Port Scanning with Nmap
Port scanning is the act of scanning a network or hosts in order to determine which network ports are open and thus which service they provide.
While the web (also known as the World Wide Web) is the most used service on the Internet, there are many more services available out there. Some of those services, such as DNS and SMTP, are at the core of the Internet and are crucial for it to run properly. Protecting those services are very important and companies invest a lot of money in that.
In this tutorial, you will learn how to do scanning using nmap utility, as well as how scanning actually works.
To understand port scanning, we also need to understand the basic of how applications communicate on the Internet.
Client-Server Model
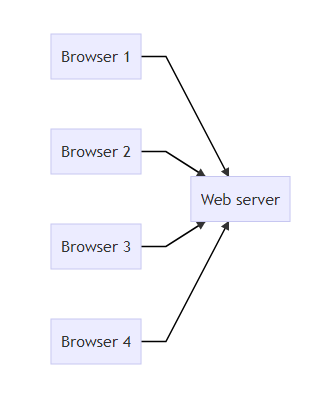
To be able to use the services on the internet, client applications connect to the servers and start exchanging information. This is called the client-server model. Whenever you access a website on the web, your browser acts like a client which connects to a server, the web server. This model also allows multiple clients to connect to a single server.
Connections are done through ports using either TCP or UDP protocol. Depending of the service provided by servers, the ports will be in either TCP or UDP. Both protocols works at layer 4, the transport layer, just over the IP protocol.
TCP
TCP – Transmission Control Protocol is one of the main protocols on the Internet and provide a reliable connection-oriented communication. It is used in emails, web, remote connections such as SSH and FTP, etc.
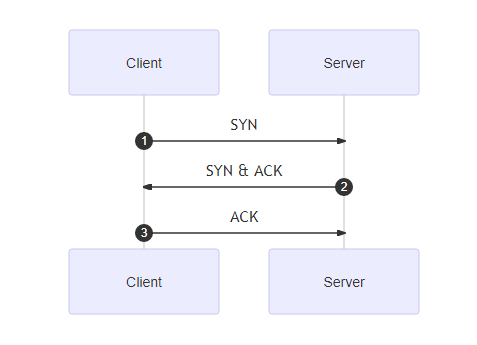
As TCP is connection-oriented, a connection must be initiated for the communication to be done. The famous TCP 3-way handshake is used for that.
Below is a packet capture using tcpdump of a 3-way handshake on port 80:
19:13:34.771079 IP 172.17.0.3.56238 > server.http: Flags [S], seq 1796216297, win 64240, options [mss 1460,sackOK,TS val 1066273657 ecr 0,nop,wscale 7], length 0 19:13:34.771135 IP server.http > 172.17.0.3.56238: Flags [S.], seq 3021625986, ack 1796216298, win 65160, options [mss 1460,sackOK,TS val 3475146296 ecr 1066273657,nop,wscale 7], length 0 19:13:34.771168 IP 172.17.0.3.56238 > server.http: Flags [.], ack 1, win 502, options [nop,nop,TS val 1066273658 ecr 3475146296], length 0Once the handshake has been done, data can be exchanged after that.
Below table are some of the famous TCP ports:
| Service | Port number |
|---|---|
| SSH (Remote connection) | 22 |
| STMP (Email) | 25 |
| HTTP (WEB) | 80 |
| HTTPS (Encrypted WEB) | 443 |
UDP
UDP on the other side is a connection-less communication. Being connection-less, it is also unreliable but gains in speed as it avoids a lot of processing. Audio and Video streaming are often done in UDP.
Some famous UDP ports are:
| Service | Port number |
|---|---|
| DNS | 53 |
| TFTP | 69 |
| SNMP | 161 |
Hands-on with Nmap
Let’s start our hands-on session with a lab using Nmap. Nmap is the most popular port scanner out there and is also open-source. It works on both Linux and Windows and has a lot of advanced features which can be overwhelming. Feel free to check its manual if needed with the command man nmap .
Host Discovery
If you already know the IP of the host you want to scan, you can skip this part and go to the scanning techniques section directly.
Discovering your hosts, especially in a local network can be done with a series of techniques. One of the simplest is way is with a ping scan on the whole network with port scanning disabled with nmap -sn 172.17.0.0/24 :
root@client1:/# nmap -sn 172.17.0.0/24 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-09 19:44 +04 Nmap scan report for 172.17.0.1 Host is up (0.000055s latency). MAC Address: 02:42:00:66:86:22 (Unknown) Nmap scan report for 172.17.0.2 Host is up (0.000019s latency). MAC Address: 02:42:AC:11:00:02 (Unknown) Nmap scan report for 172.17.0.4 Host is up (0.000018s latency). MAC Address: 02:42:AC:11:00:04 (Unknown) Nmap scan report for client1 (172.17.0.3) Host is up.Appending the /24 (CIDR Notation) to the network address means we’re looking for hosts from 172.17.0.1 to 172.17.0.255 , this can change from private IP range to another, you can use ipconfig/ifconfig commands to get your private IP range.
Now that we have discovered hosts. Let’s scan them.
Scanning Techniques
Simply using nmap with an IP as target will launch a port scan with basic information:
root@client1:/# nmap 172.17.0.2 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-09 19:53 +04 Nmap scan report for 172.17.0.2 Host is up (0.0000090s latency). Not shown: 999 closed ports PORT STATE SERVICE 80/tcp open http MAC Address: 02:42:AC:11:00:02 (Unknown) Nmap done: 1 IP address (1 host up) scanned in 1.18 secondsWe can see that port 80 is open and running the HTTP service. The service here is just indicative and deducted based on the port number. To be sure which application is running behind the port, we can use the -sV switch:
root@client1:/# nmap -sV 172.17.0.2 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-09 19:57 +04 Nmap scan report for 172.17.0.2 Host is up (0.000013s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http nginx 1.18.0 (Ubuntu) MAC Address: 02:42:AC:11:00:02 (Unknown) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.57 secondsWe now see that it’s the application running port 80 is Nginx 1.18 running on Ubuntu. The application version is useful, especially if you want to launch attacks against vulnerable application.
Filtered Ports
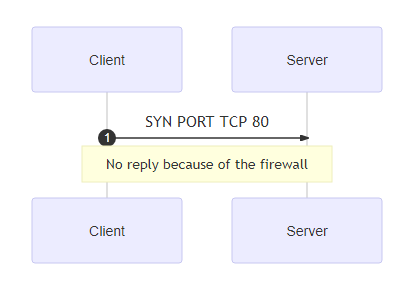
Note also that in the above examples, the port state is open, indicating that there is nothing blocking it at TCP level. Adding a firewall on this port on the server will show a different result:
PORT STATE SERVICE VERSION 80/tcp filtered httpHere, the port state is filtered. This indicates that the 3 way TCP handshake has not been completed nor ended by the target:
Evasive Scans
You can also perform evasive port scan, one of the simplest is a SYN scan with nmap -sSV 172.17.0.2 :
root@client1:/# nmap -sSV 172.17.0.2 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-09 20:52 +04 Nmap scan report for 172.17.0.2 Host is up (0.0000080s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp ProFTPD 80/tcp open http nginx 1.18.0 (Ubuntu) MAC Address: 02:42:AC:11:00:02 (Unknown) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelIn this case, nmap didn’t complete the TCP 3-way handshake and sent just a SYN. As the TCP connection is not complete, it is often not logged on the targeted system. Check out man nmap for more evasive scan options. The scan also detected a new service FTP running on port 21 served by ProFTPD.
OS Detection
Another useful feature of Nmap is the OS detection. It can be done using the -O switch:
root@client1:/# nmap -O -sV 172.17.0.2 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-09 20:38 +04 Nmap scan report for 172.17.0.2 Host is up (0.00018s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http nginx 1.18.0 (Ubuntu) MAC Address: 02:42:AC:11:00:02 (Unknown) No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=2/9%OT=80%CT=1%CU=43799%PV=Y%DS=1%DC=D%G=Y%M=0242AC%TM OS:=6022BAB3%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10D%TI=Z%CI=Z%II=I% OS:TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5 OS:=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6= OS:FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O% OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0 OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N OS:%T=40%CD=S) Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.68 secondsIt correctly detected a Linux system here and also gave us the TCP/IP fingerprint of the target. This gives us information about the TCP/IP implementation on the target.
NSE: Nmap Scripting Engine
Nmap has another feature called scripts. It allows running custom command depending on the service detected to get more information from the target. To launch the common scripts, use the -sC switch:
root@client1:/# nmap -sC 172.17.0.2 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-09 20:54 +04 Nmap scan report for 172.17.0.2 Host is up (0.000012s latency). Not shown: 998 closed ports PORT STATE SERVICE 21/tcp open ftp 80/tcp open http |_http-title: Welcome to nginx! MAC Address: 02:42:AC:11:00:02 (Unknown)We can see that Nmap got the content on the web page served by port 80 on the target:
80/tcp open http |_http-title: Welcome to nginx!This can be used to do more complex actions, adding interaction after the port has been scanned. It could for example list files on an FTP server or launch attacks like brute force on the target! More on this topic here.
Preventing Port Scanning
Port scanning can be countered through a technique called Port knocking. This involve sending a sequence on connection on different port (Like knocking on a door). If the sequence is the good one, it will then open the port allowing only the IP having done the sequence.
This is rarely used though, as the implementation on client side can be complex. Classic Firewalling is often preferred over Port knocking.
Conclusion
Port scanning is a great tool for cyber-security, and Nmap has all that is needed and even more to do this task. Be careful if you intend to scan public servers and this might be illegal. A good understanding of TCP, UDP and network protocols will allow you to do more complex discovery and scanning.