- What makes a Unix process die with Broken pipe?
- 3 Answers 3
- What does «broken pipe» mean?
- How to Prevent the SSH Broken Pipe Error
- What Is the SSH Broken Pipe Error
- How to Prevent the SSH Broken Pipe Error
- On the Client Side
- On the Server Side
- Conclusion
- About the author
- Denis Kariuki
- What does the Broken pipe message mean in an SSH session?
- 9 Answers 9
What makes a Unix process die with Broken pipe?
What’s your question? Are you asking which of those is correct, or if there are any other things that can cause the broken pipe?
3 Answers 3
A process receives a SIGPIPE when it attempts to write to a pipe (named or not) or socket of type SOCK_STREAM that has no reader left.
It’s generally wanted behaviour. A typical example is:
You don’t want find to keep on running once head has terminated (and then closed the only file descriptor open for reading on that pipe).
The yes command typically relies on that signal to terminate.
Will write «y» until some-command terminates.
Note that it’s not only when commands exit, it’s when all the reader have closed their reading fd to the pipe. In:
There will be 1 (the subshell), then 2 (subshell + sleep), then 1 (subshell) then 0 fd reading from the pipe after the subshell explicitely closes its stdin, and that’s when yes will receive a SIGPIPE.
Above, most shells use a pipe(2) while ksh93 uses a socketpair(2) , but the behaviour is the same in that regard.
When a process ignores the SIGPIPE, the writing system call (generally write , but could be pwrite , send , splice . ) returns with a EPIPE error. So processes wanting to handle the broken pipe manually would typically ignore SIGPIPE and take action upon a EPIPE error.
Writing failed because there are no processes which could read from the pipe.
Although unless you duplicate descriptors and fork, there can only be one process to start with: generally a pipe has one reader and one writer, and when one of them closes the connection, the pipe is defunct. If you are using a named pipe, you can can make multiple connections (in serial) with it, but each one represents a new pipe in this sense. So a «pipe» to a thread or process is synonymous with a file descriptor.
If all file descriptors referring to the read end of a pipe have been closed, then a write(2) will cause a SIGPIPE signal to be generated for the calling process. If the calling process is ignoring this signal, then write(2) fails with the error EPIPE.
So a «broken pipe» is to the writer what EOF is to the reader.
What does «broken pipe» mean?
I was trying to upgrade from 14.04 to 16.04 and got a funny message. I am currently stuck between versions, can’t go forward or back. All I have are terminal command functions, no GUI. These are my results (typed longhand) after running:
$ sudo apt-get -f install 87 upgraded, 29 newly installed, 7 to remove, and 1732 not upgraded. 4 not fully installed or removed need to get 0B/404 MB of archives After this operation, 257 MB of additional disk space will be used Do you want to continue? [Y/n] Y Extracting templates from packages: 100% Preconfiguring packages. (Reading database. 423378 files and directories currently installed.) Preparing to unpack. /texlive-latex-base-doc_2015.20160320-1_all.deb unpacking texlive-latex-base-doc (2015.20160320-1) over (2013.20140215-1). dpkg: error processing archive /var/cache/apt/archives/texlive-latex-base-doc_2015.20160320-1_all.deb (--unpack): trying to Trying to overwrite '/usr/share/doc/texlive-doc/latex/url/url.tx.gz, which is also in package texlive-latex-recommended-doc 2013.20140215-1 dpkg-deb: error subprocess paste was killed by signal (broken pipe) Warning: Old configuration style found in /etc/texmf/updmap.d Warning: for now these files have been included Warning: but expect inconsistencies Warning: these packages should be rebuilt with tex-common Warning: please see /usr/share/doc/tex-common/NEWS.Debian.gz Warning: found file: /etc/texmf/updmap.d/00updmap.cfg Warning: found file: /etc/texmf/updmap.d/101modern.cfg Warning: found file: /etc/texmf/updmap.d/10texlive-base.cfg Warning: found file: /etc/texmf/updmap.d/texlive-latex-base.cfg Warning: found file: /etc/texmf/updmap.d/texlive-latex-extra.cfg Warning: found file: /etc/texmf/updmap.d/texlive-pictures.cfg Errors were encountered while processing /var/cache/apt/archives/texlive-latex-base-doc_2015.20160320-1_all.deb E: Subprocess /usr/bin/dpkg returned an error code (1) How to Prevent the SSH Broken Pipe Error
When connecting to a remote server, you can do so using a secure transmission protocol such as SSH. With SSH, you need the remote IP of the machine that you wish to connect to and the username. Once you execute the SSH connect command, you will get prompted to enter the password to complete the connection.
Unfortunately, you may sometimes run into the SSH broken pipe error which disconnects you from the remote server and hinders your activities. You will quickly get frustrated when you don’t understand what this error means or how you can fix it. This post explains everything about preventing the SSH broken pipe error to avoid interruptions. Take a look!
What Is the SSH Broken Pipe Error
There are different instances when the SSH broken pipe error may occur. In most instances, you are trying to log in to a remote machine only for the error to occur after you log in and you end up getting disconnected. The error can frustrate you, especially since you must initiate the connection repeatedly.
The broken pipe error signifies that the client and the server can’t connect, and their TCP has been broken. Sometimes, the error may arise when there is a timeout error of the interval period for requests between the client and the server. The client relies on the interval period to receive responses. When none gets shared or the set intervals are reached, you will encounter the broken pipe error.
How to Prevent the SSH Broken Pipe Error
The SSH broken pipe error is undesirable; you can use the different measures to ensure that you don’t encounter it. The aim is to keep the connection between the client and the server alive by adjusting various metrics in the SSH config file for the client and the server. There are two metrics to note when preventing the SSH broken pipe: ClientAliveInterval and ClientAliveCountMax.
The ClientAliveCountMax is the number of cycles after which the connection is interrupted if the SSH client is unresponsive. The ClientAliveInterval is the time interval in seconds in which the server takes to send the null data packets to a connected client to ensure that the connection is kept alive.
Here’s how you can prevent the SSH broken pipe error:
On the Client Side
You can specify how long to keep a SSH connection alive before the disconnection occurs. That way, you increase the ServerAliveInterval. You can adjust it when making your SSH connection or creating a config file on the client side.
When connecting via SSH, you can use the following syntax to prevent the SSH broken pipe:
Alternatively, you can create an SSH config file. We used the “touch” command in this case:
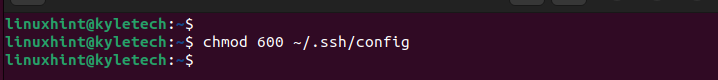
Once created, change its file permissions correctly with the following command:
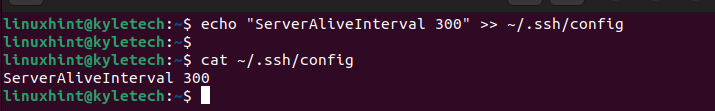
Lastly, echo the preferred ServerAliveInterval. We set it to 5 minutes in the following example:
With that, you prevented the SSH broken pipe error.
On the Server Side
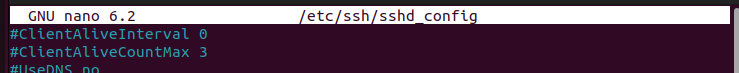
You can get the config file in the /etc/ssh/sshd_config location on the server side. The file has the ClientAliveInterval and the ClientAliveCountMax metrics which you can configure to help prevent the SSH broken pipe error.
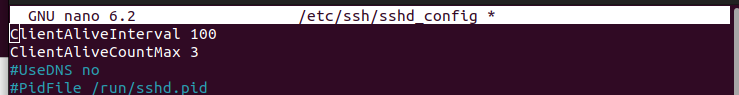
If your ClientAliveInterval is set to 100 seconds and the ClientAliveCountMax is set to 4, the server send the alive messages every 100 seconds four times. After which, it displays an SSH broken pipe error.
So, to prevent the error from occurring, you must open this config file and set your preferred parameters. By default, the metrics are commented out. Remove the hashtag (#) at the start to uncomment them. Here’s an example of configuring and uncommenting the metrics:
Save your file and exit. With that, you won’t face the error at any instance.
Conclusion
The SSH broken pipe error occurs when the client fails to get responses from the client which causes the connection to disconnect. You can prevent this by adjusting the ClientAliveInterval and the ClientAliveCountMax on the server side. Still, you can use the ServerAliveInterval metric when connecting to it via SSH or create a SSH config file on the client and add the ServerAliveInterval. This post elaborated on the two options in detail.
About the author
Denis Kariuki
Denis is a Computer Scientist with a passion for Networking and Cyber Security. I love the terminal, and using Linux is a hobby. I am passionate about sharing tips and ideas about Linux and computing.
What does the Broken pipe message mean in an SSH session?
Sometimes my SSH session disconnects with a Write failed: Broken pipe message. What does it mean? And how can I keep my session open? I know about screen , but that’s not the answer I’m looking for. I think this is a sshd config option.
9 Answers 9
It’s possible that your server closes connections that are idle for too long. You can update either your client ( ServerAliveInterval ) or your server ( ClientAliveInterval )
ServerAliveInterval Sets a timeout interval in seconds after which if no data has been received from the server, ssh(1) will send a message through the encrypted channel to request a response from the server. The default is 0, indicating that these messages will not be sent to the server. This option applies to protocol version 2 only. ClientAliveInterval Sets a timeout interval in seconds after which if no data has been received from the client, sshd(8) will send a message through the encrypted channel to request a response from the client. The default is 0, indicating that these messages will not be sent to the client. This option applies to protocol version 2 only. To update your server (and restart your sshd )
echo "ClientAliveInterval 60" | sudo tee -a /etc/ssh/sshd_config echo "ServerAliveInterval 60" >> ~/.ssh/config @AwQiruiGuo Yes, you should create the directory ( ~/.ssh ) first. So mkdir -p ~/.ssh; chmod 700 ~/.ssh; touch ~/.ssh/config
In my case that sure is irrelevant to being idle. I once got a disconnect in two terminals simultaneously, while I was typing in one of them. And in general, the time I’m not touching the connection then get a disconnect is often smaller than the time I’m also not touching the connection, while not getting any disconnects. I think, the notable thing here is that disconnects are always in all ssh connections I had simultaneously rather than in just one of them.
so basically by modify the config at the client-side could solve the problem? What if I am an admin of some server, and I really want to shut down some ssh sessions that are idle for 1 hour?
If you want to have a longer connection period, in the client add:
echo 'ServerAliveInterval 30' | tee -a ~/.ssh/config echo 'ServerAliveCountMax 1200' | tee -a ~/.ssh/config ServerAliveCountMax by default this is set to 3. Therefore once the ServerAliveInterval has sent 3 small packs of info to your server it will then automatically log out. Setting it to 1200 means this process will have to occur at least 1200 times. In short you should be connected at least 30*1200 seconds (10 hours).
I tried setting it to 0, but still kept getting the broken connection error, only way to stop it was to use some larger values like mentioned in the answer
Setting ServerAliveCountMax=1200 is a bad idea. It’s not a cumulative counter, it’s the number of failed server alive messages that can happen in a row before disconnecting. In your example your server could be down for 10 hours and your connection would still be open. See the man page man.openbsd.org/ssh_config
An alternative solution would be to use mosh — the mobile shell. In contrast to ssh it connects via UDP and supports roaming. You can start your session at home, suspend your laptop, take it to work / friends / wherever else you have internet, unsuspend your laptop and continue to work as if nothing has happened. It is especially useful if you are on a lousy internet connection: It shows instant feedback if your keystrokes don’t reach the server and continuously tries to reestablish the connection.
Installation and setup are simple: It is now included in all current Linux (plus a few non-Linux) distributions and it coordinates the session initialization and authentication via a prior ssh connection. So if you are able to connect via ssh user@server you are very likely to be able to connect with mosh just by calling mosh user@server , if the mosh packages are installed on both ends.
The main reason for connection failures is that you have to reach the server on a UDP port (default range: 60000-61000) for mosh to work. So if the server is behind a firewall you are mostly out of luck if can’t punch holes in it yourself (security implications).