- What is Root Account in Linux
- Short History
- How do I become a Root User on Linux?
- What is the Sudo Group?
- Back to the Root User
- Who Is Root? Why Does Root Exist?
- What is root?
- Gaining Access to root Permissions
- ROOT command in Linux: what it is and how it works
- What is root
- Types of users in Linux
- When to use sudo and when to use su
- Sudo
- His
- Disable root account in Linux
- Recover root password
- with GRUB
- From a LiveCD
What is Root Account in Linux
The root account, or root user, has the highest privilege over the system, having complete control over it.
They can easily install any program with the highest privilege, create a user account, assign permissions, and give different privileges to users’ accounts.
Short History
The root account is created by the system administrator who sets up the system or server.
The default user ID for the root user in most Linux distributions is 0.
How do I become a Root User on Linux?
To log into the system as the root user, you need to use “root” as the username and the password that the system administrator used while setting up the system or server.
However, it is not recommended to directly access a Linux system with a root user; instead, create a normal account and add him to the sudo group.
What is the Sudo Group?
The sudo group exists in most Linux systems and holds root level privileges. If you add your normal user to this group, you will have access to those root level privileges.
Only the root user or a user with sudo access can add a normal user to the sudo group.
Once the normal user is added to the sudo group, they can easily execute any command with the highest privileges by adding sudo in front of each command.
$ sudo apt updateAfter that, they will require the current user’s password to execute the command.
$ sudo apt update [sudo] password for linuxtldr: Back to the Root User
Having access to the system as the root user lets some applications or packages act smartly (referring to malware) to get system access without user awareness.
In those cases, it is recommended to create an application profile by using a program like SELinux or AppArmor for Red Hat or Ubuntu.
That’s all for now. If you have any suggestions for adding more to this article, do let us know in the comment section.
Who Is Root? Why Does Root Exist?
Have you ever wondered why there is a special account named root in Linux? Do you know what are the recommended best practices to use this account? Are you aware of the scenarios where it must be used and those where it doesn’t? If you answered “yes” to one or more of these questions, keep reading.
In this post we will provide a reference with information about the root account that you will want to keep handy.
What is root?
To begin, let us keep in mind that the hierarchy of directories in Unix-like operating systems has been designed as a tree-like structure. The starting point is a special directory represented by a forward slash (/) with all other directories initially branching off from it. Since this is analogous to an actual tree, / is called the root directory.
In the following image we can see the output of:
which illustrates the analogy between / and the root of a tree.
Although the reasons behind the naming of the root account are not quite clear, it is likely due to the fact that root is the only account having write permissions inside / .
Additionally, root has access to all files and commands in any Unix-like operating system and it is often referred to as the superuser for that reason.
On a side note, the root directory (/) must not be confused with /root , which is the home directory of the root user. In fact, /root is a subdirectory of / .
Gaining Access to root Permissions
When we talk about root (or superuser) privileges, we refer to the permissions that such account has on the system. These privileges include (but are not limited to) the ability to modify the system and to grant other users certain access permissions to its resources.
The reckless use of this power can lead to system corruption at best and total failure at worst. That is why the following guidelines are accepted as best practices when it comes to accessing the privileges of the root account:
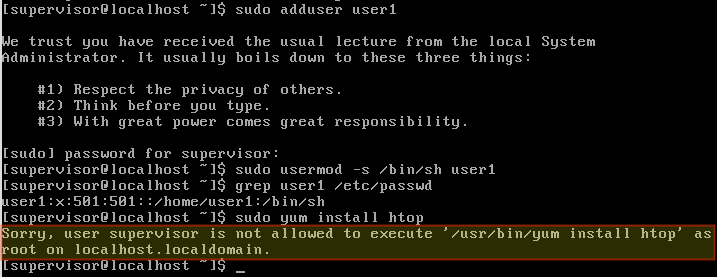
Initially, use the root account to run visudo. Use that command to edit /etc/sudoers to grant the minimum superuser privileges that a given account (e.g. supervisor) needs.
Moving forward, login as supervisor and use sudo to perform user management tasks. You will notice that attempting to perform other tasks that require superuser permissions (removing packages, for example) should fail.
Repeat the above two steps whenever needed, and once done, use the exit command to return to your unprivileged account immediately.
At this point you should ask yourself, Are the any other tasks that pop up on a periodic basis that need superuser privileges? If so, grant the necessary permissions in /etc/sudoers either for a given account or group, and continue avoiding the use of the root account at the extent possible.
Summary
This post can serve as a reference for the proper use of the root account in a Unix-like operating system. Feel free to add it to your bookmarks and return as many times as you want!
As always, drop us a note using the comment form below if you have any questions or suggestions about this article. We look forward to hearing from you!
ROOT command in Linux: what it is and how it works
If we have been using Linux for a relatively short time or we plan to give Linux a try to see if we can really do the same as in Windows, we must be clear about a series of concepts that differ from Windows but are similar to other operating systems that we probably use. such as Android smartphones. We are talking about the term root.
When we talk about rooting Android, we are talking about a method that removes all protections (to call it in a way that is easily understood) from the system and that allows you to make changes to the device that would be impossible with them. This protection is not implemented to limit the possibilities of modification that users have on their devices (which is also the case), but rather to prevent changes to the system that endanger its integrity and operation.
If we talk about Linux, unlike Android, where the device comes standard with the operating system and the corresponding customization layer of each manufacturer, the users are the ones who install the distro that we want to use on our computer, so we don’t have to No limitation when making modifications to the equipment, modifications that affect any part of the system.
What is root
The root user in Linux is the user that has administrative access to the entire system and can make any type of modification to modify its operation. It is not recommended to log in with root permissions if we are not very clear about what we are doing or if we do not want to put the stability of the system at risk if we make any changes.
If we want to make any changes to the system, it is not necessary to log in with administrator permissions, but we can request permission using the sudo application to perform administrative tasks by entering our user’s account to confirm that we are the legitimate users of that account and not it is a third person who has had access to our equipment. We can also use the su command if we need to maintain root privileges over time.
Types of users in Linux
- root . This user has absolute power and control over the computer and can do and undo as they please without any type of limitation beyond their knowledge. This type of user is, if we compare it with Windows, the administrator user, although in Linux we have much more decision-making power than in Windows.
- User . Normal users are user accounts in which a series of limitations are established based on their needs and priorities, without having the option of carrying out administrative tasks reserved for root accounts. These types of users have limited options when it comes to installing applications or creating directories on the system. However, they can gain root permissions to make any changes via the sudo or su commands.
When to use sudo and when to use su
Once we are clear that it is root and what are the possibilities of these accounts and the limitations of user accounts, it is time to talk about the sudo and su commands, commands that allow us to obtain administrator permissions to make changes to the system.
Sudo
Normal user accounts have limited ability to install off-system applications. The sudo command allows us to execute a command as root, that is, with full privileges over the system, but without ceasing to be a normal user. We must accompany this word always before any operation.
For example, if we want to install an application, as normal users we cannot carry out this process. But, if we use the sudo command first, we’re going to get root permissions to perform that operation. Once it has been done, we will once again have the limitations associated with a normal user account. Whenever we use the sudo command, we will have to enter the root password.
If we want to install another application, we will have to precede the command, again, with the word sudo and enter the administrator password.
His
While sudo allows us to obtain administrator permissions to perform certain administrative tasks such as installing applications, creating users and so on, once the command is executed, we are normal users again. If we have to perform various operations on the computer for which administrator privileges are necessary, and we do not want to add sudo to each command, we will use su and enter the root password.
As of now, we have root privileges, so we can make any changes to the system without using sudo. Being the previous example, to install the Gparted application, once we have root permissions, instead of preceding the installation command with the word sudo, we can do it without it.
When we no longer need root privileges, it is recommended to exit this mode to avoid making any unintentional changes, the exit command is used.
If we want to change the user, the command to use is the following.
Disable root account in Linux
If we use a computer with Linux that has different user accounts, it is possible that the root password ends up circulating freely in our environment without realizing it. With this password in the wrong hands, users can make any kind of changes and install applications on the system that are not necessary for everyday use. The solution to this problem, as long as we run that risk, is to disable the root account in Linux.
In this way, without a root account, users will not be able to use either sudo or su to enable administrator privileges in the system, having a positive impact on the security of the work computer. To deactivate the root account, we must open terminal and enter the following command
In this way, the computer blocks this user so that it cannot be used either with the su command or with sudo . If we want to recover the user account again, we will have to configure a new one.
Recover root password
Whether we have disabled the root account or if we have lost the master password, Linux allows us to regenerate a new password through two methods: from the boot GRUB or using a LiveCD with a Linux distribution.
with GRUB
Once the bootable GRUB is displayed, we must access the advanced options, an option that is not on the main screen, and then select Recovery Mode to then select the root option for a superuser console.
From the command line, the first thing we will do is mount the drive with write permissions with the command
Next, we will use the passwd command to set a new password.
Finally, with the commands we use the sync and reboot commands to reboot the computer and for the changes to be applied.
From a LiveCD
To recover the root password, we can use any LiveCD distro, although from ITIGIC we recommend Ubuntu. Once we have started the computer with this distribution, on the welcome screen, we select Spanish so that the interface is displayed in our language and then Try Ubuntu.
Next, we open the Terminal application and enter the following command:
Next, we must identify the partition where the Linux distribution we want to recover the root password is located. To do this we will use the command:
In the next step, we need to mount the system unit:
mkdir /mnt/recover mount /dev/sda1 /mnt/recover
In our case, the partition is sda1. If it is different on our computer, we must modify sda1 for the partition corresponding to our computer. Once we have mounted the unit, we can start working with it to recover the root password. The first thing is to go to the recovery directory with the command:
And finally, we use the passwd command to enter a new root password