- What is kali linux persistence
- Multiple Persistence Stores
- Emergency Self Destruction of Data in Kali
- What is kali linux persistence
- How To Make Kali Linux Live USB Persistence 2022
- Let’s Make Kali Linux Live USB Persistence
- Add New Partition in Kali Linux Live USB Device
- Follow the given instruction:
- Add New Partition in Kali Linux Live USB Device
- Add persistent configuration file by using following command.
What is kali linux persistence
In this workshop, we will examine the various features available to us when booting Kali Linux from USB devices. We will explore features such as persistence, creating LUKS encrypted persistence stores, and even dabble in “LUKS Nuking” our USB drive. The default Kali Linux ISOs (from 1.0.7 onwards) support USB encrypted persistence.
0x01 — Start by imaging the Kali ISO onto your USB drive (ours was /dev/sdb). Once done, you can inspect the USB partition structure using parted /dev/sdb print:
For ease of use, please use a root account. This can be done with “sudo su”.
[email protected]:~$ dd if=kali-linux-2023.2-live-amd64.iso of=/dev/sdb conv=fsync bs=4M 0x02 — Create and format an additional partition on the USB drive. In our example, we create a persistent partition in the empty space above the Kali Live partitions:
When fdisk completes, the new partition should have been created at /dev/sdb3 ; this can be verified with the command lsblk .
0x03 — Encrypt the partition with LUKS:
[email protected]:~$ cryptsetup --verbose --verify-passphrase luksFormat /dev/sdb3 0x04 — Open the encrypted partition:
[email protected]:~$ cryptsetup luksOpen /dev/sdb3 my_usb 0x05 — Create an ext4 filesystem and label it:
[email protected]:~$ mkfs.ext4 -L persistence /dev/mapper/my_usb [email protected]:~$ e2label /dev/mapper/my_usb persistence 0x06 — Mount the partition and create your persistence.conf so changes persist across reboots:
[email protected]:~$ mkdir -p /mnt/my_usb [email protected]:~$ mount /dev/mapper/my_usb /mnt/my_usb [email protected]:~$ echo "/ union" | sudo tee /mnt/my_usb/persistence.conf [email protected]:~$ umount /dev/mapper/my_usb 0x07 — Close the encrypted partition:
[email protected]:~$ cryptsetup luksClose /dev/mapper/my_usb Now your USB drive is ready to plug in and reboot into Live USB Encrypted Persistence mode.
Multiple Persistence Stores
At this point we should have the following partition structure:
We can add additional persistence stores to the USB drive, both encrypted or not… and choose which persistence store we want to load, at boot time. Let’s create one more additional non-encrypted store. We’ll label and call it “work”.
0x01 — Create an additional, 4th partition which will hold the “work” data. We’ll give it another 5GB of space:
[email protected]:~$ parted /dev/sdb GNU Parted 2.3 Using /dev/sdb Welcome to GNU Parted! Type 'help' to view a list of commands. (parted) print Model: SanDisk SanDisk Ultra (scsi) Disk /dev/sdb: 31.6GB Sector size (logical/physical): 512B/512B Partition Table: msdos Number Start End Size Type File system Flags 1 32.8kB 2988MB 2988MB primary boot, hidden 2 2988MB 3050MB 64.9MB primary fat16 3 3050MB 10.0GB 6947MB primary (parted) mkpart primary 10000 15000 (parted) quit Information: You may need to update /etc/fstab. 0x02 — Format the fourth partition, label it “work”:
[email protected]:~$ mkfs.ext4 /dev/sdb4 [email protected]:~$ e2label /dev/sdb4 work 0x03 — Mount this new partition and create a persistence.conf in it:
[email protected]:~$ mkdir -p /mnt/usb [email protected]:~$ mount /dev/sdb4 /mnt/usb [email protected]:~$ echo "/ union" > /mnt/usb/persistence.conf [email protected]:~$ umount /mnt/usb Boot the computer, and set it to boot from USB. When the boot menu appears, edit the persistence-label parameter to point to your preferred persistence store!
Emergency Self Destruction of Data in Kali
As penetration testers, we often need to travel with sensitive data stored on our laptops. Of course, we use full disk encryption wherever possible, including our Kali Linux machines, which tend to contain the most sensitive materials. Let’s configure a nuke password as a safety measure:
[email protected]:~$ sudo apt install -y cryptsetup-nuke-password [email protected]:~$ dpkg-reconfigure cryptsetup-nuke-password The configured nuke password will be stored in the initrd and will be usable with all encrypted partitions that you can unlock at boot time.
Backup you LUKS keyslots and encrypt them:
[email protected]:~$ cryptsetup luksHeaderBackup --header-backup-file luksheader.back /dev/sdb3 [email protected]:~$ openssl enc -e -aes-256-cbc -in luksheader.back -out luksheader.back.enc Now boot into your encrypted store, and give the Nuke password, rather than the real decryption password. This will render any info on the encrypted store useless. Once this is done, verify that the data is indeed inacessible.
Lets restore the data now. We’ll decrypt our backup of the LUKS keyslots, and restore them to the encrypted partition:
[email protected]:~$ openssl enc -d -aes-256-cbc -in luksheader.back.enc -out luksheader.back [email protected]:~$ cryptsetup luksHeaderRestore --header-backup-file luksheader.back /dev/sdb3 Our slots are now restored. All we have to do is simply reboot and provide our normal LUKS password and the system is back to its original state.
Updated on: 2023-May-30
Author: g0tmi1k
What is kali linux persistence
Kali Linux “Live” has two options in the default boot menu which enable persistence — the preservation of data on the “Kali Live” USB drive — across reboots of “Kali Live”. This can be an extremely useful enhancement, and enables you to retain documents, collected testing results, configurations, etc., when running Kali Linux “Live” from the USB drive, even across different systems. The persistent data is stored in its own partition on the USB drive, which can also be optionally LUKS-encrypted.
To make use of the USB persistence options at boot time, you’ll need to do some additional setup on your “Kali Linux Live” USB drive; this article will show you how.
This guide assumes that you have already created a Kali Linux “Live” USB drive as described in the doc page for that subject. For the purposes of this article, we’ll assume you’re working on a Linux-based system.
You’ll need to have root privileges to do this procedure, or the ability to escalate your privileges with sudo .
In this example, we assume:
- your USB drive is /dev/sdb (last letter will probably be different). Check the connected usb drives with the command lsblk and modify the device name in the usb variable before running the commands)
- your USB drive has a capacity of at least 8GB — the Kali Linux image takes over 3GB, and for this guide, we’ll be creating a new partition of about 4GB to store our persistent data in
In this example, we’ll create a new partition to store our persistent data into, starting right above the second Kali Live partition, put an ext4 file system onto it, and create a persistence.conf file on the new partition.
- First, begin by imaging the latest Kali Linux ISO (currently 2023.2) to your USB drive as described in this article. We’re going to assume that the two partitions created by the imaging are /dev/sdb1 and /dev/sdb2 . This can be verified with the command lsblk .
- Create and format an additional partition on the USB drive. First, let’s create the new partition in the empty space above our Kali Live partitions. We have to do this from the command line as gparted will read the imaged ISO as a large block:
[email protected]:~$ usb=/dev/sdb [email protected]:~$ [email protected]:~$ sudo fdisk $usb When fdisk completes, the new partition should have been created at /dev/sdb3 ; again, this can be verified with the command lsblk .
[email protected]:~$ usb=/dev/sdb [email protected]:~$ [email protected]:~$ sudo mkfs.ext4 -L persistence $3 - Create a mount point, mount the new partition there, and then create the configuration file to enable persistence. Finally, unmount the partition:
[email protected]:~$ usb=/dev/sdb [email protected]:~$ [email protected]:~$ sudo mkdir -p /mnt/my_usb [email protected]:~$ sudo mount $3 /mnt/my_usb [email protected]:~$ echo "/ union" | sudo tee /mnt/my_usb/persistence.conf [email protected]:~$ sudo umount $3 We can now reboot into “Live USB Persistance.” Keep in mind we will need to select this boot option every time we wish to have our work stored.
How To Make Kali Linux Live USB Persistence 2022
As you know Kali Linux is one of the popular operating systems for hacking and penetration testing.
It has a feature to install kali Linux on a flash drive, this feature is amazing you have kali os in your pocket.
Run Kali Linux on any system with the help of this pen drive.
But the problem is “when you restart the OS, your saved data, and any changes/configuration in Kali Linux will be removed.
Kali Linux live USB persistence is a solution
Now your Kali Linux will run from USB on any system without losing saved data, configurations, installed programs, and any changes.
Let’s Make Kali Linux Live USB Persistence
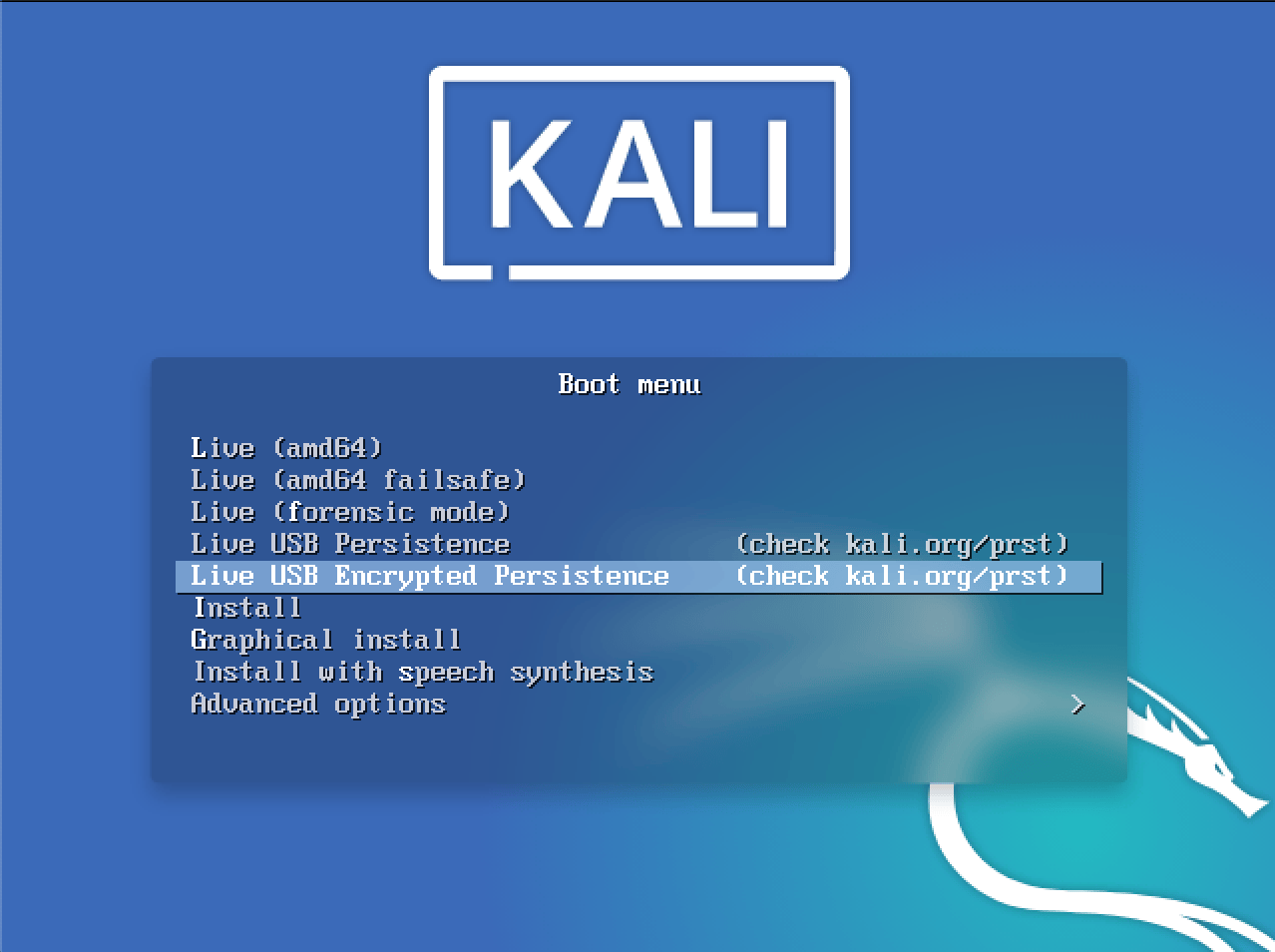
First, you just make Kali Linux bootable USB live andy boot your system with it.
When your computer will boot from Pendrive you will reach to boot menu. Where you must select “Live USB Persistence” as shown in the following image.
Add New Partition in Kali Linux Live USB Device
You can use any tool for creating partition including, parted, fdisk etc. Here I am using fdisk command to create partition.
STEP 1: First step to have eyes on attached disk and partitions in your system. Worng selection will give you high shock.
In the above image you can see one hard disk and 1 Flash drive is connected in my system.
I have create Bootable Pen drive so It is my targeted device to make Kali Linux Live useb persistece.
- Press ‘n’ and hit enter
- press ‘p’ for primary partition
- Remain default and hit enter
- First Sector default and hit enter
- Last sector default and hit enter
- Press “w” and hit enter for writing changes into hard disk
Created a new partition 3 of type ‘Linux’ and of size 11.7 GiB. Check again using fdisk -l command to check new created partition.
Format the partition using following commands
Command : mkfs.ext3 -L persistence /dev/sdb3
┌──( root 💀 kali ) – [ ~ ]
└─ # mkfs.ext3 -L persistence /dev/sdb3
mke2fs 1.46.2 (28-Feb-2021)
Creating filesystem with 3062464 4k blocks and 767040 inodes
Filesystem UUID: 1e7863b4-78b2-4203-b433-01a87e80cdc5
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632, 2654208
Allocating group tables: done
Writing inode tables: done
Creating journal (16384 blocks): done
Writing superblocks and filesystem accounting information: done
┌──( root 💀 kali ) – [ ~ ]
└─ #
At the time of creating a persistent USB drive, size does matter! The larger size of the USB drive, the better, also depending on the Linux version. In this process, Linux System will be used so make sure the tool GParted is installed. If the GParted tool does not exist in your system then install it by using the given method:
After completing the installation of GParted.
Follow the given instruction:
- Download Kali Linux ISO file & plug the thumb drive
- Open terminal and find the USB device location by using following commands
mount | grep –I udisks |awk ‘’ - Its needed to transfer Kali Linux ISO image into the USB device by using following commands
dd if = Kali_Image.iso of =/dev/sdb bs =512k - Open Gparted
gparted /dev/sdb
The device should have one partition with the image of Kali Linux that was just installed.
Add New Partition in Kali Linux Live USB Device
Add new partition in Pen Drive, launch the Gparted by given method then follow the given instruction:
- Select unallocated space and right click then click on ‘New’.
- Create as New & Select ext4 from drop down menu in File system .
- Add.
- Apply All Operations.
Add persistent configuration file by using following command.
- #mkdir /mnt/usb
- #mount /dev/sdb2 /mnt/usb
- #echo “/ union” >> /mnt/usb/persistence.conf
- #umount /mnt/usb
Now Creation of LiveUSB installation be completed, Reboot the computer and boot from SUB Drive .