- How to Secure Network Services Using TCP Wrappers in Linux
- Understanding hosts.allow and hosts.deny
- How to Use TCP Wrappers to Restrict Access to Services
- What are TCP wrappers in Linux?
- How does TCP wrappers differ from a firewall in Linux?
- Is TCP Wrapper a firewall?
- Which service Cannot be used with TCP wrappers?
- Is Ifconfig deprecated?
- What is the ETC hosts file used for?
- Can Apache be secured with TCP wrappers?
- Linux access control using TCP WRAPPERS
- Deny requests for a particular service
How to Secure Network Services Using TCP Wrappers in Linux
In this article we will explain what TCP wrappers are and how to configure them to restrict access to network services running on a Linux server. Before we start, however, we must clarify that the use of TCP wrappers does not eliminate the need for a properly configured firewall.
In this regard, you can think of this tool as a host-based access control list, and not as the ultimate security measure for your system. By using a firewall and TCP wrappers, instead of favoring one over the other, you will make sure that your server is not left with a single point of failure.
Understanding hosts.allow and hosts.deny
When a network request reaches your server, TCP wrappers uses hosts.allow and hosts.deny (in that order) to determine if the client should be allowed to use a given service.
By default, these files are empty, all commented out, or do not exist. Thus, everything is allowed through the TCP wrappers layer and your system is left to rely on the firewall for full protection. Since this is not desired, due to the reason we stated in the introduction, make sure both files exist:
# ls -l /etc/hosts.allow /etc/hosts.deny
The syntax of both files is the same:
- services is a comma-separated list of services the current rule should be applied to.
- clients represent the list of comma-separated hostnames or IP addresses affected by the rule. The following wildcards are accepted:
- ALL matches everything. Applies both to clients and services.
- LOCAL matches hosts without a period in their FQDN, such as localhost.
- KNOWN indicate a situation where the hostname, host address, or user are known.
- UNKNOWN is the opposite of KNOWN.
- PARANOID causes a connection to be dropped if reverse DNS lookups (first on IP address to determine host name, then on host name to obtain the IP addresses) return a different address in each case.
You may want to keep in mind that a rule allowing access to a given service in /etc/hosts.allow takes precedence over a rule in /etc/hosts.deny prohibiting it. Additionally, if two rules apply to the same service, only the first one will be taken into account.
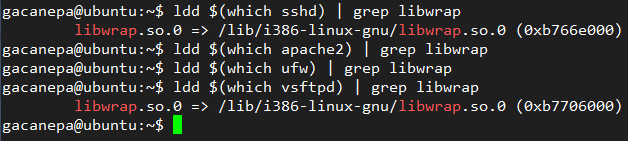
Unfortunately, not all network services support the use of TCP wrappers. To determine if a given service supports them, do:
# ldd /path/to/binary | grep libwrap
If the above command returns output, it can be TCP-wrapped. An example of this are sshd and vsftpd, as shown here:
How to Use TCP Wrappers to Restrict Access to Services
As you edit /etc/hosts.allow and /etc/hosts.deny , make sure you add a newline by pressing Enter after the last non-empty line.
To allow SSH and FTP access only to 192.168.0.102 and localhost and deny all others, add these two lines in /etc/hosts.deny :
and the following line in /etc/hosts.allow :
sshd,vsftpd : 192.168.0.102,LOCAL
# # hosts.deny This file contains access rules which are used to # deny connections to network services that either use # the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # The rules in this file can also be set up in # /etc/hosts.allow with a 'deny' option instead. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd,vsftpd : ALL ALL : ALL
# # hosts.allow This file contains access rules which are used to # allow or deny connections to network services that # either use the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd,vsftpd : 192.168.0.102,LOCAL
These changes take place immediately without the need for a restart.
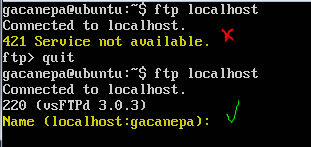
In the following image you can see the effect of removing the word LOCAL from the last line: the FTP server will become unavailable for localhost. After we add the wildcard back, the service becomes available again.
To allow all services to hosts where the name contains example.com , add this line in hosts.allow :
and to deny access to vsftpd to machines on 10.0.1.0/24, add this line in hosts.deny :
On the last two examples, notice the dot at the beginning and the end of the client list. It is used to indicate “ALL hosts and / or clients where the name or the IP contains that string”.
Was this article helpful to you? Do you have any questions or comments? Feel free to drop us a note using the comment form below.
What are TCP wrappers in Linux?
TCP Wrappers (also known as tcp_wrappers) is a host-based networking ACL system, used to filter network access to Internet Protocol servers on (Unix-like) operating systems such as Linux or BSD. However most common network service daemons today can be linked against libwrap directly.
How does TCP wrappers differ from a firewall in Linux?
For instance, an iptables-based firewall filters out unwelcome network packets within the kernel’s network stack. For network services that utilize it, TCP wrappers add an additional layer of protection by defining which hosts are or are not allowed to connect to “wrapped” network services.
Is TCP Wrapper a firewall?
TCP Wrapper can act as a firewall to prevent this. TCP Wrapper monitors incoming packets.
Are TCP Wrappers deprecated?
The TCP Wrappers package has been deprecated in RHEL 7 and therefore it will not be available in RHEL 8 or later RHEL releases.
Why is iptables important?
iptables is a user-space utility program that allows a system administrator to configure the IP packet filter rules of the Linux kernel firewall, implemented as different Netfilter modules. The filters are organized in different tables, which contain chains of rules for how to treat network traffic packets.
Which service Cannot be used with TCP wrappers?
The wrappers do not work with RPC services over TCP. The user name lookup feature of TCP Wrappers uses identd to identify the username of the remote host. By default, this feature is disabled, as identd may appear hung when there are a large number of TCP connections.
Is Ifconfig deprecated?
ifconfig has been officially deprecated for the ip suite, so while many of us are still using the old ways, it is time to put those habits to rest and move on with the world. Since there is no “without options” variant of the ip command, let’s look at how to display IP addresses associated with interfaces.
What is the ETC hosts file used for?
Description. The /etc/hosts file contains the Internet Protocol (IP) host names and addresses for the local host and other hosts in the Internet network. This file is used to resolve a name into an address (that is, to translate a host name into its Internet address).
What is use of iptables in Linux?
iptables is a command line interface used to set up and maintain tables for the Netfilter firewall for IPv4, included in the Linux kernel. The firewall matches packets with rules defined in these tables and then takes the specified action on a possible match.
What is iptables Linux?
Can Apache be secured with TCP wrappers?
If you control client access with TCP wrappers, keep as much of your client control data in the /etc/hosts. allow and /etc/hosts. deny files as you can, rather than spreading it across both TCP wrappers and iptables….TCP Wrappers: Securing Local Services.
Service HTTPS Port 443 Description Apache/web SSL Daemon httpd Linux access control using TCP WRAPPERS
As i mentioned earlier «ALL» acts as a wildcard for all services that are compatible with tcp wrappers . In the above shown example, it will allow all requests to the machine from «slashroot.in» domain.
Also note the fact that in the above case «hosts.deny» file is empty. Even if you add the same entry in hosts.deny, it will not be of any use, because hosts.allow is processed first.
Deny requests for a particular service
[root@myvm1 ~]# cat /etc/hosts.allow sshd: .slashroot.in [root@myvm1 ~]#In the above shown example sshd service is only allowed from «slashroot.in» domain.
[root@myvm1 ~]# cat /etc/hosts.allow vsftpd: .slashroot.in [root@myvm1 ~]#In the above shown example, vsftpd service is only allowed from slashroot.in domain.
Again keep the fact in mind that a conflicting entry in hosts.deny will be ignored, because hosts.allow is processed first and if a request pattern is allowed, it will never process hosts.deny file at all.
Also you can deny these same requests as shown in the above examples, by making the same entry in hosts.deny , but in that case your hosts.allow must be empty or else must not contain similar rule for allowing.
Let’s see another pattern for allowing and denying hosts.
[root@myvm1 ~]# cat /etc/hosts.allow ALL: 172.16. [root@myvm1 ~]#In the above example all hosts with the ip address 172.16.*.* is allowed to make connections to all TCP wrapper based services on the hosts.
In the above example if you add ALL: 172.16.104.54, in the file hosts.deny will not be of any use, because you have already allowed all requests from 172.16.*.* in hosts.allow file.
You can also make the same entry with IP and subnet mask based style, as shown below.
[root@myvm1 ~]# cat /etc/hosts.allow ALL: 172.16.0.0/255.255.0.0 [root@myvm1 ~]#If you want to deny or allow a large number of hosts, then you can also do that by mentioning the list of ip/hostnames in another file and pointing to that file in /etc/hosts.allow.
[root@myvm1 ~]# cat /etc/hosts.allow sshd: /etc/sshd.hosts [root@myvm1 ~]#In the above rule, an important point to note is that the rule starts with a «/», mentioning the path for the file.
Previously we saw that you can allow/deny an entire domain, but what if you want to make exceptions to some hosts on that domain.
[root@myvm1 ~]# cat /etc/hosts.allow ALL: .slashroot.in EXCEPT example.slashroot.in [root@myvm1 ~]#In the above example all hosts from slashroot.in domain will be allowed except example.slashroot.in.
In the exact similar manner, you can also deny one particular service, after allowing the rest to a group of hosts or domain, as shown below.
[root@myvm1 ~]# cat /etc/hosts.allow ALL EXCEPT sshd: 172.16.0.0/255.255.0.0 [root@myvm1 ~]#In the above shown method all hosts from 172.16.0.0 network are allowed for all the services except ssh.
The field in the tcp wrapper entry can also be used to make all entry in one files itself(Yeah that’s correct, you can use a single file for accept and deny rules. This is the best method to avoid confusion.), the syntax for such entry should be made, by taking an extra care.
[root@myvm1 ~]# cat /etc/hosts.deny vsftpd : example1.slashroot.in : allow sshd : example1.slashroot.in : deny sshd : example2.slahroot.in : allow [root@myvm1 ~]#In the above example, i have made the entry of both allowing and denying connections to service in hosts.deny file(i have kept my hosts.allow file empty). «allow» and «deny» are part of the options filed in the entry.
Another important fact that must be kept in mind is the length of the access rule that you are making in tcp wrapper files.
One rule per line is the way it must be made. Otherwise rules might get skipped without applying them while processing. There is a workaround for this problem, by including «/», for all those rules that are lengthy. An example is shown below.
In the above example, we have used backslashes to denote that the rule is one line. Also we have spawned echo process to make a text redirect to ftp log file. This kind of actions can be taken with the help of options field as shown above.
Like we have used spawn to echo some text content in ftp log, this can be made very detailed log with the help of some options.
[root@myvm1 ~]# cat /etc/hosts.allow vsftpd : 172.16.103.150 \ : spawn /bin/echo %c %h %p %u ftp access prohibited>>/var/log/ftp.log \ : deny [root@myvm1 ~]#In the above example, i have used
%c for complete client information like username and hostname
%h is used to determine client’s ip address
%p is used to log process id of the process
%u is used for username of the client who is requesting the service.
You can make much more interesting things to trigger on matching a rule, using the same spawn method and redirection .
A complete mannuel entry for TCP wrapper can be found by running the below command as shown below.
[root@myvm1 ~]# man hosts_options [root@myvm1 ~]#Hope this article was helpful in understanding the concept of TCP wrappers in Linux.