Configuring IWA on Linux¶
Integrated Windows Authentication (IWA) is a popular authentication mechanism that is used to authenticate users in Microsoft Windows servers. It uses Negotiate/Kerberos or NTLM to authenticate users based on an encrypted ticket/message passed between a browser and a server. Follow the instructions in the sections below to configure IWA for local or federated authentication in WSO2 Identity Server (IS).
This IWA authenticator is provided OOTB and was implemented from WSO2 IS 5.3.0 onwards. It uses Kerberos internally and is the recommended approach as it overcomes some limitations of the IWA authenticator provided in previous versions of WSO2 IS which was based on NTLM. If you still want to use the previous IWA authenticator that was based on NTLM, it is available as an extension . For more information on how to setup the NTLM-based IWA authenticator, see Configuring IWA Single-Sign-On.
The benefits of using the authenticator based on Kerberos vs the authenticator based on NTLM are as follows:
- Can be used on any operating system unlike NTLM which has to be run on a Windows server.
- Performance and security on Kerberos are better.
- For more information about IWA, see Integrated Windows Authentication
- To configure Active Directory as a user store, see Configuring a Read-write Active Directory User Store.
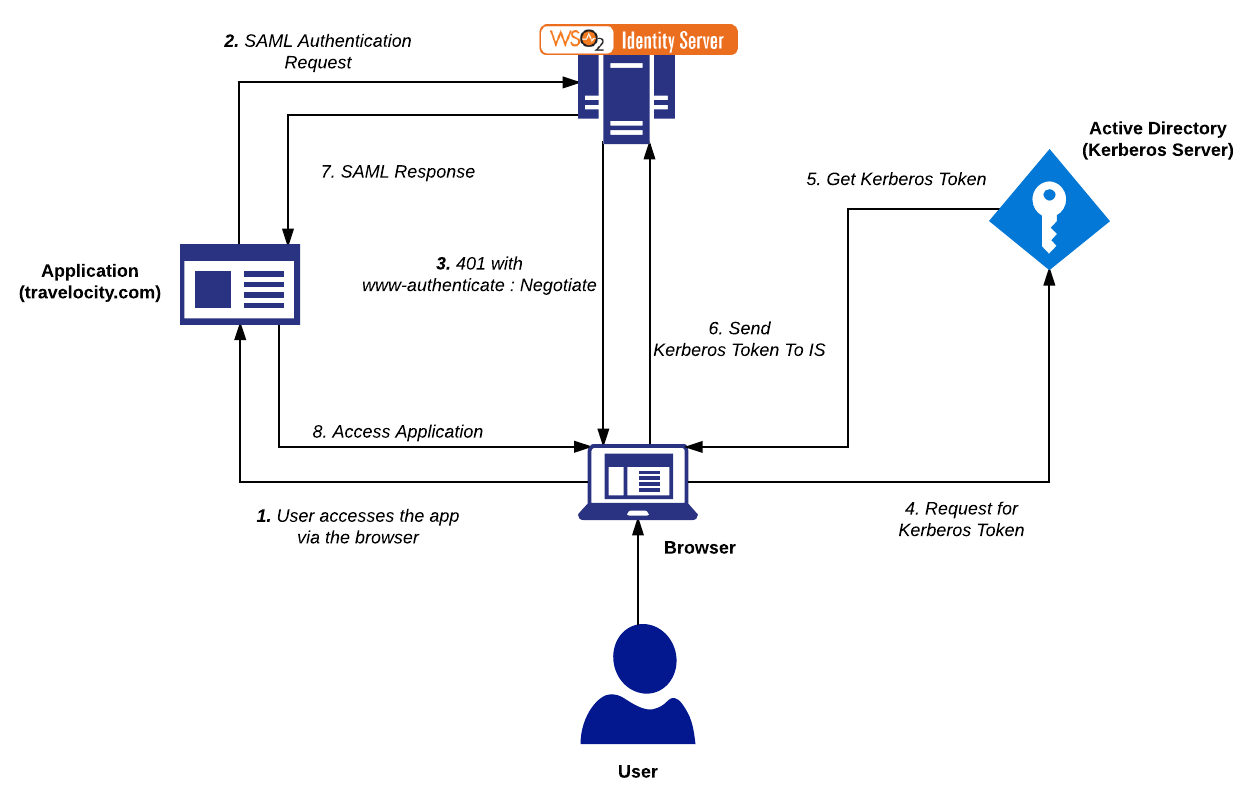
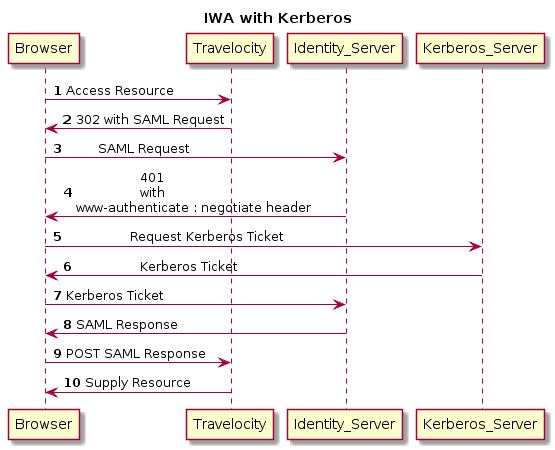
How IWA with Kerberos works¶
Setting up IWA¶
- Add a DNS host entry in the Active Directory (AD) to map the IP address of the WSO2 Identity Server to a hostname. If there are multiple Kerberos domains, WSO2 IS should have a virtual host name for each Kerberos domain.
Info When adding the DNS entry, generally the first part of the hostname is given. The AD will append the rest with its AD domain. For example, if the AD domain is ‘wso2.com, after you add a DNS host entry, the final result will be similar to the following:
[server] hostname="idp.wso2.com"Note The account used for WSO2 IS needs to be different from the one used by the user to login to the application.
Note Replace is_linux with the username of your service account in the command below. The format of the command is as follows: [setspn -A HTTP/
setspn -A HTTP/idp.wso2.com is_linux setspn -A HTTP/idp is_linuxYou can now set up IWA either as a local authenticator or as a federated authenticator.
Configuring WSO2 IS with IWA as a local or federated authenticator¶
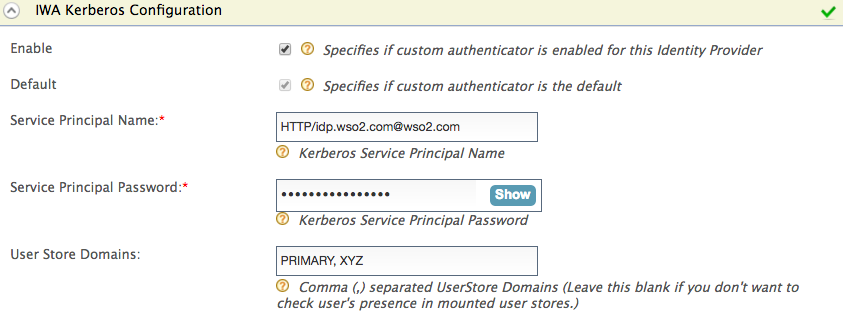
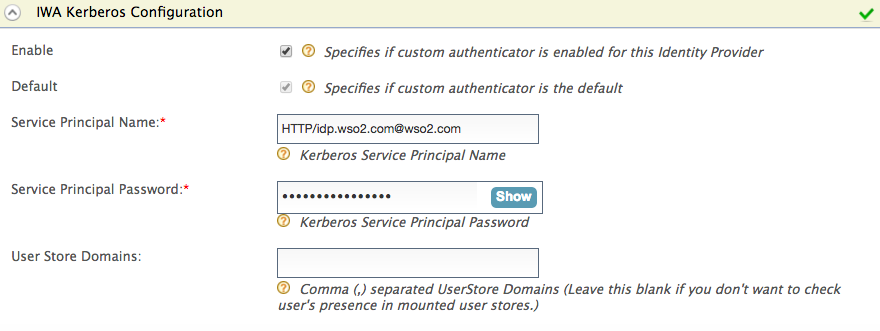
The SPNName should be the SPN you registered in step 6 of Setting up IWA, with the Active Directory domain. The SPNName follows this format:
For example, If the SPN is HTTP/idp.wso2.com , where HTTP is a service class (in this case, HTTP is not the standard protocol; it is the service class) and IS.wso2.com is the Active Directory domain, the SPNName will be HTTP/[email protected]
- To configure IWA as a local authenticator , mount the user store domain names of the relevant user stores that you expect the user to be in.
- To configure IWA as a federated authenticator , leave this field blank.
- IWA as a Local Authenticator
- IWA as a Federated Authenticator
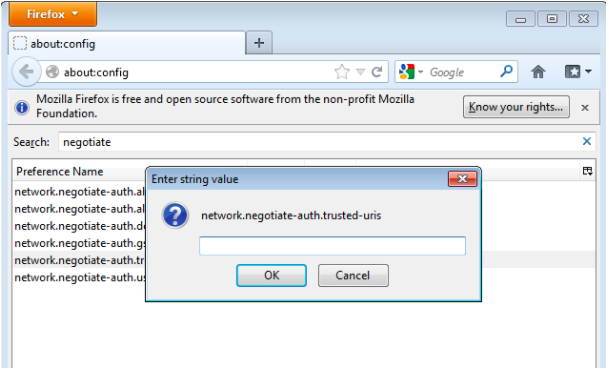 3. Add the WSO2 Identity Server URL and click OK.
3. Add the WSO2 Identity Server URL and click OK. 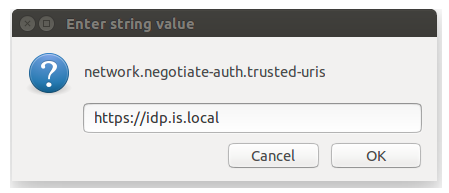 Configuring Internet Explorer/Chrome 1. Go to Tools ->Internet Options. 2. In the “security” tab select local intranet.
Configuring Internet Explorer/Chrome 1. Go to Tools ->Internet Options. 2. In the “security” tab select local intranet. 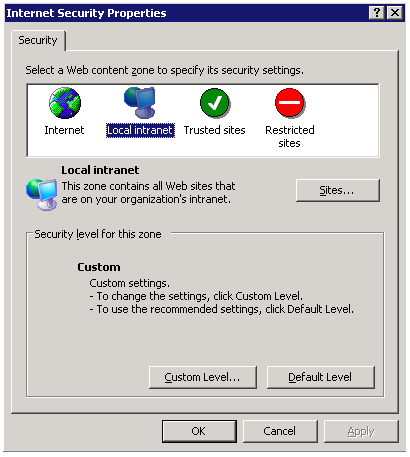 3. Click the Sites button. Then add the URL of WSO2 Identity Server there.
3. Click the Sites button. Then add the URL of WSO2 Identity Server there. 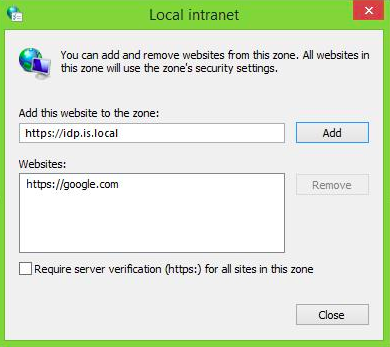 Chrome simply inherits the settings from Internet Explorer. So you don’t have to configure anything additionally.
Chrome simply inherits the settings from Internet Explorer. So you don’t have to configure anything additionally.Testing the IWA authenticator¶
- Set up IWA as a local authenticator or as a federated authenticator by following the steps above.
- Download and set up the Travelocity sample application. To do this, follow the instructions on the Deploying the Sample Applications page.
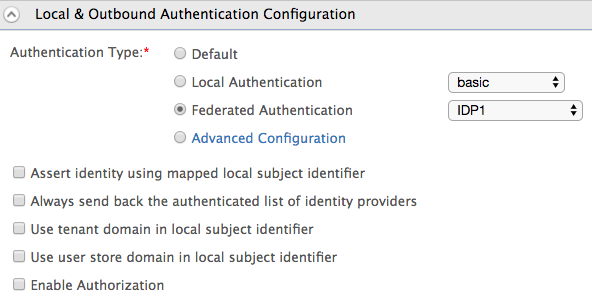
- Edit the service provider you created for the Travelocity sample, and expand the Local and Outbound Authentication section.
- Select Federated Authentication as the Authentication Type and select the identity provider you created above.
- Restart the Apache Tomcat server and run the Travelocity sample application from a Windows machine.
- Use hostnames only (no IP addresses).
- Check the configuration of the jaas.conf file, particularly the isInitiator=false property under the Server section (see step 3 of the Setting Up IWA section).
- Make sure that your service principal (IS) is associated with only one account.
- If you get an exception with an error message similar to “Checksum failed”, check whether you have given the correct password.
Connect To SQL Server With Windows Authentication From A Linux Machine Through JDBC
I want to be able to connect to a SQL Server using jdbc and windows authentication. I saw some answers on the internet saying i should add the following property to the connection string:
To the java path. But this, as far as i understand applies only when i’m connecting from a Windows machine. When i try this on a Linux machine i get:
java.sql.SQLException: This driver is not configured for integrated authentication «dll» is a hint that this is probably a windows library. On Linux you’d probably have a «.so» or something other than «dll».
Thank you @GordThompson my problem is that I can’t use jTDS as I also use ssl and the jTDS has a bug that prevents using ssl.
6 Answers 6
Well, eventually I answer my own question: This is not possible to use Windows authentication from a linux machine using the Microsoft JDBC driver. This is possible using the jTDS JDBC driver using the following connection string:
jdbc:jtds:sqlserver://host:port;databaseName=dbname;domain=domainName;useNTLMv2=true; Thank you all for all the comments
I am trying to implement the same. I am able to connect to SqlServer using jtDs and Windows Authentication from Unix machine but the insert queries are failing. Requesting you to please take a look at this Stack Overflow question
How are you proving user auth details in this connection string ? I need to embed everything in the connection url.
@Pradatta to provide the user and password in the connection string simply add them as key-value pairs at the end of the url. The template url for SQL Server is: jdbc:jtds:
@zuckermanori Thanks. I exactly did that by random guess, after posting this comment, And it worked. Thanks a lot.
It is not possible to use native Windows Authentication for JDBC connections to MSSQL from a JVM running on Linux.
This MSDN article explains the authentiation methods with JDBC on Linux, potential errors, and available options:
- NativeAuthentication (default) – This uses the sqljdbc_auth.dll and is specific to the Windows platform. This was the only option prior to the JDBC 4.0 driver.
- JavaKerberos – Makes use of the Java API’s to invoke kerberos and does not rely on the Windows Platform. This is java specific and not bound to the underlying operating system, so this can be used on both Windows and Linux platforms.
The following document outlines how to use Kerberos with the JDBC Driver and walks through what is needed to get JavaKerberos working properly.
I read this article as well. I still don’t understand if i can use the JavaKerberos flag to authenticate with Windows authentication.
@zuckermanori Kerberos authentication requires a Kerberos server. It is a different standard than native Windows authentication. So you need to check with your system / network administrator first if Kerberos is available for your environment.
I know it is different, i’m looking for a way to use Windows authentication, not kerberos. Thanks anyway.
Kerberos can (and does) work with Active Directory via LDAP (usually). If you can get Kerberos configured and talking with your active directory service, then you should be able to authenticate through it to you MS SQL Server. I’m in the process of proving if this works (or not).
@Mishter_Jingles — Never had the time to go into the kerberos solution (Adds a level of complexity that I don’t have time to work through right now). I’ll try it again at some point.. Just not now.
For those who are using DBeaver the way to connect to the SQL Server Database is:
In order to connect to the SQL Server from Linux Debian using DBeaver
1.- Select SQL Server jTDS driver
2.- Enter the connection information
3.- Go to Driver Properties tab and add the domain, user, password
Just as a note, in some post I found that they needed to change the property USENTLMV2 to TRUE but it worked for me either by putting the USERTLNMV2 in true or false.
A problem that I found was that when I was trying to connect to the database using my user and password the next error was thrown:
Login failed. The login is from an untrusted domain and cannot be used with Windows authentication.
This error was thrown because of my user was about to expire. I tried with another AD user and it could connect.
I know this is kind of an older topic but in case Google sends people here:
There are two main JDBC drivers for SQL Server. One is from Microsoft and the other from jTDS. jTDS can, amazingly, connect using Windows auth (NTLM) from other platforms, including Linux, as described here: http://jtds.sourceforge.net/faq.html#windowsAuth. It can, of course, also use SQL-authenticated logins. SQL-authenticated logins are no harder to use from any OS than any other, so don’t forget about those an option.
The version provided by Microsoft is the one from which @mjn provided a quote from the documentation. It is able to connect using Windows authentication by specifying integratedSecurity=true , authenticationScheme=javaKerberos , and authentication=NotSpecified .
It is tricky to get this working even if you don’t go out of your way to find more confusion, so always keep in mind which driver you are using — and tell us in these posts so that you can get more specific help.