Tool Documentation:
Do not perform jamming ( -nJ ), create a wireless access point ( -e “Free Wi-Fi” ) and present a fake firmware upgrade to clients ( -T firmware-upgrade ). When a client connects, they a presented with a webpage to enter the PSK of their network:
[email protected]:~# wifiphisher -nJ -e "Free Wi-Fi" -T firmware-upgrade [*] Starting Wifiphisher 1.1GIT at 2017-02-22 13:52 [+] Selecting wlan0 interface for creating the rogue Access Point [*] Cleared leases, started DHCP, set up iptables [+] Selecting Firmware Upgrade Page template [*] Starting the fake access point. Jamming devices: DHCP Leases: 1487839973 c0:cc:f8:06:53:93 10.0.0.93 Victims-iPhone 11:c0:cc:38:66:a3:b3 HTTP requests: [*] GET 10.0.0.93 [*] GET 10.0.0.93 [*] GET 10.0.0.93 [*] POST 10.0.0.93 wfphshr-wpa-password=s3cr3tp4s5 [*] GET 10.0.0.93 [*] GET 10.0.0.93 [*] GET 10.0.0.93 Packages and Binaries:
wifiphisher
This package contains a security tool that mounts automated phishing attacks against Wi-Fi networks in order to obtain secret passphrases or other credentials. It is a social engineering attack that unlike other methods it does not include any brute forcing. It is an easy way for obtaining credentials from captive portals and third party login pages or WPA/WPA2 secret passphrases.
Installed size: 7.91 MB
How to install: sudo apt install wifiphisher
- cowpatty
- dnsmasq-base
- hostapd
- iptables
- net-tools
- python3
- python3-pbkdf2
- python3-pyric
- python3-roguehostapd
- python3-scapy
- python3-tornado
wifiphisher
[email protected]:~# wifiphisher -h usage: wifiphisher [-h] [-i INTERFACE] [-eI EXTENSIONSINTERFACE] [-aI APINTERFACE] [-iI INTERNETINTERFACE] [-pI PROTECTINTERFACE [PROTECTINTERFACE . ]] [-mI MITMINTERFACE] [-iAM MAC_AP_INTERFACE] [-iEM MAC_EXTENSIONS_INTERFACE] [-iNM] [-kN] [-nE] [-nD] [-dC DEAUTH_CHANNELS [DEAUTH_CHANNELS . ]] [-e ESSID] [-dE DEAUTH_ESSID] [-p PHISHINGSCENARIO] [-pK PRESHAREDKEY] [-hC HANDSHAKE_CAPTURE] [-qS] [-lC] [-lE LURE10_EXPLOIT] [--logging] [-dK] [-lP LOGPATH] [-cP CREDENTIAL_LOG_PATH] [--payload-path PAYLOAD_PATH] [-cM] [-wP] [-wAI WPSPBC_ASSOC_INTERFACE] [-kB] [-fH] [-pPD PHISHING_PAGES_DIRECTORY] [--dnsmasq-conf DNSMASQ_CONF] [-pE PHISHING_ESSID] options: -h, --help show this help message and exit -i INTERFACE, --interface INTERFACE Manually choose an interface that supports both AP and monitor modes for spawning the rogue AP as well as mounting additional Wi-Fi attacks from Extensions (i.e. deauth). Example: -i wlan1 -eI EXTENSIONSINTERFACE, --extensionsinterface EXTENSIONSINTERFACE Manually choose an interface that supports monitor mode for deauthenticating the victims. Example: -eI wlan1 -aI APINTERFACE, --apinterface APINTERFACE Manually choose an interface that supports AP mode for spawning the rogue AP. Example: -aI wlan0 -iI INTERNETINTERFACE, --internetinterface INTERNETINTERFACE Choose an interface that is connected on the InternetExample: -iI ppp0 -pI PROTECTINTERFACE [PROTECTINTERFACE . ], --protectinterface PROTECTINTERFACE [PROTECTINTERFACE . ] Specify the interface(s) that will have their connection protected (i.e. NetworkManager will be prevented from controlling them). Example: -pI wlan1 wlan2 -mI MITMINTERFACE, --mitminterface MITMINTERFACE Choose an interface that is connected on the Internet in order to perform a MITM attack. All other interfaces will be protected.Example: -mI wlan1 -iAM MAC_AP_INTERFACE, --mac-ap-interface MAC_AP_INTERFACE Specify the MAC address of the AP interface -iEM MAC_EXTENSIONS_INTERFACE, --mac-extensions-interface MAC_EXTENSIONS_INTERFACE Specify the MAC address of the extensions interface -iNM, --no-mac-randomization Do not change any MAC address -kN, --keepnetworkmanager Do not kill NetworkManager -nE, --noextensions Do not load any extensions. -nD, --nodeauth Skip the deauthentication phase. -dC DEAUTH_CHANNELS [DEAUTH_CHANNELS . ], --deauth-channels DEAUTH_CHANNELS [DEAUTH_CHANNELS . ] Channels to deauth. Example: --deauth-channels 1,3,7 -e ESSID, --essid ESSID Enter the ESSID of the rogue Access Point. This option will skip Access Point selection phase. Example: --essid 'Free WiFi' -dE DEAUTH_ESSID, --deauth-essid DEAUTH_ESSID Deauth all the BSSIDs in the WLAN with that ESSID. -p PHISHINGSCENARIO, --phishingscenario PHISHINGSCENARIO Choose the phishing scenario to run.This option will skip the scenario selection phase. Example: -p firmware_upgrade -pK PRESHAREDKEY, --presharedkey PRESHAREDKEY Add WPA/WPA2 protection on the rogue Access Point. Example: -pK s3cr3tp4ssw0rd -hC HANDSHAKE_CAPTURE, --handshake-capture HANDSHAKE_CAPTURE Capture of the WPA/WPA2 handshakes for verifying passphrase. Requires cowpatty. Example : -hC capture.pcap -qS, --quitonsuccess Stop the script after successfully retrieving one pair of credentials -lC, --lure10-capture Capture the BSSIDs of the APs that are discovered during AP selection phase. This option is part of Lure10 attack. -lE LURE10_EXPLOIT, --lure10-exploit LURE10_EXPLOIT Fool the Windows Location Service of nearby Windows users to believe it is within an area that was previously captured with --lure10-capture. Part of the Lure10 attack. --logging Log activity to file -dK, --disable-karma Disables KARMA attack -lP LOGPATH, --logpath LOGPATH Determine the full path of the logfile. -cP CREDENTIAL_LOG_PATH, --credential-log-path CREDENTIAL_LOG_PATH Determine the full path of the file that will store any captured credentials --payload-path PAYLOAD_PATH Payload path for scenarios serving a payload -cM, --channel-monitor Monitor if target access point changes the channel. -wP, --wps-pbc Monitor if the button on a WPS-PBC Registrar is pressed. -wAI WPSPBC_ASSOC_INTERFACE, --wpspbc-assoc-interface WPSPBC_ASSOC_INTERFACE The WLAN interface used for associating to the WPS AccessPoint. -kB, --known-beacons Broadcast a number of beacon frames advertising popular WLANs -fH, --force-hostapd Force the usage of hostapd installed in the system -pPD PHISHING_PAGES_DIRECTORY, --phishing-pages-directory PHISHING_PAGES_DIRECTORY Search for phishing pages in this location --dnsmasq-conf DNSMASQ_CONF Determine the full path of a custom dnmasq.conf file -pE PHISHING_ESSID, --phishing-essid PHISHING_ESSID Determine the ESSID you want to use for the phishing page Top Wireless Attack tools in Kali Linux 2020.1
Wi-Fi device is highly vulnerable to hacking because everywhere the signals generated by a Wi-Fi device can be discovered by anyone. Many routers contain vulnerabilities that can be exploited with software tools present in Kali Linux operating system. ISPs and Router have WPS security turn on by default that makes these devices prone to wireless attacks. Bluetooth devices are at equal risk as Wi-Fi devices, as Bluetooth signals can also be picked by anyone. This makes wireless security and pentesting an essential thing. Some of the top wireless attack tools are explained here.
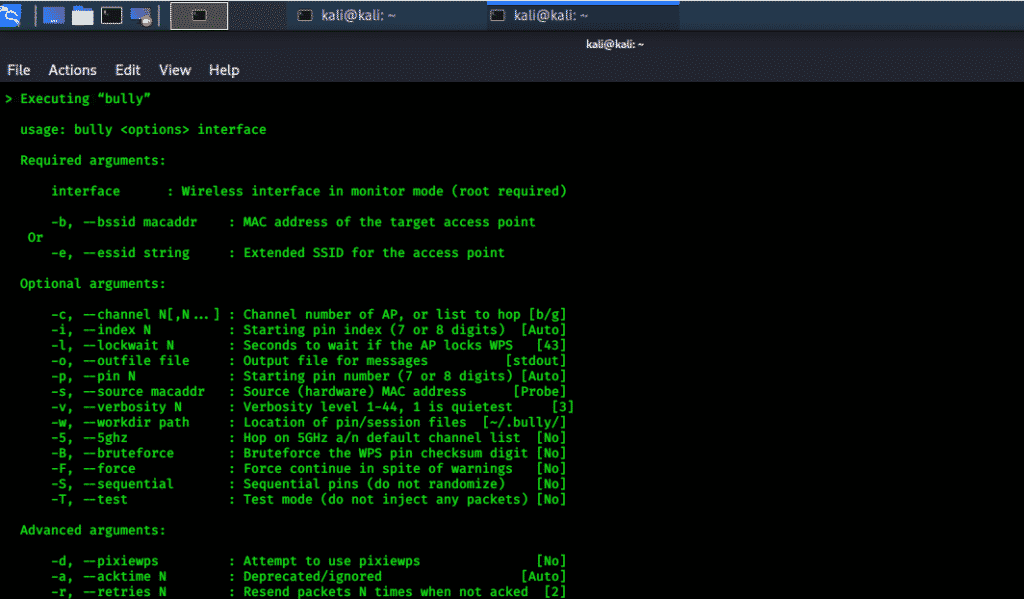
Bully:
A C-language tool that implements a WPS brute force attack that exploits the design flaws in a WPS protected device. It is reflected as an improved tool than the original Reaver code, as it incorporates limited dependencies, enhanced CPU and memory performance, precise management of errors, and a wide range of decisions. It includes various enhancements in detecting and handling of abnormal situations. It is tested on several Wi-Fi vendors that had different configuration settings with successful results. It is open-source and specifically designed for Linux operating systems.
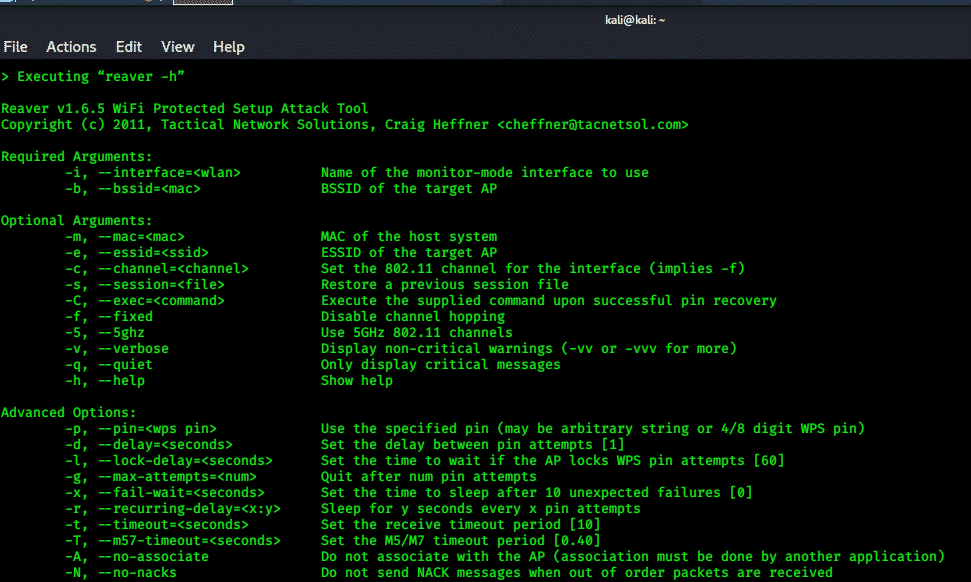
Reaver:
To recover WPA / WPA2 passphrases, Reaver adopts a brute force against Wi-Fi Protected Setup (WPS) registrar PINs. Reaver is built to be a reliable and effective WPS attack tool and is tested against a broad range of access points and WPS frameworks.
Reaver can recover the desired Access point WPA/WPA2 secured password in 4-10 hours, depending on the Access Point. But in actual practice, this time might be reduced to half.
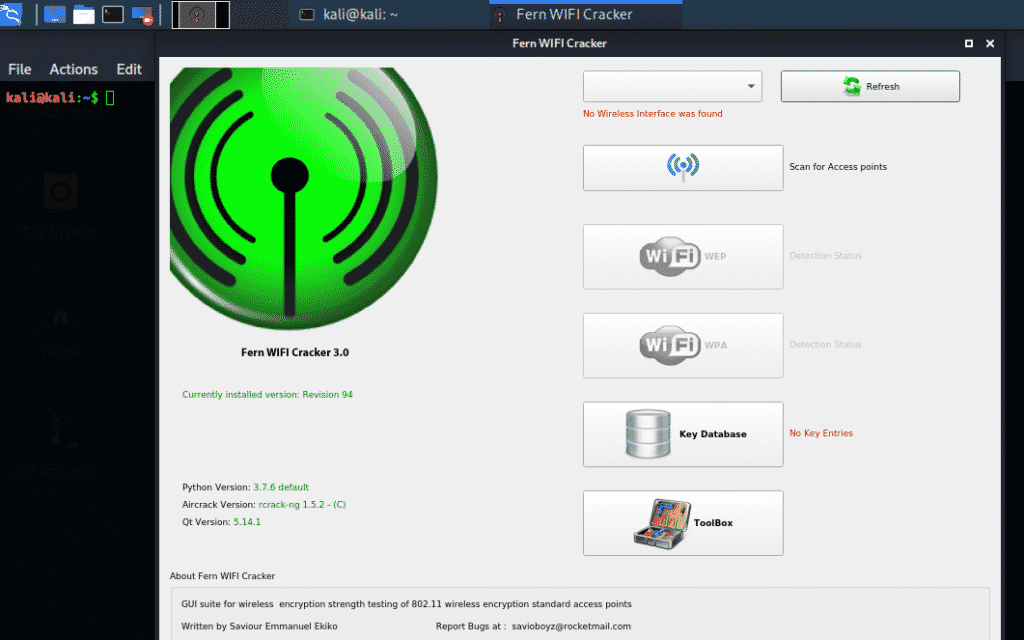
Fern wifi cracker:
A Python software tool that uses the Python Qt GUI library to perform wireless security attacks and auditing. Fern wifi cracker can crack and recover lost WPA/WEP and WPS keys. It can also launch network-based attacks on ethernet or wireless networks. It has a graphical user interface and very easy to use.
It supports WEP key cracking with many attacks such as ARP request replay, fragment attacks, caffe-latte attacks, or chop-chop attacks. It can also launch a dictionary-based attack or WPS attacks for cracking WPA/WPA2 key. After a successful attack, the recovered key is stored in a database. It has an automatic Access Point (AP) attack system and can hijack sessions in different ethernet modes. Fern can also track AP Mac address and Geographical location. It can launch brute force and internal man-in-the-middle engine attacks on HTTP, HTTPS, TELNET and FTP servers.
Spooftooph:
Spooftooph is a Bluetooth device automatic spoofing and cloning tool, and it makes a Bluetooth device disappear by cloning it. It can clone and save Bluetooth device information. It generates a new random Bluetooth profile based on the spoofed information, and the profiles get changed after a defined time. All you have to do is list down device information for Bluetooth interface and clone a device that is selected from a scan log.
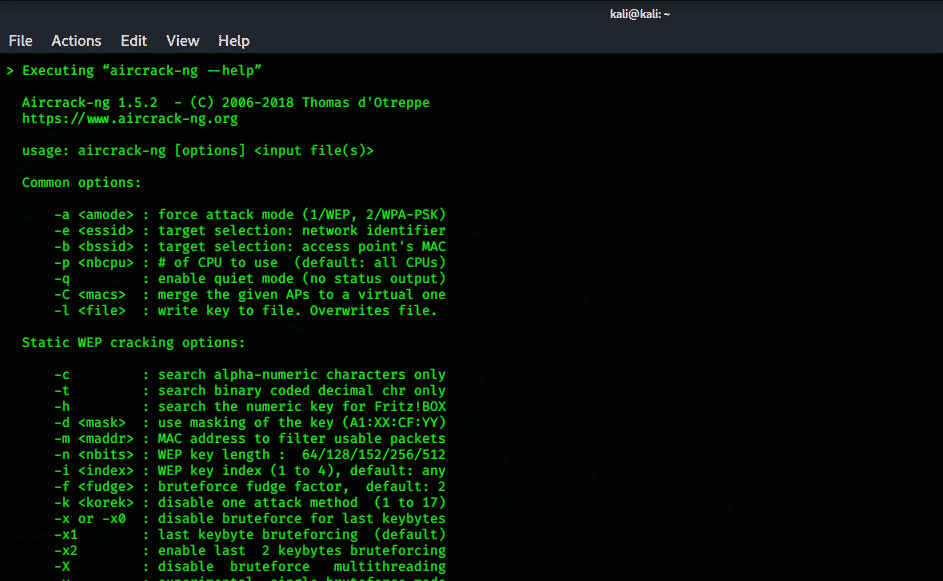
Aircrack-ng:
Aircrack-ng is one of the most popular toolkits in Kali Linux and is widely used in other distros as well. It is a key cracking utility for Wi-Fi 802.11 WEP and WPA-PSK, and through capturing data packets, keys are recovered. It launches Fluhrer, Mantin, and Shamir (FMS) attack with optimization attacks like PTW attack and KoreK attacks that in turns makes this WEP key cracking tool faster than other tools.
Kismet:
It detects, sniffs an 802.11 wireless network, and also works as an intrusion detection system. It works on layer 2 of a wireless network, but it can work with only those wireless cards that can support rfmon mode. It sniffs 802.11 a/b/g/n data traffic. Kismet can use various other programs to play audial alarms for reading out network summaries, events or deliver GPS location coordinates. Kismet has three different tools for core, client, and server.
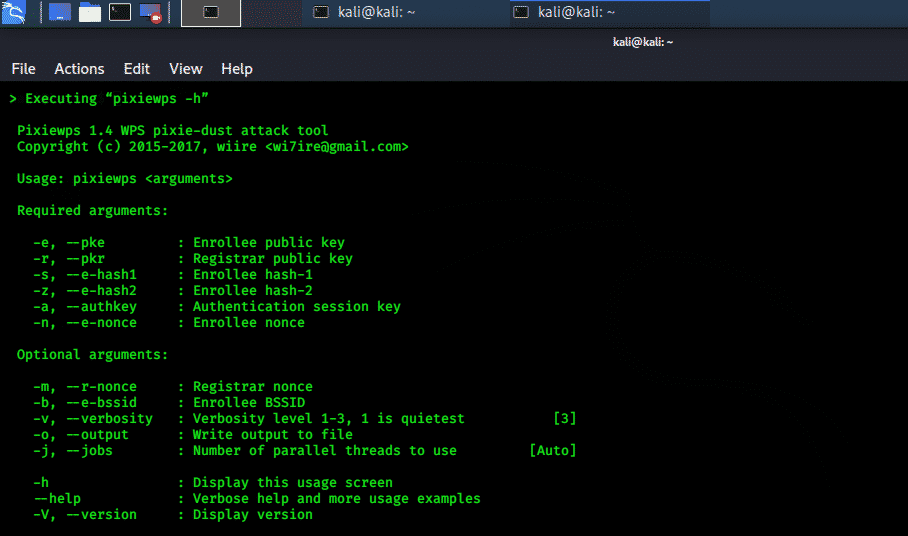
PixieWPS:
PixieWPS is a C language tool that uses brute force attacks to offline the WPS pin and exploits the low entropy of some Access Points, and this attack is called pixie dust attack. It is an opensource tool that can perform checksum optimization, produce small Diffie-Hellman keys while working with the Reaver tool. It can reduce the entropy level of some Access point seeds from 32 to 25 bit, and this is done to achieve the requirement of C LCG pseudo-random function.
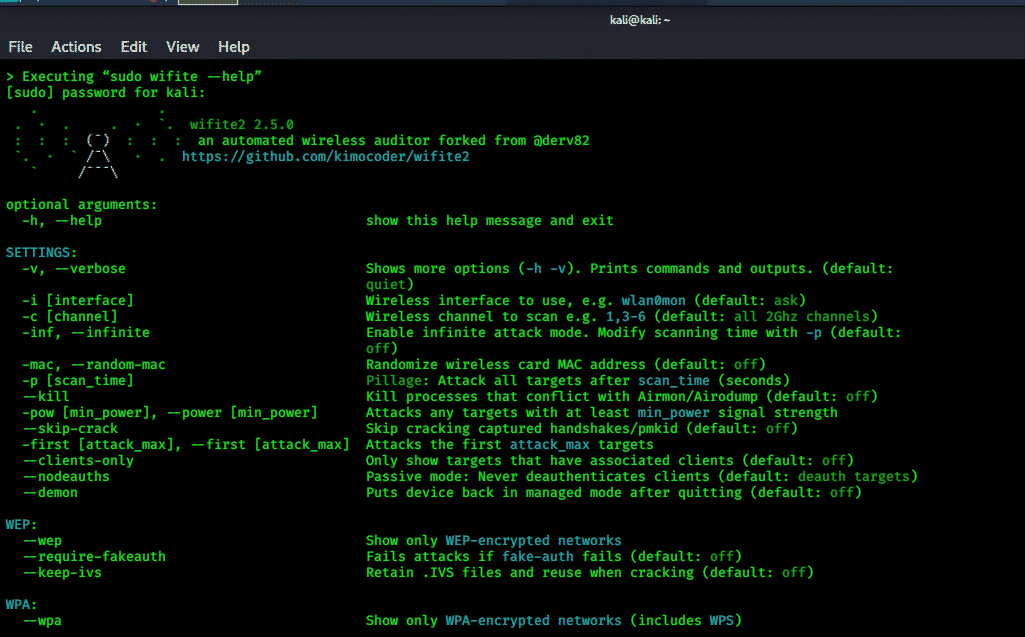
Wifite:
Wifite is a highly customizable tool with only a few arguments, and it is used for attacking networks that are encrypted by WEP, WPA, and WPS keys simultaneously. It is also known as “set it and forget it” auditing tool for wireless networks. It finds targets by their signal strength in which is measured in decibels (dB) and starts cracking the closest AP first. It de-authenticates clients on a hidden network to automatically show their SSIDs. It contains several filters for specifying a target for attack. It can change MAC address to a unique random address before attacking, and when it is done attacking the original MAC address is restored. Upon exit, the session summary is displayed with cracked keys, and cracked passwords are saved to local file cracked.txt.
Conclusion:
These are the “must-have” tools when performing wireless attacks in Kali Linux. All of these tools are open source and included in Kali Linux 2020.1 version.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.