- How can I see the password of another user in Linux?
- 1 Answer 1
- You must log in to answer this question.
- Related
- Hot Network Questions
- Subscribe to RSS
- Where and How are Passwords Stored on Linux
- Examining the /etc/passwd File
- Searching User in the /etc/passwd File
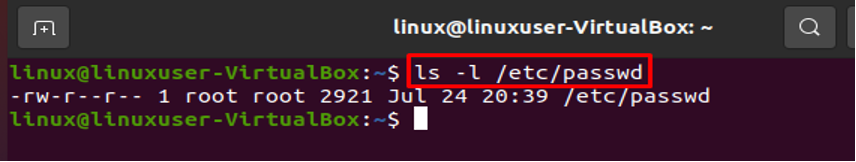
- View the /etc/passwd File’s Permissions
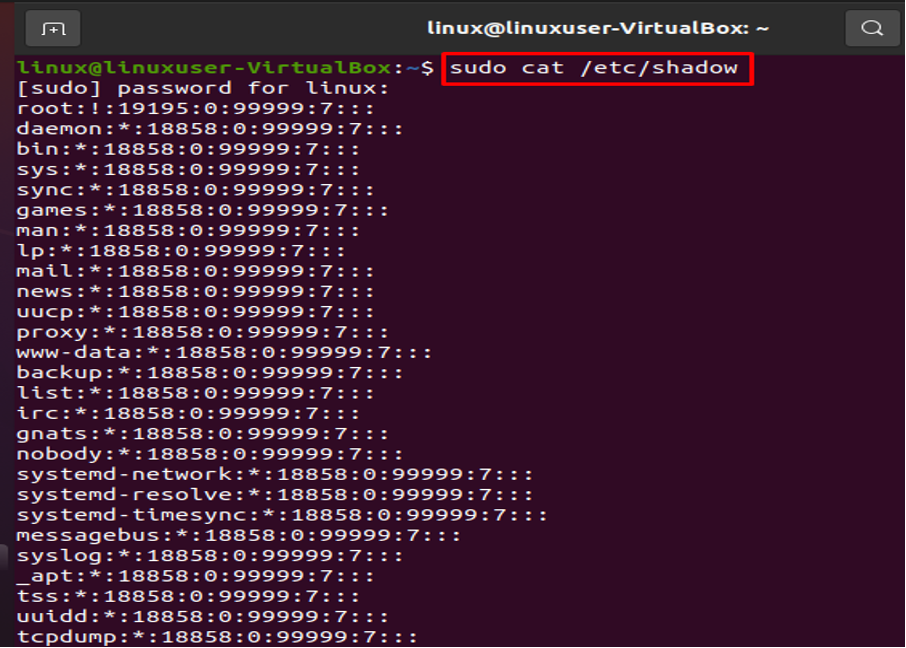
- Examine the File /etc/shadow
- Conclusion
- About the author
- Karim Buzdar
- Where to find password for users created in Ubuntu (16.04)
- 1 Answer 1
- Where my linux password is stored on my system and how i can retrieve it? [duplicate]
- 3 Answers 3
- Linked
- Related
- Hot Network Questions
How can I see the password of another user in Linux?
I made 4 users on my server, but unfortunately I changed the password of the «first» user while configuring the server, but I don’t know how I changed it. How can I see the password of users in root?
1 Answer 1
As root you can change any users password by using the «passwd» command followed by the username;
This will then prompt you to enter the new password twice.
To clarify there is no way to see an existing users password.
@blackcornail Did you copy-paste this error message? It indicates some kind of misconfiguration. Echoing Dayvo, tell us exactly what operating system you’re running (what version etc.), and anything you think might be relevant about its configuration (e.g. do you use NIS/LDAP/…?)
You must log in to answer this question.
Related
Hot Network Questions
Subscribe to RSS
To subscribe to this RSS feed, copy and paste this URL into your RSS reader.
Site design / logo © 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA . rev 2023.7.17.43535
Linux is a registered trademark of Linus Torvalds. UNIX is a registered trademark of The Open Group.
This site is not affiliated with Linus Torvalds or The Open Group in any way.
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.
Where and How are Passwords Stored on Linux
“A username and password for a single account are the primary requirements for accessing a Linux system. In order to verify a user during a system login attempt, all user accounts passwords are saved in a file or database. Finding this file on a user’s machine is beyond the knowledge and abilities of every user. Linux checks the password given by the user against an entry in one or more files located in the directory named “/etc.” when the user logs in with a username and password.
All the crucial data required for user login is stored in the /etc/passwd files. The user’s account information is kept in the /etc/passwd file, to put it another way. The entire list of users on your Linux system is contained in this plain text file. It contains data about the user name, password, group ID, user id, shell, and home directory. Only superuser or root user accounts should have restricted write access permissions.”
This article will show you where and how to save the passwords for system user accounts on Linux distributions.
Examining the /etc/passwd File
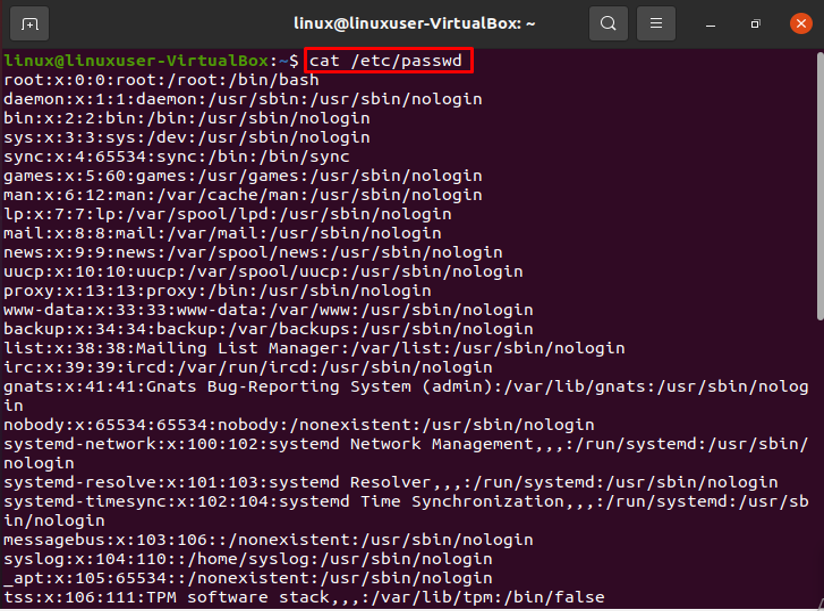
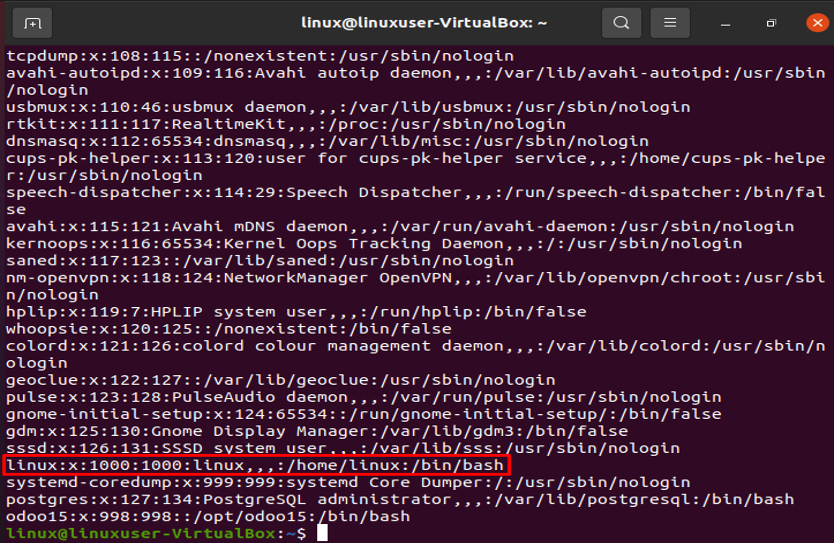
In order to run administrative commands, you must have root access. The details of your system’s user account are in the /etc/passwd file. The colon “:” symbol separates each stored field. The following command will display each entry in the /etc/passwd file:
The command mentioned above will list every user on your Linux system, and hence terminal’s screen will show the following format:
The information about the currently used account is shown in the highlighted portion below.
There are several fields of data divided by colons (:).
Linux: Username is shown in field one. The username field can only have between 1 and 32 characters. Linux is the username in the sample above.
Password (x): The “x” character denotes the encrypted password, as can be seen in the aforementioned example.
UID (1000): Each user must have their own unique user ID. The user ID in the aforementioned screenshot is 1000.
GID (1000): The group ID is represented by the following field. The GID is kept in the file /etc/group. The example indicates that the user is a member of group 1000.
Details (linux): Comments should go in the field below. You can enter further details about the identified person in this box, such as the individual’s complete name, contact information, etc. The user does not offer a phone number in the case above, though.
Home directory (/home/linux): The location of the user’s current home directory is displayed in this field. It will show “/” if the requested directory does not exist.
/bin/bash shell: /bin/bash is the default absolute path for a shell or command.
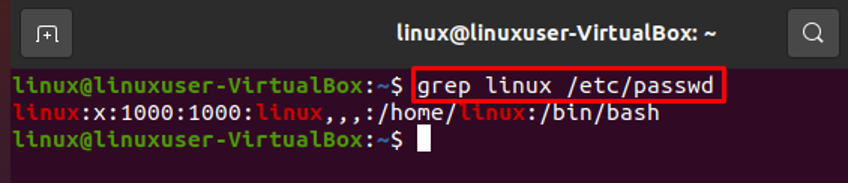
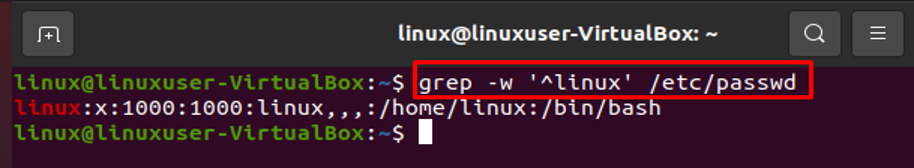
Searching User in the /etc/passwd File
A specific user can be found easily by using the grep command. For instance, if we wish to search for the username “linux” in the /etc/passwd file, we may quickly do it by using the following command, which will save us time:
In this regard, we can also use the following command:
View the /etc/passwd File’s Permissions
As we stated above, the /etc/passwd file must have the owner be superuser or root, and all users other than root should have read rights.
To check the read rights on the file, type the following:
Examine the File /etc/shadow
Your whole encrypted password collection is stored in the root-only /etc/shadow file. Every password is viewable in encrypted form. Let’s execute the next command to show the content:
Conclusion
The aforementioned article demonstrates that the Linux operating system keeps all user account details and passwords in the /etc/passwd file. Additionally, we have seen every encrypted password kept in the /etc/shadow file. To learn more about the user’s group, you can also look through the /etc/group file.
About the author
Karim Buzdar
Karim Buzdar holds a degree in telecommunication engineering and holds several sysadmin certifications. As an IT engineer and technical author, he writes for various web sites. He blogs at LinuxWays.
Where to find password for users created in Ubuntu (16.04)
I’m new to Ubuntu. I have made two ordinary users on my Ubuntu and provided them with the same password. Now I want to check if the passwords are similar but I don’t know where to look for or what command to write in a terminal. Where do I find /etc/password ?.
1 Answer 1
There are two main files related to system user authentication: /etc/passwd and /etc/shadow . The actual user’s passwords are stored as hashed version in the shadow file. They are hashed by the crypt function. It is not possible to «decrypt» any password from the shadow file, because hashing is one way mechanism.
Most simply: When the user enters а password, it is processed and compared to the hashed password stored in the shadow file. But when one try to «decrypt» a password from the shadow file — there are over than thousands possible results.
/etc/passwd contains one line for each user account, with seven fields delimited by colons ( : ).
These fields are: 1. login name; 2. optional encrypted password; 3. UID; 4. GID; 5. user name or comment field; 6. user home directory; 7. optional user command interpreter.
The encrypted password field may be blank, in which case no password is required. However, some applications which read the /etc/passwd file may decide not to permit any access at all if the password field is blank.
If the password field is a lower-case x , then the encrypted password is actually stored in the shadow file instead; there must be a corresponding line in the /etc/shadow file, or else the user account is invalid. If the password field is any other string, then it will be treated as an encrypted password, as specified by crypt . (source: man passwd )
/etc/shadow — shadowed password file — is a file which contains the password information for the system’s accounts and optional aging information. Each line of this file contains 9 fields, separated by colons ( : ).
The fields are: 1. login name; 2. encrypted password — refer to crypt for details on how this string is interpreted; 3. date of last password change; 4. min password age; 5. max password age; 6. password warning period; 7. password inactivity period; 8. account expiration date; 9. reserved field. (source: man shadow ).
Where my linux password is stored on my system and how i can retrieve it? [duplicate]
I am currently logged in on my Linux system and i want to output my Linux password and username on my terminal, what commands i need to write and in which file it is stored and how i can retrieve it ?
3 Answers 3
In short: you can’t find out what your password is.
Although it’s stored in the file /etc/shadow , it’s stored in a «protected» format called a hash. It’s like a baked cake is to a set of ingredients, there’s no way to get the flour back out of the cake.
The passwords are not stored anywhere on the system at all. What is stored in /etc/shadow are so called hashes of the passwords.
A hash of some text is created by performing a so called one way function on the text (password), thus creating a string to check against. By design it is «impossible» (computationally infeasible) to reverse that process.
What can be done is to try a «brute force» attack — by hashing a lot of possible passwords until the outcome equals the found hash. There is no other way, you cannot compute a text (=password) that matches the hash you have.
There are several algorithms to create hashes, they differ in complexity, length of the hash, probability/possibility of so called collisions (two different texts have the same hash, which eventually must happen if the hash is shorter than the original text).
Typical current algorithms are
both should not be used for cryptographic/security purposes any more!!
- SHA-256
- SHA-512
- SHA-3 (KECCAK was announced the winner in the competition for a new federal approved hash algorithm in October 2012) — not used in Ubuntu yet.
As you know from other answers you can’t see your password. Let me explain why. Design where passwords are stored in their normal form (it’s called plain) isn’t very secure (not only for operating systems) because if list of such passwords falls into hands of malicious person, he can log in instantly, since list of user names is usually easy to retrieve (in Linux from /etc/passwd file). That’s why hash functions are used instead. These are one-way functions — you can create hash based on value but you can’t create value based on hash. If malicious person gets a list of hash values he can’t retrieve actual passwords from them (or at least it’s more difficult) and user still can login — when he passes his password, it’s translated to hash and compared with stored value.
Once in a while you can heard that someone hacked some website and get passwords or that some list of passwords leaked somewhere. If those were stored in plain text, attacker got instant access to some accounts. If those were hashed he had to break them first. It means more trouble for him and more time for reaction like changing a password to a new one. Linux (and any Unix based system) follows this design and that’s why you can’t print your password in any other way that hashed — only if you have root user privileges and can read /etc/shadow file.
To print your username, type whoami .
Linked
Related
Hot Network Questions
Site design / logo © 2023 Stack Exchange Inc; user contributions licensed under CC BY-SA . rev 2023.7.17.43535
Ubuntu and the circle of friends logo are trade marks of Canonical Limited and are used under licence.
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy.