- Saved searches
- Use saved searches to filter your results more quickly
- License
- sherlock-project/sherlock
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- Инструменты Kali Linux
- Список инструментов для тестирования на проникновение и их описание
- Sherlock
- Описание Sherlock
- Справка по Sherlock
- Руководство по Sherlock
- Примеры запуска Sherlock
- Packages and Binaries:
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
🔎 Hunt down social media accounts by username across social networks
License
sherlock-project/sherlock
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Hunt down social media accounts by username across social networks
# clone the repo $ git clone https://github.com/sherlock-project/sherlock.git # change the working directory to sherlock $ cd sherlock # install the requirements $ python3 -m pip install -r requirements.txt
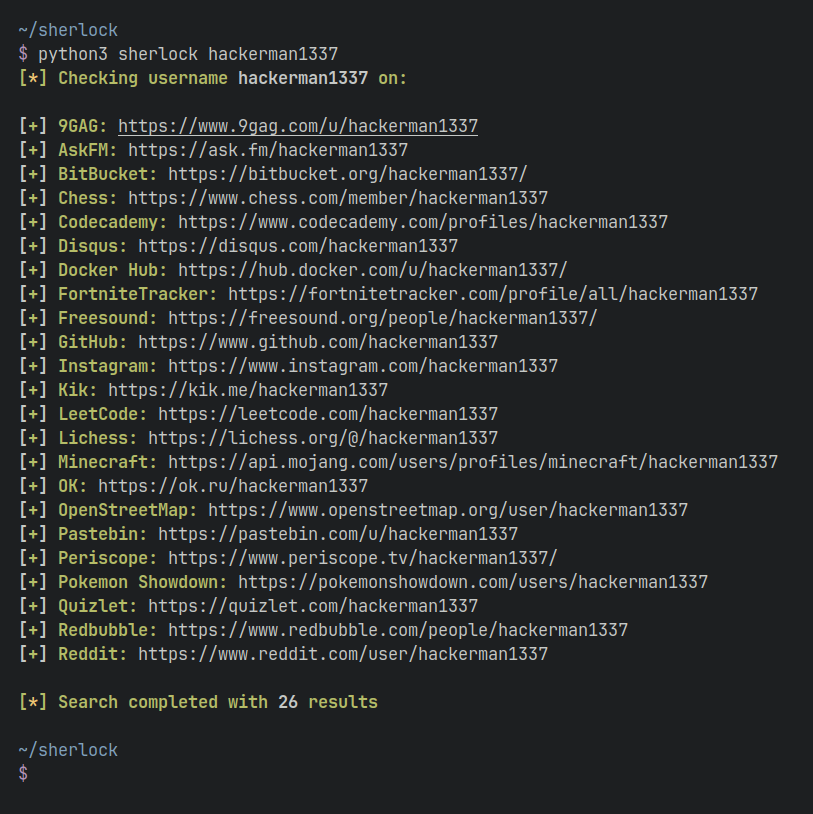
$ python3 sherlock --help usage: sherlock [-h] [--version] [--verbose] [--folderoutput FOLDEROUTPUT] [--output OUTPUT] [--tor] [--unique-tor] [--csv] [--site SITE_NAME] [--proxy PROXY_URL] [--json JSON_FILE] [--timeout TIMEOUT] [--print-all] [--print-found] [--no-color] [--browse] [--local] [--nsfw] USERNAMES [USERNAMES . ] Sherlock: Find Usernames Across Social Networks (Version 0.14.2) positional arguments: USERNAMES One or more usernames to check with social networks. Check similar usernames using (replace to '_', '-', '.'). optional arguments: -h, --help show this help message and exit --version Display version information and dependencies. --verbose, -v, -d, --debug Display extra debugging information and metrics. --folderoutput FOLDEROUTPUT, -fo FOLDEROUTPUT If using multiple usernames, the output of the results will be saved to this folder. --output OUTPUT, -o OUTPUT If using single username, the output of the result will be saved to this file. --tor, -t Make requests over Tor; increases runtime; requires Tor to be installed and in system path. --unique-tor, -u Make requests over Tor with new Tor circuit after each request; increases runtime; requires Tor to be installed and in system path. --csv Create Comma-Separated Values (CSV) File. --xlsx Create the standard file for the modern Microsoft Excel spreadsheet (xslx). --site SITE_NAME Limit analysis to just the listed sites. Add multiple options to specify more than one site. --proxy PROXY_URL, -p PROXY_URL Make requests over a proxy. e.g. socks5://127.0.0.1:1080 --json JSON_FILE, -j JSON_FILE Load data from a JSON file or an online, valid, JSON file. --timeout TIMEOUT Time (in seconds) to wait for response to requests (Default: 60) --print-all Output sites where the username was not found. --print-found Output sites where the username was found. --no-color Don't color terminal output --browse, -b Browse to all results on default browser. --local, -l Force the use of the local data.json file. --nsfw Include checking of NSFW sites from default list.
To search for only one user:
To search for more than one user:
python3 sherlock user1 user2 user3 Accounts found will be stored in an individual text file with the corresponding username (e.g user123.txt ).
If you are using Anaconda in Windows, using python3 might not work. Use python instead.
If docker is installed you can build an image and run this as a container.
docker build -t mysherlock-image . Once the image is built, sherlock can be invoked by running the following:
docker run --rm -t mysherlock-image user123 Use the following command to access the saved results:
docker run --rm -t -v "$PWD/results:/opt/sherlock/results" mysherlock-image -o /opt/sherlock/results/text.txt user123 Docker is instructed to create (or use) the folder results in the current working directory and to mount it at /opt/sherlock/results on the docker container by using the -v «$PWD/results:/opt/sherlock/results» options. Sherlock is instructed to export the result using the -o /opt/sherlock/results/text.txt option.
You can use the docker-compose.yml file from the repository and use this command:
docker-compose run sherlock -o /opt/sherlock/results/text.txt user123 We would love to have you help us with the development of Sherlock. Each and every contribution is greatly valued!
Here are some things we would appreciate your help on:
- Addition of new site support ¹
- Bringing back site support of sites that have been removed in the past due to false positives
[1] Please look at the Wiki entry on adding new sites to understand the issues.
Thank you for contributing to Sherlock!
Before creating a pull request with new development, please run the tests to ensure that everything is working great. It would also be a good idea to run the tests before starting development to distinguish problems between your environment and the Sherlock software.
The following is an example of the command line to run all the tests for Sherlock. This invocation hides the progress text that Sherlock normally outputs, and instead shows the verbose output of the tests.
$ cd sherlock/sherlock $ python3 -m unittest tests.all --verbose
Note that we do currently have 100% test coverage. Unfortunately, some of the sites that Sherlock checks are not always reliable, so it is common to get response problems. Any problems in connection will show up as warnings in the tests instead of true errors.
If some sites are failing due to connection problems (site is down, in maintenance, etc) you can exclude them from tests by creating a tests/.excluded_sites file with a list of sites to ignore (one site name per line).
MIT © Sherlock Project
Original Creator — Siddharth Dushantha
Инструменты Kali Linux
Список инструментов для тестирования на проникновение и их описание
Sherlock
Описание Sherlock
Sherlock — это программа на Python, которая на множестве сайтов социальных сетей проверяет, зарегистрирован ли там пользователь с указанным именем, то есть имеется ли учётная запись с таким именем пользователя (ником).
В настоящее время поддерживаются около 300 сайтов, полный список здесь: https://github.com/sherlock-project/sherlock/blob/master/sites.md
Для работы требуется Python 3.6 и выше, данную программу можно запустить на Linux, MacOS и Windows
Справка по Sherlock
sherlock.py [-h] [--version] [--verbose] [--rank] [--folderoutput FOLDEROUTPUT] [--output OUTPUT] [--tor] [--unique-tor] [--csv] [--site ИМЯ_САЙТА] [--proxy PROXY_URL] [--json JSON_FILE] [--proxy_list СПИСОК_ПРОКСИ] [--check_proxies ЧИСЛО] [--timeout TIMEOUT] [--print-found] [--no-color] ИМЯ_ПОЛЬЗОВАТЕЛЯ [ИМЯ_ПОЛЬЗОВАТЕЛЯ . ]
обязательные аргументы: ИМЯ_ПОЛЬЗОВАТЕЛЯ Одно или более имён пользователей для проверки по социальным сетям. Необязательные аргументы: -h, --help показать справку и выйти --version Показать информацию о версии и выйти. --verbose, -v, -d, --debug Показывать дополнительную отладочную информацию и метрики. --rank, -r Выводить веб-сайты в порядке их популярности на основе глобального рейтинга Alexa.com. --folderoutput FOLDEROUTPUT, -fo FOLDEROUTPUT Если для проверки указано несколько имён пользователей, вывод результатов будет сохранён в эту папку. --output OUTPUT, -o OUTPUT Если для проверки указано одно имя пользователя, вывод результатов будет сохранён в этот файл. --tor, -t Делать запросы через Tor; увеличивает время выполнения; требует, чтобы Tor был установлен в системной переменной path. --unique-tor, -u Делать запросы через Tor с новым маршрутом Tor после каждого запроса; увеличивает время выполнения; требует, чтобы Tor был установлен в системной переменной path. --csv Создать файл со значениями, разделёнными запятой (CSV). --site ИМЯ_САЙТА Ограничить анализ только перечисленными сайтами. Добавьте несколько опция для указания более чем одного сайта. --proxy PROXY_URL, -p PROXY_URL Делать запросы через прокси. Например, socks5://127.0.0.1:1080 --json JSON_FILE, -j JSON_FILE Загрузить данные из файла JSON или валидного файла JSON, размещённого онлайн. --proxy_list СПИСОК_ПРОКСИ, -pl СПИСОК_ПРОКСИ Делать запросы через случайные прокси, выбираемые из списка из размещённого в файле .csv. --check_proxies ЧИСЛО, -cp ЧИСЛО Для использования с параметром '--proxy_list'. Будет выполнена проверка на работоспособность и анонимности прокси из файла .csv. Укажите 0 для снятия ограничений на количество прошедших проверку прокси, или укажите другое число для установления лимита. --timeout TIMEOUT Время (в секундах) для ожидания ответа на запрос. По умолчанию равно 60.0s. Более долгий таймаут увеличит шанс получения ответа от медленных сайтов но с другой стороны это может стать причиной долгой задержки для сбора всех результатов. --print-found Не выводить сайты, где имя пользователя не было найдено. --no-color Не раскрашивать вывод в терминал
Руководство по Sherlock
Примеры запуска Sherlock
Найти все профили пользователя в социальных сетях (miloserdov):
Packages and Binaries:
This package contains a tool to find usernames across social networks.
Installed size: 158 KB
How to install: sudo apt install sherlock
- python3
- python3-certifi
- python3-colorama
- python3-openpyxl
- python3-pandas
- python3-requests
- python3-requests-futures
- python3-socks
- python3-stem
- python3-torrequest
sherlock
[email protected]:~# sherlock -h usage: sherlock [-h] [--version] [--verbose] [--folderoutput FOLDEROUTPUT] [--output OUTPUT] [--tor] [--unique-tor] [--csv] [--xlsx] [--site SITE_NAME] [--proxy PROXY_URL] [--json JSON_FILE] [--timeout TIMEOUT] [--print-all] [--print-found] [--no-color] [--browse] [--local] [--nsfw] USERNAMES [USERNAMES . ] Sherlock: Find Usernames Across Social Networks (Version 0.14.3) positional arguments: USERNAMES One or more usernames to check with social networks. Check similar usernames using (replace to '_', '-', '.'). options: -h, --help show this help message and exit --version Display version information and dependencies. --verbose, -v, -d, --debug Display extra debugging information and metrics. --folderoutput FOLDEROUTPUT, -fo FOLDEROUTPUT If using multiple usernames, the output of the results will be saved to this folder. --output OUTPUT, -o OUTPUT If using single username, the output of the result will be saved to this file. --tor, -t Make requests over Tor; increases runtime; requires Tor to be installed and in system path. --unique-tor, -u Make requests over Tor with new Tor circuit after each request; increases runtime; requires Tor to be installed and in system path. --csv Create Comma-Separated Values (CSV) File. --xlsx Create the standard file for the modern Microsoft Excel spreadsheet (xslx). --site SITE_NAME Limit analysis to just the listed sites. Add multiple options to specify more than one site. --proxy PROXY_URL, -p PROXY_URL Make requests over a proxy. e.g. socks5://127.0.0.1:1080 --json JSON_FILE, -j JSON_FILE Load data from a JSON file or an online, valid, JSON file. --timeout TIMEOUT Time (in seconds) to wait for response to requests (Default: 60) --print-all Output sites where the username was not found. --print-found Output sites where the username was found. --no-color Don't color terminal output --browse, -b Browse to all results on default browser. --local, -l Force the use of the local data.json file. --nsfw Include checking of NSFW sites from default list.