- What is a Captive Portal? Your Guide to Capturing More Business Wirelessly
- What Does “Captive Portal” Mean?
- What is Captive Portal Authorization?
- What is a Captive Portal Login?
- What are Captive Portals Used for?
- How To Set Up a Captive Portal Web Page
- How To Use a Captive Portal as a Marketing Tool
- Enhance the Guest Experience
- Bolster Your Brand Image
- Encourage Customer Loyalty
- The Benefits of Using a Captive Portal
- Launch your own branded Captive Portal
- What is a captive portal and why is it essential for your network structure?
- How does a captive portal work and why is it necessary for your network security
- The benefits of using a captive portal for your business or organization
- How to set up a captive portal on your network
- The best practices for deploying and using a captive portal
What is a Captive Portal? Your Guide to Capturing More Business Wirelessly
If you’re running a physical business, free Wi-Fi access for customers is an expected perk these days. You can simply give away your Wi-Fi password, or you can use a captive portal to restrict access to legitimate customers.
What is a captive portal? How does it work? Why do you need it for your business? Here’s everything you need to know to help you capture more business through your wireless network.
What Does “Captive Portal” Mean?
A captive portal is a customized landing page that businesses use as a primary access point to their Wi-Fi network. The client of the public access or business network is required to pass through this “portal” in order to connect to the hotspot.
Captive portals are widely used by hotels, coffee shops, shopping centers, and airports, among many others.
Small businesses can provide guests with internet access by giving them a password when they come in. But what will prevent these customers from accessing the network any time they’re within range?
One option is for business owners/managers to change the password on a regular basis. Using a captive portal, however, is the simpler solution.
What is Captive Portal Authorization?
When a user attempts to log into a public-access or business network with a captive portal, they are taken to a landing page where they must take a certain action before being given internet access.
The process of user authorization is typically in the form of an acknowledgment of the network’s usage agreement or acceptable use policy, or the entry of a pre-assigned user ID and password. You can also set up designated devices to bypass the login screen using their individual MAC address.
This means captive portals are customisable in how they allow users onto the network, depending on the businesses security requirements.
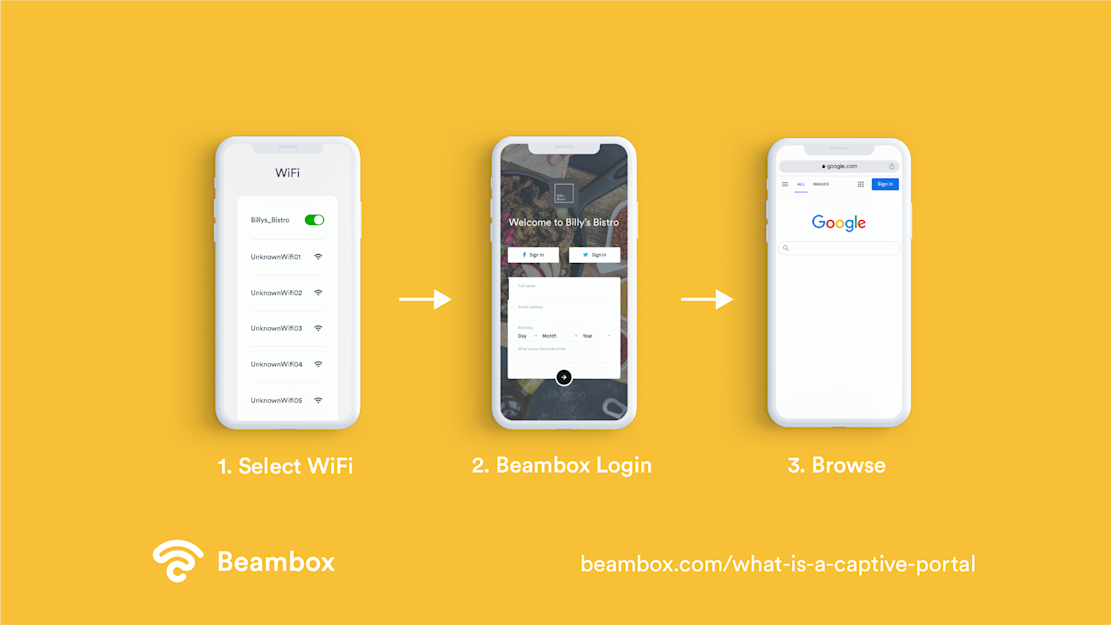
What is a Captive Portal Login?
When users try to connect to a network or open a browser while already using a particular Wi-Fi network, they are first taken to the captive portal login page.
This webpage serves as a transitional or access page that typically requires an authorized user’s log-in information.
In hotels, for example, new guests who are checking in are provided with the hotel’s Wi-Fi name and a limited-use username and password to access the internet for the length of their stay.
The guest enters their assigned username and password into the log-in page in order to use the hotel’s internet connection.
What are Captive Portals Used for?
Why should you get a captive portal for your business? Unrestricted access to your business’ internet poses security risks, both to your business and legit users, and also facilitates potential bandwidth hogging.
A captive portal’s purpose is to strengthen network security and bandwidth management, enhance the user experience, and even give you excellent opportunities for marketing and business growth.
How To Set Up a Captive Portal Web Page
Setting up a captive portal for a Wi-Fi network may vary depending on a business’ network setup. Here are the basic steps.
- Make sure your firmware is up-to-date.
- Access the web-based setup page for your network’s access point.
- Enable a captive portal for your network. Go to your network’s access point’s setup menu and find the option to enable it under “captive portal” or “global configuration.” If you can’t find the feature, you’ll need to upgrade your access point to a model that supports it.
- Customize your portal settings. You’ll be able to name your portal, protect it with a password, and choose to redirect it to an existing web page.
- Customize what your customers see when they attempt to access your wifi network. This also allows you to determine how to authorize guests.
- Associate your captive portal with a wireless radio band to control customer access, and with an SSID profile to allow guest access.
- Use a Wi-Fi enabled device to test.
How To Use a Captive Portal as a Marketing Tool
What a captive portal is for guest users and for businesses has taken on a whole new meaning. As a marketing platform, it helps companies to enhance guest user experience, capture relevant customer data to better understand regular clients, and give customers more options to engage with them.
Enhance the Guest Experience
A captive portal can give you key insights about the people who support your business. You can collect relevant and actionable marketing information from guests who log into your Wi-Fi network. Now you can utilize this to analyze metrics based on daily, weekly, and monthly network traffic and compare the business performance of multiple locations based on guest data.
Bolster Your Brand Image
With guest information collected from your login page, you can create a mailing list and ask customers for feedback. Your app will also allow you to manage all your reviews so you can publish positive ones to strengthen your online presence and divert negative reviews through an internal feedback form.
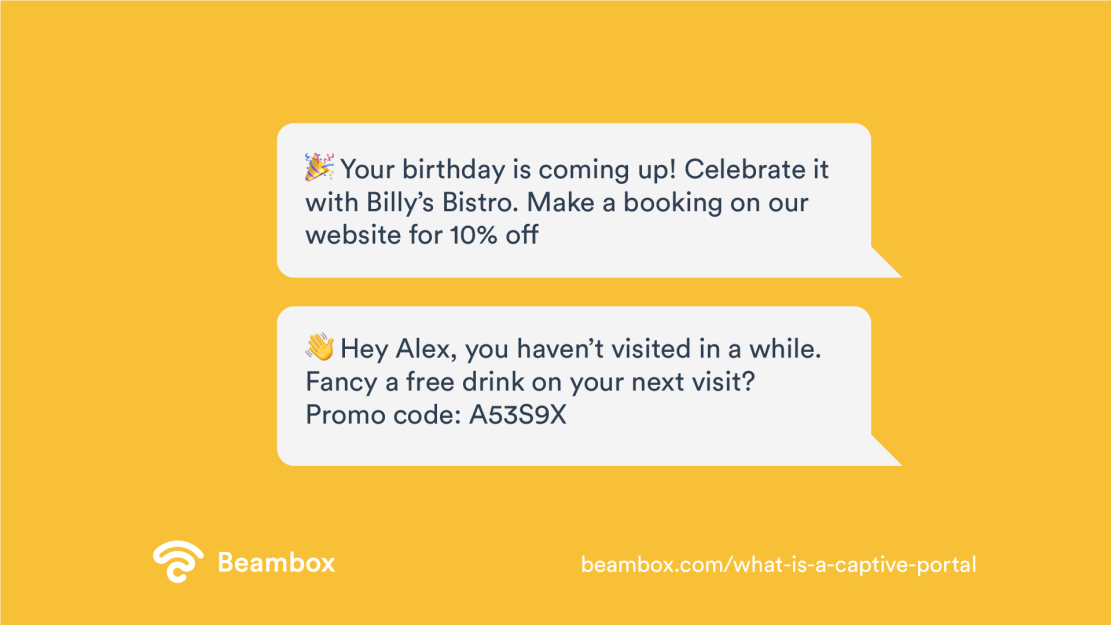
Encourage Customer Loyalty
Your captive portal can be used as a smart marketing tool that lets you customize customer engagement. Send personalized emails during birthdays. Coffee shops can use customer rewards for loyal patronage and start campaigns that increase the number of returning customers.
The Benefits of Using a Captive Portal
Now that you understand what captive portals are, let’s take a look at captive portal benefits and why you should start using one to enhance your guest services.
- Use a captive portal landing page to require users to agree with your Terms of Service. As you have no control over how your guest’s HTTP requests are used, this measure will protect you from liability in case a guest engages in illegal, malicious, or destructive online activities.
- Provide granted access to verified customers. You can make sure that only paying customers can use the internet by providing them with the password (and, sometimes, a customized username) on their receipt or together with their key card, for example.
- Control bandwidth allocation. A captive portal also lets you customize time limits for use per device or customer, limit the number of devices that can connect (per hotel room, for example), and prevent bandwidth hogging. You can program your portal page to enable “bandwidth throttling” or “traffic shaping” and limit the size of downloaded files, the download speed for large files, the number of downloads per session, or even block sites that are commonly accessed to download large files.
- Take advantage of Wi-Fi marketing options for your business. A captive portal is a web page that now has expanded uses for seamless marketing. As a marketing platform, this splash page can be used for customer surveys or reviews, sponsored ads, ongoing or upcoming promotions, and social media engagement, among others.
Launch your own branded Captive Portal
Beambox helps businesses like yours grow with data capture, marketing automation and reputation management.
What is a captive portal and why is it essential for your network structure?
A captive portal is a vitally important part of your network structure, yet it is often overlooked. A captive portal is a web page displayed to users of a wireless network before they are granted access to the internet and it is often used in public places, such as airports, hotels, and schools. It provides secure authentication and authorization for employees and customers accessing your WiFi network. Captive portals can also be used for a variety of purposes, such as marketing or tracking the activity of customers.
How does a captive portal work and why is it necessary for your network security
A captive portal is a security measure that restricts access to a network until the user meets certain criteria. This usually means providing some login or authentication, but it can also include other actions like accepting terms and conditions or completing a CAPTCHA. By requiring users to enter their credentials, you can be sure that only authorized users can use your WiFi network. Additionally, captive portals help improve network efficiency by ensuring that only authorized users are using your bandwidth or preventing users from accessing sites they don’t need to. For example, if you only want employees to access certain websites, you can use a captive portal to restrict access to those sites.
The benefits of using a captive portal for your business or organization
Captive portals are essential for any network structure because they provide a quick and easy way to control access to the internet and can be utilized for both employee and customer networks. For employees, they can be used for tracking work hours or managing bandwidth usage. For customers, captive portals provide an easy way to sign in to your network. They also help with marketing by providing information about your new products or services and displaying advertisements or promotional content to your customers before they are granted internet access.
How to set up a captive portal on your network
To set up a captive portal on your network, log in to the Omada management page and go to Wireless Control. Click Portal and then click Add Portal. You will need to give your portal a name and specify the MAC address of the access point you would like it to apply to. If you have more than one access point, you can choose which SSIDs the portal will be applied to. If you want users to be able to browse the internet without having to log in, select the Enable DNS checkbox. Otherwise, users will be directed to a login page where they can enter their credentials. To configure your captive portal’s appearance, return to the Wireless Control page and click Appearance under Portal Settings. You can choose a background image or colour and enter the text that will be displayed on the login screen. You can also specify how long users have to log in before their sessions expire. When you’re done configuring your captive portal, click Save Changes.
The best practices for deploying and using a captive portal
The best practices for deploying and using a captive portal include changing the password often and ensuring that the portal is adequately secured. It is also essential to have a clear and concise usage policy to make sure that users understand how to access the network. Additionally, you can test the captive portal before releasing it to users, whether for your employees or your customers.
While keeping your network secured, you can still give flexibility to your users by offering different ways to access your network. TP-Link Omada provides eight kinds of captive portal authentication methods, including Facebook Login, Voucher, SMS and other flexible options. Our networking solutions include a variety of security features that can help protect your users’ data when using a captive portal. On top of our multiple authentication methods, we also use a firewall to restrict access to certain ports and services, preventing unauthorized access to customer data. In addition, all of the traffic that passes through the captive portal is encrypted so that no one can see the data sent or received.

_540x300px_20220408205625c.png)