- Linux LDAP authentication (Using Linux LDAP)
- Step 1: Install OpenLDAP Server
- Step 2: Set Access Controls
- Step 3: Add Base Data to the LDAP Tree
- Step 3: Add Users
- Step 4: Set Up the Client LDAP Server
- Step 5: Configure NSS
- Step 6: Configure PAM
- Step 7: Create Home Folders at the Login
- Step 8: Enable sudo
- Conclusion
- About the author
- Kennedy Brian
- What Is Linux LDAP Authentication?
- What Is Linux LDAP?
- Linux LDAP Entries
- How Linux LDAP Works
- Conclusion
- About the author
- Kennedy Brian
Linux LDAP authentication (Using Linux LDAP)
This article will focus on using a Linux server to authenticate against the Linux directory. LDAP directories in Linux environments can either be local or network directories. Notably, network directories come in handy where and when there is a need for central authentication, while local directories operate within the same computer and not over a network.
While we will focus on LDAP protocol, discussing a Linux LDAP authentication is impossible without including NSS and PAM in the tutorial. Thus, we will also discuss how to configure NSS and PAM modules to work with client computers through the authentication process. This guide focuses on online authentication.
Step 1: Install OpenLDAP Server
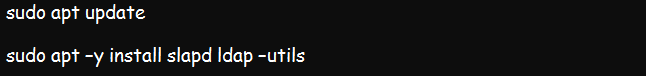
You will not authenticate with LDAP if you do not have it installed in your systems. So, the first step is ensuring that you have OpenLDAP installed in your system. We already discussed the installation process elaborately in our previous write-up.
This command should help you install OpenLDAP on Ubuntu 22:04:
Step 2: Set Access Controls
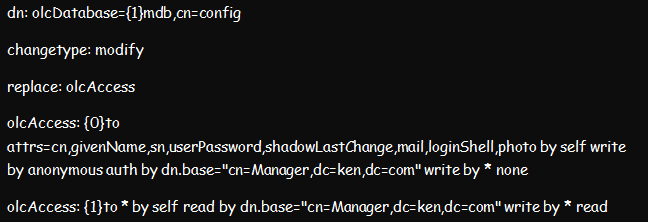
Once the installation process is complete, proceed to set up the access controls. Setting up the access controls ensures that no one can access and read any encrypted passwords from the LDAP server. Yet, users can still edit some of their attributes, such as personal passwords and photos.
You can achieve this setup by creating and importing the below ldif file. And once done, you can restart the slapd.service.
Step 3: Add Base Data to the LDAP Tree
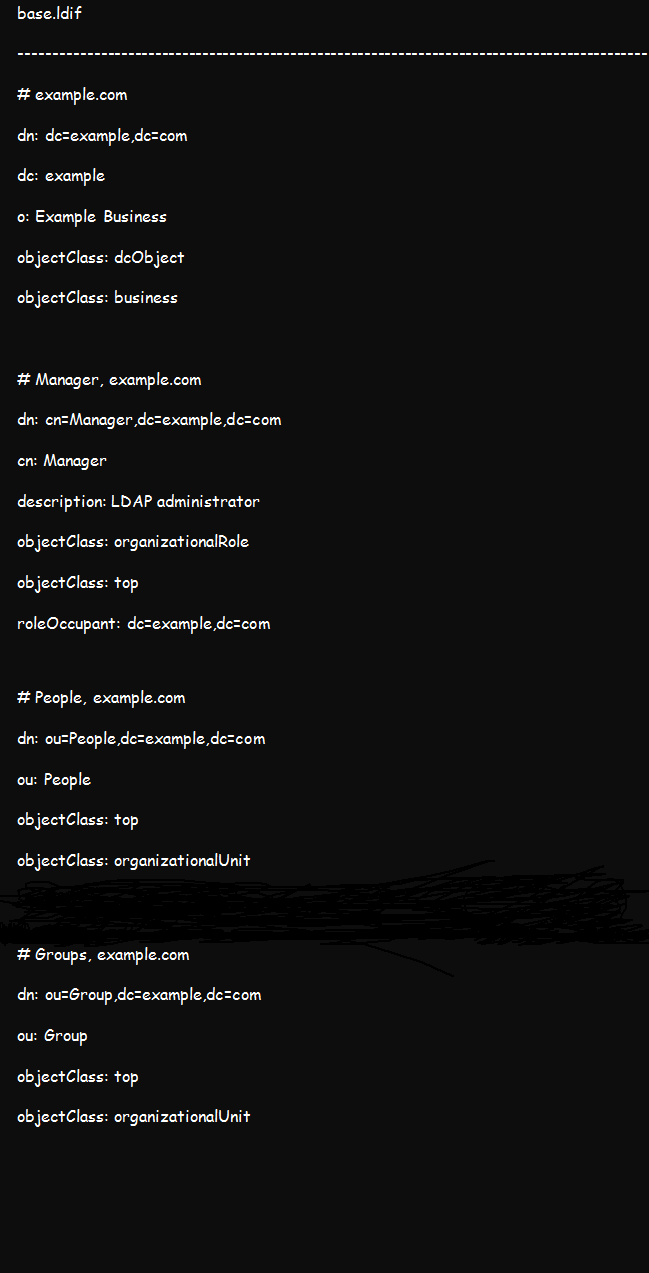
Create a temporary base.ldif file containing the following details:
You can customize the details by replacing example and org with your actual domain credentials. Once done, add the above details to your OpenLDAP tee using this command:
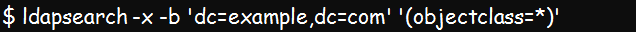
Test using the below command to confirm if the data importation was successful:
Step 3: Add Users
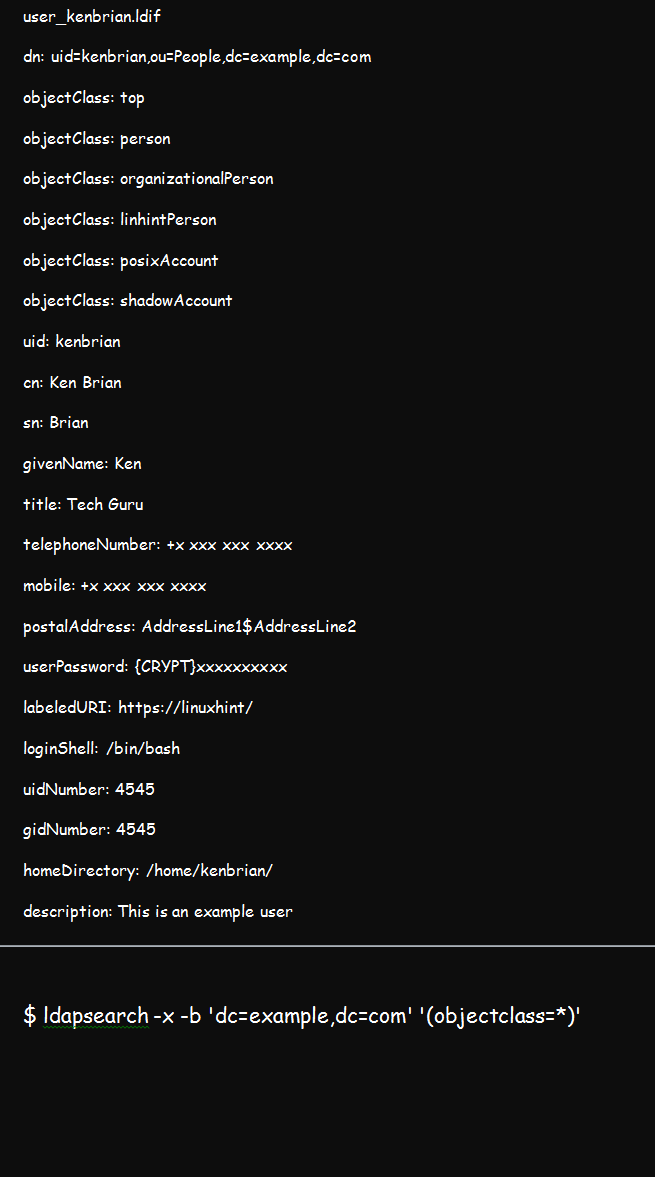
To add a user, you should create a .ldif file such as the one below. Our user for this demonstration is kenbrian and our domain credential is linhint.com.
The ********* present in the userPassword entry represents your password, which is the value of slappasswd or /etc/shadow. You can now add the user once you have the .ldif file using the below command:
You can also use the ldapadd command to add more than one user to the directory by creating their various credentials all at once and adding them using the above utility. A list of credentials can look like this:
Step 4: Set Up the Client LDAP Server
You can set up an OpenLDAP server and ensure you can successfully query the server using the ldapsearch command. Once set up, you can decide whether to proceed with online and offline or online-only authentication.
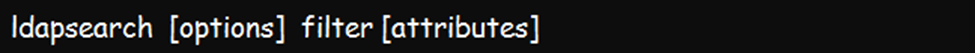
Below is the basic ldapsearch command line or syntax:
Step 5: Configure NSS
NSS, also known as Name Service Switch, is a system often used for managing configuration databases of different sources. So, you will find it vital in a range of LDAP applications. The following steps will be vital for configuring NSS:
- Install NSS using the nss-pam-ldapd package.
- Edit the NSS central configuration file, which is the /etc/nsswitch.conf. This file informs NSS of the files to use for respective system databases. Editing the file will require you to add ldap directives to the group, passwd, and shadow databases. Ensure that your edited file looks like this:
- You will also need to edit the /etc/nsswitch.conf. file to change the uri and base lines so that they fit your ldap server settings.
- If your LDAP server prompts for a password, edit both the bindpw and binddn sections. Continue to replace your /etc/nsswitch.conf permission from nslcd to 0600for a proper start.
- Use the systemd command to start the nslcd.service. With that, your LDAP users should be visible when you run getent passwd command on your client-server.
Step 6: Configure PAM
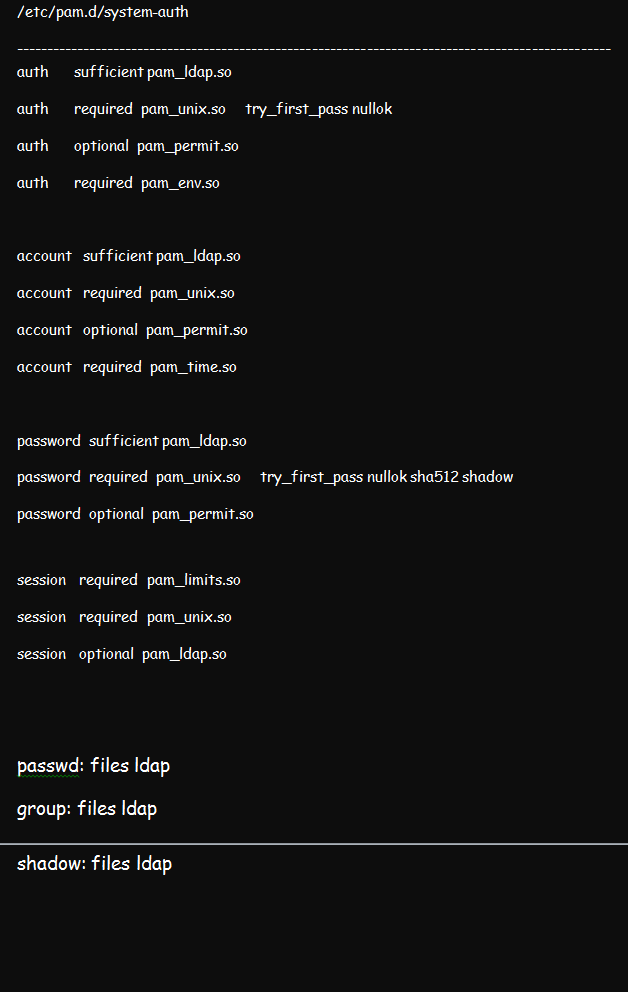
We discussed how to configure PAM in a Linux environment in a previous article. But for this illustration, ensure that you configure the Pluggable Authentication Module using the pam_ldap.so. While at that, edit the /etc/pam.d/system-auth file from pam.d. the result should be like in the figure below:
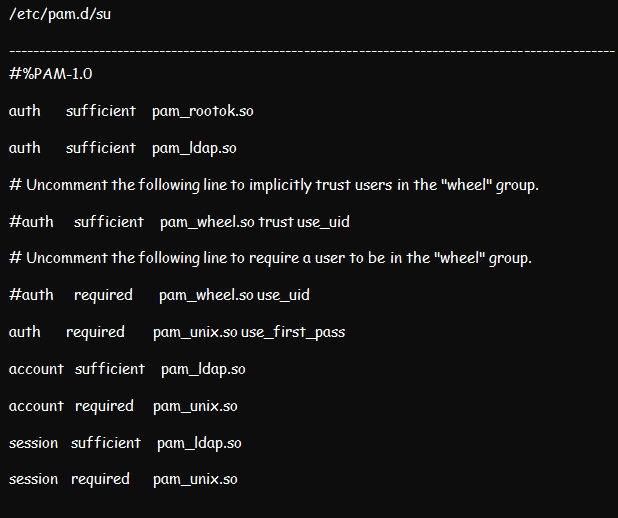
Proceed to edit the /etc/pam.d/su as well as the /etc/pam.d/su-l files. The /etc/pam.d/su-l file comes in handy whenever the /etc/pam.d/su login is run by the user. Place pam_ldap.so sufficient above each section except the pam_rootok.
Now, permit users to edit their passwords by making edits to the /etc/pam.d/passwd file.
Step 7: Create Home Folders at the Login
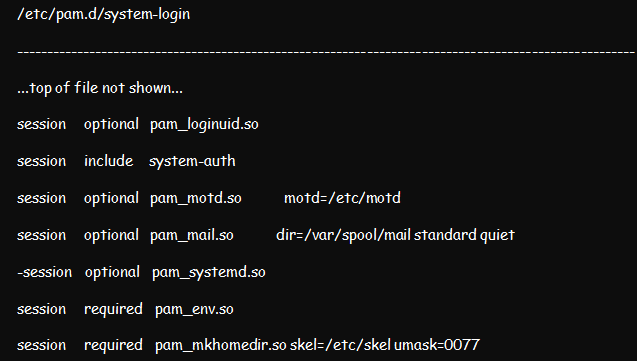
You can choose to create home folders at the login in case your system does not use NFS to store folders. Create a home folder at login by editing /etc/pam.d/system-login and then adding pam_mkhomedir.so to session sections above all sufficient items.
Step 8: Enable sudo
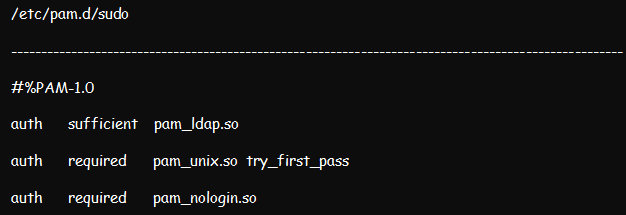
Enable sudo from the LDAP user by editing /etc/pam.d/sudo and modifying it appropriately.
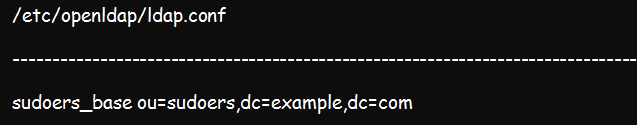
Add the command below to the /etc/openldap/ldap.conf file:
Conclusion
The above steps should help you implement an online authentication of Linux LDAP alongside PAM and NSS. This system comes in handy in securing your systems. More importantly, you can use it to query and manage your company information.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.
What Is Linux LDAP Authentication?
Lightweight Directory Access Protocol (LDAP) is a system that enables applications and programs to query user credentials or information rapidly. It is a client-server protocol often used for accessing directory services. Notably, this lightweight protocol is handy for accessing X.500-based directory services.
For example, someone within your systems wants to send mail to a new colleague and print the correspondences from a new printer. LDAP will only query the user identity and make the two services possible. The essence is that employees can use LDAP to verify passwords, connect to printers, or switch to Google for email services.
This article introduces you to Linux LDAP. So, it will define Linux LDAP and discuss the concept of Linux LDAP entries. The article will also provide a tutorial on how Linux LDAP works.
What Is Linux LDAP?
LDAP comes in handy as an open, vendor-neutral protocol for storing, maintaining, and accessing directory data. It allows systems and users to access centrally-stored data or information over a network. LDAP also comes in handy in authenticating users and allowing users to access their system accounts from any machine within the network.
Organizations can, therefore, use LDAP to store and manage usernames, passwords, printer connections, email addresses, phone numbers, network services, authentication data, and an array of other static data in directories.
Lightweight Directory Access Protocol, as the name suggests, is a protocol. It is not an authentication protocol per se. Instead, you can use it to store and quickly search authentication operations.
So, rather than specifying how directory services and programs work, it functions as a form of language. Thus, allowing users to find the data and information they need instantly.
Linux LDAP Entries
Generally, directories are databases optimized to read, browse, and search. They contain various types of information and provide support for an array of sophisticated filtering capabilities.
LDAP is lightweight and does not support complicated rollback schemes or transactions synonymous with database management systems that handle high-volume and complex tasks. Directory updates are generally simple with no or very minimal changes.
The information model for Linux LDAP focuses on entries, a collection of attributes with a unique Distinguished Name (DN). Usually, a DN is often used to refer to entries unambiguously since each attribute of an entry has a type and at least one value.
Since it is a vendor-neutral protocol, LDAP is useable with various directory programs. A typical directory will often contain data/information of the following categories:
- Descriptive Data – These are multiple points that collectively define an asset. They include names and locations.
- Static Data – This is an information category that rarely changes. Even when they do, the deviations are pretty subtle.
- Valuable Data – This category of data is integral to the functioning of a business or company. Often, this data should be accessible as it is useable repeatedly.
Ideally, the Lightweight Directory Access Protocol is not new. And despite having been published in 2003, LDAP remains widespread and useable across various platforms.
How Linux LDAP Works
Linux LDAP stands out as a querying mechanism. With Linux LDAP in your organization, an average employee will connect with the protocol dozens of times daily. And while the steps are pretty complex and can be taxing, an average employee will not know what it takes to make the connection.
An LDAP query involves the following processes:
- Session Connection – This is the first step. It involves a user connecting to the server or system through an LDAP port.
- Request – The user sends or submits a query to the server. A query could be a login request or an email lookup.
- Response – The LDAP protocol does a search relating to the query in the directory, fetches the correct information, and gives feedback to the user.
- Completion – The user ends the session by disconnecting from the LDAP port.
While the previous search process looks simple, a lot of coding is at stake to make it successful. Developers and system administrators have to determine the processing duration for the server, the size search limit, the variables worth including, and many other considerations. Thus, configuring your LDAP will determine how your search process responds.
Of course, Linux LDAP must authenticate the user before any search process to ensure that only authorized entities initiate searches. The two primary systems that LDAP uses to authenticate users include:
- Simple Authentication Process – This involves a correct username and password.
- Simple Authentication and Security Layer (SASL) – This is a secondary authenticating service like the Kerberos protocol. It performs a connection before a user gains a connection to the server.
Users can perform searches from the technological devices within the company. Yet, it is also possible to send queries from smartphones, laptops, or home computing devices. Ideally, LDAP communication happens without encryption or scrambling, which can cause a security threat. Many organizations use Transport Layer Security or TLS to prevent leakage or interception of LDAP messages.
Other operations you can accomplish with LDAP besides searching include adding, deleting, comparing, and modifying entries.
Conclusion
That brings us to the end of our introductory topic on LDAP. While this is an incredibly broad but essential area for system administrators, we compressed it to ensure that we address all the concerns. Still, the performance of your LDAP will depend on how you configure LDAP into your systems and how you use it.
About the author
Kennedy Brian
Brian is a computer scientist with a bias for software development, programming, and technical content development. He has been in the profession since 2015. He reads novels, jogs, or plays table tennis whenever not on gadgets. He is an expert in Python, SQL, Java, and data and network security.