- Saved searches
- Use saved searches to filter your results more quickly
- gnos-project/gnos-vpngate
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
- Easily Use Free VPNs From VPN Gate In Linux With These 2 Tools
- VPNGate With Proxy
- autovpn
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
🌉 VPN Gate Linux client for Softether SSL-VPN protocol
gnos-project/gnos-vpngate
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
VPN Gate Linux client for Softether SSL-VPN protocol
Written with bash & node.js for GNOS.
- Configurable profiles
- Linux netns isolation
- Scrap VPN Gate using phantomjs
- SYN Scan to check servers latency
- Filtering & Selection using jq
- Supports both pkexec & sudo
- Softether SSL-VPN protocol
- HTTP & SOCKS4 proxy support
- Managed DHCP: dhclient
- Automatic dependency installation (Ubuntu)
NAME: vpngate DESC: VPN Gate client for SoftEther VPN-SSL protocol AUTH: elias@gnos.in DEPS: SoftEther vpnclient + vpncmd DEPS: policykit-1 isc-dhcp-client npm jq FEAT: polkit integration GUI server selector scapping to JSON cache jq filtering & selection auto $http_proxy support HTTP & SOCKS4 proxy support netns (Linux network namespaces) user profiles with command execution USAGE: vpngate [ OPTS . ] [ PROFILE_NAME | PROFILE_PATH [ COMMAND [ ARGS . ] ] ] vpngate -d PROFILE_NAME vpngate -l vpngate -h ARGS: PROFILE_NAME Profile name, stored in ~/.config/vpngate/ PROFILE_PATH Profile path COMMAND Command to execute, or "null" to keep connected ARGS Command arguments OPTS: -d Disconnect profile -l List active profiles -h Show help -r Force reconnect -u Force cache update -p HTTP_PROXY HTTP proxy: [http://][user[:password]@]host[:port] -s SOCKS_PROXY SOCKS4 proxy: [socks://][user[:password]@]host[:port] -g GUI server selector -v Verbose output PROFILE-FORMAT: BASH cmd Command to execute proxy HTTP proxy socks SOCKS4 proxy filter [VPN Gate] Server-list filter, jq select syntax select [VPN Gate] Server-list sorter, jq sort_by syntax connect [VPN] Private server, see args: vpnssl-connect -h Profiles are stored in ~/.config/vpngate .
Profiles files are simple bash declarations.
| Variable | Default | Description |
|---|---|---|
| filter | ‘true’ | jq select() expression |
| select | ‘.»SYN scan (ms)»‘ | jq sort_by() expression |
| mirror | «» | Alternative Scrapping url |
connect replaces Scrapping/Filtering/Scanning/Selecting.
| Variable | Default | Description |
|---|---|---|
| connect | » | Connection string |
IP_ADDR TCP_PORT [ USER_NAME PASSWORD [HUB_NAME] ] Default USER_NAME is vpn with empty PASSWORD , default HUB_NAME is vpngate .
# Private server connect='1.1.1.1 443 my_username "s3cr3t" HUB' # Forced VPN Gate server: NO credentials required connect='2.2.2.2 443' | Variable | Default | Description |
|---|---|---|
| cmd | ‘bash’ | Command to execute, or «null» to keep connected |
| proxy | » | HTTP proxy |
| socks | » | SOCKS proxy |
cmd='curl -sSL https://wtfismyip.com/text' cmd='firejail firefox' Content is eval -ed so you can write complex commands but beware of security implications:
cmd='true ; echo "Executed as $(id -u) out of isolation [$(ip netns identify $$)]" ' Also have fun with quoting:
cmd="bash -c 'echo \"quoted text\"'" cmd='bash -c '\''echo "quoted text"'\' Application defaults overrides
| Variable | Default | Description |
|---|---|---|
| cacheSeconds | 7200 | Scrapping cache validity in seconds |
| verbose | «» | Set to -v to force verbose output |
| reconnect | «» | Set to -r to force reconnection |
| update | «» | Set to -u to disable cache |
| gui | «» | Set to -g to enable GUI server selector |
| mirror | «» | Scrapping url, read https://bunkerbustervpn.com/vpngate.html |
- Softether vpnclient , integrated with systemd .
- Softether vpncmd , declared in PATH .
- Node.js (lts/10), managed by nvm .
- OPTIONAL, yad for GUI
Put files somewhere, for example /opt/vpngate .
Auto dependencies installation
Tested on latest Ubuntu with NPM configured to run npm install -g without sudo.
This will call pkexec to gain privileges and pull missing dependencies:
Manual dependencies installation
sudo apt-get install npm jq isc-dhcp-client yad sudo npm install -g phantomjs casperjs sudo mkdir /opt/vpngate/node_modules sudo chown $(id -u) /opt/vpngate/node_modules npm install ip local-ipv4-address raw-socket # sudo chown -hR root:root /opt/vpngate/node_modules To use sudo instead of default automatic pkexec use this alias:
alias vpngate="sudo --set-home NVM_BIN='$NVM_BIN' /opt/vpngate/vpngate -v" Set $SUDO_UID to empty to run command as root, not recommended.
alias vpngate="sudo --set-home SUDO_UID= NVM_BIN="$NVM_BIN" /opt/vpngate/vpngate -v" VPN Gate Scrapping cache is kept at ~/.cache/vpngate/cache.json
VPN Gate Profile cache at ~/.cache/vpngate/PROFILE_NAME/vpngate_.json
DHCP caches are ~/.cache/vpngate/PROFILE_NAME/dhclient
JSON array of objects, named data , attributes:
"Country code" str notnull empty! "DDNS hostname" str null! "IP address" str notnull notempty "ISP hostname" str null! "Cumulative users" int null! "Cumulative transfers (GB)" int null! "Operator" str null! "Ping (ms)" int null! "Score" int null! "SSL-VPN TCP port" int notnull "SYN scan (ms)" int notnull "Throughput (Mbps)" int null! "Uptime (min)" int null! "VPN sessions" int null! About
🌉 VPN Gate Linux client for Softether SSL-VPN protocol
Easily Use Free VPNs From VPN Gate In Linux With These 2 Tools
In case you’re not familiar with VPN Gate, this is project that offers free VPN servers that are ran by volunteers who use SoftEther. It was designed with the Great Firewall of China in Mind and is sponsored by the University of Tsukuba, Japan.
It’s important to note that free VPNs are insecure, and they shouldn’t be used for sensitive / important stuff!
VPNGate With Proxy
- allows connecting to free OpenVPN servers at VPN Gate directly or through proxy;
- adds DNS to fix DNS leak;
- automatically filters out dead VPN servers;
- can execute user defined script after vpn_tunnel is established or broken;
- multiple interfaces: two command line interfaces (a lightweight interface aimed to run on a server, and a terminal interface with a better UI, colors, and easier to use) as well as an AppIndicator;
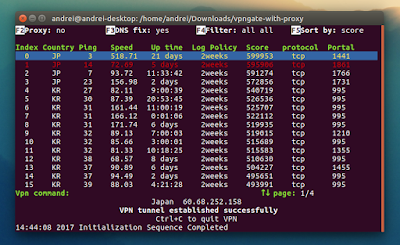
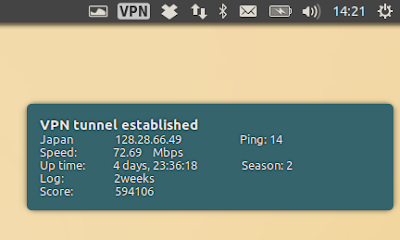
- displays VPN server country, ping, speed, up time, log policy, score, protocol and port in the command line interfaces.
According to its developer, the application has been tested on Ubuntu, Raspbian and Fedora, and may not work with other Linux distributions.
To run VPNGate With Proxy, you’ll need Python 2.7.x, python-requests, openvpn, resolvconf, python-urwid 1.3+ (only if you want to use the advanced terminal user interface, called «tui»), wmctrl and realpath.
For the AppIndicator you’ll also need gir1.2-appindicator3-0.1, gir1.2-notify-0.7 and python-gobject.
sudo apt install python-requests openvpn resolvconf python-urwid wmctrl realpath gir1.2-appindicator3-0.1 gir1.2-notify-0.7 python-gobject gitNext, clone the VPNGate With Proxy GitHub repository and run the application (with the advanced terminal user interface) using the commands below:
git clone https://github.com/Dragon2fly/vpngate-with-proxy.git cd vpngate-with-proxy ./run tuiOn older systems, if python-urwid version 1.3 is not available, VPNGate With Proxy will automatically install it via python-pip.
The application GitHub page provides instructions for how to clone the repository if you’re behind a proxy. You can also download the repository as an archive.
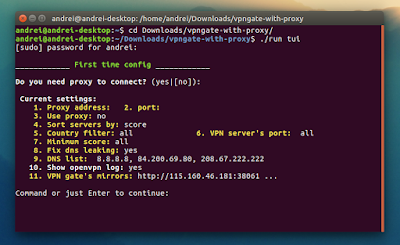
The first time you run VPNGate With Proxy, it will run the initial configuration, which includes proxy configuration (if you don’t use a proxy to connect to the Internet, simply press ENTER), etc.:
Once you’re done with the initial configuration, the application will download a list of OpenVPN servers from VPN Gate — to connect to a VPN, enter its number and press ENTER:
You can sort the VPN list by score (default), ping, speed or uptime. To do this, press F5 and select the sort option.
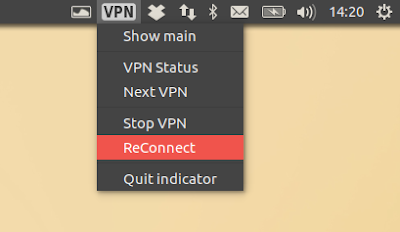
The VPNGate With Proxy AppIndicator should start automatically when running the application. Using it, you can easily stop the VPN, reconnect, choose the next VPN, or show the VPN status:
To see if the VPN is working, you can check your IP by visiting VPN Gate (or any of the many websites that offer this service).
autovpn
autovpn is a small and simple command line tool written in Go, which allows connecting to a random free VPN. Under the hood, autovpn uses OpenVPN to connect to free VPN servers from VPN Gate.
To install and use autovpn, you’ll need to install golang-go, openvpn (autovpn depends on it) and git (to clone the autovpn GitHub repository). In Debian, Ubuntu or Linux Mint, you can install these packages using the following command:
sudo apt install golang-go openvpn gitgit clone https://github.com/adtac/autovpn cd autovpn go build autovpn.goAnd finally, install the generated executable — using the command below, the autovpn executable is installed in /usr/local/bin/:
sudo install autovpn /usr/local/bin/autovpn is extremely easy to use — all you have to do is run it and it will automatically connect you to a VPN. By default (without specifying a country code), it connects to a random US server:
If you want to use a VPN from another country, add the country code, like this (the command below is an example to connect to a free VPN server from Japan):
Not all country codes will work, since autovpn relies on the VPN Gate iPhone API, which returns around 100 VPN servers, and the country you want to use a VPN from may or may not be in this server list.
To see if the VPN is working, you can check your IP by visiting VPN Gate (or any of the many websites that offer this service).