- Wireshark windows or linux
- 1.2.1. Microsoft Windows
- 1.2.2. macOS
- 1.2.3. UNIX, Linux, and BSD
- Capture Protocol Packets from Remote Windows or Linux Computer using Wireshark
- Author: Srikanta
- One thought on “Capture Protocol Packets from Remote Windows or Linux Computer using Wireshark”
- Leave a Reply Cancel reply
- You might be interested in:
- Most viewed in this month
Wireshark windows or linux
The amount of resources Wireshark needs depends on your environment and on the size of the capture file you are analyzing. The values below should be fine for small to medium-sized capture files no more than a few hundred MB. Larger capture files will require more memory and disk space.
A busy network can produce huge capture files. Capturing on even a 100 megabit network can produce hundreds of megabytes of capture data in a short time. A computer with a fast processor, and lots of memory and disk space is always a good idea.
If Wireshark runs out of memory it will crash. See https://gitlab.com/wireshark/wireshark/-/wikis/KnownBugs/OutOfMemory for details and workarounds.
Although Wireshark uses a separate process to capture packets, the packet analysis is single-threaded and won’t benefit much from multi-core systems.
1.2.1. Microsoft Windows
Wireshark should support any version of Windows that is still within its extended support lifetime. At the time of writing this includes Windows 10, 8.1, Server 2019, Server 2016, Server 2012 R2, and Server 2012. It also requires the following:
- The Universal C Runtime. This is included with Windows 10 and Windows Server 2019 and is installed automatically on earlier versions if Microsoft Windows Update is enabled. Otherwise you must install KB2999226 or KB3118401.
- Any modern 64-bit Intel or Arm processor.
- 500 MB available RAM. Larger capture files require more RAM.
- 500 MB available disk space. Capture files require additional disk space.
- Any modern display. 1280 × 1024 or higher resolution is recommended. Wireshark will make use of HiDPI or Retina resolutions if available. Power users will find multiple monitors useful.
- A supported network card for capturing
- Ethernet. Any card supported by Windows should work. See the wiki pages on Ethernet capture and offloading for issues that may affect your environment.
- 802.11. See the Wireshark wiki page. Capturing raw 802.11 information may be difficult without special equipment.
- Other media. See https://gitlab.com/wireshark/wireshark/-/wikis/CaptureSetup/NetworkMedia.
Older versions of Windows which are outside Microsoft’s extended lifecycle support window are no longer supported. It is often difficult or impossible to support these systems due to circumstances beyond our control, such as third party libraries on which we depend or due to necessary features that are only present in newer versions of Windows such as hardened security or memory management.
- Wireshark 3.6 was the last release branch to officially support 32-bit Windows.
- Wireshark 3.2 was the last release branch to officially support Windows 7 and Windows Server 2008 R2.
- Wireshark 2.2 was the last release branch to support Windows Vista and Windows Server 2008 sans R2
- Wireshark 1.12 was the last release branch to support Windows Server 2003.
- Wireshark 1.10 was the last release branch to officially support Windows XP.
See the Wireshark release lifecycle page for more details.
1.2.2. macOS
Wireshark supports macOS 10.14 and later. Similar to Windows, supported macOS versions depend on third party libraries and on Apple’s requirements. Apple Silicon hardware is supported natively starting with version 4.0
- Wireshark 3.6 was the last release branch to support macOS 10.13.
- Wireshark 3.4 was the last release branch to support macOS 10.12.
- Wireshark 2.6 was the last release branch to support Mac OS X 10.6 and 10.7 and OS X 10.8 to 10.11.
- Wireshark 2.0 was the last release branch to support OS X on 32-bit Intel.
- Wireshark 1.8 was the last release branch to support Mac OS X on PowerPC.
The system requirements should be comparable to the specifications listed above for Windows.
1.2.3. UNIX, Linux, and BSD
Wireshark runs on most UNIX and UNIX-like platforms including Linux and most BSD variants. The system requirements should be comparable to the specifications listed above for Windows.
Binary packages are available for most Unices and Linux distributions including the following platforms:
- Alpine Linux
- Arch Linux
- Canonical Ubuntu
- Debian GNU/Linux
- FreeBSD
- Gentoo Linux
- HP-UX
- NetBSD
- OpenPKG
- Oracle Solaris
- Red Hat Enterprise Linux / CentOS / Fedora
If a binary package is not available for your platform you can download the source and try to build it. Please report your experiences to wireshark-dev[AT]wireshark.org.
Capture Protocol Packets from Remote Windows or Linux Computer using Wireshark
Wireshark is a widely used networking tool to capture and analyze protocol packets from networking interfaces of local or remote computer. When two networking devices, like computer, mobile, printer etc, communicate with each other, they exchange information in form of data chunks, also known as protocol packets or messages. This is also true when we access some website, send or receive emails or even we send messages using WhatsApp. Sometimes you need to capture the protocol packets that are being exchanged among networking devices, especially, if you are a network administrator. You want to do so to debug some problem when something wrong in the network is happening or to detect unusual or harmful behavior of any user of your network. Capturing packets from local computer is very trivial, by default Wireshark does that. Many times capturing local system is not sufficient. To understand the overall networking behavior, you might need to capture packets from one or more routers. Routers are usually remote systems, not where you work. The routers could be Windows or Linux computers, most of the time they are Linux ones. This guide will help to configure Wireshark to capture protocol packets from remote computer.
Capturing packet from remote Windows system
- WinPcap needs to be installed on the remote Windows computer. If WireShark is installed on that computer, WinPcap is already there. If not, install WireShark there.
- Open the services panel of the remote computer. Type “View Local Service” on the windows search box if you are using Windows 8 or “services.msc” in the run box of the start menu for pre-Windows 8 systems.
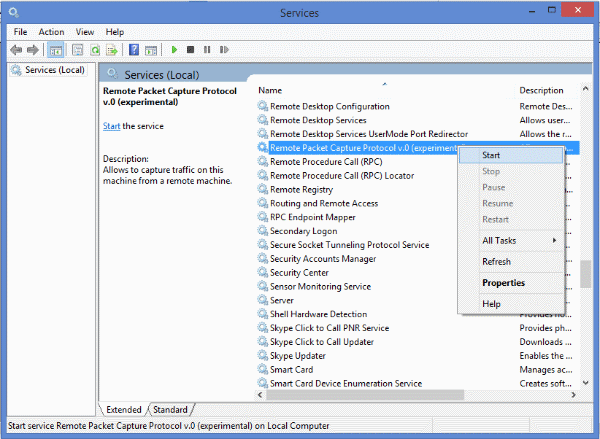
- Start the “Remote Packet Capture Protocol” service.
By default this service is not started. To start the right-click of the service and press start.
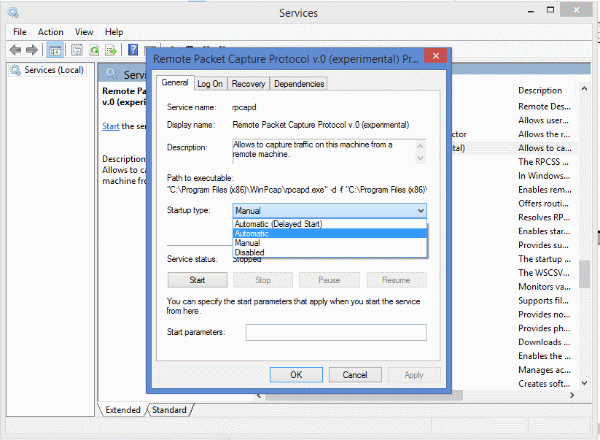
- If you want this service to automatically start after system reboot, double click on the service.
Select “Automatic” from the “Startup type” drop down box. Press Apply and then OK.
- Launch the WireShark application on the local computer where you want to see the captured packets.
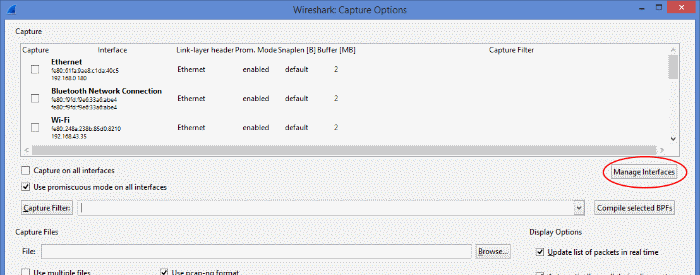
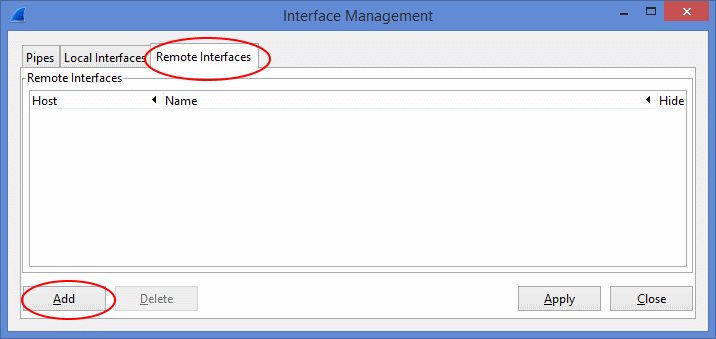
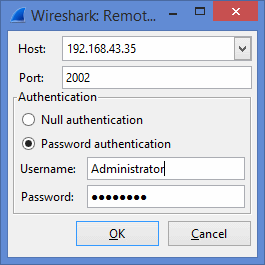
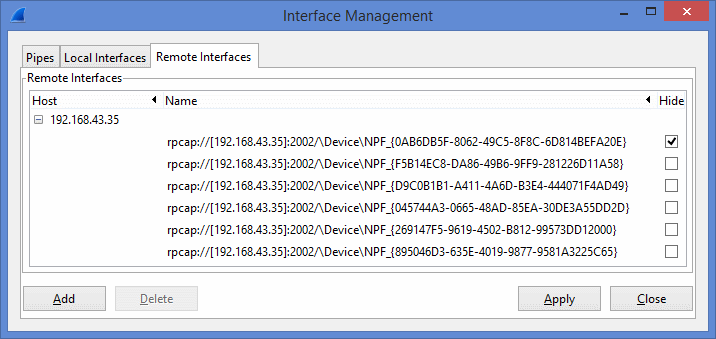
- Select “Capture -> Options”. Then press “Manage Interfaces” to open the “Interface Management” window.
Enter the IP address of the remote computer. In this example IP of the remote computer is 192.168.43.35. Enter 2002 as Port. Then Username and Password of the remote computer.
- All the network interfaces of the remote computer will be listed in the middle list. Select the interfaces you want to capture and press “Apply”.
- The selected netwok intefaces will be added to the main “Wireshark Capture Options” windws’ interface list. Now press “start” on the “Wireshark Capture Options” to capture the packets on the selected network interfaces of the remote computer.
Capturing packet from remote Linux system
- The packet capturing tool in Linux is called tcpdump. So tcpdump needs to be installed on the remote Linux computer. Install tcpdump on RedHat based linux if not already installed.
plink.exe -ssh -pw pass123 root@192.168.0.1 "tcpdump -ni ens33 -s 0 -w - not port 22" | "C:Program FilesWiresharkWireshark.exe" -k -i -
Author: Srikanta
I write here to help the readers learn and understand computer programing, algorithms, networking, OS concepts etc. in a simple way. I have 20 years of working experience in computer networking and industrial automation. View all posts by Srikanta
If you also want to contribute, click here.
Author Srikanta Posted on January 15, 2016 February 15, 2017 Categories Networking, Technology Tags Wireshark
One thought on “Capture Protocol Packets from Remote Windows or Linux Computer using Wireshark”
“Remote Packet Capture Protocol” service is NOT installed with WinPcap or NPcap. I don’t understand where did you and Wireshark devs. got the idea that installing NPcap or WinPcap will also install such a service, but that’s simply not true. At least at the time of writing this comment (2019-04-11).
Leave a Reply Cancel reply
You might be interested in:
Most viewed in this month
- C Program to Append to a File 1k views
- C Program to Sleep in Milliseconds 489 views
- C Program to Implement a Singly Linked List 479 views
- How to install Ping or Ping6 using YUM 394 views
- Change a Variable from inside a C Function 317 views
- C Program to Count Characters, Words and Lines in a File 261 views
- C Program to Get a Digit of Any Position of a Number 233 views
- C Program to Find the Longest Word in a String 184 views
- How to Implement Periodic and Single Shot Timers in Linux? 183 views
- C Program to Toggle Bits 161 views