- named Linux Service
- How to use the Linux BIND command to install and configure DNS
- How DNS works
- Great Linux resources
- Where does DNS get IP addresses?
- Forward and reverse lookups
- Install and configure DNS
- Configure the /etc/named.conf file
- Define the forward and reverse zones
- Create forward and reverse zone files
- Add the nameserver IP to /etc/resolv.conf
- Start/restart and enable the named service
- Verify the DNS name resolution
- Query with nslookup
- Query with dig
- Wrap up
- Linux Network Administrator’s Guide, Second Edition by
- Chapter 6. Name Service and Resolver Configuration
named Linux Service
Now lets see the manual of named service.
Manual named:
NAME
named — Internet domain name server
SYNOPSIS
named [ -c config-file ] [ -d debug-level ] [ -f ] [ -g ] [ -n #cpus ] [ -p port ] [ -s ] [ -t directory ] [ -u user ] [ -v ] [ -x cache-file ]
DESCRIPTION
named is a Domain Name System (DNS) server, part of the BIND 9 distribution from ISC. For more information on the DNS, see RFCs 1033, 1034, and 1035.
When invoked without arguments, named will read the default configuration file /etc/named.conf, read any initial data, and listen for queries.
OPTIONS
-c config-file
Use config-file as the configuration file instead of the default, /etc/named.conf. To ensure that reloading the configuration file continues to work after the server has changed its working directory due to to a pos- sible directory option in the configuration file, config-file should be an absolute pathname.
-d debug-level
Set the daemon’s debug level to debug-level. Debugging traces from named become more verbose as the debug level increases.
-f Run the server in the foreground (i.e. do not daemonize).
-g Run the server in the foreground and force all logging to stderr.
-n #cpus
Create #cpus worker threads to take advantage of multiple CPUs. If not specified, named will try to deter- mine the number of CPUs present and create one thread per CPU. If it is unable to determine the number of CPUs, a single worker thread will be created.
-p port
Listen for queries on port port. If not specified, the default is port 53.
-s Write memory usage statistics to stdout on exit.
Note: This option is mainly of interest to BIND 9 developers and may be removed or changed in a future release.
-t directory
chroot() to directory after processing the command line arguments, but before reading the configuration file.
Warning: This option should be used in conjunction with the -u option, as chrooting a process running as root doesn’t enhance security on most systems; the way chroot() is defined allows a process with root privi- leges to escape a chroot jail.
-u user
setuid() to user after completing privileged operations, such as creating sockets that listen on privileged ports.
Note: On Linux, named uses the kernel’s capability mechanism to drop all root privileges except the ability to bind() to a privileged port and set process resource limits. Unfortunately, this means that the -u option only works when named is run on kernel 2.2.18 or later, or kernel 2.3.99-pre3 or later, since previ- ous kernels did not allow privileges to be retained after setuid().
-v Report the version number and exit.
-x cache-file
Load data from cache-file into the cache of the default view.
Warning: This option must not be used. It is only of interest to BIND 9 developers and may be removed or changed in a future release.
SIGNALS
In routine operation, signals should not be used to control the nameserver; rndc should be used instead.
SIGHUP Force a reload of the server.
SIGINT, SIGTERM
Shut down the server.
The result of sending any other signals to the server is undefined.
CONFIGURATION
The named configuration file is too complex to describe in detail here. A complete description is provided in the BIND 9 Administrator Reference Manual.
FILES
/etc/named.conf
The default configuration file.
/var/run/named.pid
The default process-id file.
SEE ALSO
RFC 1033, RFC 1034, RFC 1035, rndc(8), lwresd(8), BIND 9 Administrator Reference Manual.
AUTHOR
Internet Systems Consortium
How to use the Linux BIND command to install and configure DNS
The Domain Name System helps you get where you want to be on the internet. Make sure you know what it is and how to set up, configure, and test it.
The Domain Name System (DNS) is used to resolve (translate) hostnames to internet protocol (IP) addresses and vice versa. A DNS server, also known as a nameserver, maps IP addresses to hostnames or domain names.
In this article, you will learn the basics of DNS, from how DNS gets the IP address and hostname, to the concepts of forward and reverse lookup zones. It will also show you how to install and configure DNS, define and edit zone files, and verify whether the DNS can resolve to the correct address with the help of commands. If you are new to DNS, this article will help you play with it on your system using basic configurations.
How DNS works
When a client requests information from a nameserver, it usually connects to port 53, and then the nameserver resolves the name requested.
Great Linux resources
Where does DNS get IP addresses?
You might wonder how DNS gets the IP of the corresponding hostname or domain name. How does DNS search among different IP addresses and associate your domain name correctly? Who stores those mappings between domain names and IP addresses?
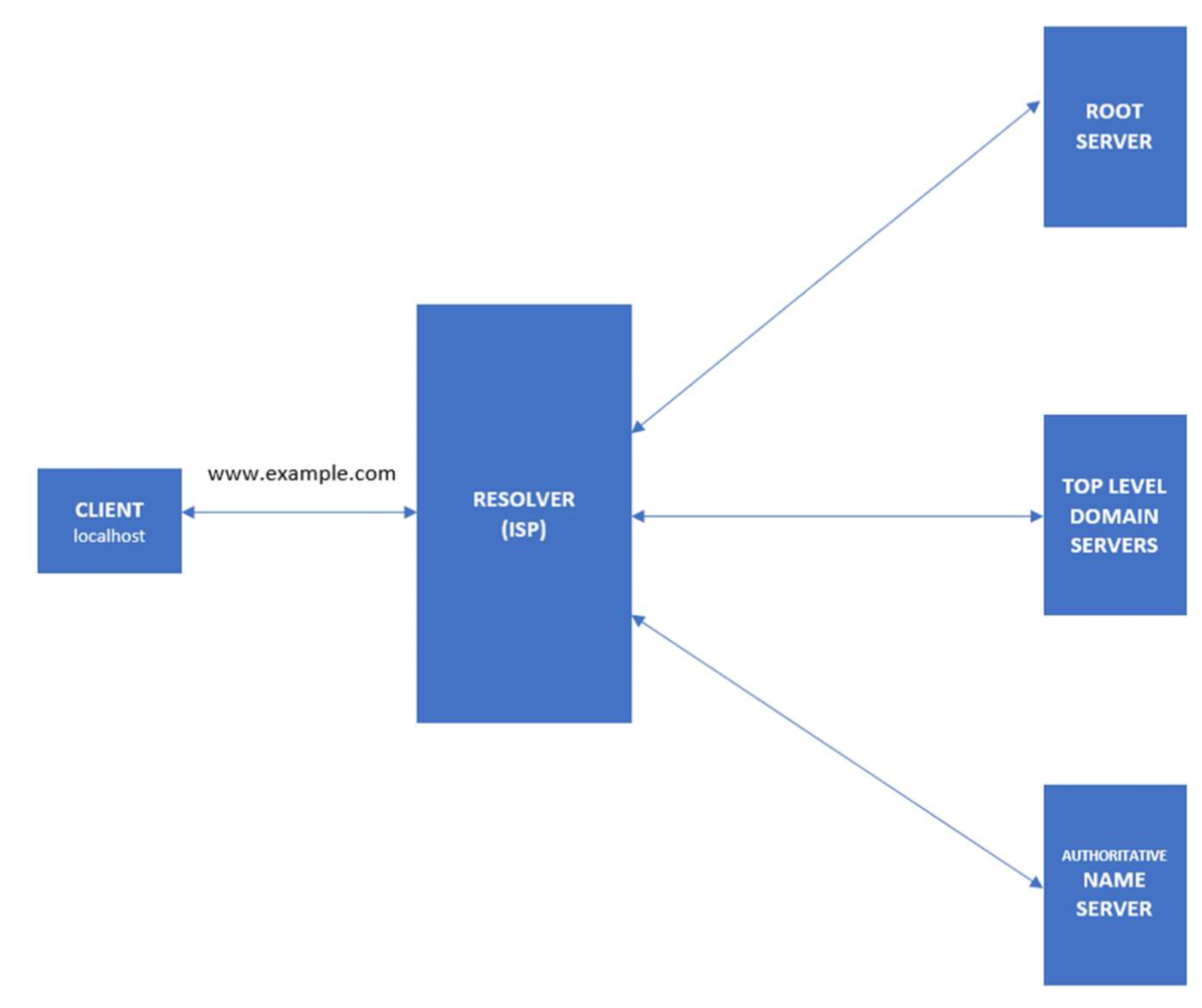
The DNS workflow illustrates how communication happens within DNS and how it resolves the addresses.
- When the client searches for the domain www.example.com , the request will initially go to the internet service provider’s (ISP) resolver. It will respond to the user’s request to resolve a domain name.
- If the IP address is not found on the resolver, the request is forwarded to a root DNS server and later to the top-level domain (TLD) servers.
- TLD servers store information for top-level domains, such as .com or .net.
- Requests are forwarded to the nameservers, which know detailed information about domains and IP addresses.
- Nameservers respond to the ISP’s resolver, and then the resolver responds to the client with the requested IP.
- When the resolver doesn’t know the IP, it stores the IP and its domain in a cache to service future queries.
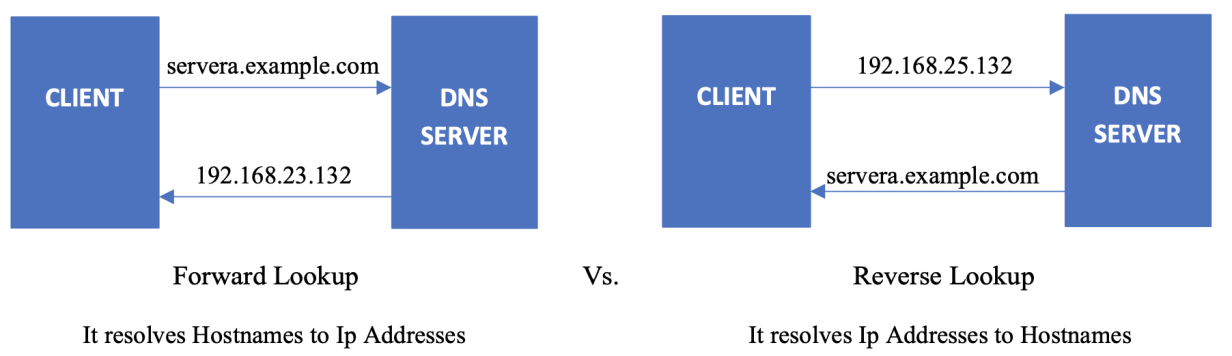
Forward and reverse lookups
The forward lookup zone uses the domain name to search for IP addresses, whereas the reverse lookup zone uses IP addresses to search for the domain name.
Install and configure DNS
BIND is a nameserver service responsible for performing domain-name-to-IP conversion on Linux-based DNS servers.
[root@servera ~] # yum install bindThe BIND package provides the named service. It reads the configuration from the /etc/named and /etc/named.conf files. Once this package is installed, you can start configuring DNS.
Configure the /etc/named.conf file
First, add or edit the two values in the options field. One is the DNS server address, and the other is the allow-query to any.
[root@servera ~] # vim /etc/named.conf listen-on port 53 < 127.0.0.1; 192.168.25.132; >; allow-query < localhost; any; >;Here are the values from the above file:
- 192.168.25.132 – DNS server address
- any – matches every IP address
Define the forward and reverse zones
Define the forward and reverse zones in the /etc/named.conf or /etc/named.rfc1912.zones (you can define zones in either of those files). In this example, I am appending zone definition details to the /etc/named.rfc1912.zones file.
[root@servera ~] # vim /etc/named.rfc1912.zones zone "example.com" IN < type master; file "example.forward.zone"; allow-update < none; >; >; zone "25.168.192.in-addr.arpa" IN < type master; file "example.reverse.zone"; allow-update < none; >; >; Create forward and reverse zone files
You also need to create forward and reverse zone files in the /var/named directory.
Note: By default, the named.conf file includes the /var/named directory for checking zone files. Sample zone files named.localhost and named.loopback are created during the installation of the BIND package.
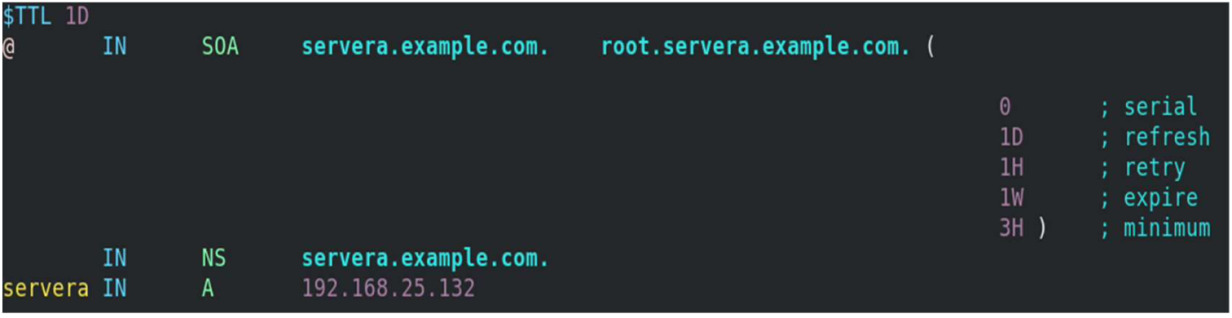
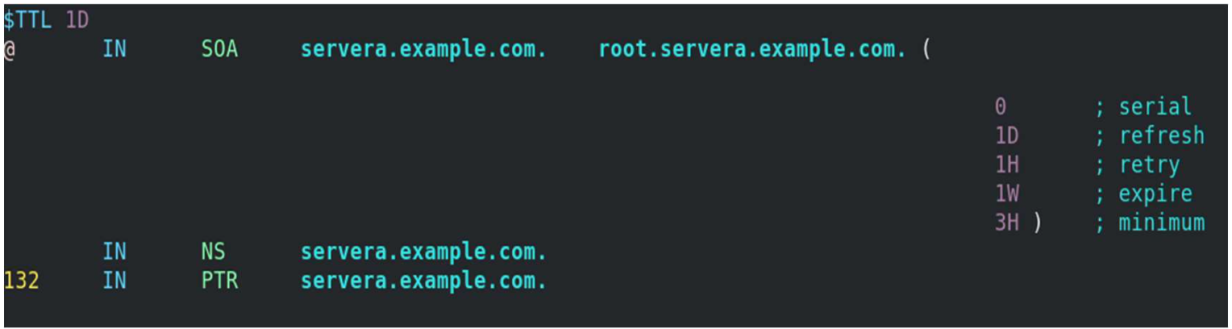
[root@servera ~] # vim /var/named/example.forward.zone[root@servera ~] # vim /var/named/example.reverse.zoneAdd the nameserver IP to /etc/resolv.conf
First, you must disable DNS processing by NetworkManager because it dynamically updates the /etc/resolv.conf file with DNS settings from its active connection profiles. To disable this and allow manual editing of /etc/resolv.conf , you must create a file (For example, 90-dns-none.conf ), as root in the /etc/NetworkManager/conf.d/ directory that contains the following:
Save the file and reload (restart) NetworkManager.
# systemctl reload NetworkManagerAfter you reload NetworkManager, it won’t update /etc/resolv.conf . Now, you can manually add the nameserver’s IP address to the /etc/resolv.conf file.
[root@servera ~] # vim /etc/resolv.conf # Generated by NetworkManager search localdomain example.com nameserver 192.168.25.132[ Be prepared in case something goes wrong. Read An introduction to DNS troubleshooting. ]
Start/restart and enable the named service
If the named service is not running or is disabled, then start and enable it. If it is already active (running) and you made all these configurations, you need to restart the service to make changes.
[root@servera ~] # systemctl status named.service [root@servera ~] # systemctl start named.service [root@servera ~] # systemctl enable named.service [root@servera ~] # systemctl restart named.service Verify the DNS name resolution
You have installed the BIND package, configured named files, created lookup zones, and restarted the service to make configurations take effect. Now use the nslookup and dig commands to check whether DNS is working properly and verify whether you are getting the intended results.
- nslookup is a program to query internet domain name servers.
- dig is a tool for interrogating DNS servers. It performs DNS lookups and displays the answers that are returned from the nameserver.
Query with nslookup
[root@servera ~] # nslookup servera.example.com Server: 192.168.25.132 Address: 192.168.25.132#53 Name: servera.example.com Address: 192.168.25.132 [root@servera ~] # nslookup 192.168.25.132 132.25.168.192.in-addr.arpa name = servera.example.com.Query with dig
Here is a forward lookup, where DNS responds with 192.168.11.132 as an IP for servera.example.com:
[root@servera ~] # dig servera.example.com . output truncated. ;; ANSWER SECTION: servera.example.com. 86400 IN A 192.168.25.132 ;; AUTHORITY SECTION: example.com. 86400 IN NS servera.example.com. . output truncated. This example displays a reverse lookup, where the DNS server responds with servera.example.com as the domain name for 192.168.25.132:
[root@servera ~] # dig -x 192.168.25.132 . output truncated. ;; ANSWER SECTION: 132.25.168.192.in-addr.arpa. 86400 IN PTR servera.example.com. ;; AUTHORITY SECTION: 25.168.192.in-addr.arpa. 86400 IN NS servera.example.com. ;; ADDITIONAL SECTION: servera.example.com. 86400 IN A 192.168.25.132 . output truncated. [ Network getting out of control? Check out Network automation for everyone, a free book from Red Hat. ]
Wrap up
In this article, you learned what DNS is and how it works. Also, you now know what forward and reverse lookup zones are and how they work. You also learned how to install the BIND package, which is responsible for setting up DNS on the system and configuring the named files and lookup zones. Finally, you learned two commands, nslookup and dig , to interrogate DNS resolutions.
Linux Network Administrator’s Guide, Second Edition by
Get full access to Linux Network Administrator’s Guide, Second Edition and 60K+ other titles, with a free 10-day trial of O’Reilly.
There are also live events, courses curated by job role, and more.
Chapter 6. Name Service and Resolver Configuration
As we discussed in Chapter 2, TCP/IP networking may rely on different schemes to convert names into addresses. The simplest way is a host table stored in /etc/hosts . This is useful only for small LANs that are run by one single administrator and otherwise have no IP traffic with the outside world. The format of the hosts file has already been described in Chapter 5.
Alternatively, you can use the Berkeley Internet Name Domain service (BIND) for resolving hostnames to IP addresses. Configuring BIND can be a real chore, but once you’ve done it, you can easily make changes in the network topology. On Linux, as on many other Unixish systems, name service is provided through a program called named . At startup, it loads a set of master files into its internal cache and waits for queries from remote or local user processes. There are different ways to set up BIND, and not all require you to run a name server on every host.
This chapter can do little more than give a rough sketch of how DNS works and how to operate a name server. It should be sufficient if you have a small LAN and an Internet uplink. For the most current information, you may want to check the documentation contained in the BIND source package, which supplies manual pages, release notes, and the BIND Operator’s Guide (BOG). Don’t let this name scare you off; it’s actually a very useful document. For a more comprehensive coverage of DNS and associated issues, you may .
Get Linux Network Administrator’s Guide, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.