Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
WebSpy, A fork from uptime
License
brantje/webspy
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
A remote monitoring application using Node.js, MongoDB, and Twitter Bootstrap.
- Monitor thousands of websites (powered by Node.js asynchronous programming)
- Tweak frequency of monitoring on a per-check basis, up to the second
- Check the presence of a pattern in the response body
- Receive notifications whenever a check goes down
- On screen (powered by socket.io)
- By email
- On the console
WebSpy 0.5 requires Node.js 0.10.25 and MongoDB 2.1. Older versions provide compatibility with Node 0.8 (Uptime v3.1) and 0.6 (Uptime v1.4).
To install from GitHub, clone the repository and install dependencies using npm and bower :
$ git clone git://github.com/fzaninotto/uptime.git $ cd uptime $ npm install $ bower installNext install reddis server, this is only necessary when you use cluster config.
wget http://download.redis.io/releases/redis-2.8.19.tar.gz tar xzf redis-2.8.19.tar.gz cd redis-2.8.19 make sudo make install cd utils sudo ./install_server.sh
Lastly, start the application with:
By default, the web UI runs on port 8082, so just browse to
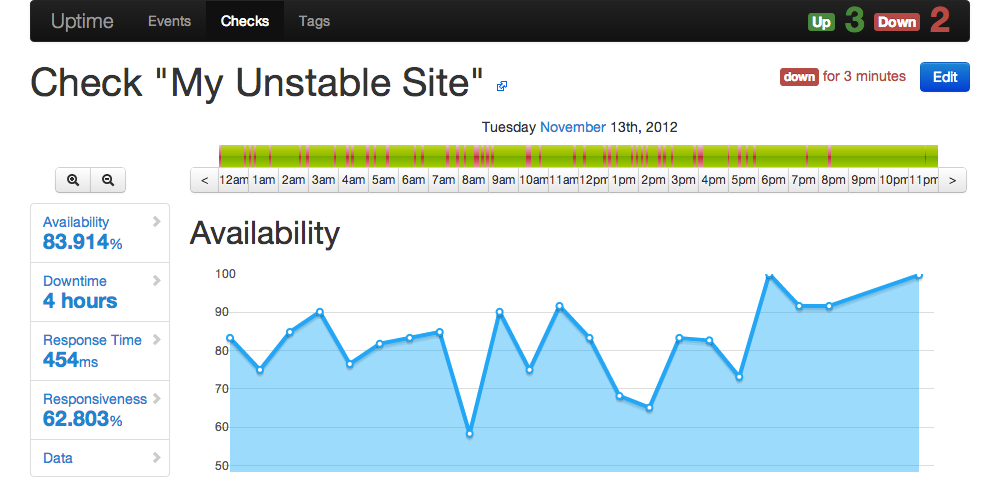
And you’re ready to begin. Create your first check by entering an URL, wait for the first ping, and you’ll soon see data flowing through your charts!
WebSpy uses node-config to allow YAML configuration and environment support. Here is the default configuration, taken from config/default.yaml :
url: 'http://localhost:8082' mongodb: server: localhost database: uptime user: root password: connectionString: # alternative to setting server, database, user and password separately monitor: name: origin apiUrl: 'http://localhost:8082/api' # must be accessible without a proxy pollingInterval: 10000 # ten seconds timeout: 5000 # five seconds userAgent: NodeUptime/2.0 (https://github.com/fzaninotto/uptime) analyzer: updateInterval: 60000 # one minute qosAggregationInterval: 600000 # ten minutes pingHistory: 8035200000 # three months autoStartMonitor: true plugins: - ./plugins/console - ./plugins/patternMatcher - ./plugins/httpOptions # - ./plugins/email
To modify this configuration, create a development.yaml or a production.yaml file in the same directory, and override just the settings you need. For instance, to run WebSpy on port 80 in production, create a production.yaml file as follows:
Node that WebSpy works great behind a proxy — it uses the http_proxy environment variable transparently.
By default, WebSpy uses regular HTTP on the API and monitor server, but it’s possible to enable SSL for encrypting the connection to your monitor instance. The settings for this are located in the config/default.yaml file:
ssl: enabled: true certificate: uptime.crt # path to certificate file key: uptime.key # path to key file selfSigned: false
You must specify true for the selfSigned option when using a self-signed certificate, otherwise Node.js will throw an «UNABLE_TO_VERIFY_LEAF_NODE» error and will not poll.
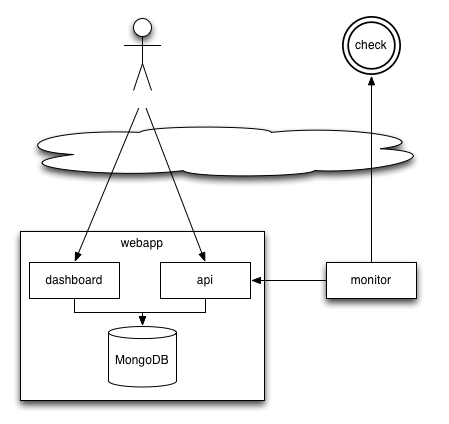
WebSpy is composed of two services: a webapp (in app.js ), and a polling monitor (in monitor.js) . For your convenience, the two services start together when you call node app .
However, heavily browsing the webapp may slow down the whole server — including the polling monitor. In other terms, using the application can influence the uptime measurements. To avoid this effect, it is recommended to run the polling monitor in a separate process.
To that extent, set the autoStartMonitor setting to false in the production.yaml , and launch the monitor by hand:
You can also run the monitor in a different server. This second server must be able to reach the API of the webapp server: set the monitor.apiUrl setting accordingly in the production.yaml file of the monitor server.
Monitoring From Various Locations
You can even run several monitor servers in several datacenters to get average response time. In that case, make sure you set a different monitor.name setting for all monitor servers to be able to tell which server make a particular ping.
Plugins can add more notification types, more poller types, new routes to the webapp, etc. Uptime currently bundles three plugins:
- console : log pings and events in the console in real time
- email : notify events (up, down pause) by email
- patternMatcher : allow HTTP & HTTPS pollers to test the response body against a pattern
- httpOptions : add custom HTTP options and headers to HTTP and HTTPS checks (e.g. to allow self-signed certificate on HTTPS, custom headers, custom HTTP methods, . )
- basicAuth : add HTTP Basic Access Authentication to the dashboard and API applications
To enable plugins, just add a line to the plugins: section of the configuration file. Three of the bundled plugins are already enabled by default:
# in config/default.yaml plugins: - ./plugins/console - ./plugins/patternMatcher - ./plugins/httpOptions # - ./plugins/email # - ./plugins/basicAuth
You can override these settings in your environment configuration, for instance:
# in config/production.yaml # disable the console plugin and enable the email plugin plugins: # - ./plugins/console - ./plugins/patternMatcher - ./plugins/httpOptions - ./plugins/email # - ./plugins/basicAuth
- webhooks : notify events to an URL by sending an HTTP POST request
- campfire : notify events to Campfire
- pushover : Notify events to mobile devices
A plugin is a simple Node.js module which hooks into predefined extension points. Uptime automatically requires plugin modules when starting the webapp and the monitor, and tries to call the two following functions:
- initWebApp(options) when starting the webapp
- initMonitor(options) when starting the monitor
Check the app.js and monitor.js to see a detail of the options passed to each hook. Also, check the code of existing plugins to understand how they can add new pollers, new notification types, etc.
For instance, if you had to recreate a simple version of the console plugin, you could write it as follows:
// in plugins/console/index.js var CheckEvent = require('../../models/checkEvent'); exports.initWebapp = function() CheckEvent.on('afterInsert', function(checkEvent) checkEvent.findCheck(function(err, check) console.log(new Date() + check.name + checkEvent.isGoDown ? ' goes down' : ' goes back up'); >); >); >
All WebSpy entities emit lifecycle events that you can listen to on the Model class. These events are beforeInsert , afterInsert , beforeUpdate , afterUpdate , beforeSave (called for both inserts and updates), afterSave (called for both inserts and updates), beforeRemove , and afterRemove . For more information about these events, check the mongoose-lifecycle plugin.
All API requests should be prefixed with api . The API response always uses the application/json mimetype. API requests do not require authentication.
Example of a valid API request:
Example for a valid API request using curl :
curl -i -H «Accept: application/json» -X PUT -d «name=example» -d «url=http://mysite.com» -d «interval=120» http://example.com/api/checks
The API is designed to return different status codes :
- 200 Ok : The request was successful, the resource(s) itself is returned as JSON
- 400 Bad Request : An attribute of the API request is invalid or missing (e.g. the url of a check is missing)
- 404 Not Found : A resource could not be accessed (e.g. a check ID could not be found)
- 500 Server Error : Something went wrong on the server side (e.g. a check could not be saved in database)
Return a list of all checks
Return a list of checks that need a poll (i.e. not paused, plus new or last tested > interval set between tests)
Toggle the status (isPaused) of a check
Updates the last checked date for a check. Used to avoid double check when a target is slow. Return the number of affected records in the database (1 or 0).
Return a list of all pings
- ?page=1 : (optional) Paginate results by 50
- ?check=:id : (optional) Return only the pings for a given check
Return a list of events (CheckEvent) aggregated by day, limited to the latest week, and to 100 results
Create a ping for a check, if the check exists and is not already polled
- checkId : (required) Id of the check
- status : (required) Status
- timestamp : (optional) Date of polling
- time : (required) Response time
- name : (optional) Monitor name
- error : (optional)
- details : (optional)
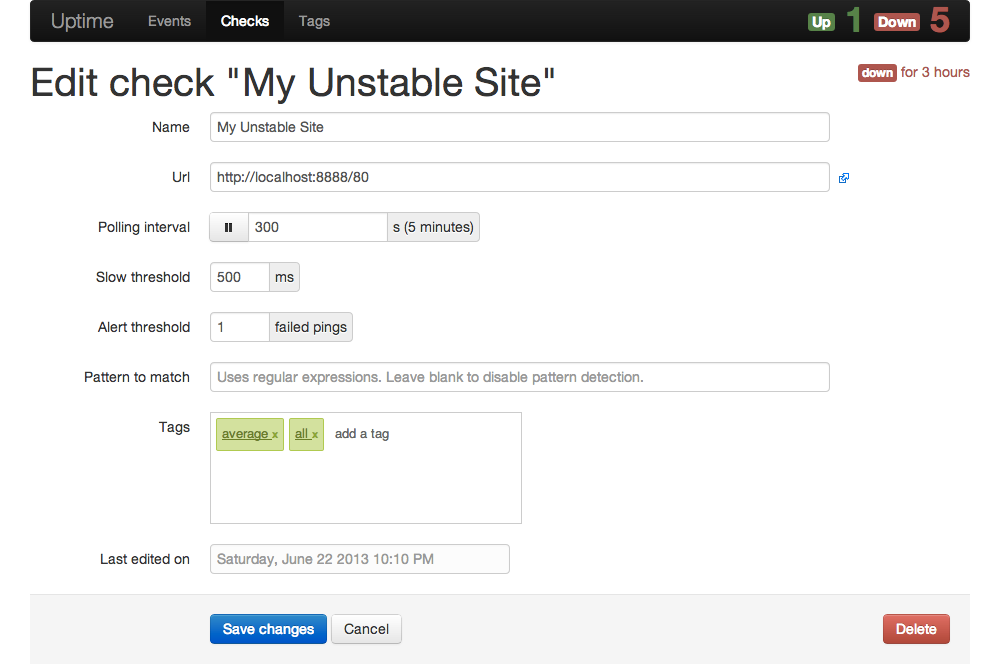
Create a new check and return it
- url : (required) Url of the check
- name : (optional) Name of the check — if empty, url will be set as check name
- interval : (optional) Interval of polling
- maxTime : (optional) Slow threshold
- isPaused : (optional) Status of polling
- alertTreshold : (optional) set the threshold of failed pings that will create an alert
- tags : (optional) list of tags (comma-separated values)
- type : (optional) type of check (auto|http|https|udp)
Update a check and return it
- id : (required) Id of the check
- url : (optional) Url of the check
- name : (optional) Name of the check — if empty, url will be set as check name
- interval : (optional) Interval of polling
- maxTime : (optional) Slow threshold
- isPaused : (optional) Status of polling
- alertTreshold : (optional) set the threshold of failed pings that will create an alert
- tags : (optional) list of tags (comma-separated values)
- type : (optional) type of check — values : auto | http | https | udp
Webspy in kali linux
Various tools to sniff network traffic for cleartext insecurities
- Maintainer: Debian Security Tools <[email protected]>
- Homepage:http://www.monkey.org/~dugsong/dsniff/
- Section: net
Install
Debian apt-get install dsniff
Arch Linux pacman -S dsniff
Kali Linux apt-get install dsniff
dsniff
Various tools to sniff network traffic for cleartext insecurities
This package contains several tools to listen to and create network traffic: * arpspoof — Send out unrequested (and possibly forged) arp replies. * dnsspoof — forge replies to arbitrary DNS address / pointer queries on the Local Area Network. * dsniff — password sniffer for several protocols. * filesnarf — saves selected files sniffed from NFS traffic. * macof — flood the local network with random MAC addresses. * mailsnarf — sniffs mail on the LAN and stores it in mbox format. * msgsnarf — record selected messages from different Instant Messengers. * sshmitm — SSH monkey-in-the-middle. proxies and sniffs SSH traffic. * sshow — SSH traffic analyser. * tcpkill — kills specified in-progress TCP connections. * tcpnice — slow down specified TCP connections via «active» traffic shaping. * urlsnarf — output selected URLs sniffed from HTTP traffic in CLF. * webmitm — HTTP / HTTPS monkey-in-the-middle. transparently proxies. * webspy — sends URLs sniffed from a client to your local browser (requires libx11-6 installed). Please do not abuse this software.
API – webspy
An ASCII, decimal, hexadecimal, octal dump. More information: .
Report CPU statistics. More information: .
An alternative to find. Aims to be faster and easier to use than find. More information: .
debhelper script for zope packaging
Central Test Node, a DICOM implementation for medical imaging
Perl module to patch perl source à la Devel::PPPort’s buildperl.pl
Tools for the Observational Data Processing (ODB) API