How Smart Locks and Bluetooth
Work to Keep Your Home Safe
Guest blog by Ralph Goodman, the lead writer on all things locks and security over at the Lock Blog. The Lock Blog is a great resource to learn about keys, locks, safety, and locksmith services. They offer tips, advice and how-to’s for consumers, locksmiths, and security professionals. For more information about United Locksmith, follow them on social media on Twitter, Facebook, and Pinterest.
In part one of this how-to series, we covered how home automation is impacting the future of home security and provided some background information about Bluetooth ® technology. Now, let’s continue.
Bluetooth and Smart Locks
Years from now, people are going to look back and view smart locks and home automation as a key part of history, and there is no doubt that Bluetooth will be a huge part of those conversations, just as it is now.
There are many questions that people raise when it comes to smart locks and their use of Bluetooth. Is it safe enough? Will anyone with Bluetooth ® capabilities on their phone be able to walk right into my home? Will I be hacked? Each and every one of those questions is supremely valid and they have been addressed by Bluetooth and many smart lock manufacturers.
Every device that has Bluetooth capabilities benefits from the security practices Bluetooth devices have in place. Bluetooth security has standards that authenticate, authorize, encrypt, and keep your data private. This is done in order to make sure that unauthorized persons do not have access to your devices. Bluetooth also encrypts the data that is transferred between paired devices to make it much more difficult for anyone to get a hold of your private information.
It wouldn’t be much help if someone with a Bluetooth enabled device was able to open your door simply by being there, would it? Smart locks are paired with a primary device, which in most cases is a smartphone. Once your smartphone has been set up as a primary device, your lock can only be operated (unless you use a physical key) from your phone and from whomever you grant access to (in the form of temporary keys or additional users).
For further clarification, let us take a look at the Kwikset Kevo. The Kevo is one of the leading smart lock brands that utilize Bluetooth. When homeowners are installing the Kwikset Kevo, the lock has to be paired with the homeowner’s smartphone via the Kevo app. A back section of the lock is removed and the programming button is pressed in order for the lock to be made visible. This is done to allow the lock to communicate with your phone and establish it as the primary device. Once the primary device has been established, the lock will only respond to that device and any other devices that are added to that network through the Kevo app.
PICTURE SOURCE: http://august.com
The same concept applies to other smart locks, like the August Smart Lock for example. Once the lock has been installed in the door, homeowners will have to download the August App, enable their Bluetooth connectivity, and scan the lock with their phones in order to pair the devices together. Once the lock has been connected to a primary device, it cannot be paired to another device without authorization from the primary device.
Security and convenience need to be balanced and well thought through when it comes to devices that concern our homes and our information. Smart locks manufacturers and developers have looked at ways to provide both, bringing the highest levels of trusted security while also giving you the ability to provide one-off key access with limitations to allow visiting family members or a housekeeper to access your house without you being there but only when you allow it.
The security features of Bluetooth, coupled with the additional security features that these smart locks have, work to keep you safe. This is done mainly by designating the primary devices that are allowed to exchange data with your lock and other smart devices.
The latest version of Bluetooth, Bluetooth 4.2, boasts enhanced privacy safeguards as well as AES (Advanced Encryption Standard) 128-bit encryption. Needless to say, that’s a whole lot of security.
How Do Smart Locks And Bluetooth Keep Your Home Safe?
Smart locks with Bluetooth capabilities keep your home safe in a variety of ways, and Bluetooth ® technology has a major role to play in all of these variations. First, Bluetooth is in use in so many different products, as compared to competing technologies. Almost every smartphone comes equipped with Bluetooth, and the same can be said for the vast majority of smart devices on the market. With so many smart devices being capable of using and communicating with Bluetooth, it makes it much easier for homeowners to integrate their smart locks with other smart devices. This casts a much wider safety net, which will help keep homeowners safe.
Also, in comparison to smart locks and smart devices that run solely on Wi-Fi connectivity or other similar protocols, Bluetooth devices are much safer, especially with the advent of the low energy feature of Bluetooth. Smart locks and smart devices with these capabilities do not have to be constantly connected to the Internet, which drastically reduces the chances of someone hacking into your home. In addition to this, they operate with the minimal use of power, which in turn makes them long lasting and efficient. These two features go hand in hand to make it nearly impossible for someone to infiltrate your network. Bluetooth transmissions are also done through adaptive frequency hopping. This doubly ensures that the proper transmissions are being sent from one point to another without any external interference.
The main flaw of Bluetooth transmissions over ad hoc networks is the lack of network access control, however, this issue is nullified by authentication methods that make sure that only authorized ‘nodes’ can inject traffic into a network. In this case, your smartphone would be the authorized node attempting to communicate with your smart lock.
Conclusion
There is no doubt that Bluetooth ® technology will have a hand in shaping the future of home security. It is already a major talking point when home automation is being discussed and with good reason. Bluetooth continues to pave the way to making life more secure, convenient and efficient and smart locks and home automation devices are just a small part of the big picture.
The Bluetooth smart lock which spoke too much
A few years ago, looking for something fun to do, we stumbled upon what seemed to be a nice Bluetooth Smart Lock on Amazon. It was controlled by a mobile application (Android or iOS), supposedly compliant to lock anything (from your scooter to your dungeon’s cave) and cost around 30€ with possible refund without any question asked. We thought this could be a nice project to look at its security, especially at the communication level.
Android application main screen
First thing first, we have to register the device and set up the app. To do this, you have to wake up the lock by pressing a button. It then waits for incoming connections. Using the mobile application, you create an account on the vendor’s website and then send the default password (000000) to the lock. And that’s it! You’re done! You can now do anything: change its password, query log information (with dates and location), rename it, etc. We set our lock password to 123789.
Communication analysis
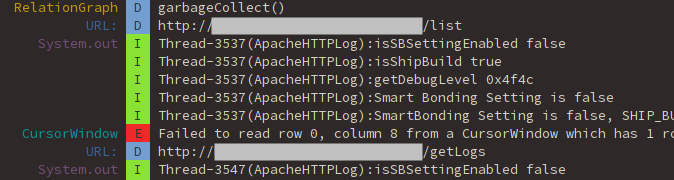
The communication is based on Bluetooth 4.0. We used BlueFruit LE Sniffer to intercept it, and Wireshark/tshark to display the capture.
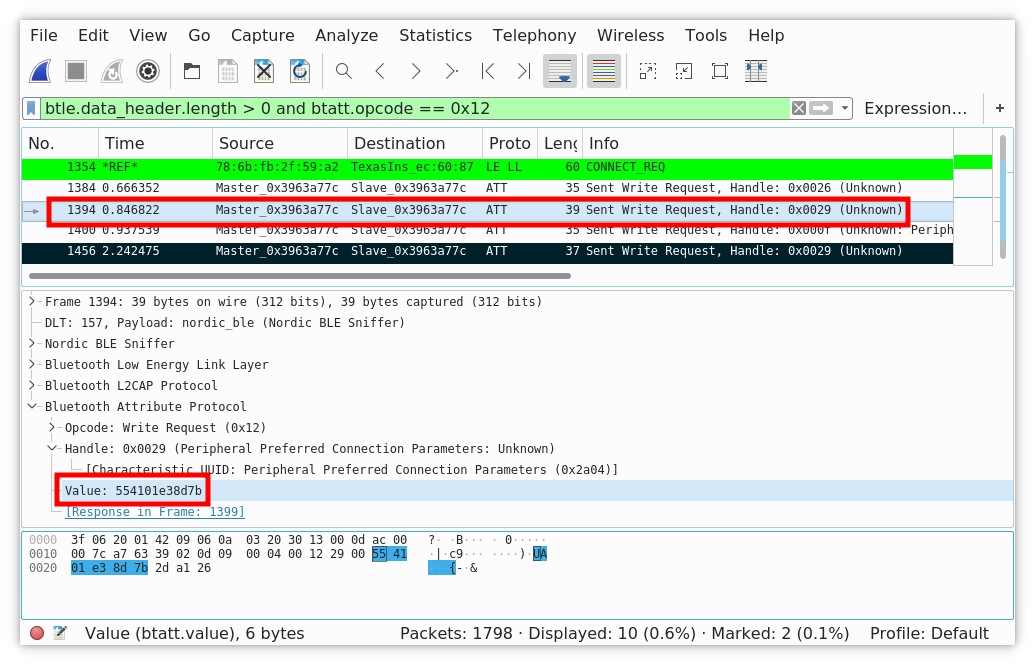
We recorded the communication when we opened the lock with its password. The frame analysis enabled us to spot precious information: our password value in hexadecimal: 0x01E38D. The command delivering the password to the lock is likely to be identified: 0x554101E38D7B.
We can quickly identify the frame sending the password.
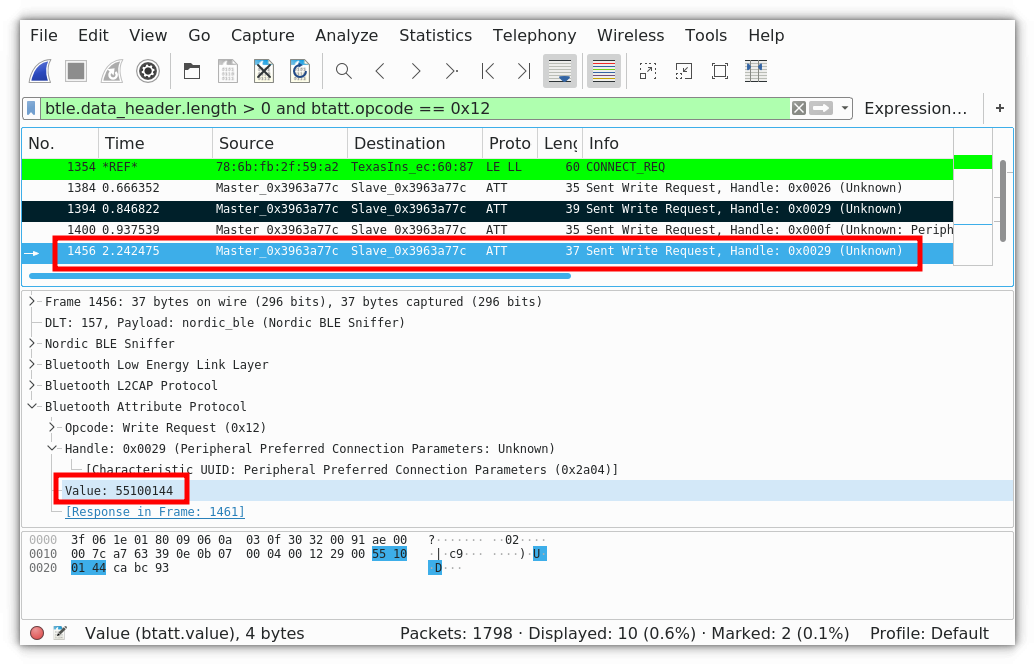
We examined the frames after this one, and found a potential candidate for the command opening the lock: 0x55100144.
The frame opening the lock.
We did this multiple times and each time the password was sent in clear and the opening command was the same. It seemed to us that no cryptography was implemented at the communication level. This allowed us to replay the frame sequence to authenticate and open the lock, or pair another mobile with it since we can intercept its password.
Well, that’s it! If we come back to our analogy with physical locks:
- Opening it with cutting pliers lets an obvious sign of a break-in, while we can open the smart lock without leaving any trace.
- Another option would be to lockpick it, but it requires skills, and above all if someone sees you, it is difficult to say that you are the legitimate owner. The smart lock communication can be sniffed cheaply within a few meter range. So, it can be recovered quickly without drawing attention.
As we were a little disappointed by this part, we then analyzed the Android application, desperately looking for a security mechanism we would have missed.
Android Application
The Android application shares the same level of security. The analysis is straightforward:
- There is no anti-tampering or anti-hooking mechanisms,
- The code is not obfuscated,
- The protocol can be easily inferred, and it confirms our previous observations.
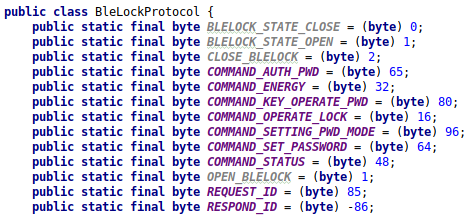
Method to build the authentication command.
Thanks to this code, we can now translate the data in the frames we identified earlier:
- 0x55: REQUEST_ID
- 0x41: COMMAND_AUTH_PASSWORD
- 0x01E38D: PIN
- 0x7B: Checksum
And, the second one to open the lock:
The code analysis confirmed our hypothesis with the sniffed frames. So, crafting and installing a malware targeting the password thief is straightforward.
I can see you coming! “Meh, just another IoT device with no security!” But that’s not all, folks! Just out of curiosity, we went a little further and checked the communications with the server. And oh my! We were not disappointed!
Server Privacy Data Leakage
Indeed, if we continue to analyze the application, a simple logcat gives a lot of information, especially two URLs:
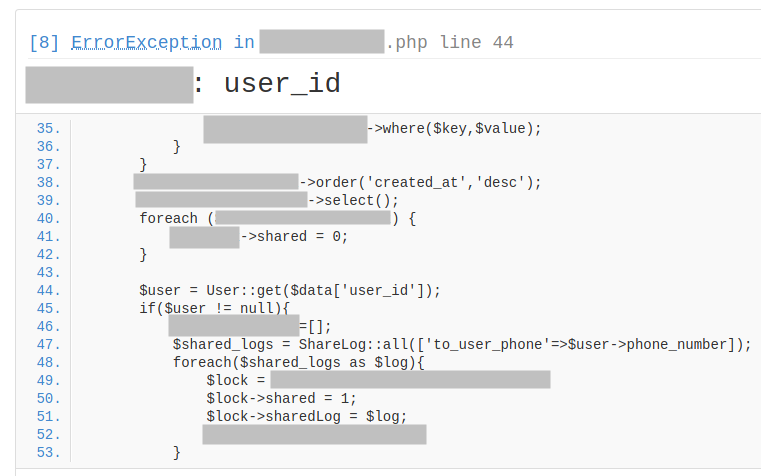
Why not check them? If we open the first link, we see a page with a raised exception:
The first URL page raises an exception.
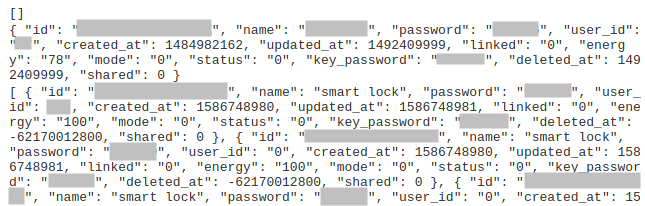
If we go further in this page, juicy information appears in a JSON format:
The first URL page contains a juicy JSON structure.
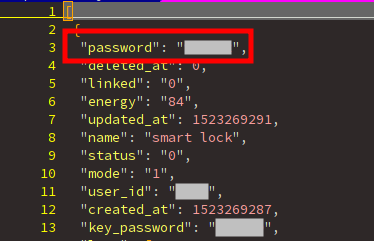
As we can see, the server leaks a lot of data, including the passwords of every device without requiring any authentication from us.
JSON structure caption.
So, information about lock of each user is recorded:
- we can get the password. Quickly, we can see that 85% of the users do not change the default password (000000).
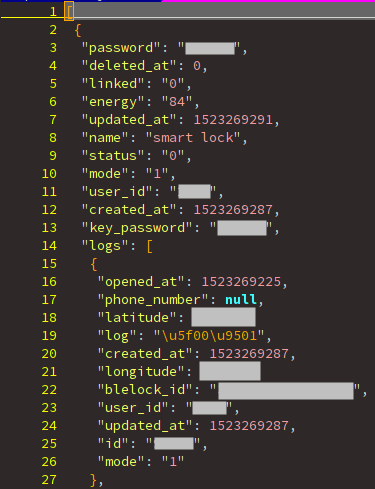
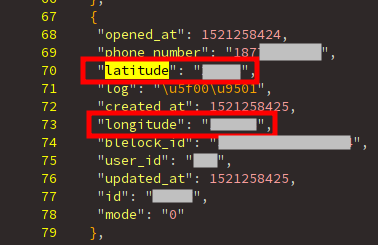
But also, we can know each time that a lock was opened and exactly where!
The latitude and longitude fields.
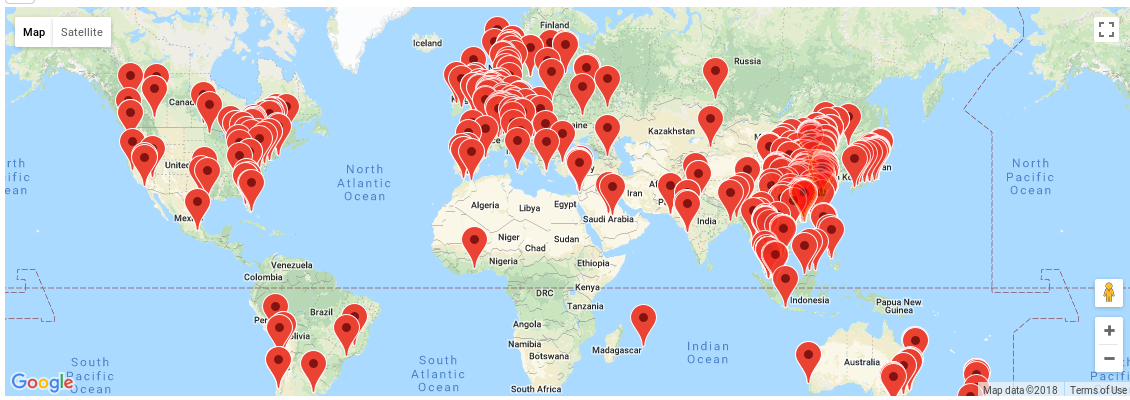
With a straightforward script, you can pinpoint them on a map:
- you know exactly the location of the locks all over the world!
- with each of their passwords and you just need a mobile to use it!
- No onerous hardware or dedicated skills are required!
A worldwide crime syndicate could coordinate a cheap and massive robbery without leaving any traces!
It highlights one of the biggest IoT challenges. A risk is characterized by its likelihood to happen and the severity of the consequences if it occurs. But, a third item must not be missed: the scalability. Devices communicate between them or with a server by design. A security flaw impacting a device is more likely to be exploitable remotely, thus affecting concurrently all the deployed devices. Also, hardware or software not designed to be upgraded might let it unfixed forever. A risk requiring to be physically near the device is much less dangerous than another one you can execute remotely.
How to mitigate all these issues?
You must consider the new risks induced by the connectivity. First, start with identifying all the assets of your product and their associated threats that could affect them, with a risk analysis like EBIOS. It lets you better understand which protections shall be implemented. For the smart lock, a message could be sent to the owner each time it is opened to warn him about suspicious activity.
Second, find the correct balance between the risks that must be prevented and the cost to implement the required level of protection:
- For the lock communication, cryptographic algorithms must be implemented to create a secure channel before exchanging sensitive commands such as the authentication or the lock opening. Use random counters in the frames to prevent replay.
- For the Android application, obfuscate the code and detect instrumentation or modification. Critical operations shall be implemented in native code, or even better from the server side. Sensitive strings, as the server URL, must not leak in a simple logcat: either you delete them in production, or you encrypt them.
- For the server, implement secure authentication and access rights. Check the available APIs and make penetration tests.