a specific port. Nmap will investigate all open ports and will collect information from services running on each port.
It works to obtain information about the hostname and the current operating system running on the target system. The “vsftpd” version 2.3.4 is running on this machine, which is a pretty old version of VSftpd, which is alarming for the administrator. For this particular version (ExploitDB ID – 17491), a serious vulnerability was found back in 2011.
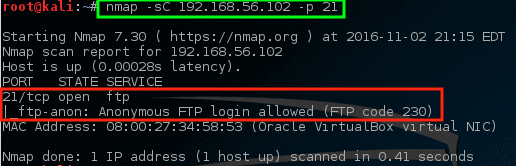
Find Anonymous FTP Logins on Hosts:
To gather more information, let Nmap have a closer look.
The above command has found out that anonymous FTP sign-in is allowed on this specific server.
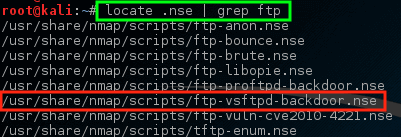
Check for Vulnerabilities on Hosts:
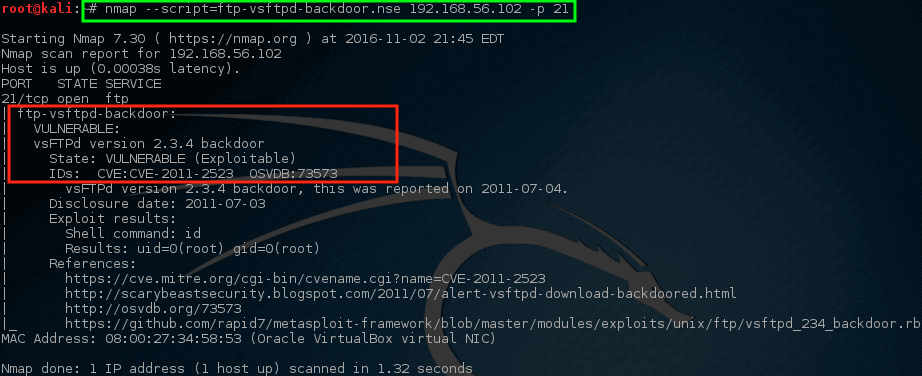
As the mentioned earlier version of VSftd is old and vulnerable, so it is quite concerning. Let us see if Nmap can check for the vulnerability of vsftpd.
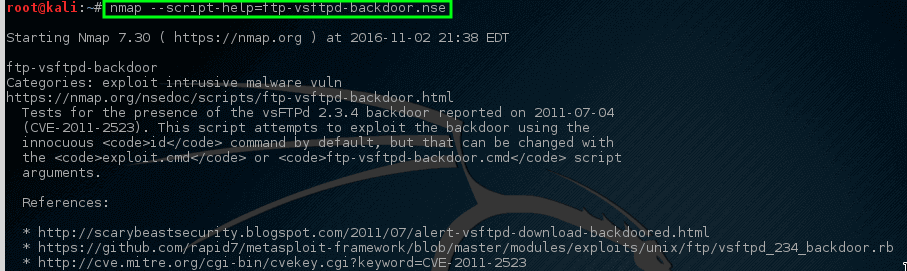
It is notable that for the VSftpd backdoor problem, Nmap has NSE script, (Nmap Scripting Engine) is one of Nmap’s most useful and adaptable features. It allows users to write simple scripts to mechanize a broad range of networking tasks. Before running this script against the host, we should know how to use it.
It can be used to check if the machine is vulnerable or not.
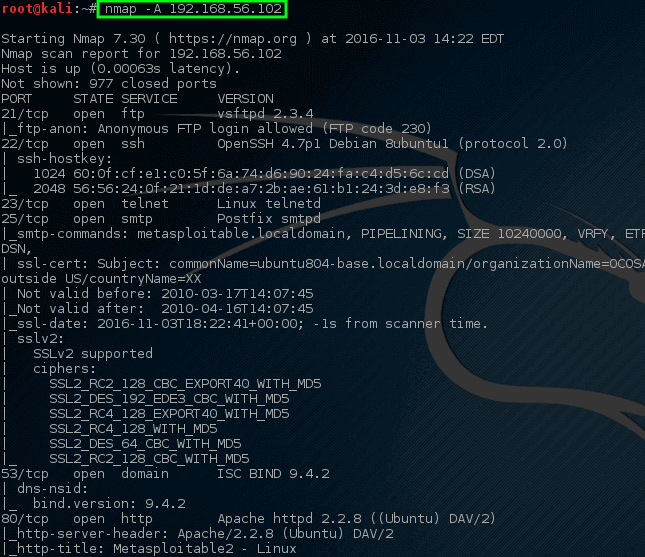
Nmap has the quality to be quite and selective. In this manner, to scan a personally owned network can be tedious. A more aggressive scan can be done by using Nmap. It will give somewhat the same information, but the difference that lies is we can do it by using one command instead of using loads of them. Use the following command for aggressive scan:
It is evident that using only one command, Nmap can return loads of information. Much of this information can be used to check what software may be on the network and to determine how to protect this machine.
Conclusion:
Nmap is a versatile tool to be used in the hacking community. This article provides you with a brief description of Nmap and its function.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.
How To Install nmap on Kali Linux
In this tutorial we learn how to install nmap on Kali Linux.
What is nmap
Nmap is a utility for network exploration or security auditing. It supports ping scanning (determine which hosts are up), many port scanning techniques, version detection (determine service protocols and application versions listening behind ports), and TCP/IP fingerprinting (remote host OS or device identification). Nmap also offers flexible target and port specification, decoy/stealth scanning, sunRPC scanning, and more. Most Unix and Windows platforms are supported in both GUI and commandline modes. Several popular handheld devices are also supported, including the Sharp Zaurus and the iPAQ.
There are three ways to install nmap on Kali Linux . We can use apt-get , apt and aptitude . In the following sections we will describe each method. You can choose one of them.
Install nmap Using apt-get
Update apt database with apt-get using the following command.
After updating apt database, We can install nmap using apt-get by running the following command:
sudo apt-get -y install nmap Install nmap Using apt
Update apt database with apt using the following command.
After updating apt database, We can install nmap using apt by running the following command:
Install nmap Using aptitude
If you want to follow this method, you might need to install aptitude first since aptitude is usually not installed by default on Kali Linux. Update apt database with aptitude using the following command.
After updating apt database, We can install nmap using aptitude by running the following command:
sudo aptitude -y install nmap How To Uninstall nmap on Kali Linux
To uninstall only the nmap package we can use the following command:
Uninstall nmap And Its Dependencies
To uninstall nmap and its dependencies that are no longer needed by Kali Linux, we can use the command below:
sudo apt-get -y autoremove nmap Remove nmap Configurations and Data
To remove nmap configuration and data from Kali Linux we can use the following command:
Remove nmap configuration, data, and all of its dependencies
We can use the following command to remove nmap configurations, data and all of its dependencies, we can use the following command:
sudo apt-get -y autoremove --purge nmap References
Summary
In this tutorial we learn how to install nmap using different package management tools like apt, apt-get and aptitude.